一:服务端安装ldap
yum install db4 db4-utils db4-devel cyrus-sasl* krb5-server-ldap -y
yum install openldap openldap-servers openldap-clients openldap-devel compat-openldap -y
cd /usr/share/openldap-servers

cp DB_CONFIG.example /var/lib/ldap/DB_CONFIG
cd /etc/openldap/schema/
cd /usr/share/doc/krb5-server-ldap-1.15.1/
cp kerberos.schema /etc/openldap/schema/
cd /etc/openldap
cp /usr/share/openldap-servers/slapd.ldif /etc/openldap
cd /etc/openldap
vi slapd.ldif
修改1:
include: file:///etc/openldap/schema/core.ldif
include: file:///etc/openldap/schema/corba.ldif
include: file:///etc/openldap/schema/cosine.ldif
include: file:///etc/openldap/schema/duaconf.ldif
include: file:///etc/openldap/schema/dyngroup.ldif
include: file:///etc/openldap/schema/pmi.ldif
include: file:///etc/openldap/schema/inetorgperson.ldif
include: file:///etc/openldap/schema/java.ldif
include: file:///etc/openldap/schema/misc.ldif
include: file:///etc/openldap/schema/nis.ldif
include: file:///etc/openldap/schema/openldap.ldif
include: file:///etc/openldap/schema/ppolicy.ldif
include: file:///etc/openldap/schema/collective.ldif
修改2:
dn: olcDatabase=monitor,cn=config
objectClass: olcDatabaseConfig
olcDatabase: monitor
olcAccess: to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,c
n=auth" read by dn.base="cn=Manager,dc=hadoop,dc=com" read by * none
#
# Backend database definitions
#
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=hadoop,dc=com
olcRootDN: cn=Manager,dc=hadoop,dc=com
oclRootPW: {SSHA}3Gu7KienllejvDUUhGpLZGKKpILyjhaY
olcDbDirectory: /var/lib/ldap
olcDbIndex: objectClass eq,pres
olcDbIndex: ou,cn,mail,surname,givenname eq,pres,sub
生成基础账号密码:
slappasswd
输入:123456
生成:{SSHA}r2fcL6Exxgr8oKkaWROUQDCZKqXrH7bE
二:生成基础配置文件
把最初 slapd.d 进行备份:
mv slapd.d slapd.d.bak
mkdir slapd.d
chown -R ldap:ldap slapd.d
slapadd -n 0 -F slapd.d -l slapd.ldif
slaptest -u 测试是否成功
cp slapd.d.bak/cn\=config/olcDatabase={2}hdb.ldif slapd.d/cn\=config/
修改 {2}hdb.ldif :
olcSuffix: dc=hadoop,dc=com
olcRootDN: cn=Manager,dc=hadoop,dc=com
olcRootPW: {SSHA}B8/sd62sgK+wdzOk7ZPhu4ZxQI3jKCXo(注意,一定要在最后一行,不然没法启动)
查看 ll /var/lib/ldap,ll /etc/openldap 权限是否都是 ldap
chown -R ldap:ldap slapd.d
三:启动服务
systemctl start slapd
systemctl enable slapd
systemctl status slapd验证slapd服务是否已经启动
$ ps aux | grep slapd | grep -v grep
ldap 1290 0.0 0.0 714732 6312 ? Ssl 20:53 0:00 /usr/sbin/slapd -u ldap -h ldapi:/// ldap:///
$ netstat -tunlp | grep :389
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 1290/slapd
tcp6 0 0 :::389 :::* LISTEN 1290/slapd
四:添加一个kerberos用户
kadmin.local -q "addprinc [email protected]"
kadmin.local -q "addprinc ldap/[email protected]"
kadmin.local -q "addprinc -randkey ldap/[email protected]"
kadmin.local -q "xst -k /etc/openldap/ldap.keytab ldap/[email protected]"
kadmin.local -q "ktadd -k /etc/openldap/ldap.keytab ldap/[email protected]"
chown ldap:ldap /etc/openldap/ldap.keytab && chmod 640 /etc/openldap/ldap.keytab
klist -ket ldap.keytab(查看生成的keytab文件)
kinit ldapadmin
确保 LDAP 启动时使用上一步中创建的keytab文件,在 vi /etc/sysconfig/slapd 增加 KRB5_KTNAME 配置:
vi /etc/sysconfig/slapd
export KRB5_KTNAME=/etc/openldap/ldap.keytab重启ldap:
service slapd restart
五: vi /etc/openldap/modify.ldif
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=hadoop,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: uid=ldapadmin,ou=people,dc=hadoop,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: 123456
dn: cn=config
changetype: modify
add: olcAuthzRegexp
olcAuthzRegexp: uid=([^,]*),cn=GSSAPI,cn=auth uid=$1,ou=people,dc=hadoop,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to dn.base="" by * read
olcAccess: {1}to * by dn="uid=ldapadmin,ou=people,dc=hadoop,dc=com" write by * read
六: 使用下面命令导入更新配置:
ldapmodify -Y EXTERNAL -H ldapi:/// -f modify.ldif
如果 报错:
ldap_modify: Inappropriate matching (18)
additional info: modify/add: olcRootPW: no equality matching rule
修改对应的add为replace即可。
七:添加用户和组
vi setup.ldif
dn: dc=hadoop,dc=com
objectClass: top
objectClass: dcObject
objectclass: organization
o: hadoop com
dc: hadoop
dn: ou=people,dc=hadoop,dc=com
objectclass: organizationalUnit
ou: people
description: Users
dn: ou=group,dc=hadoop,dc=com
objectClass: organizationalUnit
ou: group
dn: uid=ldapadmin,ou=people,dc=hadoop,dc=com
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
cn: LDAP admin account
uid: ldapadmin
sn: ldapadmin
uidNumber: 1001
gidNumber: 100
homeDirectory: /home/ldap
loginShell: /bin/bash
ldapadd -x -D "uid=ldapadmin,ou=people,dc=hadoop,dc=com" -w 123456 -f setup.ldif
八:采用工具导入用户和组(生成passwd.ldif文件)
yum install migrationtools -y
cd /usr/share/migrationtools/
vi migrate_common.ph
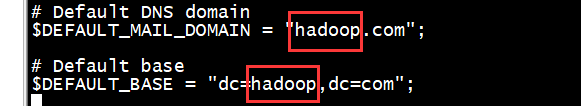
./migrate_passwd.pl /etc/passwd passwd.ldif
mv passwd.ldif /etc/openldap/ (先生成,再移动)
九:把用户导入ldap
cd /etc/openldap/
ldapadd -x -D "uid=ldapadmin,ou=people,dc=hadoop,dc=com" -w 123456 -f passwd.ldif
十:导入用户组到ldap
./migrate_group.pl /etc/group group.ldif
mv group.ldif /etc/openldap/ (先生成,再移动)
ldapadd -x -D "uid=ldapadmin,ou=people,dc=hadoop,dc=com" -w 123456 -f group.ldif
十一:从ldap中移除
删除用户
ldapdelete -x -D "uid=ldapadmin,ou=people,dc=hadoop,dc=com" -w 123456 -h hadoop01 -p 389 "uid=apache,ou=People,dc=hadoop,dc=com"
删除用户组
ldapdelete -x -D "uid=ldapadmin,ou=people,dc=hadoop,dc=com" -w 123456 -h hadoop01 -p 389 "cn=apache,ou=Group,dc=hadoop,dc=com"
