部署环境
OS:CentOS Linux release 7.6.1810 (Core)
kernel: 3.10.0-957.21.3.el7.x86_64
1 台master 2台node
环境准备(三台机器都做以下操作)
关闭防火墙:
systemctl stop firewalld
systemctl disable firewalld
关闭selinux:
sed -i 's/enforcing/disabled/' /etc/selinux/config
setenforce 0
关闭swap:
swapoff -a # 临时
vim /etc/fstab # 永久
添加主机名与IP对应关系:
cat /etc/hosts
192.168.214.92 k8s-master
192.168.214.97 k8s-node1
192.168.214.98 k8s-node2
下载阿里云源
Centos_repo
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
kubernetes_repo
配置kubenetes yum源
cat <<EOF > /etc/yum.repos.d/kubernetes.repo
[kubernetes]
name=Kubernetes
baseurl=https://mirrors.aliyun.com/kubernetes/yum/repos/kubernetes-el7-x86_64/
enabled=1
gpgcheck=1
repo_gpgcheck=1
gpgkey=https://mirrors.aliyun.com/kubernetes/yum/doc/yum-key.gpg https://mirrors.aliyun.com/kubernetes/yum/doc/rpm-package-key.gpg
EOF
所有设备均执行如下命令
安装docker和kube组件
yum install -y kubelet kubeadm kubectl docker-ce
systemctl enable docker kubelet
docker架构关系图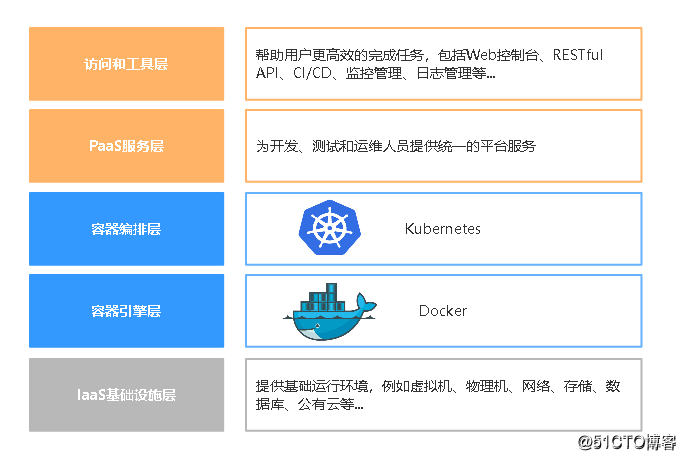
master:
下载所需docker镜像
这里下载v1.15.0版本
docker pull mirrorgooglecontainers/kube-apiserver-amd64:v1.15.0
docker pull mirrorgooglecontainers/kube-controller-manager-amd64:v1.15.0
docker pull mirrorgooglecontainers/kube-scheduler-amd64:v1.10.0
docker pull mirrorgooglecontainers/kube-proxy-amd64:v1.15.0
docker pull mirrorgooglecontainers/pause:3.1
docker pull mirrorgooglecontainers/etcd:3.3.10
docker pull coredns/coredns:1.3.1
镜像打标
docker tag mirrorgooglecontainers/kube-apiserver-amd64:v1.15.0 k8s.gcr.io/kube-apiserver:v1.15.0
docker tag mirrorgooglecontainers/kube-scheduler:v1.15.0 k8s.gcr.io/kube-scheduler:v1.15.0 docker tag mirrorgooglecontainers/kube-controller-manager:v1.15.0 k8s.gcr.io/kube-controller-manager:v1.15.0
docker tag mirrorgooglecontainers/etcd:v1.15.0 k8s.gcr.io/etcd:v1.15.0
docker tag mirrorgooglecontainers/etcd:3.3.10 k8s.gcr.io/etcd:3.3.10
docker tag mirrorgooglecontainers/pause:3.1 k8s.gcr.io/pause:3.1
docker tag coredns/coredns:1.3.1 k8s.gcr.io/coredns:1.3.1
初始化master
docker 服务器开启
[root@master ~]# systemctl start docker
忽略swap报错
[root@master ~]# vim /etc/sysconfig/kubelet
KUBELET_EXTRA_ARGS="--fail-swap-on=false"
安装
kubeadm init --kubernetes-version=v1.15.0 --ignore-preflight-errors=Swap --ignore-preflight-errors=Numcpu --pod-network-cidr 10.244.0.0/16
#10.244.0.0/16为pod网络
初始化集群出错时,需要所有节点清掉这些数据.可用以下命令
kubeadm reset
systemctl stop kubelet
docker rm -f -v $(docker ps -a -q)
rm -rf /etc/kubernetes
rm -rf /var/lib/etcd
rm -rf /var/lib/kubelet
rm -rf $HOME/.kube/config
iptables -F && iptables -t nat -F && iptables -t mangle -F && iptables -X
yum reinstall -y kubelet
systemctl daemon-reload
systemctl restart docker
kubectl 客户端用户配置文件配置
mkdir -p $HOME/.kube
cp -i /etc/kubernetes/admin.conf $HOME/.kube/config
chown $(id -u):$(id -g) $HOME/.kube/config
记录安装后输出,供后面添加work-node使用
kubeadm join 192.168.214.92:6443 --token cmpc1v.bxbssutot9uwn3go \
--discovery-token-ca-cert-hash sha256:a6206427396768bf14a9bb85bf3d726ad5441ccd646a3949ece417b1607a2c2b
安装flannel网络
kubectl apply -f https://raw.githubusercontent.com/coreos/flannel/master/Documentation/kube-flannel.yml
加入master
[root@node1 ~]# kubeadm join 192.168.214.92:6443 --token cmpc1v.bxbssutot9uwn3go \
--discovery-token-ca-cert-hash sha256:a6206427396768bf14a9bb85bf3d726ad5441ccd646a3949ece417b1607a2c2b
[root@node2 ~]# kubeadm join 192.168.214.92:6443 --token cmpc1v.bxbssutot9uwn3go \
--discovery-token-ca-cert-hash sha256:a6206427396768bf14a9bb85bf3d726ad5441ccd646a3949ece417b1607a2c2b
加入master节点初始化成功的token
master获取token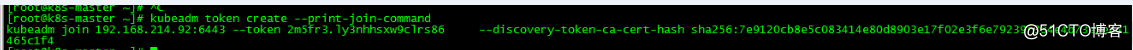
kubectl get nodes 查看集群状态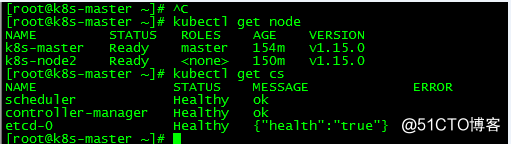
搭建dashboard
vi kubernetes-dashboard.yaml
Copyright 2017 The Kubernetes Authors.
Licensed under the Apache License, Version 2.0 (the "License");
you may not use this file except in compliance with the License.
You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
Configuration to deploy release version of the Dashboard UI compatible with
Kubernetes 1.8.
Example usage: kubectl create -f <this_file>
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: admin
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
roleRef:
kind: ClusterRole
name: cluster-admin
apiGroup: rbac.authorization.k8s.io
subjects:
kind: ServiceAccount
name: admin
namespace: kube-system
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin
namespace: kube-system
labels:
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
--
------------------- Dashboard Secret ------------------- #
apiVersion: v1
kind: Secret
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard-certs
namespace: kube-system
type: Opaque
--
------------------- Dashboard Service Account ------------------- #
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
--
------------------- Dashboard Role & Role Binding ------------------- #
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
rules:
Allow Dashboard to create 'kubernetes-dashboard-key-holder' secret.
apiGroups: [""]
resources: ["secrets"]
verbs: ["create"]
Allow Dashboard to create 'kubernetes-dashboard-settings' config map.
apiGroups: [""]
resources: ["configmaps"]
verbs: ["create"]
Allow Dashboard to get, update and delete Dashboard exclusive secrets.
apiGroups: [""]
resources: ["secrets"]
resourceNames: ["kubernetes-dashboard-key-holder", "kubernetes-dashboard-certs"]
verbs: ["get", "update", "delete"]
Allow Dashboard to get and update 'kubernetes-dashboard-settings' config map.
apiGroups: [""]
resources: ["configmaps"]
resourceNames: ["kubernetes-dashboard-settings"]
verbs: ["get", "update"]
Allow Dashboard to get metrics from heapster.
apiGroups: [""]
resources: ["services"]
resourceNames: ["heapster"]
verbs: ["proxy"]
apiGroups: [""]
resources: ["services/proxy"]
resourceNames: ["heapster", "http:heapster:", "https:heapster:"]
verbs: ["get"]
--
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: kubernetes-dashboard-minimal
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: kubernetes-dashboard-minimal
subjects:
kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
--
------------------- Dashboard Deployment ------------------- #
kind: Deployment
apiVersion: apps/v1beta2
metadata:
labels:
k8s-app: kubernetes-dashboard
name: kubernetes-dashboard
namespace: kube-system
spec:
replicas: 1
revisionHistoryLimit: 10
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
spec:
containers:
name: kubernetes-dashboard
image: harbor.shinezone.com/shinezonetest/kubernetes-dashboard-amd64:v1.8.3
image: lizhenliang/kubernetes-dashboard-amd64:v1.10.1
ports:
containerPort: 8443
protocol: TCP
args:
--auto-generate-certificates
Uncomment the following line to manually specify Kubernetes API server Host
If not specified, Dashboard will attempt to auto discover the API server and connect
to it. Uncomment only if the default does not work.
- --apiserver-host=http://my-address:port
- --authentication-mode=basic
volumeMounts:
name: kubernetes-dashboard-certs
mountPath: /certs
Create on-disk volume to store exec logs
mountPath: /tmp
name: tmp-volume
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
name: kubernetes-dashboard-certs
secret:
secretName: kubernetes-dashboard-certs
name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard
Comment the following tolerations if Dashboard must not be deployed on master
tolerations:
key: node-role.kubernetes.io/master
effect: NoSchedule
--
------------------- Dashboard Service ------------------- #
kind: Service
apiVersion: v1
metadata:
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard
namespace: kube-system
spec:
type: NodePort
ports:
port: 443
targetPort: 8443
nodePort: 30000
selector:
k8s-app: kubernetes-dashboard
--
apiVersion: v1
kind: ServiceAccount
metadata:
name: admin-user
namespace: kube-system
--
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: admin-user
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
kind: ServiceAccount
name: admin-user
namespace: kube-system
kubectl create -f kubernetes-dashboard.yaml
kubectl get pod -n kube-system -o wide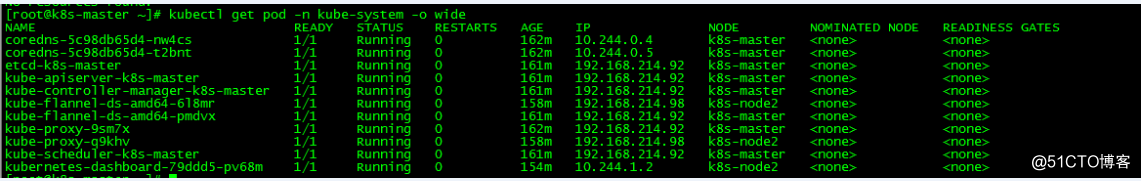
所有的pod状态为running即可
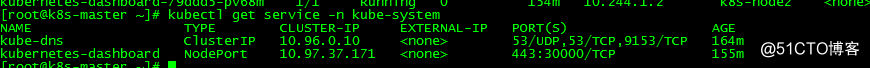
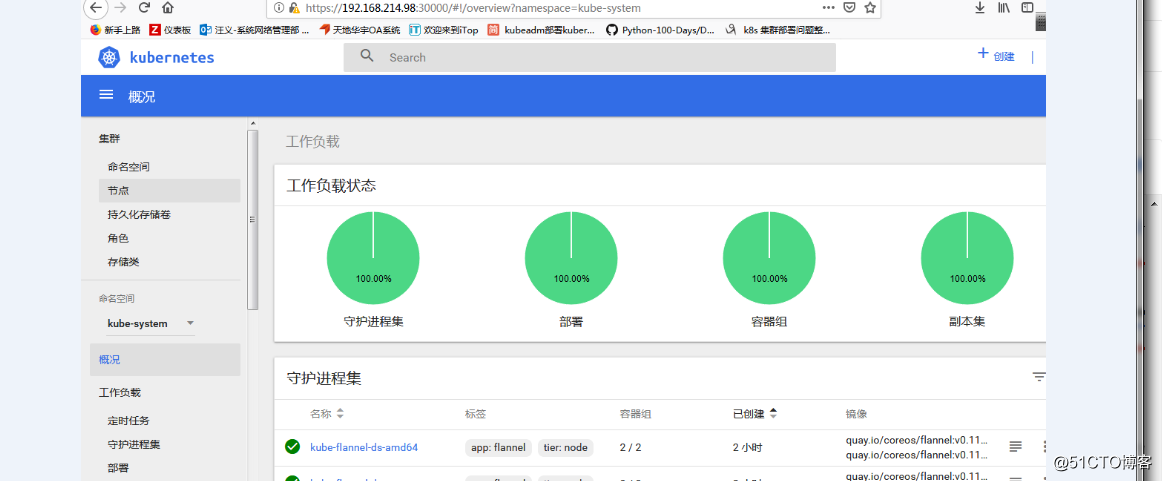
浏览器访问
https://ip:port
例如我的是:https://192.168.214.92:30000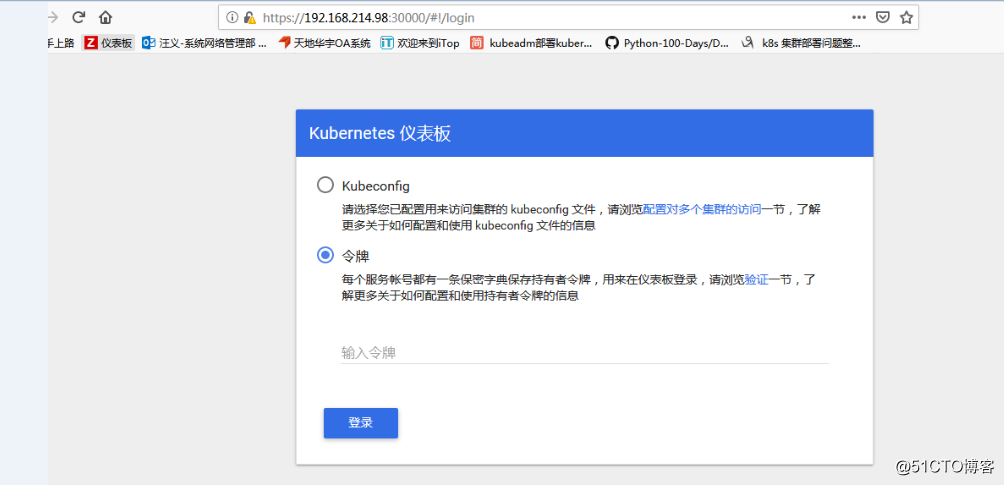
创建admin权限账号
kubectl create serviceaccount dashboard-admin -n kube-system
kubectl create clusterrolebinding dashboard-admin --clusterrole=cluster-admin --serviceaccount=kube-system:dashboard-admin
获取token在登陆
kubectl describe secrets -n kube-system $(kubectl -n kube-system get secret | awk '/dashboard-admin/{print $1}')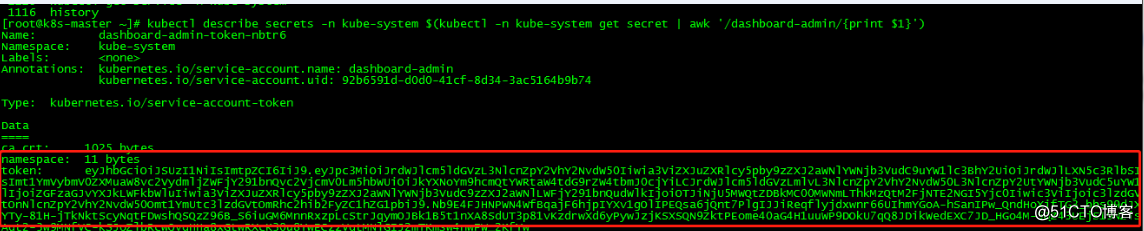
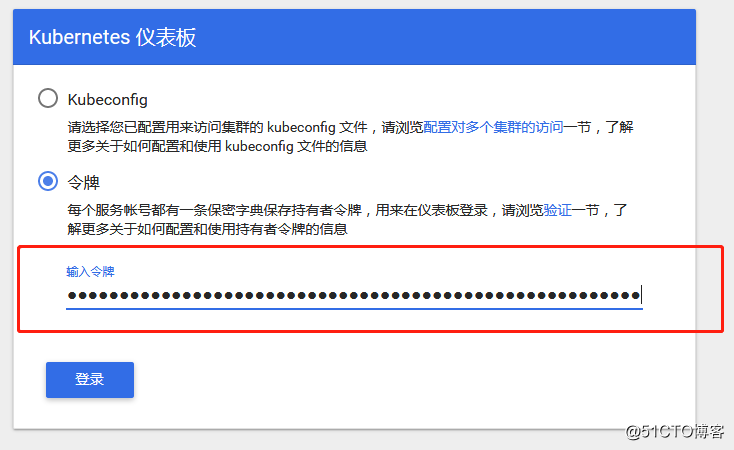
大功告成