携程的登录分析,思路是很清晰的
POST https://passport.ctrip.com/gateway/api/soa2/12559/userValidate HTTP/1.1
Host: passport.ctrip.com
Connection: keep-alive
Content-Length: 1031
Accept: application/json, text/javascript, */*; q=0.01
Origin: https://passport.ctrip.com
X-Requested-With: XMLHttpRequest
contentType: application/json; charset=utf-8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3719.3 Safari/537.36
Content-Type: application/json; charset=UTF-8
Referer: https://passport.ctrip.com/user/login?BackUrl=https%3A%2F%2Fwww.ctrip.com%2F
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: _RGUID=71ac057c-665c-4a70-8fdd-d9ce59460391; _RSG=mf4NcnN1i67HEWHPvSsT_8; _RDG=281eecb0a9929920551fa1397940a1cdb6; _abtest_userid=d806f509-30c1-4ce0-a027-6f0141ccb793; _RF1=194.124.34.202; _ga=GA1.2.530851293.1551234078; MKT_Pagesource=PC; _jzqco=%7C%7C%7C%7C%7C1.924630241.1551234079179.1551234079179.1551234079179.1551234079179.1551234079179.0.0.0.1.1; __zpspc=9.1.1551234079.1551234079.1%234%7C%7C%7C%7C%7C%23; gad_city=87da0552ec06dcc023dea4c59ce3d7de; _gid=GA1.2.1002763003.1551328710; _gat=1; Session=smartlinkcode=U130026&smartlinklanguage=zh&SmartLinkKeyWord=&SmartLinkQuary=&SmartLinkHost=; Union=AllianceID=4897&SID=130026&OUID=&Expires=1551933509878; _bfa=1.1551234071921.2kwg9q.1.1551234071921.1551328699816.2.3; _bfs=1.2; _bfi=p1%3D10320670296%26p2%3D0%26v1%3D3%26v2%3D0
{"AccountHead":{"Token":"p0c3a134862d264cb626ee3c94501814264cdbe8b02e5","SliderVersion":"2.5.24","Platform":"P","Extension":{}},"Data":{"accessCode":"7434E3DDCFF0EDA8","strategyCode":"63A70EA9BB38F5D","userName":"sfdf","certificateCode":"ggggggggggggg","extendedProperties":[{"key":"LoginName","value":"sfdf"},{"key":"Platform","value":"P"},{"key":"PageId","value":"10320670296"},{"key":"rmsToken","value":"fp=wcerw3-12cww2x-66g1x2&vid=1551234071921.2kwg9q&pageId=10320670296&r=71ac057c665c4a708fddd9ce59460391&ip=194.124.34.202&rg=fin&kpData=0_0_0&kpControl=0_0_0-0_0_0&kpEmp=0_0_0_0_1305_5_0_1_0_0-0_0_0_0_4812_13_0_0_0_0-0_0_0_0_0_0_0_0_0_0&screen=1366x768&tz=+8&blang=zh-CN&oslang=zh-CN&ua=Mozilla%2F5.0%20(Windows%20NT%2010.0%3B%20Win64%3B%20x64)%20AppleWebKit%2F537.36%20(KHTML%2C%20like%20Gecko)%20Chrome%2F74.0.3719.3%20Safari%2F537.36&d=passport.ctrip.com&v=22"},{"key":"URL","value":"https://passport.ctrip.com/user/login?BackUrl=https%3A%2F%2Fwww.ctrip.com%2F"},{"key":"http_referer","value":"https://www.ctrip.com/"}]}}
主要分析的是POST提交的参数
{"AccountHead":{"Token":"p0c3a134862d264cb626ee3c94501814264cdbe8b02e5","SliderVersion":"2.5.24","Platform":"P","Extension":{}},"Data":{"accessCode":"7434E3DDCFF0EDA8","strategyCode":"63A70EA9BB38F5D","userName":"sfdf","certificateCode":"ggggggggggggg","extendedProperties":[{"key":"LoginName","value":"sfdf"},{"key":"Platform","value":"P"},{"key":"PageId","value":"10320670296"},{"key":"rmsToken","value":"fp=wcerw3-12cww2x-66g1x2&vid=1551234071921.2kwg9q&pageId=10320670296&r=71ac057c665c4a708fddd9ce59460391&ip=194.124.34.202&rg=fin&kpData=0_0_0&kpControl=0_0_0-0_0_0&kpEmp=0_0_0_0_1305_5_0_1_0_0-0_0_0_0_4812_13_0_0_0_0-0_0_0_0_0_0_0_0_0_0&screen=1366x768&tz=+8&blang=zh-CN&oslang=zh-CN&ua=Mozilla%2F5.0%20(Windows%20NT%2010.0%3B%20Win64%3B%20x64)%20AppleWebKit%2F537.36%20(KHTML%2C%20like%20Gecko)%20Chrome%2F74.0.3719.3%20Safari%2F537.36&d=passport.ctrip.com&v=22"},{"key":"URL","value":"https://passport.ctrip.com/user/login?BackUrl=https%3A%2F%2Fwww.ctrip.com%2F"},{"key":"http_referer","value":"https://www.ctrip.com/"}]}}
主要的js部分有浏览器的信息,ip地址信息,这些都有办法搞到.
i.AccountHead = {
Token: safeToken,//传入
SliderVersion: "2.5.24",
Platform: "P",
Extension: {
rmsToken: undefined
}
},
i.Data = {
accessCode: "7434E3DDCFF0EDA8",//固定
strategyCode: '63A70EA9BB38F5D',//固定
userName: loginName,//传入
certificateCode: password,// 传入密码
extendedProperties: [{"key":"LoginName","value":loginName},{"key":"Platform","value":"P"},{"key":"PageId","value":PageId},{"key":"rmsToken","value":"fp=13awamm-1b897f5-12498f7&vid=1551234892336.3vakub&pageId="+PageId+"&r=aaf3c6d4899640d6bc40879710c994ec&ip="+ip+"&rg=fin&kpData=0_0_0&kpControl=0_0_0-0_0_0&kpEmp=0_0_0_0_848_12_0_0_0_0-0_0_0_0_960_15_0_0_0_0-0_0_0_0_0_0_0_0_0_0&screen=1366x768&tz=+8&blang=zh-CN&oslang=zh-CN&ua=Mozilla%2F5.0%20(Windows%20NT%206.1%3B%20Win64%3B%20x64)%20AppleWebKit%2F537.36%20(KHTML%2C%20like%20Gecko)%20Chrome%2F74.0.3719.4%20Safari%2F537.36&d=passport.ctrip.com&v=22"},{"key":"URL","value":"https://passport.ctrip.com/user/login?BackUrl=https%3A%2F%2Fwww.ctrip.com%2F"},{"key":"http_referer","value":"https://www.ctrip.com/?utm_source=baidu&utm_medium=cpc&utm_campaign=baidu81&campaign=CHNbaidu81&adid=index&gclid=&isctrip=T"}]
};
Token参数
最关机键的参数是Token,因为Token值是通过携程的后台計算前端的風險返回的一個風險值,如果沒有返回風險值說明需要滑動驗證,或者點擊字體的來驗證.
GET https://ic.ctrip.com/captcha/risk_inspect?callback=captcha09119219248822854&extend_param=2V6x7pDkvcrysIz84iab1jwDqMR%2Fk9je8xAbwc5hVBSCCtefBDf%2FH3Ge1WWkjoxPo%2B7flj6ZQM5%2FDEEKZ2Z9hI255D6t%2B8YzNS1Oc1FQWmQ%3D&appid=100008493&business_site=crm_login_online&version=2.5.24&dimensions=VjmGo%2BEwaj%2FHmvpWl%2BOXiPYl9e8ucSF74NCaaO2Du3ShEkA%2B1avx6r3oNDN71WhMlYIs%2FvsgxRQYJAJiUsGn7%2Bd1ViixpBDhfaTOse1nUK1i99L90pLfIVKZtEUAEJDpjX4WwHnuHnu8D8wCZA9chFVLPVzA%2FsUZtuEehlOTCoLK8lFgK7eR6L2i%2BWZE3BTsPohgpPh0t0wWIVNDxAj5AA32paKwRvq9N499ftKyx5WaaQzKmtYehlHvYPdx1ClcGthP8G8ZbnRuP0iUWnUGeAAJUmJydKxvDqnO7IN9GC%2FBS9wzzU3H84APWddFDHoE54n8N9bM6tTLckd75sFiVEHyHj0Stw511cfdgk77HNvL%2F7yPfuGQuCN56dWNwwNilDoTe0QDxrtCeJDomh%2FQUo89abLhUu197Z%2BeSSMmXyAqB6kWlnUBWKDOrwXhMD%2Bb2cbh%2BwATFJfSzxDiiRtWpaPqPbgLlnWyNfYh4LI3IzO4vYiIxkXlCWUB6rO6xLgj%2BQs%2FZ2puoSgZTfuHJLtV0tGT7UG0j80ZlJHWlgS5iYcNgY1QQHikEeNkscpVRK%2FUk1M6xH41%2FPRLzXYrM8ggovxNCK4oEmBImaf2fp2ZIldfNFw6vwOljAq13Yk%2BkWtN3GTaEcelSegmZI5crTFy%2F72lfoZea5MtS2TF693YQx9aqKb6EnbQNODuBi71nRKHMZBjX1NMFzG2l8QHVH9QIfR1CoKfsvh3i35aKGvS3RJy0Hf5cJ0C2aL4YdJrkjqbWGC%2BpwXZQZ4nrQGQNjXws0so%2BjarskWsk0YRahfnAIT9y5%2FtG3ade4f3Fp9vFytsjHvVPkS2a9oaQyRKNcJYsoML7o4Zii6Ivl%2FfXZqjzINCf4FzLOJFVF3MaUE98JaBj3bRRh9%2FxgOH6%2BBoDs8vFxJVItBSEyqR39sqiy%2FsA3dNjSPw9NsXaSdeS9tfr2TRpJxRqRGAkekmzr1s%2BSSRl3kq7jYwM0LiREJJ6jKeKHZy2ZiZTSYlC0ntHGHM7R0URP68rHo0R%2BeePfQA5Xi8X9hD5xpbfaX1EyShBhTZb92dEHrhdayfyjv7dsKT2frlNm2aX4oVFnSp7wwcfdq90DZ%2B2KIlIc17Yokw4m64wj3ujA0XPUy5yrVRNKPx673sxFQ1kk2reSCPVBFsf5Law%2B2tTq%2Bj4zgfGVmqoFmOvGRfEltU373OF8QrWP1opWFpIbC1zWjU0hwSPalOFyTXRy49r0m7yu40VjsfVWQOFWm%2FJIhBHoJWM2%2B1SKdnaPP9m%2BuaNaUzZW4HcSO15TLXMSxlfscoKZZW3AKXA1PnMoc%3D&sign=30a01c21556cb3137c5a2aa7aad40080 HTTP/1.1
Host: ic.ctrip.com
Connection: keep-alive
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/74.0.3721.3 Safari/537.36
Accept: */*
Referer: https://passport.ctrip.com/user/login?BackUrl=https%3A%2F%2Fwww.ctrip.com%2F
Accept-Encoding: gzip, deflate, br
Accept-Language: zh-CN,zh;q=0.9
Cookie: _RGUID=71ac057c-665c-4a70-8fdd-d9ce59460391; _RSG=mf4NcnN1i67HEWHPvSsT_8; _RDG=281eecb0a9929920551fa1397940a1cdb6; _abtest_userid=d806f509-30c1-4ce0-a027-6f0141ccb793; _ga=GA1.2.530851293.1551234078; MKT_Pagesource=PC; Session=smartlinkcode=U130026&smartlinklanguage=zh&SmartLinkKeyWord=&SmartLinkQuary=&SmartLinkHost=; Union=AllianceID=4897&SID=130026&OUID=&Expires=1552027226375; Mkt_UnionRecord=%5B%7B%22aid%22%3A%224897%22%2C%22timestamp%22%3A1551422426403%7D%5D; __zpspc=9.3.1551422426.1551422426.1%232%7Cwww.baidu.com%7C%7C%7C%7C%23; _jzqco=%7C%7C%7C%7C%7C1.924630241.1551234079179.1551411498483.1551422426630.1551411498483.1551422426630.0.0.0.3.3; _RF1=194.124.34.202; gad_city=2b565ea2e8ff53ecb7394782e7e5595d; _bfa=1.1551234071921.2kwg9q.1.1551428801037.1551665877246.6.18; _bfs=1.2
这里面有3个加密参数extend_param,dimensions,sign
找到加密的部分:
R = {
rt: k.rms,
ua: k.userAgent,
p: la,
fp: k.FP,
vid: k.VID,
sfp: k.sFP,
svid: k.sVID,
guid: fd(),
h5_duid: Ic(wa("DUID"), "u"),
pc_duid: Ic(wa("CtripUserInfo"), "U"),
hb_uid: gd(),
pc_uid: wa("ticket_ctrip"),
h5_uid: wa("cticket"),
infosec_openid: wa("infosec_openid"),
device_id: ab(32, 3, "_bfs"),
client_id: ab(32, 0, "_bfi"),
pid: ab(16, 2, "corpid"),
sid: ab(16, 1, "SMBID"),
login_uid: ab(10, 2, "login_uid")
};
V = I(A.stringify(R), 0);
wb = {
resolution_width: k.scrW,
resolution_height: k.scrH,
language: Pb
};
ca = I(A.stringify(wb), 0);
pa = C.MD5("appid=" + M + "&business_site=" + N + "&version=" + O.ver + "&dimensions=" + V + "&extend_param=" + ca);
$a("load");
Ga(E.inter_base + E.risk_inspect, {
extend_param: encodeURIComponent(ca),
appid: M,
business_site: N,
version: O.ver,
dimensions: encodeURIComponent(V),
sign: pa.toString()
}
sfp.svid,vid参数
通过调试发现,第一次获取的R对象的时候 sfp: null, svid: null,可是实际是最后的sfp和svid是不为null的,而且这部分的代码,断点需要一步一步的调试,很麻烦.
重新的赋值sfp和svid的代码:
try {
var e = A.parse(d);
a.sFP = e.securefp;
a.sVID = e.vid
} catch (g) {}
try {
c ? (R.fp = a.FP,
R.vid = a.VID,
R.sfp = a.sFP,
R.svid = a.sVID,
V = I(A.stringify(R), 0)) : (c = !0,
b())
} catch (g) {
X(g)
}
vid参数是从cookie中来的,而且这个cookie的有效期有1年多,所以可以写成固定的,这里就没有分析是如何生成的.
_bfa=1.1551234071921.2kwg9q.1.1551428801037.1551665877246.6.18
其中还有I函数也需要找到,加密C對象也需要找到,這些都不難.
深入svid,sfp
可是即使你分析到了上面的代码了,你也没有办法确定这个svid和sfp是如何生成的,ctrip的代码是加密的,代码邏輯顺序被改变了,下断点只能做单步调试.
关键代码:
var a = {};
a.canvas = document.createElement("canvas"),
a.doNotCaptureKeyboard = 1,
setTimeout(function() {
var t = (a = _bfp(a)).cwrap("mixfp", "string", ["string"])
, e = a.cwrap("authEncrypt", "string", ["string"])
, n = p.encode(t(r)) // sfp參數
, i = p.encode(e(v.get_("vid"))); // svid參數
有一部分是我改写了的,v.get_函数改写之后就是这样的:
传入cookie的_bfa,就是那个有效期有一年多的那个,字符串切成数组.重組一下就是
get_=function(t){
var bfa=["1","1551336454703","281p73","1","1551336454703","1551336454703","1",2]
if (bfa) {
var e = bfa;
switch (t) {
case "vid":
return e[1] + "." + e[2];
case "sid":
return parseInt(e[6], 10) || 0;
case "pvid":
return parseInt(e[7], 10) || 0;
case "fullpv":
return e[1] + "." + e[2] + "." + e[6] + "." + e[7];
default:
return ""
}
}
}
_bfp这个函数大家可以自己找下,还有一点就是加密用到了canvas ,有點意外
當然實際分析的時候不止這些,還有很多的坑,搞定的之後使用requests模擬發包,正確的返回結果是這樣的:
captcha09119219248822854({"code":0,"message":"Success","result":{"adv":null,"param":null,"rid":"11570C27B5E14E9883322160BEE22597","risk_info":{"process_type":"NONE","process_value":null,"risk_desc":null,"risk_level":0},"tip":{"advertisement":null,"error_msg":"校验失败,请重试!","forbidden_msg":"校验出错,请稍后再试!","pass_msg":"检测风险通过!","reselect_msg":"再次点击图标取消","retry_msg":"请重新验证!","right_msg":"校验成功,通过!","select_msg":"请顺序点击图中文字","slide_msg":"请按住滑块,拖动到最右","submit_msg":"提交","timeout_msg":"请求超时,请重试!"},"token":"p0189f6fa22d28cfcb45447b34becbc16bbf3f4eefbfa"}})
token,就是最關鍵的參數了,拿著token去請求.就可以了
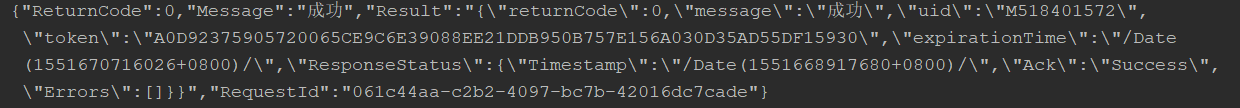
依然是最終成功的截圖:
結語:
ctrip的登錄還是很難扒的,加密的邏輯很複雜,不是一眼可直接找到的,這個過程花了不少的時間,源碼就不發了,畢竟大家都不容易.需要可以q我:[email protected]