1、说明
kubernetes nginx-ingress 为了安全考虑默认仅使用TLS 1.2,对于还在使用TLS1.0,TLS1.1的客户端或浏览器,官网介绍,需要配置ConfigMap(nginx-config 或者 nginx-configuration)来解决。
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-config
data:
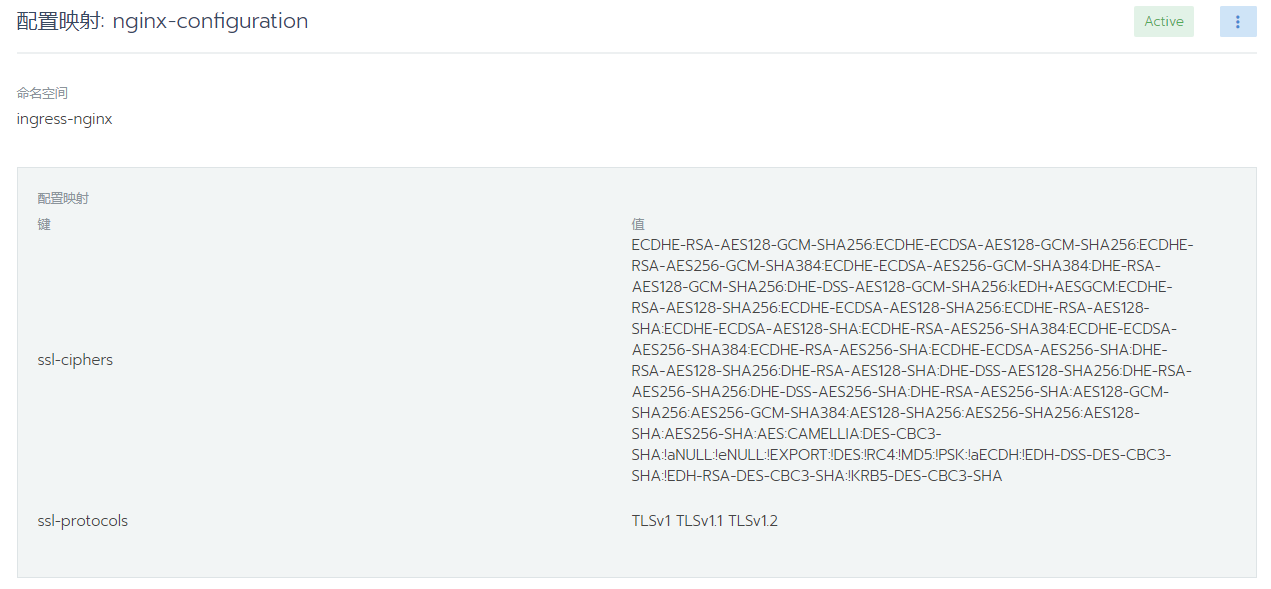
ssl-ciphers: "ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:CAMELLIA:DES-CBC3-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA"
ssl-protocols: "TLSv1 TLSv1.1 TLSv1.2"2、配置
如果使用 Rancher,可以在各个集群的 System项目 -> 配置映射 -> 命名空间 ingress-nginx 下找到 nginx-configuration,添加 ssl-ciphers 和 ssl-protocols 这两个键值对即可。
3、验证
可以通过下面2种方式进行验证
1)nmap ,需安装 yum install -y nmap,
nmap --script ssl-enum-ciphers -p 443 www.baidu.com2)curl,
curl -v --tlsv1.0 https://www.baidu.com输出:SSL connection using TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA,即支持。
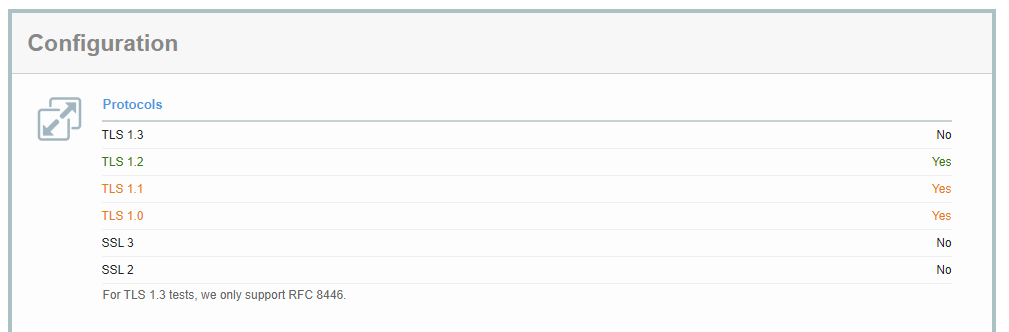
3)可以用 https://www.ssllabs.com/ssltest 网站验证
参考:
https://kubernetes.github.io/ingress-nginx/user-guide/tls/#default-tls-version-and-ciphers
https://www.cnblogs.com/lyc94620/p/11345124.html
https://blog.csdn.net/jacksonary/article/details/94756633
...