版权声明:本文为博主原创文章,未经博主允许不得转载。 https://blog.csdn.net/huangjun0210/article/details/86687432
kubeadm init流程
- 1. kubeadm init流程概览
- 2. 引导前检查
- 3. 生成私钥以及数字证书
- 3.1 查看公钥证书:自建CA,生成ca.key与ca.crt
- 3.2 apiserver的私钥与公钥证书
- 3.3 apiserver访问kubelet使用的客户端私钥与证书
- 3.4 services account需要的sa.key与sa.pub
- 3.5 Etcd相关的私钥与数字证书
- 4. 生成控制平面的kubeconfig文件
- 5. 下载镜像,等待控制平面启动
- 6. 保存MasterConfiguration
- 7. 设定Master标志
- 8. 进行基于TLS的安全引导相关的配置
- 9. 安装DNS和kube-porxy插件
1. kubeadm init流程概览
- 引导前检查
- 生成私钥以及数字证书
- 生成控制平面的kubeconfig文件
- 生成控制平面组件的manifest文件
- 下载镜像,等待控制平面启动
- 保存MasterConfiguration
- 设定Master标志
- 进行基于TLS的安全引导相关的配置
- 安装DNS和kube-porxy插件
2. 引导前检查
kubeadm init pre-flight check:
- kubeadm版本要与安装的kubernetes版本的比对检查
- kubernetes安装的系统需求检查
- 其他检查:用户<要求是root>,主机,端口,swap,工具等
3. 生成私钥以及数字证书
kubeadm init生成私钥与证书:
目录在/etc/kubernetes/pki下
- 自建CA,生成ca.key与ca.crt
- apiserver的私钥与公钥证书
- apiserver访问kubelet使用的客户端私钥与证书
- services account需要的sa.key与sa.pub
- Etcd相关的私钥与数字证书
证书存放在各个节点的/etc/kubernetes/pki下,以master节点为例:
- 证书存放路径:/etc/kubernetes/pki
root@K8S-Master:/etc/kubernetes# cd /etc/kubernetes/pki
root@K8S-Master:/etc/kubernetes/pki# ll

3.1 查看公钥证书:自建CA,生成ca.key与ca.crt
root@K8S-Node1:/etc/kubernetes/pki# openssl x509 -in ca.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 0 (0x0)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Jan 28 07:44:21 2019 GMT
Not After : Jan 25 07:44:21 2029 GMT
Subject: CN = kubernetes
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:f0:2c:9f:9d:8e:b7:cb:60:0f:91:ee:ba:50:26:
bc:ee:35:28:b4:5a:b7:ba:90:74:4c:4f:4e:3a:3d:
5e:e0:1f:d9:8f:b3:16:78:b1:5b:2c:a0:e7:ba:62:
21:c9:68:1b:d7:b7:9d:7b:c7:a1:e2:a1:5b:96:e9:
db:7a:f9:ac:ab:96:bd:7b:be:22:f0:6c:db:28:02:
23:1b:2f:77:77:ba:ca:cf:23:78:b3:62:2c:7a:99:
6c:3f:ee:f6:00:32:8a:41:57:e9:90:41:bd:6e:d9:
3c:d2:7a:4b:25:a8:2b:55:e3:2f:4d:48:6f:76:b4:
91:cf:10:df:85:42:62:39:b1:91:9f:fd:c8:da:27:
63:33:60:5b:19:b5:cc:a2:fb:c6:8c:06:22:ee:97:
31:2d:a4:a7:77:2e:a6:76:2d:45:82:c5:95:ff:5f:
56:96:1b:80:5e:59:56:91:24:b0:45:94:58:22:5d:
d8:bb:ab:01:fe:41:9f:b1:4d:b2:9c:c5:23:fe:28:
30:3c:bb:f1:c4:4c:02:2d:b5:80:37:6c:a8:ab:77:
ea:4e:88:14:ab:76:48:ce:db:85:7b:21:1b:c4:63:
3a:a7:6b:23:49:39:2c:72:5c:a9:c4:91:ce:3d:f7:
b5:aa:90:ee:02:5c:a7:ff:20:b1:f9:ad:a2:f8:db:
c9:39
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment, Certificate Sign
X509v3 Basic Constraints: critical
CA:TRUE
Signature Algorithm: sha256WithRSAEncryption
57:d6:57:4e:94:4f:51:ca:4e:0f:e0:c3:e6:9e:82:cb:34:1b:
b0:e2:1d:2e:4a:4d:47:13:f8:9a:58:7e:cc:ed:74:5d:b5:d3:
7b:0e:11:60:a9:9e:e5:7c:46:14:cc:69:41:4f:e7:69:c9:9f:
6d:0d:8c:ad:a5:96:91:c6:64:bf:dd:11:ee:23:74:cc:9b:f2:
23:11:4b:40:e8:c0:4c:ad:94:21:7d:66:46:82:de:1f:32:0d:
70:58:10:4c:c7:90:6e:89:f0:7e:af:bc:14:df:6c:b8:52:81:
d8:88:99:b7:29:df:75:8f:b3:da:0c:9c:b2:e7:23:66:86:7a:
c2:f6:6e:fb:c1:7f:b6:78:c9:05:aa:91:66:57:c2:e2:8b:ab:
16:d1:d7:55:ca:b5:d5:ce:11:55:dd:8b:70:6d:ce:99:8e:1d:
cd:2a:7c:b3:99:51:61:17:1e:5a:a1:98:cb:d9:28:e3:15:4b:
bc:d3:94:15:f9:95:eb:54:b8:c4:12:7b:45:67:64:48:23:5a:
7b:75:50:b4:a2:10:a2:d7:8b:d4:65:60:55:75:3c:7f:88:a2:
e3:b2:a2:3c:fd:1c:02:30:d5:9e:58:3c:dd:f8:65:cb:34:65:
68:dd:6b:90:e3:03:22:92:76:e6:85:ad:d6:66:48:c1:0e:55:
cc:31:43:31
- Serial Number: 0 (0x0)表示ca证书是第一个证书,所以序列号是0
- Signature Algorithm表示使用的是sha256的非对称加密算法
- Subject表示comment name
- X509v3 Key Usage表示证书的用途,该证书的用途是数字签名、秘钥加密、证书的签发
- CA:TRUE,表明了这个是CA的公钥证书
3.2 apiserver的私钥与公钥证书
root@K8S-Master:/etc/kubernetes/pki# openssl x509 -in apiserver.crt -noout -text
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 2627519582303443583 (0x2476d3238f945a7f)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = kubernetes
Validity
Not Before: Jan 28 07:44:21 2019 GMT
Not After : Jan 28 07:44:21 2020 GMT
Subject: CN = kube-apiserver
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (2048 bit)
Modulus:
00:9d:60:72:92:30:db:4f:5e:95:f1:19:de:ff:22:
60:e4:94:03:8c:a5:39:ad:b0:5c:3e:99:ec:87:92:
97:be:6d:22:e3:2e:b1:cf:64:35:e3:5d:90:17:33:
7f:3e:9d:d8:12:34:1b:de:7c:92:b9:33:d6:c3:bd:
9c:15:75:1c:fc:67:0f:c7:83:cb:63:56:9e:db:0a:
4e:2b:03:1e:fd:c6:dd:94:0a:20:a8:38:33:84:f3:
4d:a3:f5:44:c7:d6:53:97:b6:02:63:c7:a2:2f:a6:
3b:b4:aa:da:b2:78:47:ff:9f:ed:10:a5:c8:f7:4c:
e0:d8:b7:04:a7:87:8d:3f:0a:36:d7:70:ae:46:67:
c5:f2:01:f1:0a:7d:25:54:06:7f:84:08:99:7c:fc:
4a:d1:d7:1a:f7:b7:56:fc:41:06:be:0c:62:27:52:
f6:ff:c8:fd:a1:cc:d5:38:fc:d2:cc:36:8f:34:56:
97:60:02:8a:5f:8b:6e:a2:8e:7b:ad:87:de:ad:8d:
aa:6a:6e:7f:bd:0d:d7:ea:69:81:7a:87:7d:cc:8f:
5b:80:09:5e:e9:22:d2:c3:82:f1:c1:71:c7:ee:49:
9e:09:db:51:af:8b:8a:b6:2b:c1:e3:e6:5e:0f:69:
48:a4:d5:d5:35:e2:d0:7f:e8:0e:0a:13:d3:6f:ac:
f2:9d
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Key Usage: critical
Digital Signature, Key Encipherment
X509v3 Extended Key Usage:
TLS Web Server Authentication
X509v3 Subject Alternative Name:
DNS:k8s-master, DNS:kubernetes, DNS:kubernetes.default, DNS:kubernetes.default.svc, DNS:kubernetes.default.svc.cluster.local, IP Address:10.96.0.1, IP Address:172.28.65.239
Signature Algorithm: sha256WithRSAEncryption
ac:44:ec:00:16:2c:4c:2b:c1:2b:38:8a:06:2a:62:d0:e9:dd:
1f:9d:7d:37:e8:ea:c8:72:0e:f8:a1:a3:0c:19:e7:7f:5f:45:
34:b7:37:f8:35:b2:72:1e:86:ac:51:3d:f7:c9:40:ce:05:51:
62:c0:ee:52:d2:a9:82:af:92:79:d8:b1:83:e2:8b:e8:e6:e1:
57:b1:8f:76:cb:a1:c4:04:ce:f9:fd:cc:ec:4c:e9:fd:1e:b3:
28:f6:a0:d2:84:04:72:58:3b:86:88:89:3a:ea:4c:35:8b:1a:
2a:aa:b3:c7:a7:7b:c5:77:55:72:39:57:5d:0b:a5:51:54:c8:
00:3c:f5:84:05:76:63:45:d4:29:48:54:41:f5:f5:31:de:e2:
72:6e:09:af:51:38:76:71:16:93:bb:c6:31:1e:70:62:e1:83:
e0:e6:c3:bc:0f:1b:b2:81:4f:9e:9f:e6:07:62:fd:ad:f8:4c:
86:3a:e9:ea:bb:22:0c:d6:60:ef:c6:d5:d9:7b:00:cc:01:26:
fe:51:2d:ae:a6:a0:33:5b:0f:9a:e0:c0:25:d0:8f:5e:a5:8f:
d4:d1:84:57:6b:2b:66:24:74:e6:d9:44:19:f5:7f:51:88:94:
9e:0d:c3:c1:97:a3:cf:99:17:42:d5:88:d6:42:7b:09:5f:2d:
11:4c:db:31
- X509v3 Subject Alternative Name中的xxx表示的是我公网IP,这个证书的用于多种域名以及IP地址
- X509v3 Key Usage证书用途只有,证书签名,秘钥加密,没有签署证书的用途
3.3 apiserver访问kubelet使用的客户端私钥与证书
该证书是apiserver-kubelet-client.crt,没有什么特殊的地方,就不展示了。
3.4 services account需要的sa.key与sa.pub
- sa.key用于对account的token进行数字签名
- sa.pub是key对应的公钥文件
3.5 Etcd相关的私钥与数字证书
- 整个集群的控制中心,集群中唯一可以访问它的只有apiserver,其他都是通过apiserver的api来获取的
- 为建立apiserver与etcd之间的安全通道,会生成apiserver访问etcd公钥与私钥证书:apiserver-etcd-client.crt与apiserver-etcd-client.key
- 在etcd目录下,还有一堆证书
root@K8S-Master:/etc/kubernetes/pki# cd etcd/
root@K8S-Master:/etc/kubernetes/pki/etcd# ll
total 40
drwxr-xr-x 2 root root 4096 1月 28 15:44 ./
drwxr-xr-x 3 root root 4096 1月 28 15:44 ../
-rw-r--r-- 1 root root 1017 1月 28 15:44 ca.crt
-rw------- 1 root root 1679 1月 28 15:44 ca.key
-rw-r--r-- 1 root root 1094 1月 28 15:44 healthcheck-client.crt
-rw------- 1 root root 1675 1月 28 15:44 healthcheck-client.key
-rw-r--r-- 1 root root 1135 1月 28 15:44 peer.crt
-rw------- 1 root root 1679 1月 28 15:44 peer.key
-rw-r--r-- 1 root root 1135 1月 28 15:44 server.crt
-rw------- 1 root root 1679 1月 28 15:44 server.key
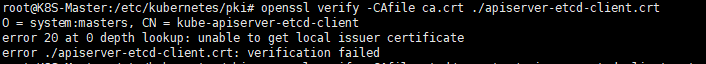
可以看到也有CA证书,那么外面的apiserver-etcd-client.crt是由那个CA证书签发的呢? 首先跟外面的对比一下
可以看到是错误的信息,说明不是由外部的CA签发的
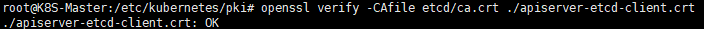
验证是不是etcd里面的签发的
说明是由etcd目录下的CA签发的
4. 生成控制平面的kubeconfig文件
生成各个控制平面的组件的文件:/etc/kubernetes/manifests
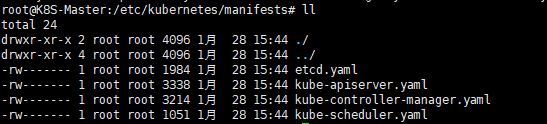
- 都是标准的yaml文件,每一个对应一个在master上的控制组件
- 跟普通组件不同的是,控制平面组件是以Static Pod形式运行的
- 静态节点Static Pod是以节点上的kubelet来管理的,不通过master节点的apiserver来管理,也不管理任何控制器
- 由kubelet自己来监控,当Static Pod崩溃的时候,kubelet会自动重启这些Pod
- 始终绑定在某个kubelet上,并且始终运行在同一节点上
- 并且kubelet会自动为每一个Static Pod在kubernetse的apiserver上创建一个镜像的pod
- 所以可以通过apiserver查询到该server,但不能管理控制它
- kubelet读取manifests目录并管理各控制平台组件的pod启动停止
5. 下载镜像,等待控制平面启动
kubeadm依赖kubelet下载镜像并启动static pod
- 从k8s.gcr.io上面下载组件镜像,我们可以从国内镜像库下载
- kubeadm会一直探测并等待localhost:6443/healthz服务返回成功
配置文件存放在manifests文件夹下的kube-apiserver.yaml中
- 这一过程之后,控制平面组件都已经启动ok了,可以通过如下命令来查看
kubectl get pods -n kube-system -o wide

6. 保存MasterConfiguration
7. 设定Master标志
8. 进行基于TLS的安全引导相关的配置
9. 安装DNS和kube-porxy插件
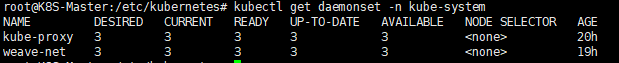
安装Addons
- 是以DaemonSet方式部署kube-proxy
查看以DaemonSet方式安装的kube-proxy
- 部署kube-dns(也可以使用CoreDNS代替)
- 安装好的DNS插件,会显示pending状态,直到cluster网络就绪,例如可以通过安装weave-net网络插件,使得DNS处于running状态