实验五 通讯协议设计-1
- 两人一组
- 基于Socket实现TCP通信,一人实现服务器,一人实现客户端
- 研究OpenSSL算法,测试对称算法中的AES,非对称算法中的RSA,Hash算法中的MD5
- 选用合适的算法,基于混合密码系统实现对TCP通信进行机密性、完整性保护
- 学有余力者,对系统进行安全性分析和改进
TCP通信
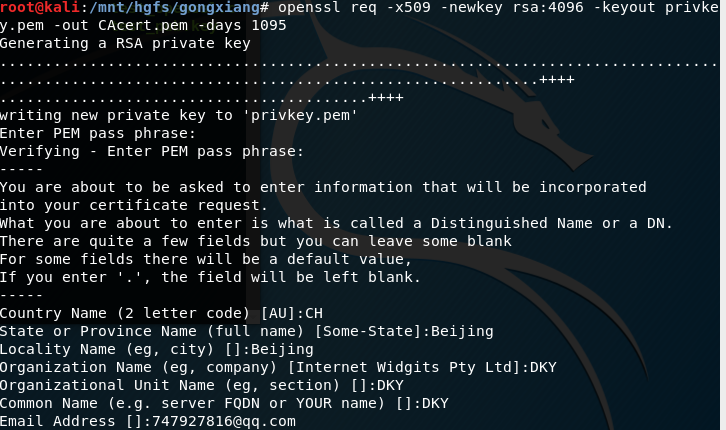
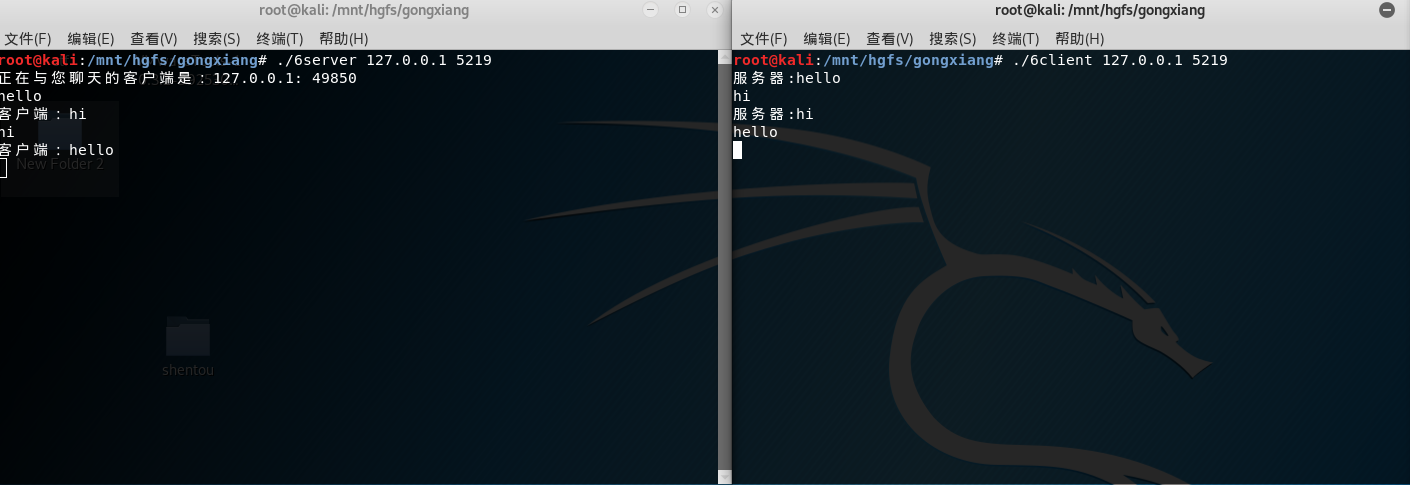
实验截图
实验代码
客户端
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <errno.h>
#include <sys/socket.h>
#include <arpa/inet.h>
#include <netinet/in.h>
#include <sys/types.h>
#include <unistd.h>
#define BUFLEN 10
int main(int argc, char **argv)
{
int sockfd;
struct sockaddr_in s_addr;
socklen_t len;
unsigned int port;
char buf[BUFLEN];
if((sockfd = socket(AF_INET, SOCK_STREAM, 0)) == -1){
perror("socket");
exit(errno);
}
if(argv[2])
port = atoi(argv[2]);
else
port = 5219;
bzero(&s_addr, sizeof(s_addr));
s_addr.sin_family = AF_INET;
s_addr.sin_port = htons(port);
if (inet_aton(argv[1], (struct in_addr *)&s_addr.sin_addr.s_addr) == 0) {
perror(argv[1]);
exit(errno);
}
if(connect(sockfd,(struct sockaddr*)&s_addr,sizeof(struct sockaddr)) == -1){
perror("connect");
exit(errno);
}
while(1){
bzero(buf,BUFLEN);
len = recv(sockfd,buf,BUFLEN,0);
if(len > 0)
printf("服务器:%s\n",buf);
bzero(buf,BUFLEN);
fgets(buf,BUFLEN,stdin);
if(strchr(buf,'\n'))
len = send(sockfd,buf,strlen(buf)-1,0);
else
len = send(sockfd,buf,strlen(buf),0);
}
close(sockfd);
return 0;
}
服务器
#include <stdio.h>
#include <stdlib.h>
#include <string.h>
#include <errno.h>
#include <sys/socket.h>
#include <arpa/inet.h>
#include <netinet/in.h>
#include <sys/types.h>
#include <unistd.h>
#define BUFLEN 10
int main(int argc, char **argv)
{
int sockfd, newfd;
struct sockaddr_in s_addr, c_addr;
char buf[BUFLEN];
socklen_t len;
unsigned int port, listnum;
if((sockfd = socket(AF_INET, SOCK_STREAM, 0)) == -1)
{
perror("socket");
exit(errno);
}
if(argv[2])
port = atoi(argv[2]);
else
port = 4567;
if(argv[3])
listnum = atoi(argv[3]);
else
listnum = 3;
bzero(&s_addr, sizeof(s_addr));
s_addr.sin_family = AF_INET;
s_addr.sin_port = htons(port);
if(argv[1])
s_addr.sin_addr.s_addr = inet_addr(argv[1]);
else
s_addr.sin_addr.s_addr = INADDR_ANY;
if((bind(sockfd, (struct sockaddr*) &s_addr,sizeof(struct sockaddr))) == -1)
{
perror("bind");
exit(errno);
}
if(listen(sockfd,listnum) == -1)
{
perror("listen");
exit(errno);
}
while(1)
{
len = sizeof(struct sockaddr);
if((newfd = accept(sockfd,(struct sockaddr*) &c_addr, &len)) == -1)
{
perror("accept");
exit(errno);
}
else
printf("正在与您聊天的客户端是:%s: %d\n",inet_ntoa(c_addr.sin_addr),ntohs(c_addr.sin_port));
while(1)
{
bzero(buf,BUFLEN);
fgets(buf,BUFLEN,stdin);
if(strchr(buf,'\n'))
len = send(newfd,buf,strlen(buf)-1,0);
else
len = send(newfd,buf,strlen(buf),0);
bzero(buf,BUFLEN);
len = recv(newfd,buf,BUFLEN,0);
if(len > 0)
printf("客户端:%s\n",buf);
}
close(newfd);
bzero(buf, BUFLEN);
fgets(buf,BUFLEN, stdin);
if(!strncasecmp(buf,"y",1))
{
printf("server 退出!\n");
break;
}
}
close(sockfd);
return 0;
}
OpenSSL算法
AES
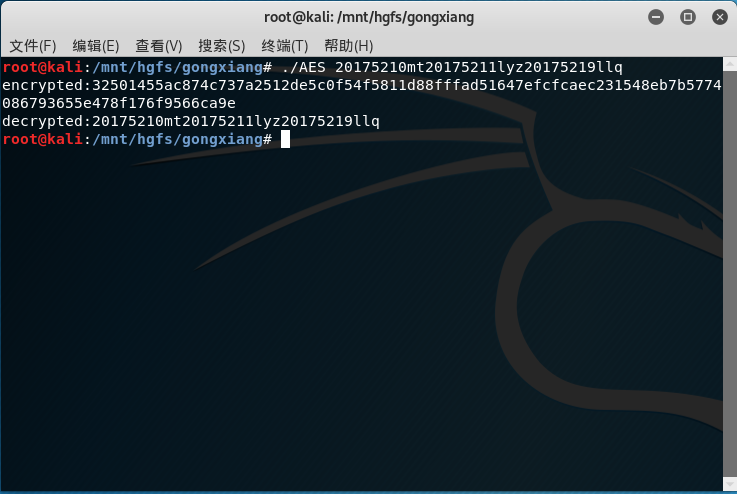
实验截图
实验代码
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <openssl/aes.h>
int main(int argc, char** argv) {
AES_KEY aes;
unsigned char key[AES_BLOCK_SIZE];
unsigned char iv[AES_BLOCK_SIZE];
unsigned char* input_string;
unsigned char* encrypt_string;
unsigned char* decrypt_string;
unsigned int len;
unsigned int i;
if (argc != 2) {
fprintf(stderr, "%s <plain text>\n", argv[0]);
exit(-1);
}
len = 0;
if ((strlen(argv[1]) + 1) % AES_BLOCK_SIZE == 0) {
len = strlen(argv[1]) + 1;
} else {
len = ((strlen(argv[1]) + 1) / AES_BLOCK_SIZE + 1) * AES_BLOCK_SIZE;
}
input_string = (unsigned char*)calloc(len, sizeof(unsigned char));
if (input_string == NULL) {
fprintf(stderr, "Unable to allocate memory for input_string\n");
exit(-1);
}
strncpy((char*)input_string, argv[1], strlen(argv[1]));
for (i=0; i<16; ++i) {
key[i] = 32 + i;
}
for (i=0; i<AES_BLOCK_SIZE; ++i) {
iv[i] = 0;
}
if (AES_set_encrypt_key(key, 128, &aes) < 0) {
fprintf(stderr, "Unable to set encryption key in AES\n");
exit(-1);
}
// alloc encrypt_string
encrypt_string = (unsigned char*)calloc(len, sizeof(unsigned char));
if (encrypt_string == NULL) {
fprintf(stderr, "Unable to allocate memory for encrypt_string\n");
exit(-1);
}
AES_cbc_encrypt(input_string, encrypt_string, len, &aes, iv, AES_ENCRYPT);
decrypt_string = (unsigned char*)calloc(len, sizeof(unsigned char));
if (decrypt_string == NULL) {
fprintf(stderr, "Unable to allocate memory for decrypt_string\n");
exit(-1);
}
for (i=0; i<AES_BLOCK_SIZE; ++i) {
iv[i] = 0;
}
if (AES_set_decrypt_key(key, 128, &aes) < 0) {
fprintf(stderr, "Unable to set decryption key in AES\n");
exit(-1);
}
AES_cbc_encrypt(encrypt_string, decrypt_string, len, &aes, iv, AES_DECRYPT);
printf("encrypted:");
for (i=0; i<len; ++i) {
printf("%x%x", (encrypt_string[i] >> 4) & 0xf, encrypt_string[i] & 0xf);
}
printf("\n");
printf("decrypted:%s\n", decrypt_string);
return 0;
}
RSA
实验截图

实验代码
#include<stdio.h>
#include<stdlib.h>
#include<string.h>
#include<openssl/rsa.h>
#include<openssl/pem.h>
#include<openssl/err.h>
#define OPENSSLKEY "test.key"
#define PUBLICKEY "test_pub.key"
#define BUFFSIZE 1024
char* my_encrypt(char *str,char *path_key);
char* my_decrypt(char *str,char *path_key);
int main(void){
char *source="20175210mt20175211lyz2017519llq";
char *ptr_en,*ptr_de;
printf("test:%s\n",source);
ptr_en=my_encrypt(source,PUBLICKEY);
printf("encrypt:%s\n",ptr_en);
ptr_de=my_decrypt(ptr_en,OPENSSLKEY);
printf("decrypt:%s\n",ptr_de);
if(ptr_en!=NULL){
free(ptr_en);
}
if(ptr_de!=NULL){
free(ptr_de);
}
return 0;
}
char *my_encrypt(char *str,char *path_key){
char *p_en;
RSA *p_rsa;
FILE *file;
int flen,rsa_len;
if((file=fopen(path_key,"r"))==NULL){
perror("open key file error");
return NULL;
}
if((p_rsa=PEM_read_RSA_PUBKEY(file,NULL,NULL,NULL))==NULL){
ERR_print_errors_fp(stdout);
return NULL;
}
flen=strlen(str);
rsa_len=RSA_size(p_rsa);
p_en=(unsigned char *)malloc(rsa_len+1);
memset(p_en,0,rsa_len+1);
if(RSA_public_encrypt(rsa_len,(unsigned char *)str,(unsigned char*)p_en,p_rsa,RSA_NO_PADDING)<0){
return NULL;
}
RSA_free(p_rsa);
fclose(file);
return p_en;
}
char *my_decrypt(char *str,char *path_key){
char *p_de;
RSA *p_rsa;
FILE *file;
int rsa_len;
if((file=fopen(path_key,"r"))==NULL){
perror("open key file error");
return NULL;
}
if((p_rsa=PEM_read_RSAPrivateKey(file,NULL,NULL,NULL))==NULL){
ERR_print_errors_fp(stdout);
return NULL;
}
rsa_len=RSA_size(p_rsa);
p_de=(unsigned char *)malloc(rsa_len+1);
memset(p_de,0,rsa_len+1);
if(RSA_private_decrypt(rsa_len,(unsigned char *)str,(unsigned char*)p_de,p_rsa,RSA_NO_PADDING)<0){
return NULL;
}
RSA_free(p_rsa);
fclose(file);
return p_de;
}
MD5
实验截图

实验代码
#include <stdio.h>
#include <string.h>
#include <stdlib.h>
#include <openssl/md5.h>
int main(int argc, char** argv) {
MD5_CTX hash_ctx;
char input_string[128];
unsigned char hash_ret[16];
int i;
if (argc != 2) {
fprintf(stderr, "%s <input string>\n", argv[0]);
exit(-1);
}
snprintf(input_string, sizeof(input_string), "%s\n", argv[1]);
MD5_Init(&hash_ctx);
MD5_Update(&hash_ctx, input_string, strlen(input_string));
MD5_Final(hash_ret, &hash_ctx);
printf("Output: ");
for (i=0; i<32; ++i) {
if (i % 2 == 0) {
printf("%x", (hash_ret[i/2] >> 4) & 0xf);
} else {
printf("%x", (hash_ret[i/2]) & 0xf);
}
}
printf("\n");
return 0;
}
实验五 通讯协议设计-2
- 在Ubuntu中实现对实验二中的“wc服务器”通过混合密码系统进行防护
- 提交测试截图
实验截图

实验代码
客户端
#include <stdio.h>
#include <string.h>
#include <errno.h>
#include <sys/socket.h>
#include <resolv.h>
#include <stdlib.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <unistd.h>
#include <openssl/ssl.h>
#include <openssl/err.h>
#include <openssl/evp.h>
#define MAXBUF 1024
void ShowCerts(SSL * ssl)
{
X509 *cert;
char *line;
cert = SSL_get_peer_certificate(ssl);
if (cert != NULL) {
printf("数字证书信息:\n");
line = X509_NAME_oneline(X509_get_subject_name(cert), 0, 0);
printf("证书: %s\n", line);
free(line);
line = X509_NAME_oneline(X509_get_issuer_name(cert), 0, 0);
printf("颁发者: %s\n", line);
free(line);
X509_free(cert);
} else
printf("无证书信息!\n");
}
int main(int argc, char **argv)
{
int sockfd, len;
struct sockaddr_in dest;
char buffer[MAXBUF + 1];
SSL_CTX *ctx;
SSL *ssl;
SSL_library_init();
OpenSSL_add_all_algorithms();
SSL_load_error_strings();
ctx = SSL_CTX_new(SSLv23_client_method());
if (ctx == NULL) {
ERR_print_errors_fp(stdout);
exit(1);
}
if ((sockfd = socket(AF_INET, SOCK_STREAM, 0)) < 0) {
perror("Socket");
exit(errno);
}
printf("socket created\n");
bzero(&dest, sizeof(dest));
dest.sin_family = AF_INET;
dest.sin_port = htons(atoi(argv[2]));
if (inet_aton(argv[1], (struct in_addr *) &dest.sin_addr.s_addr) == 0) {
perror(argv[1]);
exit(errno);
}
printf("address created\n");
if (connect(sockfd, (struct sockaddr *) &dest, sizeof(dest)) != 0) {
perror("Connect ");
exit(errno);
}
printf("server connected\n");
ssl = SSL_new(ctx);
SSL_set_fd(ssl, sockfd);
if (SSL_connect(ssl) == -1)
ERR_print_errors_fp(stderr);
else {
printf("Connected with %s encryption\n", SSL_get_cipher(ssl));
ShowCerts(ssl);
}
bzero(buffer, MAXBUF + 1);
len = SSL_read(ssl, buffer, MAXBUF);
if (len > 0)
printf("服务器:%s\n",buffer);
bzero(buffer, MAXBUF + 1);
strcpy(buffer, "hi");
len = SSL_write(ssl, buffer, strlen(buffer));
SSL_shutdown(ssl);
SSL_free(ssl);
close(sockfd);
SSL_CTX_free(ctx);
return 0;
}
服务器
#include <stdio.h>
#include <stdlib.h>
#include <errno.h>
#include <string.h>
#include <sys/types.h>
#include <netinet/in.h>
#include <sys/socket.h>
#include <sys/wait.h>
#include <unistd.h>
#include <arpa/inet.h>
#include <openssl/ssl.h>
#include <openssl/err.h>
#include <openssl/evp.h>
#define MAXBUF 1024
int main(int argc, char **argv)
{
int sockfd, new_fd;
socklen_t len;
struct sockaddr_in my_addr, their_addr;
unsigned int myport, lisnum;
char buf[MAXBUF + 1];
SSL_CTX *ctx;
if (argv[1])
myport = atoi(argv[1]);
if (argv[2])
lisnum = atoi(argv[2]);
else
lisnum = 2;
SSL_library_init();
OpenSSL_add_all_algorithms();
SSL_load_error_strings();
ctx = SSL_CTX_new(SSLv23_server_method());
if (ctx == NULL) {
ERR_print_errors_fp(stdout);
exit(1);
}
if (SSL_CTX_use_certificate_file(ctx, argv[3], SSL_FILETYPE_PEM) <= 0) {
ERR_print_errors_fp(stdout);
exit(1);
}
if (SSL_CTX_use_PrivateKey_file(ctx, argv[4], SSL_FILETYPE_PEM) <= 0){
ERR_print_errors_fp(stdout);
exit(1);
}
if (!SSL_CTX_check_private_key(ctx)) {
ERR_print_errors_fp(stdout);
exit(1);
}
if ((sockfd = socket(PF_INET, SOCK_STREAM, 0)) == -1) {
perror("socket");
exit(1);
}
bzero(&my_addr, sizeof(my_addr));
my_addr.sin_family = PF_INET;
my_addr.sin_port = htons(myport);
my_addr.sin_addr.s_addr = INADDR_ANY;
if (bind(sockfd, (struct sockaddr *) &my_addr, sizeof(struct sockaddr))
== -1) {
perror("bind");
exit(1);
} ;
if (listen(sockfd, lisnum) == -1) {
perror("listen");
exit(1);
} else
while (1) {
SSL *ssl;
len = sizeof(struct sockaddr);
if ((new_fd =accept(sockfd, (struct sockaddr *) &their_addr,&len)) == -1) {
perror("accept");
exit(errno);
}
ssl = SSL_new(ctx);
SSL_set_fd(ssl, new_fd);
if (SSL_accept(ssl) == -1) {
perror("accept");
close(new_fd);
break;
}
bzero(buf, MAXBUF + 1);
strcpy(buf, "hello");
len = SSL_write(ssl, buf, strlen(buf));
bzero(buf, MAXBUF + 1);
len = SSL_read(ssl, buf, MAXBUF);
if (len > 0)
printf("客户端:%s\n",buf);
SSL_shutdown(ssl);
SSL_free(ssl);
close(new_fd);
}
close(sockfd);
SSL_CTX_free(ctx);
return 0;
}
遇到的问题
证书的key过短
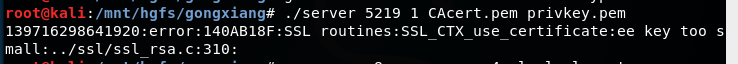
用命令自定义一个较长的key并重新生成证书