2-Apache服务的访问控制
1.开启基本认证(用户密码)
查看Apache文档-->认证
AuthType Basic
AuthName "Restricted Files"
#(下面这一行是可选的)
AuthBasicProvider file
AuthUserFile /usr/local/apache2/passwd/passwords
Require user rbowen
需求1:单个用户访问
1.创建密码文件的命令htpasswd
[root@web-server conf]# which htpasswd
/usr/bin/htpasswd
[root@web-server conf]# rpm -qf /usr/bin/htpasswd
httpd-tools-2.2.15-29.el6.centos.x86_64
[root@web-server conf]# htpasswd --help
Usage:
htpasswd [-cmdpsD] passwordfile username
htpasswd -b[cmdpsD] passwordfile username password
htpasswd -n[mdps] username
htpasswd -nb[mdps] username password
-c Create a new file.
-n Don't update file; display results on stdout.
-m Force MD5 encryption of the password. MD5加密
-d Force CRYPT encryption of the password (default).
-p Do not encrypt the password (plaintext).
-s Force SHA encryption of the password.
-b Use the password from the command line rather than prompting for it.//非交互式
-D Delete the specified user.
On Windows, NetWare and TPF systems the '-m' flag is used by default.
On all other systems, the '-p' flag will probably not work.
2.创建harry(交互设密)和jack(命令行设密)
[root@web-server conf]# htpasswd -cm /etc/httpd/conf/.passfile harry
New password:
Re-type new password:
Adding password for user harry
[root@web-server conf]# cat .passfile
harry:$apr1$yBmJw2lZ$5gOLS4WIffoYYUqbHb8j31
[root@web-server conf]# htpasswd -mb /etc/httpd/conf/.passfile jack 123 //非交互
Adding password for user jack
[root@web-server conf]# cat .passfile
harry:$apr1$yBmJw2lZ$5gOLS4WIffoYYUqbHb8j31
jack:$apr1$2mw51z8c$lvynCFG64cAMprCVqzDcD/
3.修改httpd.conf开启基本认证
vim /etc/httpd/conf/httpd.conf
<Directory "/webserver/">
Options Indexes FollowSymLinks
AllowOverride None
Order allow,deny
Allow from all
AuthType Basic
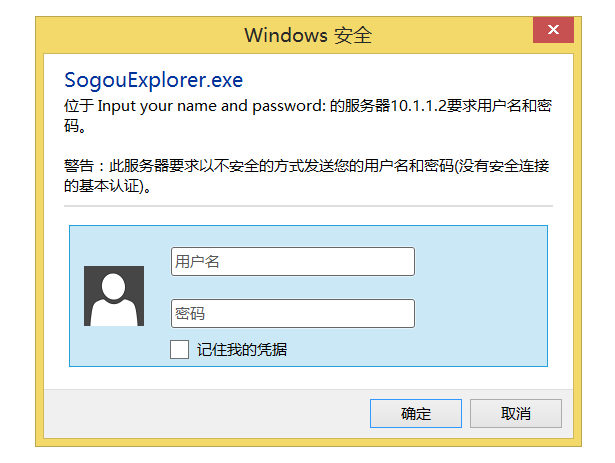
AuthName "Input your name and password:" //认证信息,可以随便写
AuthBasicProvider file //指定文件
AuthUserFile /etc/httpd/conf/.passfile //创建的密码文件
Require user harry jack //可用用户
</Directory>
重启服务
测试验证
总结:1.开启用户名密码认证有两点注意
1)需要知道网站的数据根目录 /webserver
2)将认证信息加入到<Directory "/webserver">......</Directory>
3)创建一个密码文件来保存用户名和密码 .passfile
需求2:允许多个用户访问
1.创建一个组文件保存所有用户(将很多用户加入到一个组里)
vim /etc/httpd/conf/groups
admin:user01 user02 user03
2.把用户的密码加入密码文件中
htpasswd -mb /etc/httpd/conf/.passfile user01 123
htpasswd -mb /etc/httpd/conf/.passfile user02 123
htpasswd -mb /etc/httpd/conf/.passfile user03 123
3.修改主配置文件
AuthType Basic
AuthName "请输入用户名和密码:"
AuthUserFile /etc/httpd/conf/.passfile
AuthGroupFile /etc/httpd/conf/groups
Require group admin
<Directory "/webserver/">
Options Indexes FollowSymLinks
AllowOverride None
Order allow,deny
Allow from all
AuthType Basic
AuthName "Input your name and password:"
AuthBasicProvider file
AuthUserFile /etc/httpd/conf/.passfile
AuthGroupFile /etc/httpd/conf/groups
Require group admin
#Require user harry jack //不注释掉的话,admin组不能访问
Require valid-user harry jack //harry/jack 和admin组内成员都可以访问
</Directory>
4.重启服务
5.测试验证
2.网络访问控制
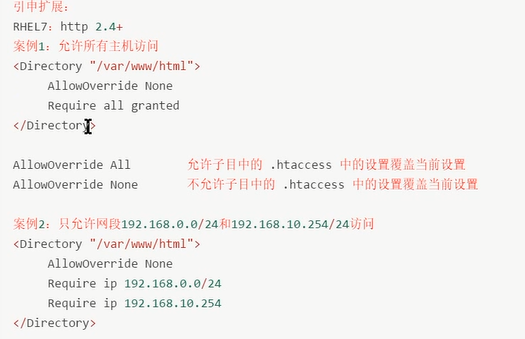
RHEL6:http 2.2版本
Order allow,deny 如果allow和deny冲突,deny为准
Order deny,allow 如果allow和deny冲突,allow为准
1.禁止部分IP不能访问网站
Order allow,deny
Allow from all
Deny from 192.168.0.254 10.1.1.5
2.针对某个网站
Order allow,deny
Allow from all
Deny from 192.168.0.0/255.255.255.0
3.针对域名
Order allow,deny
Allow from all
Deny from *.itcast.cc
4.拒绝大部分,允许某个IP
Order deny,allow
Deny from all
Allow from 192.168.0.254
需求:只拒绝10.1.1.3主机访问网站
Order allow,deny
Allow from all
Deny from 10.1.1.3
重启服务,测试验证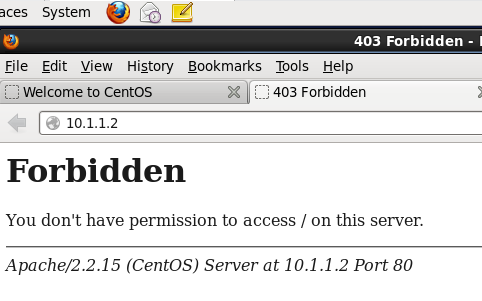
- HTTP通过状态码来标记返回信息,以下为常见的状态码:
常用状态码分类:
200:成功,请求的所有数据通过响应报文的entity-body部分发送:OK
(将上面的配置文件修改的部分注释)测试一下
[root@web-server ~]# wget http://10.1.1.2
--2019-04-28 17:47:20-- http://10.1.1.2/
Connecting to 10.1.1.2:80... connected.
HTTP request sent, awaiting response... 200 OK //状态码200
Length: 25 [text/html]
Saving to: “index.html”
100%[==================================>] 25 --.-K/s in 0s
2019-04-28 17:47:20 (5.73 MB/s) - “index.html” saved [25/25]
301:请求的URL指向的资源已经被删除,但是在响应报文中通过首部Location指明了资源现在所处的新位置:Moved Permanently
302:与301相似,但是在响应报文中通过Location指明资源现在所处的临时新位置:Found
304:客户端发出条件式请求,但是服务器上的资源未发送改变,通过响应此响应状态码通知客户端,Not Modified
401:需要客户端输入账户和密码才能访问资源:Unauthorized
403:请求被禁止:Forbidden
404:服务器无法找到客户端请求的资源:Not Found
500:服务器内部错误:Internal Server Error
502:代理服务器从后端服务器收到了一条伪响应:Bad Gateway