我们前面讲过了saltstack的c/s,ssh等推送方式,其实我们还可以使用api推送的方式来馆及节点,下面我们就来部署一下api接口的saltstack推送
1.之前因为使用ssh关掉了minion,我们重新先开启
[root@server2 minion]# systemctl start salt-minion
[root@server3 minion]# systemctl start salt-minion
2.配置签名证书
由于现在大多数的api接口使用https的方式,那么我们就来创建证书
[root@server1 salt]# cd /etc/pki/tls/private/
[root@server1 private]# openssl genrsa 1024 我们使用rsa加密,加密位数为1024
Generating RSA private key, 1024 bit long modulus
..............++++++
........................++++++
e is 65537 (0x10001)
-----BEGIN RSA PRIVATE KEY-----
MIICWwIBAAKBgQCrpYOCQdtD0AX7FBdBQxpWJjcv++XcD/GSwJAgPZRs+DLsyTyM
YWKyxVroGte3X2vD2XZfoh9tEOK80b/xC6bPaBCGIuSWu6YYp74TgRzCOTP8Fav9
rh8KuO+GR7czFkf/2YHXRNB4b0PBJkQKB9yBiLFNniR20yurGln4G/5gxwIDAQAB
AoGAS0/E4tsobJmSdja7eVwK6y+7WSdqFGM+eEhbNHowbJt+JJyrH2D/YDbtixdz
/LY2X2lD4fQNW9pj0bsqP4YAOxqIz1nB+TaYDssEL9tAOol0n5V8A9sHmf0Y1rBP
Cd+WISMKbpoddazSQq4GBw7s4mP2FBhJs3dspPp3T7qb4NECQQDW7nEe1QDu7rxP
kwLnovpqfn4qshIv+Yfzp09p24rA+MFkY2ZYKzwgktbD9NDGHqinnC5QeGBJWWBF
jYinZWdJAkEAzHHBF9A01ZAvWVf0Mhh70yr2xb1J7uoKOrq3ExTWrz7fyuInj3oj
lPGSd2KPT8psjSSKmwfMR2xjJNB5uuE3jwJAePFnuh/GDK1OTcC967ZsDyzqtf/J
+DED7XmCWGDvrTLNMD42wvphNTsrmszSBgoOgXKDJUj3dY7Te4/vC7Ml8QJAcDAA
EMw9IfBUO0fLhe3vjQpnjkz4FDWz1VR+f+cQg+wRrGh74vzYJ7SEdiTMlbFz7ePe
d4JI8+yjXyFTm1xZOwJAHheLXSk5c7DcW/VKiWe03yU9z+CMHfSEKL2qLdg2wtZi
SFEi3ioaS6NZYCHXwUGeHnU5MmOahMve3/yUZg0hUA==
-----END RSA PRIVATE KEY-----
[root@server1 private]# openssl genrsa 1024 > localhost.key
[root@server1 private]# ls
localhost.key
[root@server1 private]# cd ..
[root@server1 tls]# cd certs/
[root@server1 certs]# ls
ca-bundle.crt ca-bundle.trust.crt make-dummy-cert Makefile renew-dummy-cert
[root@server1 certs]# make testcert 因为这里有makefile的脚本文件,所以我们直接使用它来创建证书

3.编辑api.conf和auth.conf配置文件
[root@server1 certs]# cd /etc/salt/master.d/
[root@server1 master.d]# ls
[root@server1 master.d]# vim api.conf
[root@server1 master.d]# cat api.conf
rest_cherrypy:
port: 8000
ssl_crt: /etc/pki/tls/certs/localhost.crt
ssl_key: /etc/pki/tls/private/localhost.key
[root@server1 master.d]# vim auth.conf
[root@server1 master.d]# cat auth.conf
external_auth:
pam:
saltapi:
- .*
- '@wheel'
- '@runner'
- '@jobs'
4.创建一个saltapi用户(一会儿测试使用)
[root@server1 master.d]# useradd saltapi
[root@server1 master.d]# passwd saltapi
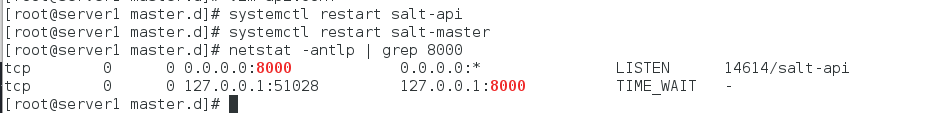
5.打开salt-api,重起master,查看8000端口是否开启
[root@server1 master.d]# systemctl restart salt-api
[root@server1 master.d]# systemctl restart salt-master
[root@server1 master.d]# netstat -antlp | grep 8000
tcp 0 0 0.0.0.0:8000 0.0.0.0:* LISTEN 14614/salt-api
tcp 0 0 127.0.0.1:51028 127.0.0.1:8000 TIME_WAIT -
6.在物理机进行测试
1.验证服务并获取token
[root@foundation66 ~]# curl -sSk https://172.25.66.1:8000/login -H 'Accept: application/x-yaml' -d username=saltapi -d password=redhat -d eauth=pam
return:
- eauth: pam
expire: 1561022083.921096
perms:
- .*
- '@wheel'
- '@runner'
- '@jobs'
start: 1560978883.921095
token: 74dd0818ddf78811b3840444d8b04785dc121e82
user: saltapi
2.利用token号进行测试
[root@foundation66 ~]# curl -sSk https://172.25.66.1:8000 -H 'Accept: application/x-yaml' -H 'X-Auth- Token: 74dd0818ddf78811b3840444d8b04785dc121e82' -d client=local -d tgt='*' -d fun=test.ping
return:
- server2: true
server3: true
3.配置python脚本测试能否成功
[root@foundation66 ~]# vim saltapi.py
# -*- coding: utf-8 -*-
import urllib2,urllib
import time
try:
import json
except ImportError:
import simplejson as json
class SaltAPI(object):
__token_id = ''
def __init__(self,url,username,password):
self.__url = url.rstrip('/')
self.__user = username
self.__password = password
def token_id(self):
''' user login and get token id '''
params = {'eauth': 'pam', 'username': self.__user, 'password': self.__password}
encode = urllib.urlencode(params)
obj = urllib.unquote(encode)
content = self.postRequest(obj,prefix='/login')
try:
self.__token_id = content['return'][0]['token']
except KeyError:
raise KeyError
def postRequest(self,obj,prefix='/'):
url = self.__url + prefix
headers = {'X-Auth-Token' : self.__token_id}
req = urllib2.Request(url, obj, headers)
opener = urllib2.urlopen(req)
content = json.loads(opener.read())
return content
def list_all_key(self):
params = {'client': 'wheel', 'fun': 'key.list_all'}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
minions = content['return'][0]['data']['return']['minions']
minions_pre = content['return'][0]['data']['return']['minions_pre']
return minions,minions_pre
def delete_key(self,node_name):
params = {'client': 'wheel', 'fun': 'key.delete', 'match': node_name}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
ret = content['return'][0]['data']['success']
return ret
def accept_key(self,node_name):
params = {'client': 'wheel', 'fun': 'key.accept', 'match': node_name}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
ret = content['return'][0]['data']['success']
return ret
def remote_noarg_execution(self,tgt,fun):
''' Execute commands without parameters '''
params = {'client': 'local', 'tgt': tgt, 'fun': fun}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
ret = content['return'][0][tgt]
return ret
def remote_execution(self,tgt,fun,arg):
''' Command execution with parameters '''
params = {'client': 'local', 'tgt': tgt, 'fun': fun, 'arg': arg}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
ret = content['return'][0][tgt]
return ret
def target_remote_execution(self,tgt,fun,arg):
''' Use targeting for remote execution '''
params = {'client': 'local', 'tgt': tgt, 'fun': fun, 'arg': arg, 'expr_form': 'nodegroup'}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
jid = content['return'][0]['jid']
return jid
def deploy(self,tgt,arg):
''' Module deployment '''
params = {'client': 'local', 'tgt': tgt, 'fun': 'state.sls', 'arg': arg}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
return content
def async_deploy(self,tgt,arg):
''' Asynchronously send a command to connected minions '''
params = {'client': 'local_async', 'tgt': tgt, 'fun': 'state.sls', 'arg': arg}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
jid = content['return'][0]['jid']
return jid
def target_deploy(self,tgt,arg):
''' Based on the node group forms deployment '''
params = {'client': 'local_async', 'tgt': tgt, 'fun': 'state.sls', 'arg': arg, 'expr_form': 'nodegroup'}
obj = urllib.urlencode(params)
self.token_id()
content = self.postRequest(obj)
jid = content['return'][0]['jid']
return jid
def main():
sapi = SaltAPI(url='https://172.25.66.1:8000',username='saltapi',password='redhat') 设置api接口,用户及用户密码
#sapi.token_id()
print sapi.list_all_key() 列出所有节点
#sapi.delete_key('test-01')
#sapi.accept_key('test-01')
#sapi.deploy('*','httpd.apache')
#print sapi.remote_noarg_execution('test-01','grains.items')
if __name__ == '__main__':
main()
这里的各种python脚本利用api接口的文件再github上有很多,可以自己下载一个,或者直接用我的这个进行测试也可以
[root@foundation66 ~]# python saltapi.py
([u'server2', u'server3'], [])
成功列出节点
修改python文件的主方法继续进行测试
def main():
sapi = SaltAPI(url='https://172.25.66.1:8000',username='saltapi',password='redhat')
#sapi.token_id()
#print sapi.list_all_key()
#sapi.delete_key('test-01')
#sapi.accept_key('test-01')
sapi.deploy('server3','nginx.service') 注意这里使用的deploy我们使用的是我们之前写的部署nginx的sls文件,我们再server3上部署nginx
#print sapi.remote_noarg_execution('test-01','grains.items')
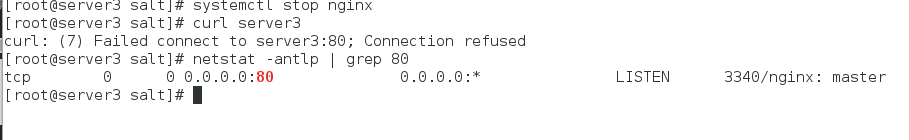
为了消除实验影响,我们关闭server3上的nginx(无论其是否开启)
[root@server3 salt]# systemctl stop nginx
[root@server3 salt]# curl server3
curl: (7) Failed connect to server3:80; Connection refused
测试