先上加密脚本:
import org.apache.commons.codec.binary.Base64; import java.io.ByteArrayOutputStream; import java.security.Key; import java.security.KeyFactory; import java.security.KeyPair; import java.security.KeyPairGenerator; import java.security.PrivateKey; import java.security.PublicKey; import java.security.Signature; import java.security.interfaces.RSAPrivateKey; import java.security.interfaces.RSAPublicKey; import java.security.spec.PKCS8EncodedKeySpec; import java.security.spec.X509EncodedKeySpec; import java.util.HashMap; import java.util.Map; import javax.crypto.Cipher; String RSA_PUB_KEY="你的公钥";//去掉首尾 String KEY_ALGORITHM = "RSA"; String SIGNATURE_ALGORITHM = "MD5withRSA"; int MAX_ENCRYPT_BLOCK = 117; int MAX_DECRYPT_BLOCK = 128; public static byte[] decryptByPublicKey(byte[] encryptedData, String publicKey) throws Exception { byte[] keyBytes = Base64.decodeBase64(publicKey); X509EncodedKeySpec x509KeySpec = new X509EncodedKeySpec(keyBytes); KeyFactory keyFactory = KeyFactory.getInstance(KEY_ALGORITHM); Key publicK = keyFactory.generatePublic(x509KeySpec); Cipher cipher = Cipher.getInstance(keyFactory.getAlgorithm()); cipher.init(Cipher.DECRYPT_MODE, publicK); int inputLen = encryptedData.length; ByteArrayOutputStream out = new ByteArrayOutputStream(); int offSet = 0; byte[] cache; int i = 0; // 对数据分段解密 while (inputLen - offSet > 0) { if (inputLen - offSet > MAX_DECRYPT_BLOCK) { cache = cipher.doFinal(encryptedData, offSet, MAX_DECRYPT_BLOCK); } else { cache = cipher.doFinal(encryptedData, offSet, inputLen - offSet); } out.write(cache, 0, cache.length); i++; offSet = i * MAX_DECRYPT_BLOCK; } byte[] decryptedData = out.toByteArray(); out.close(); return decryptedData; } public static byte[] encryptByPublicKey(byte[] data, String publicKey) throws Exception { byte[] keyBytes = Base64.decodeBase64(publicKey); X509EncodedKeySpec x509KeySpec = new X509EncodedKeySpec(keyBytes); KeyFactory keyFactory = KeyFactory.getInstance("RSA"); Key publicK = keyFactory.generatePublic(x509KeySpec); // 对数据加密 Cipher cipher = Cipher.getInstance("RSA"); cipher.init(Cipher.ENCRYPT_MODE, publicK); int inputLen = data.length; ByteArrayOutputStream out = new ByteArrayOutputStream(); int offSet = 0; byte[] cache; int i = 0; // 对数据分段加密 while (inputLen - offSet > 0) { if (inputLen - offSet > MAX_ENCRYPT_BLOCK) { cache = cipher.doFinal(data, offSet, MAX_ENCRYPT_BLOCK); } else { cache = cipher.doFinal(data, offSet, inputLen - offSet); } out.write(cache, 0, cache.length); i++; offSet = i * MAX_ENCRYPT_BLOCK; } byte[] encryptedData = out.toByteArray(); out.close(); return encryptedData; } String str=vars.get("body"); String result =""; try { result = Base64.encodeBase64String(encryptByPublicKey(str.getBytes(), RSA_PUB_KEY)); System.out.println(result); } catch (Exception e) { // TODO Auto-generated catch block e.printStackTrace(); } print(result); vars.put("sign",result); vars.put("RSA_PUB_KEY",RSA_PUB_KEY); log.info("加密串=",result); log.info("加密body=",str); return result;
1.因为是加密后的参数放到请求体中,所以我在另外一个beanshell定义了一个json格式的字符串,然后这就造成了一个问题:字符串带转义符,jmeter对带转义符的字符串用$来引用会直接报错!!!!解决办法是改用vars.get(“body”)来获取公共变量
2.加密后的字符串直接塞进请求体里了
3.返回的报文是私钥加密,公钥解密的密文,这里我选择了用后置处理器来解密:
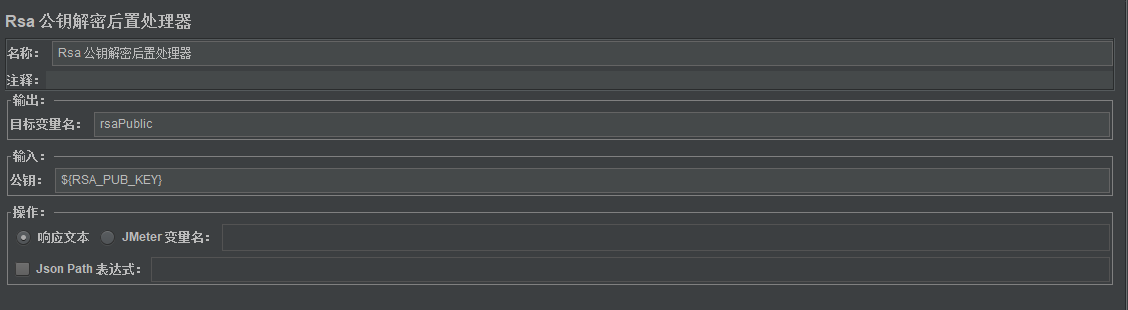
输出:将解密结果输出的参数命名
输入:导入rsa公钥,这在上面的脚本已经提前定义好
操作:要是解密的是响应的json,则勾选响应文本-jsonpath表达式
要是返回的直接是加密的密文,则只勾选响应文本,不勾选jsonpath,这里我是使用了这种方法
针对其他变量解密,勾选变量名并输入即可
所用jmeter的版本:5.1.1 r1855173
下载地址:
链接:https://pan.baidu.com/s/1lpvmNd7jd5v7vG3IGfum2A 提取码:q8ym
参考链接:https://www.cnblogs.com/artoftest/p/7298929.html
https://blog.csdn.net/q13554515812/article/details/99298387