Juniper vSRX的安装与部署
一、准备工作
- Juniper官网下载15.1的.ova模板的junos
- 一台安装ESXI5.1, 5.5 ,6.0的服务器
- 两台vmx模拟PC测试,一台vsrx防火墙(15.1x49-d170)
二、操作部署
- 使用vSphere Client登录ESXI服务器
- 在登录的界面中,点击文件部署”OVA模板“
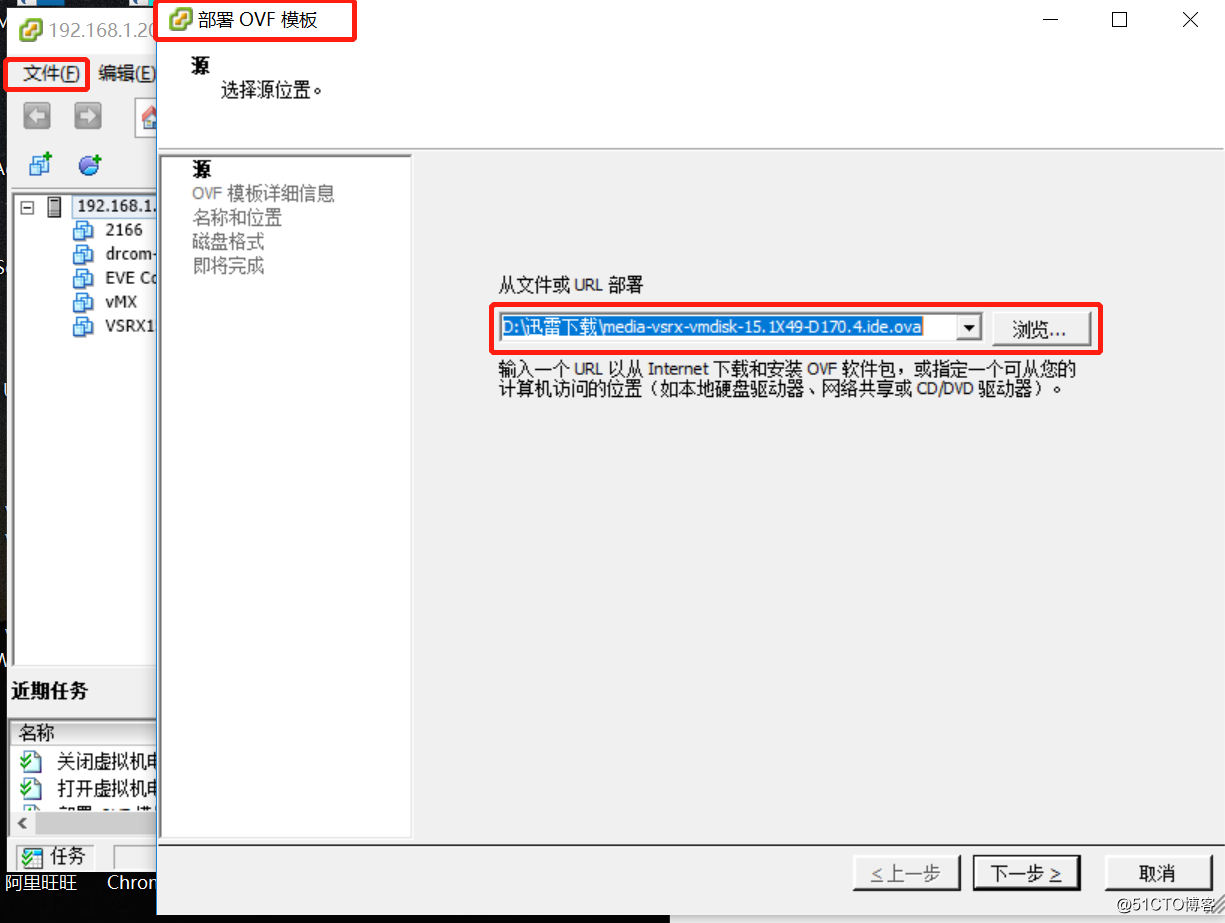
- 根据提示,点击完成
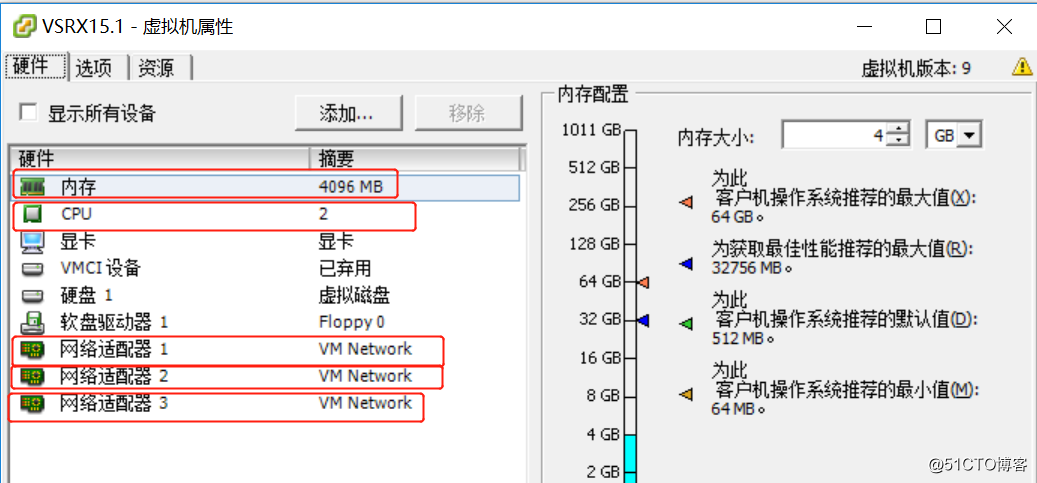
- 编辑虚拟机,设置相关参数
- 启动vsrx虚拟机,直至进入login界面
- 启动完成后,进入Login界面,用户名root,密码为空
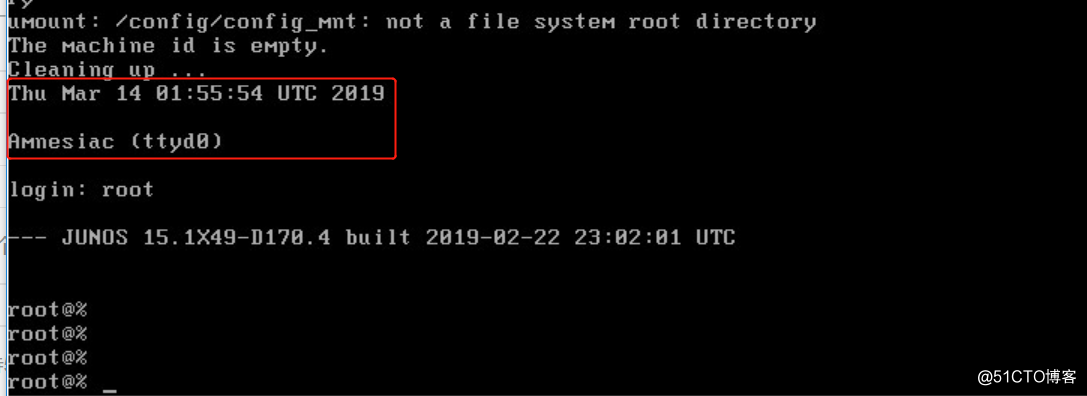
- 通过root用户名,直接进入shell界面,输入cli进入操作界面

- 从操作界面进入到配置界面,输入configuration
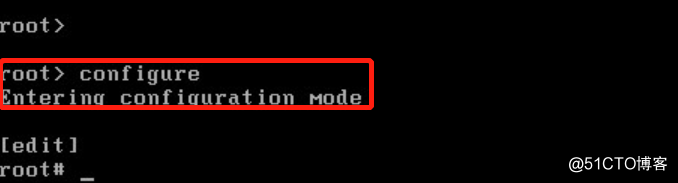
- 至此,vsrx换安装已经完成;
二、实验拓扑搭建
- 实现通过vmx、vsrx、isp链路组成逻辑拓扑图
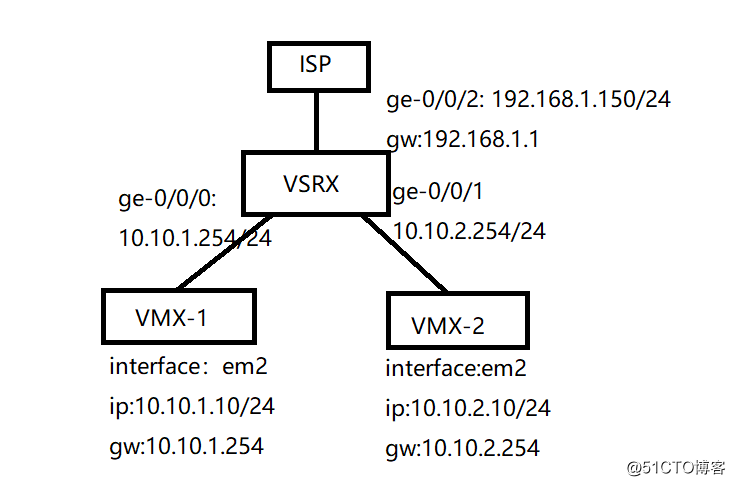
vmx-1网卡与vsrx ge-0/0/0在虚拟网卡vm2中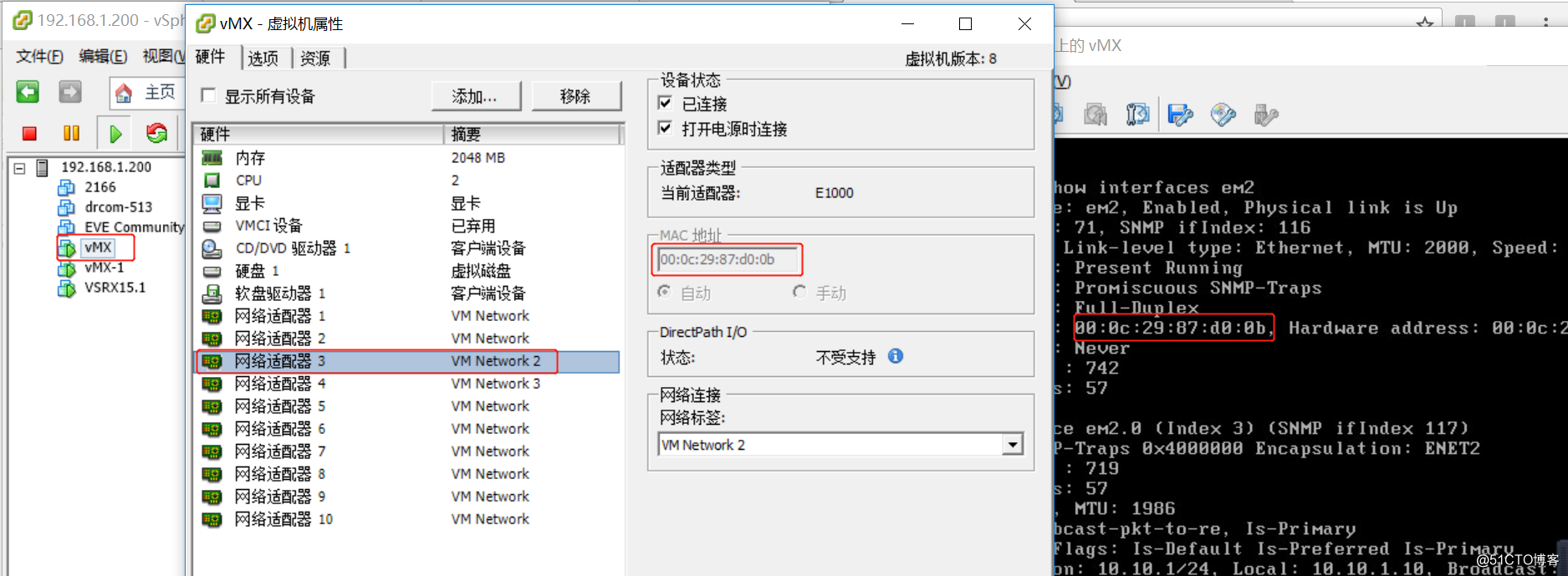
vmx-2网卡与vsrx ge-0/0/1在虚拟网卡vm3中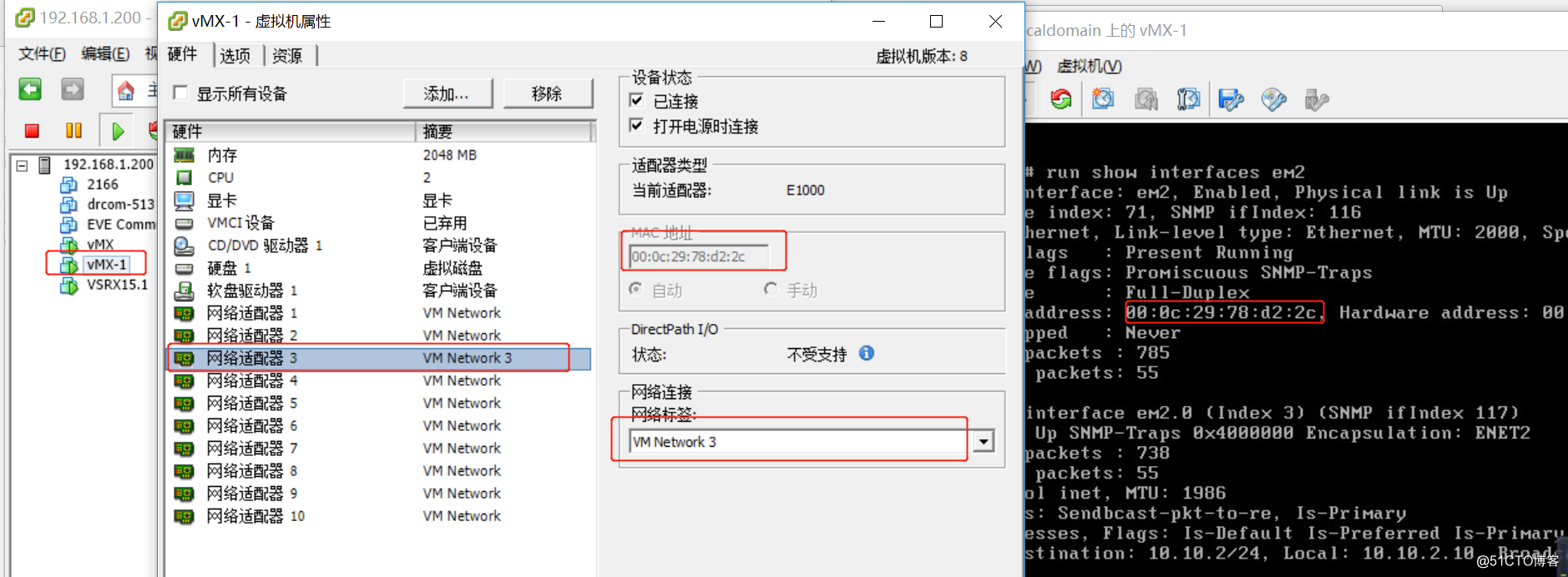
vsrx ge-0/0/0与isp在虚拟网卡vm中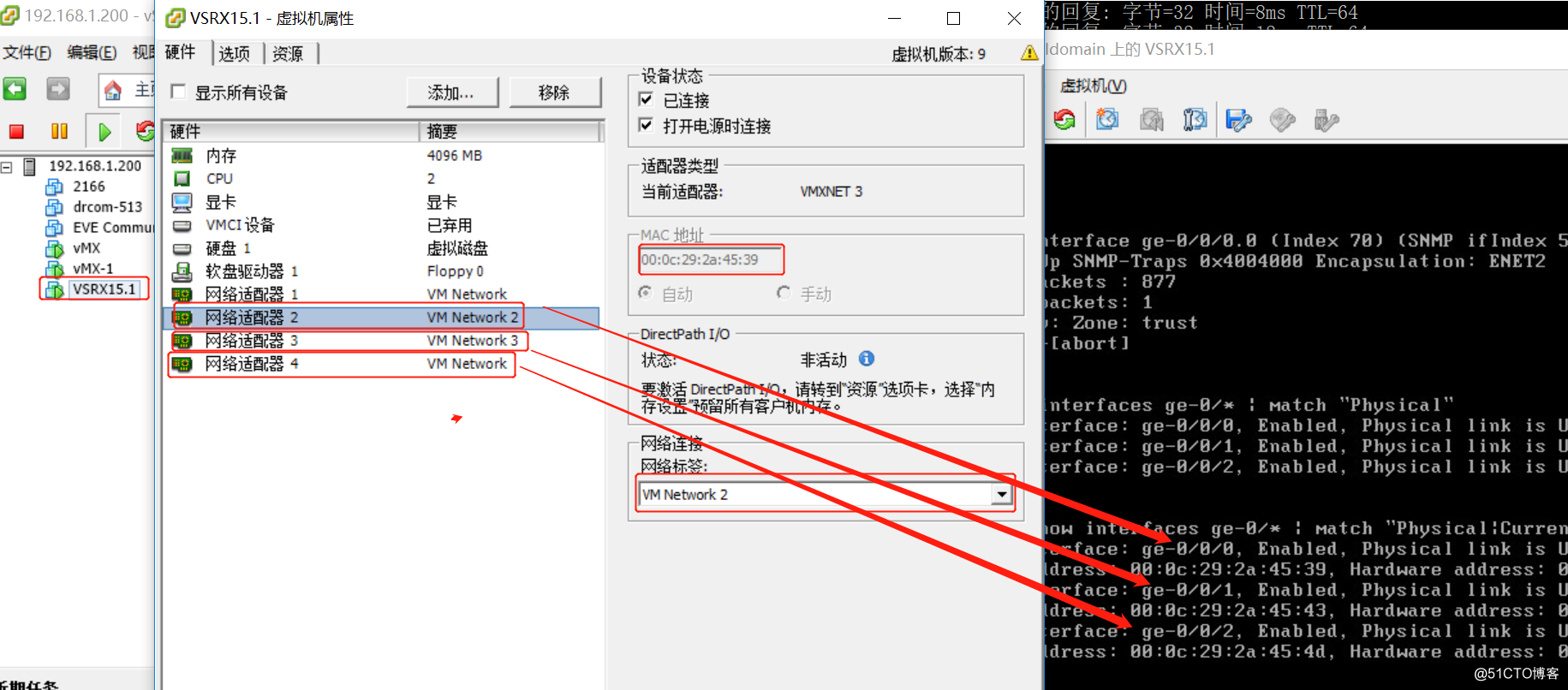
-
连通性测试:
vmx-1 ping vsrx ge-0/0/0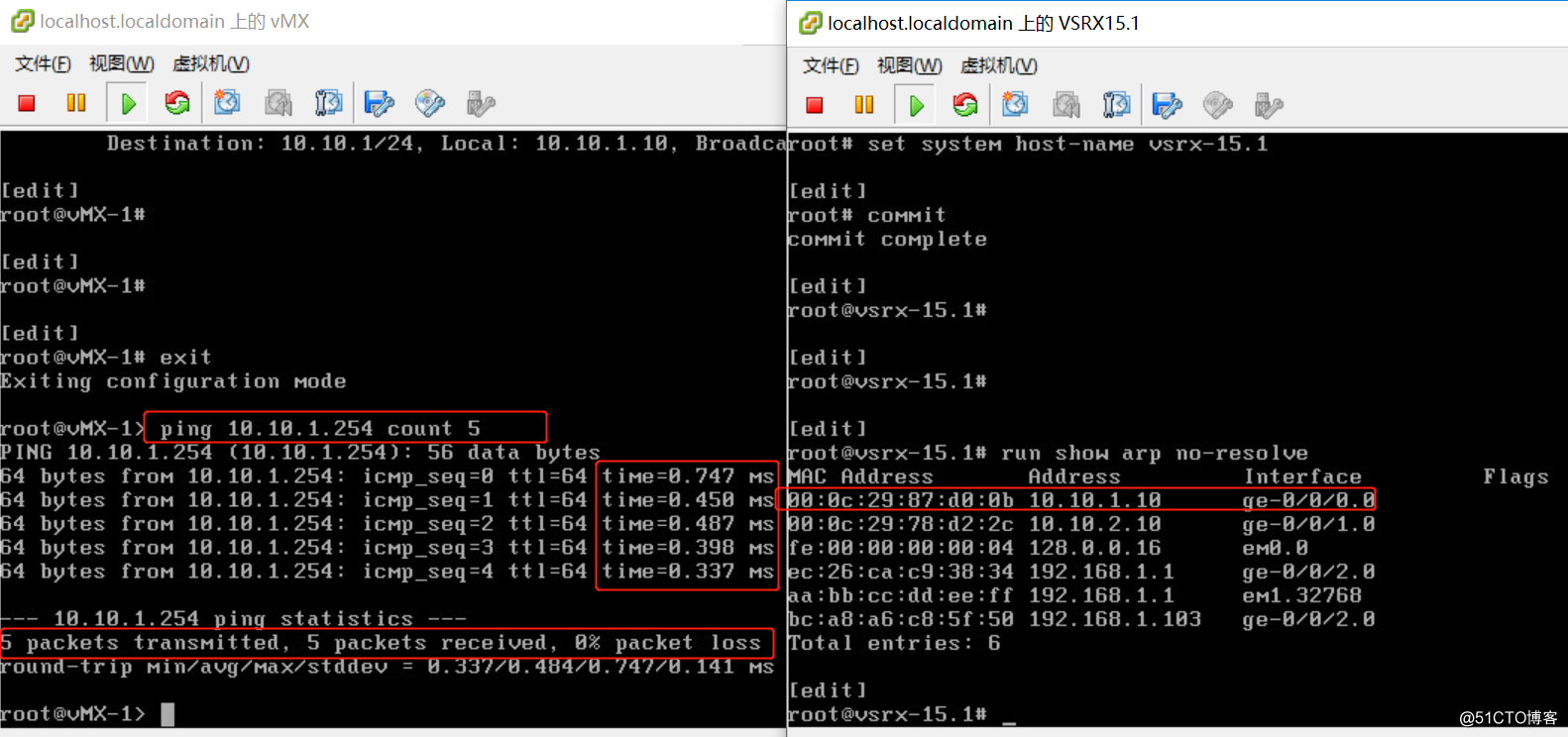
vmx-2 ping vsrx ge-0/0/1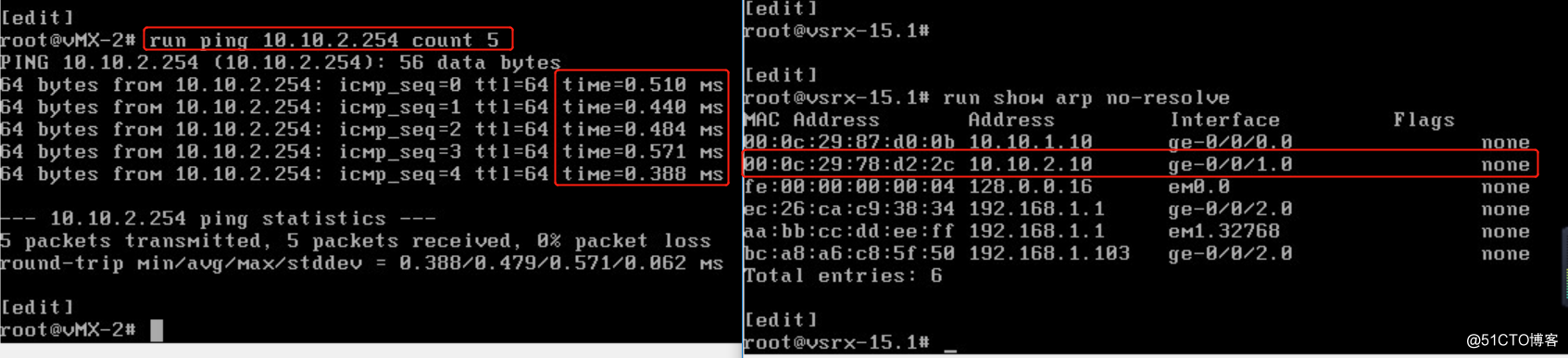
vsrx ge-0/0/2 ping isp 192.168.1.1, ping 114.114.114.114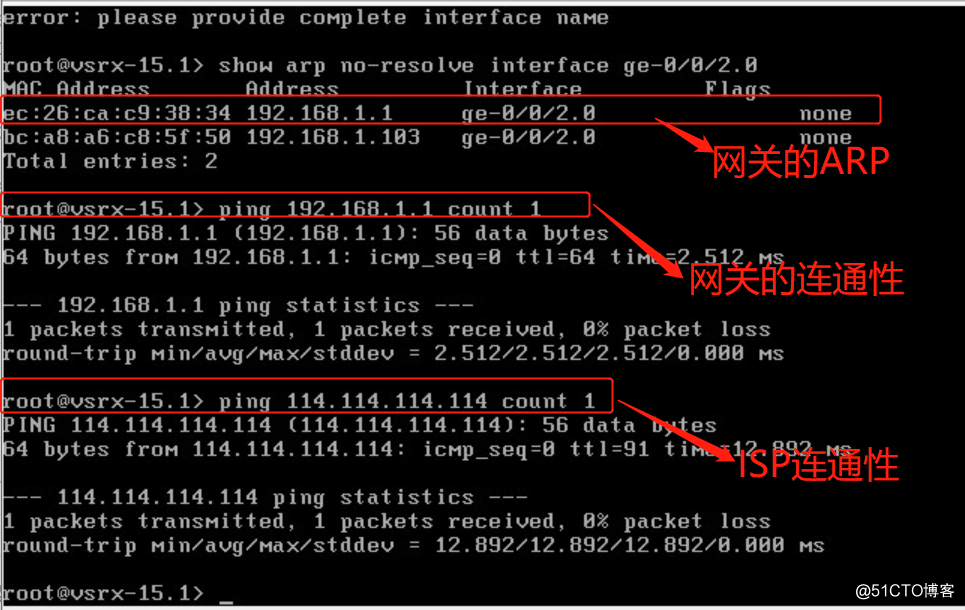
- vmx-1与vmx-2的连通性测试
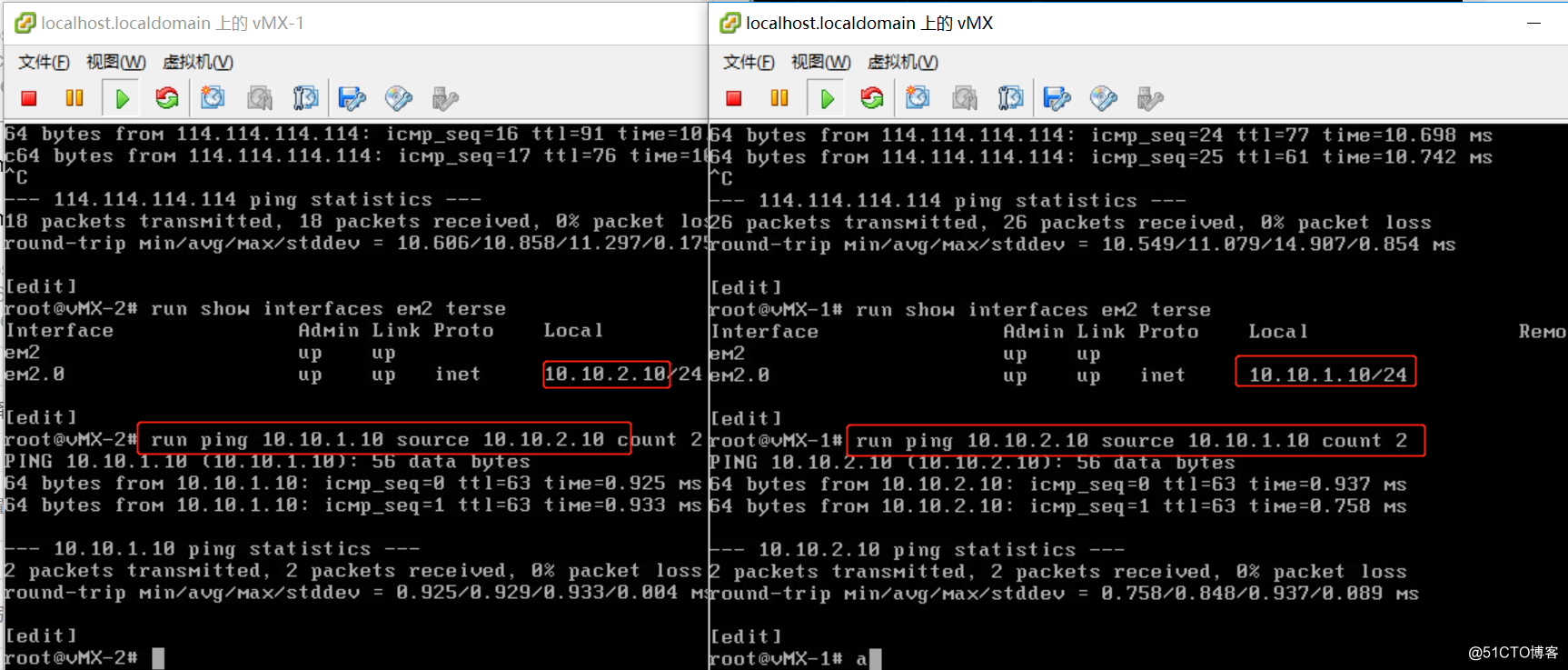
- vmx-1与vmx-2的Internet测试
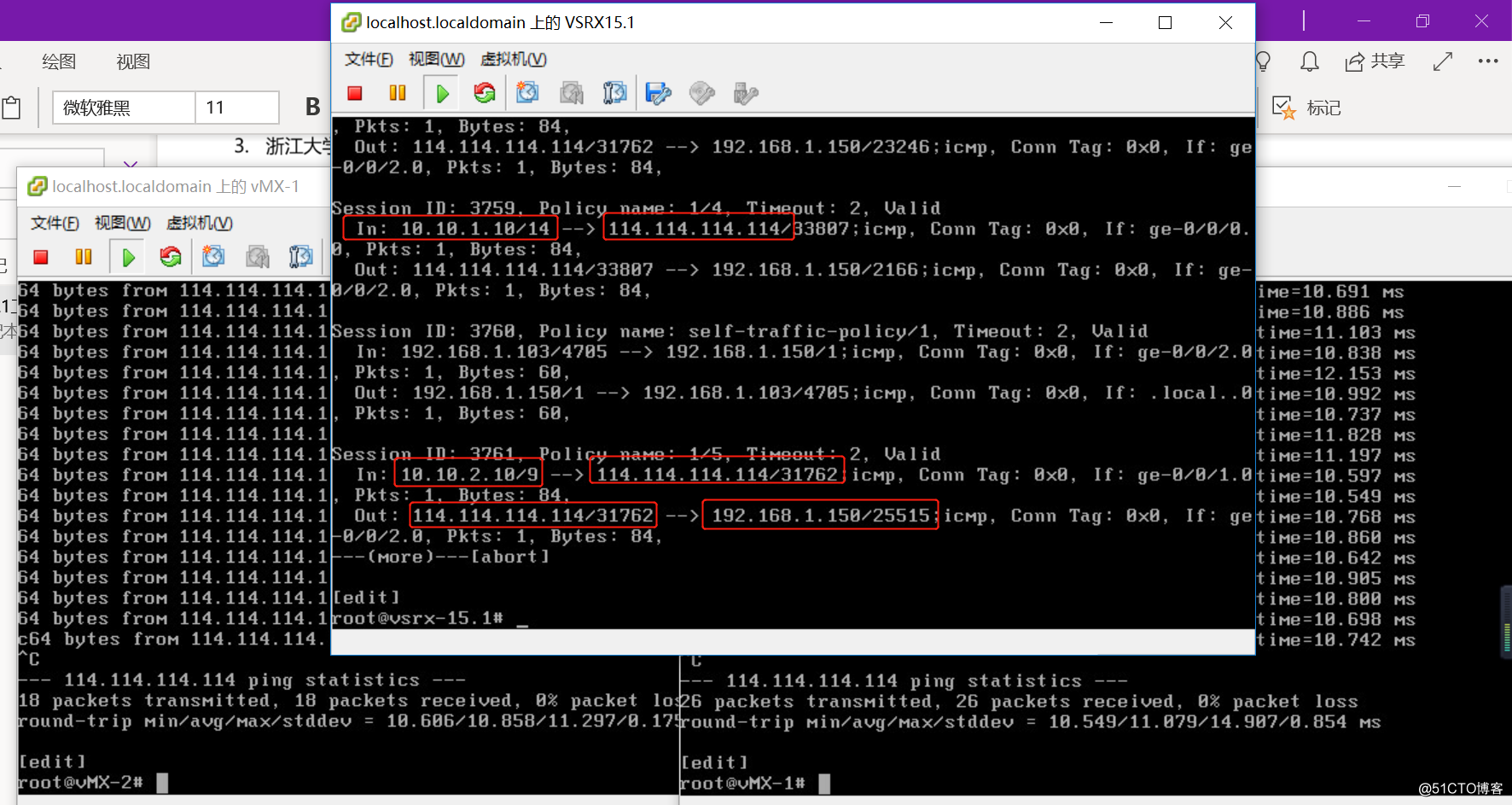
-
控制vmx-1和vmx-2的流量,不允许ping,ssh,只允许telnet。
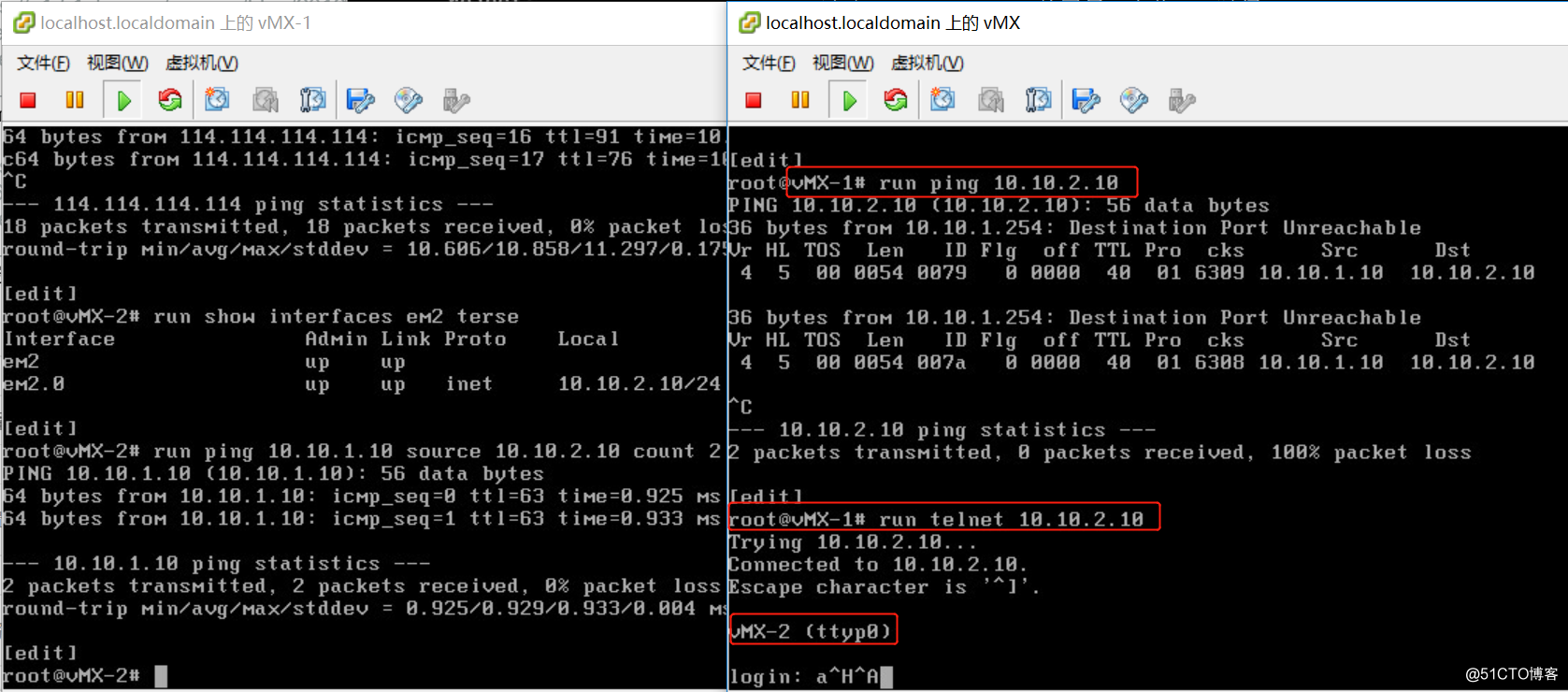
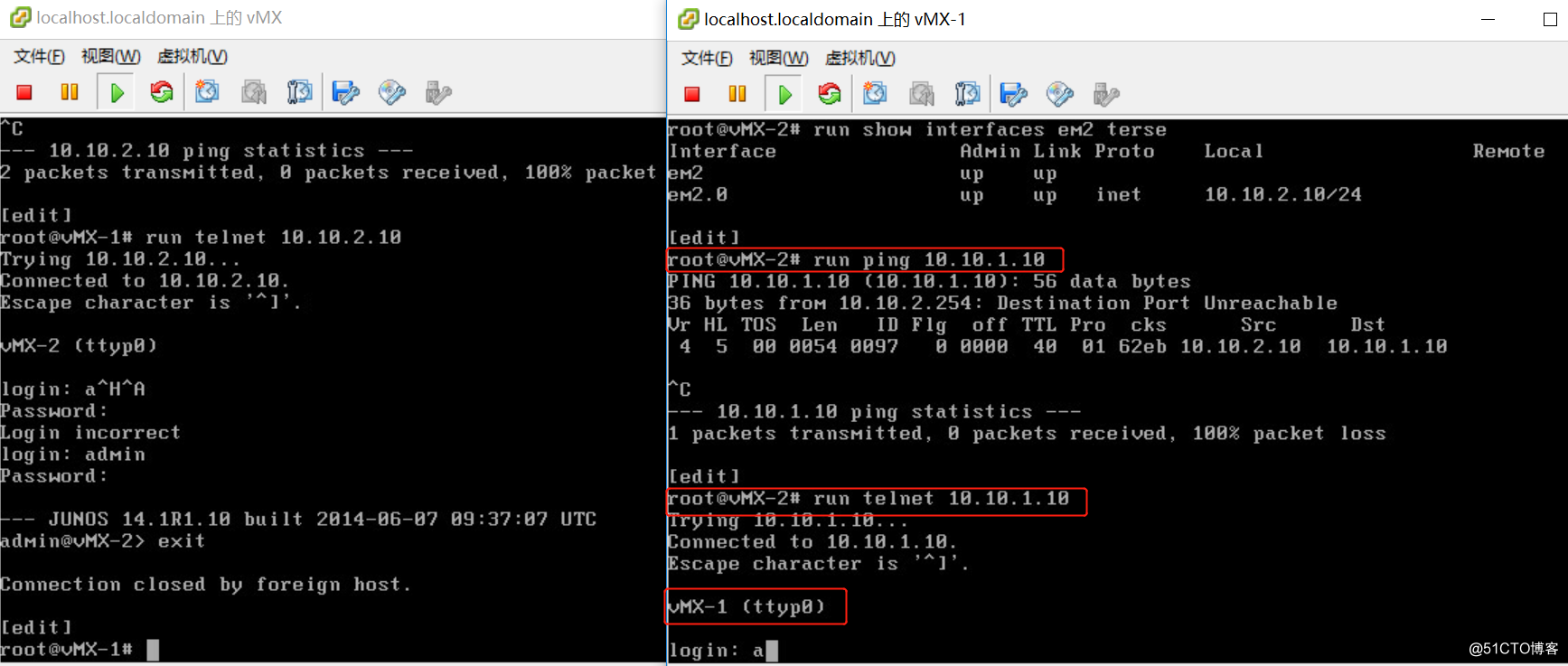
- 查看防火墙策略匹配的数量
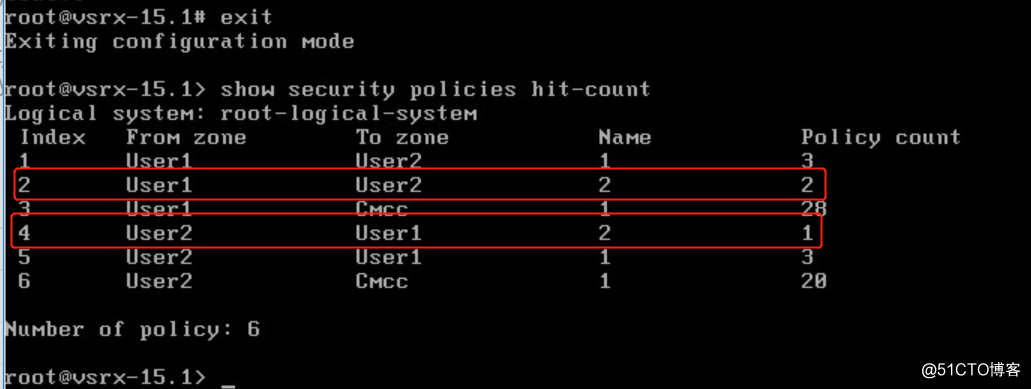
总结:
以上为vsrx防火墙在vm中的部署步骤,注意vsrx网卡的桥接,vsrx防火墙使用的也是junos,操作方式和配置方式和物理防火墙一样,接触过srx防火墙,可以很快的上手vsrx。
vSRX防火墙配置输出:
--- JUNOS 15.1X49-D170.4 built 2019-02-22 23:02:01 UTC
[email protected]> show configuration | no-more | display set
set version 15.1X49-D170.4
set system host-name vsrx-15.1
set system root-authentication encrypted-password "$5$AUnhweol$AN5LIIlwt5sXB1OvLkrM7TpuCrAu/JLQqDmNfXuFZd5"
set system name-server 8.8.8.8
set system name-server 114.114.114.114
set system login user admin uid 2000
set system login user admin class super-user
set system login user admin authentication encrypted-password "$5$ibd52KZv$NvtKlvBhZ3B5.5atZT0ipKRJ/BVqMruiO1lbY1PPsS4"
set system services ssh
set system services telnet
set system services web-management http
set system services web-management https system-generated-certificate
set system syslog user * any emergency
set system syslog file messages any any
set system syslog file messages authorization info
set system syslog file policy_session user info
set system syslog file policy_session match RT_FLOW
set system syslog file policy_session archive size 1000k
set system syslog file policy_session archive world-readable
set system syslog file policy_session structured-data
deactivate system syslog file policy_session
set system syslog file event-log any any
set system syslog file event-log archive files 1
set system syslog file event-log structured-data
set system license autoupdate url https://ae1.juniper.net/junos/key_retrieval
set security log mode event
set security address-book global address vmx-1 10.10.1.10/32
set security address-book global address vmx-2 10.10.2.10/32
set security screen ids-option untrust-screen icmp ping-death
set security screen ids-option untrust-screen ip source-route-option
set security screen ids-option untrust-screen ip tear-drop
set security screen ids-option untrust-screen tcp syn-flood alarm-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood attack-threshold 200
set security screen ids-option untrust-screen tcp syn-flood source-threshold 1024
set security screen ids-option untrust-screen tcp syn-flood destination-threshold 2048
set security screen ids-option untrust-screen tcp syn-flood queue-size 2000
set security screen ids-option untrust-screen tcp syn-flood timeout 20
set security screen ids-option untrust-screen tcp land
set security nat source rule-set snat from zone User1
set security nat source rule-set snat from zone User2
set security nat source rule-set snat to zone Cmcc
set security nat source rule-set snat rule 1 match source-address 10.10.1.0/24
set security nat source rule-set snat rule 1 match source-address 10.10.2.0/24
set security nat source rule-set snat rule 1 match destination-address 0.0.0.0/0
set security nat source rule-set snat rule 1 then source-nat interface
set security policies from-zone User1 to-zone Cmcc policy 1 match source-address any
set security policies from-zone User1 to-zone Cmcc policy 1 match destination-address any
set security policies from-zone User1 to-zone Cmcc policy 1 match application any
set security policies from-zone User1 to-zone Cmcc policy 1 then permit
set security policies from-zone User2 to-zone Cmcc policy 1 match source-address any
set security policies from-zone User2 to-zone Cmcc policy 1 match destination-address any
set security policies from-zone User2 to-zone Cmcc policy 1 match application any
set security policies from-zone User2 to-zone Cmcc policy 1 then permit
set security policies from-zone User1 to-zone User2 policy 2 match source-address vmx-1
set security policies from-zone User1 to-zone User2 policy 2 match destination-address vmx-2
set security policies from-zone User1 to-zone User2 policy 2 match application junos-icmp-ping
set security policies from-zone User1 to-zone User2 policy 2 match application junos-ssh
set security policies from-zone User1 to-zone User2 policy 2 then reject
set security policies from-zone User1 to-zone User2 policy 2 then log session-init
set security policies from-zone User1 to-zone User2 policy 2 then log session-close
set security policies from-zone User1 to-zone User2 policy 2 then count
set security policies from-zone User1 to-zone User2 policy 1 match source-address any
set security policies from-zone User1 to-zone User2 policy 1 match destination-address any
set security policies from-zone User1 to-zone User2 policy 1 match application any
set security policies from-zone User1 to-zone User2 policy 1 then permit
set security policies from-zone User2 to-zone User1 policy 2 match source-address vmx-2
set security policies from-zone User2 to-zone User1 policy 2 match destination-address vmx-1
set security policies from-zone User2 to-zone User1 policy 2 match application junos-icmp-ping
set security policies from-zone User2 to-zone User1 policy 2 match application junos-ssh
set security policies from-zone User2 to-zone User1 policy 2 then reject
set security policies from-zone User2 to-zone User1 policy 2 then log session-init
set security policies from-zone User2 to-zone User1 policy 2 then log session-close
set security policies from-zone User2 to-zone User1 policy 2 then count
set security policies from-zone User2 to-zone User1 policy 1 match source-address any
set security policies from-zone User2 to-zone User1 policy 1 match destination-address any
set security policies from-zone User2 to-zone User1 policy 1 match application any
set security policies from-zone User2 to-zone User1 policy 1 then permit
set security zones security-zone User1 interfaces ge-0/0/0.0 host-inbound-traffic system-services all
set security zones security-zone User1 application-tracking
set security zones security-zone User2 interfaces ge-0/0/1.0 host-inbound-traffic system-services all
set security zones security-zone User2 application-tracking
set security zones security-zone Cmcc interfaces ge-0/0/2.0 host-inbound-traffic system-services all
set security zones security-zone Cmcc application-tracking
set interfaces ge-0/0/0 unit 0 family inet address 10.10.1.254/24
set interfaces ge-0/0/1 unit 0 family inet address 10.10.2.254/24
set interfaces ge-0/0/2 unit 0 family inet address 192.168.1.150/24
set routing-options static route 0.0.0.0/0 next-hop 192.168.1.1
vMX-1配置输出:
admin@vMX-1> show configuration | no-more | display set
set version 14.1R1.10
set system host-name vMX-1
set system root-authentication encrypted-password "$1$wt0dI4la$d7JtEZv8MdB/aFx2Sf0cN."
set system name-server 8.8.8.8
set system login user admin uid 2001
set system login user admin class super-user
set system login user admin authentication encrypted-password "$1$ZndUPvaG$jUKRfxwDPyKgx8GJ5wJ0M/"
set system services ftp
set system services ssh
set system services telnet connection-limit 5
set system syslog user * any emergency
set system syslog file messages any notice
set system syslog file messages authorization info
set system syslog file interactive-commands interactive-commands any
set interfaces em2 unit 0 family inet address 10.10.1.10/24
set routing-options static route 0.0.0.0/0 next-hop 10.10.1.254
vMX-2配置输出:
admin@vMX-2> show configuration | no-more | display set
set version 14.1R1.10
set system host-name vMX-2
set system root-authentication encrypted-password "$1$A6hZKEhm$h/SdcxNgtaL0yN8NThxeu/"
set system name-server 114.114.114.114
set system login user admin uid 2001
set system login user admin class super-user
set system login user admin authentication encrypted-password "$1$HSS00OAL$KJx8HU4Ve6vTX9I.1SZWw/"
set system services ftp
set system services ssh
set system services telnet connection-limit 5
set system syslog user * any emergency
set system syslog file messages any notice
set system syslog file messages authorization info
set system syslog file interactive-commands interactive-commands any
set interfaces em2 unit 0 family inet address 10.10.2.10/24
set routing-options static route 0.0.0.0/0 next-hop 10.10.2.254