一、网络拓扑
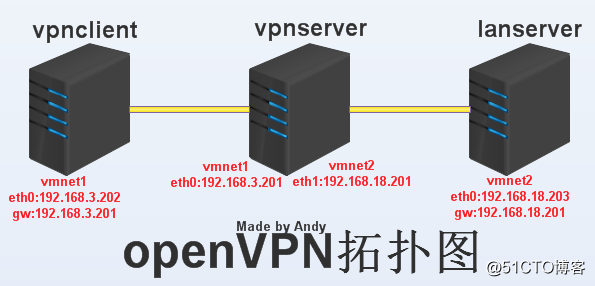
二、环境介绍
所有服务器系统均是centos6.5,内核:2.6.32-431.el6.x86_64
vpnclient:一张网卡eth0:192.168.3.202,gw:192.168.3.201,仅主机vmnet1
vpnserver:两张网卡eth0:192.168.3.201,仅主机vmnet1
eth1:192.168.18.201,仅主机vmnet2
lanserver:一张网卡eth0:192.168.18.203,gw:192.168.18.201,仅主机vmnet2
此时vpnclient(192.168.3.202) ping不通lanserver(192.168.18.203)
三、vpnserver端配置
3.1.1、基础环境配置
[root@vpnserver ~]#wget -O /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-6.repo
[root@vpnserver ~]#sed -i 's#net.ipv4.ip_forward = 0#net.ipv4.ip_forward = 1#g' /etc/sysctl.conf
[root@vpnserver ~]# sysctl -p ##开启内核转发
[root@vpnserver ~]#crontab -e ##制定计划任务校正时间
#time sync by yyc at 201712#
*/1 * * * * /usr/sbin/ntpdate ntp1.aliyun.com >/dev/null 2>&1
[root@vpnserver ~]#/etc/init.d/iptables stop ##测试完成前关掉防火墙
[root@vpnserver ~]#yum install -y lrzsz openssl* ##安装基础依赖包
3.1.2、编译安装lzo、openvpn
[root@vpnserver ~]# mkdir -p /server/tools
[root@vpnserver ~]# cd /server/tools/
[root@vpnserver tools]# rz lzo-2.09.tar.gz openvpn-2.2.2.tar.gz
[root@vpnserver tools]# tar zxvf lzo-2.09.tar.gz
[root@vpnserver tools]# cd lzo-2.09
[root@vpnserver lzo-2.09]# ./configure &&make &&make install
[root@vpnserver lzo-2.09]# mkdir /application
[root@vpnserver lzo-2.09]# cd ..
[root@vpnserver tools]# tar zxvf openvpn-2.2.2.tar.gz -C /application/
[root@vpnserver tools]# cd /application/openvpn-2.2.2
[root@vpnserver openvpn-2.2.2]# ./configure --with-lzo-lib=/usr/local/lib --with-lzo-headers=/usr/local/include &&make &&make install
[root@vpnserver openvpn-2.2.2]# ln -s /application/openvpn-2.2.2/ /application/openvpn
3.1.3、生成CA证书
[root@vpnserver openvpn-2.2.2]# cd /application/openvpn-2.2.2/easy-rsa/2.0
[root@vpnserver 2.0]# cp vars vars.bak
[root@vpnserver 2.0]# vim vars
export KEY_COUNTRY="CN"
export KEY_PROVINCE="BJ"
export KEY_CITY="BJ"
export KEY_ORG="Andy"
export KEY_EMAIL="[email protected]"
export [email protected]
export KEY_CN=Andy
export KEY_NAME=Andy
export KEY_OU=Andy
export PKCS11_MODULE_PATH=changeme
export PKCS11_PIN=1234
[root@vpnserver 2.0]# source vars
NOTE: If you run ./clean-all, I will be doing a rm -rf on /application/openvpn-2.2.2/easy-rsa/2.0/keys
[root@vpnserver 2.0]# ./clean-all
[root@vpnserver 2.0]# ls
build-ca build-key build-key-server clean-all list-crl openssl-0.9.8.cnf README vars
build-dh build-key-pass build-req inherit-inter Makefile openssl-1.0.0.cnf revoke-full whichopensslcnf
build-inter build-key-pkcs12 build-req-pas keys openssl-0.9.6.cnf pkitool sign-req
[root@vpnserver 2.0]# ll keys/
总用量 4
-rw-r--r-- 1 root root 0 4月 16 15:05 index.txt
-rw-r--r-- 1 root root 3 4月 16 15:05 serial
[root@vpnserver 2.0]# ./build-ca ##一路回车
Generating a 1024 bit RSA private key
.................................++++++
.......................++++++
writing new private key to 'ca.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BJ]:
Organization Name (eg, company) [Andy]:
Organizational Unit Name (eg, section) [Andy]:
Common Name (eg, your name or your server's hostname) [Andy]:
Name [Andy]:
Email Address [[email protected]]:
3.1.4、生成服务端证书和秘钥
[root@vpnserver 2.0]# ./build-key-server server
Generating a 1024 bit RSA private key
..++++++
......++++++
writing new private key to 'server.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BJ]:
Organization Name (eg, company) [Andy]:
Organizational Unit Name (eg, section) [Andy]:
Common Name (eg, your name or your server's hostname) [server]:
Name [Andy]:
Email Address [[email protected]]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:Andy
Using configuration from /application/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'BJ'
organizationName :PRINTABLE:'Andy'
organizationalUnitName:PRINTABLE:'Andy'
commonName :PRINTABLE:'server'
name :PRINTABLE:'Andy'
emailAddress :IA5STRING:'[email protected]'
Certificate is to be certified until Apr 13 07:12:32 2028 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
3.1.5、生成客户端证书和秘钥
生成一个无密码验证密钥,使用命令build-key,新建一个test客户端密钥,此账号无需密码验证
[root@vpnserver 2.0]# ./build-key test
Generating a 1024 bit RSA private key
...++++++
...........++++++
writing new private key to 'test.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BJ]:
Organization Name (eg, company) [Andy]:
Organizational Unit Name (eg, section) [Andy]:
Common Name (eg, your name or your server's hostname) [test]:
Name [Andy]:
Email Address [[email protected]]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:Andy
Using configuration from /application/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'BJ'
organizationName :PRINTABLE:'Andy'
organizationalUnitName:PRINTABLE:'Andy'
commonName :PRINTABLE:'test'
name :PRINTABLE:'Andy'
emailAddress :IA5STRING:'[email protected]'
Certificate is to be certified until Apr 13 07:16:39 2028 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
生成一个需要密码验证的客户端密钥Andy,密码为123456,生产环境此密码需要设置较复杂
[root@vpnserver 2.0]# ./build-key-pass Andy
Generating a 1024 bit RSA private key
..++++++
...............++++++
writing new private key to 'Andy.key'
Enter PEM pass phrase:123456
Verifying - Enter PEM pass phrase:123456
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [CN]:
State or Province Name (full name) [BJ]:
Locality Name (eg, city) [BJ]:
Organization Name (eg, company) [Andy]:
Organizational Unit Name (eg, section) [Andy]:
Common Name (eg, your name or your server's hostname) [Andy]:
Name [Andy]:
Email Address [[email protected]]:
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:123456
An optional company name []:Andy
Using configuration from /application/openvpn-2.2.2/easy-rsa/2.0/openssl-1.0.0.cnf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :PRINTABLE:'BJ'
localityName :PRINTABLE:'BJ'
organizationName :PRINTABLE:'Andy'
organizationalUnitName:PRINTABLE:'Andy'
commonName :PRINTABLE:'Andy'
name :PRINTABLE:'Andy'
emailAddress :IA5STRING:'[email protected]'
Certificate is to be certified until Apr 13 07:21:29 2028 GMT (3650 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
3.1.6、生成密码协议交换文件
[root@vpnserver 2.0]# ./build-dh
Generating DH parameters, 1024 bit long safe prime, generator 2
This is going to take a long time
.......................+.......................+...................+...................................................+..........++*++*++*
[root@vpnserver 2.0]# ll keys/dh1024.pem
-rw-r--r-- 1 root root 245 4月 16 15:23 keys/dh1024.pem
3.1.7、生成防攻击key文件
[root@vpnserver 2.0]# openvpn --genkey --secret keys/ta.key
[root@vpnserver 2.0]# ll keys/ta.key
-rw------- 1 root root 636 4月 16 15:26 keys/ta.key
3.2、编辑服务端配置文件
[root@vpnserver 2.0]# mkdir -p /etc/openvpn
[root@vpnserver 2.0]# cd /etc/openvpn/
[root@vpnserver openvpn]# cp -ap /application/openvpn/easy-rsa/2.0/keys .
[root@vpnserver openvpn]# ll
总用量 4
drwx------ 2 root root 4096 4月 16 15:26 keys
[root@vpnserver openvpn]# cp /application/openvpn/sample-config-files/server.conf server.bak
[root@vpnserver openvpn]# ll
总用量 16
drwx------ 2 root root 4096 4月 16 15:26 keys
-rw-r--r-- 1 root root 10288 4月 16 15:38 server.bak
[root@vpnserver openvpn]# egrep -v '#|;|^$' server.bak >server.conf
[root@vpnserver openvpn]# ll
总用量 20
drwx------ 2 root root 4096 4月 16 15:26 keys
-rw-r--r-- 1 root root 10288 4月 16 15:38 server.bak
-rw-r--r-- 1 root root 211 4月 16 15:39 server.conf
[root@vpnserver openvpn]# vim server.conf
local 192.168.3.201
port 1195
proto tcp
dev tun
ca /etc/openvpn/keys/ca.crt
cert /etc/openvpn/keys/server.crt
dh /etc/openvpn/keys/dh1024.pem
server 10.8.0.0 255.255.255.0
push "route 192.168.18.0 255.255.255.0"
ifconfig-pool-persist ipp.txt
keepalive 10 120
comp-lzo
persist-key
persist-tun
status openvpn-status.log
log /var/log/openvpn.log
duplicate-cn
client-to-client
verb 3
3.3、启动服务端
3.3.1 启动服务端
[root@vpnserver openvpn]# /usr/local/sbin/openvpn --config /etc/openvpn/server.conf &
[1] 28429
[root@vpnserver openvpn]# ps -ef|grep openvpn
root 28429 3086 2 16:30 pts/0 00:00:00 /usr/local/sbin/openvpn --config /etc/openvpn/server.conf
root 28487 3086 0 16:30 pts/0 00:00:00 grep openvpn
3.3.2、将OpenVPN加入开机自启动
方法一:将启动命令加入到/etc/rc.local
echo “/usr/local/sbin/openvpn --config /etc/openvpn/server.conf>/dev/null &”>>/etc/rc.local
方法二:利用sample-scripts下面的脚本
cp /application/openvpn/sample-scripts/openvpn.init /etc/init.d/openvpn
chkconfig openvpn on
chkconfig --list openvpn
openvpn 0:off 1:off 2:on 3:on 4:on 5:on 6:off
四、linux客户端安装与配置
4.1、基础环境配置
linux客户端软件的安装与服务端软件安装过程一样,也是需要先安装lzo,然后源码编译openvpn2.2.2
[root@vpnclient ~]# wget -O /etc/yum.repos.d/epel.repo http://mirrors.aliyun.com/repo/epel-6.repo
[root@vpnserver ~]#sed -i 's#net.ipv4.ip_forward = 0#net.ipv4.ip_forward = 1#g' /etc/sysctl.conf
[root@vpnserver ~]# sysctl -p ##开启内核转发
[root@vpnserver ~]#crontab -e ##制定计划任务校正时间
#time sync by yyc at 201712#
*/1 * * * * /usr/sbin/ntpdate ntp1.aliyun.com >/dev/null 2>&1
[root@vpnserver ~]#/etc/init.d/iptables stop ##测试完成前关掉防火墙
[root@vpnserver ~]#yum install -y lrzsz openssl* ##安装基础依赖包
4.2、编译安装lzo、openvpn
[root@vpnclient ~]# mkdir -p /server/tools
[root@vpnclient ~]# cd /server/tools/
[root@vpnclient tools]# rz lzo-2.09.tar.gz openvpn-2.2.2.tar.gz
[root@vpnclient tools]# tar zxvf lzo-2.09.tar.gz
[root@vpnclient tools]# cd lzo-2.09
[root@vpnclient lzo-2.09]# ./configure &&make &&make install
[root@vpnclient lzo-2.09]# cd ..
[root@vpnclient tools]# mkdir /application
[root@vpnclient tools]# tar zxvf openvpn-2.2.2.tar.gz -C /application/
[root@vpnclient tools]# cd /application/openvpn-2.2.2/
[root@vpnclient openvpn-2.2.2]# ./configure --with-lzo-lib=/usr/local/lib --with-lzo-headers=/usr/local/include&& make &&make install
[root@vpnclient openvpn-2.2.2]# ln -s /application/openvpn-2.2.2 /application/openvpn
[root@vpnclient openvpn-2.2.2]# cd ..
[root@vpnclient application]# ll
总用量 12
lrwxrwxrwx 1 root root 26 4月 16 17:10 openvpn -> /application/openvpn-2.2.2
drwxrwxr-x 17 oldboy oldboy 12288 4月 16 17:09 openvpn-2.2.2
4.3、编辑客户端配置文件
新建配置文件目录/etc/openvpn
[root@vpnclient application]# mkdir /etc/openvpn
[root@vpnclient application]# cd /etc/openvpn/
[root@vpnclient openvpn]# rz ca.crt server.conf test.crt test.key
[root@vpnclient openvpn]# mv server.conf client.conf
[root@vpnclient openvpn]# vim client.conf
[root@vpnclient openvpn]# cat client.conf
client
dev tun
proto tcp
remote 192.168.3.201 1195
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert test.crt
key test.key
ns-cert-type server
comp-lzo
verb 3
4.4、远程拔入vpn
[root@vpnclient openvpn]# /usr/local/sbin/openvpn --config /etc/openvpn/client.conf &
[1] 1071
[root@vpnclient openvpn]# Mon Apr 16 17:28:14 2018 OpenVPN 2.2.2 x86_64-unknown-linux-gnu [SSL] [LZO2] [EPOLL] [eurephia] built on Apr 16 2018
Mon Apr 16 17:28:14 2018 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables
Mon Apr 16 17:28:14 2018 WARNING: file 'test.key' is group or others accessible
Mon Apr 16 17:28:14 2018 LZO compression initialized
Mon Apr 16 17:28:14 2018 Control Channel MTU parms [ L:1544 D:140 EF:40 EB:0 ET:0 EL:0 ]
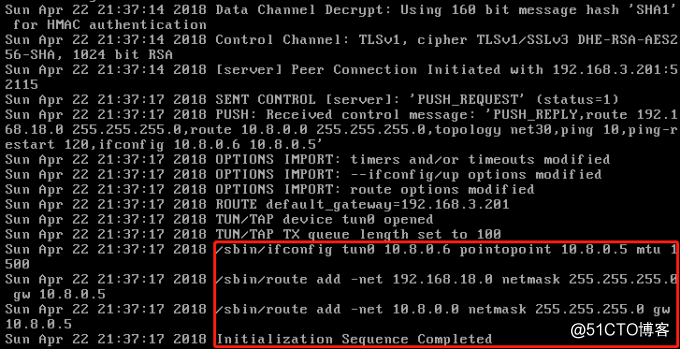
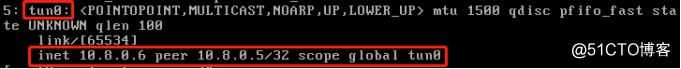
若是带密码认证的用户,以Andy为例,将Andy.crt,Andy.key,Andy.ovpn上传至/etc/openvpn,Andy.ovpn的内容如下:
client
dev tun
proto tcp
remote 192.168.3.204 1195
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert sunny.crt
key sunny.key
ns-cert-type server
comp-lzo
verb 3
在/etc/openvpn下新建密码文件pass.txt
[root@vpnclient openvpn]# vim pass.txt
[root@vpnclient openvpn]# cat pass.txt
123456
[root@vpnclient openvpn]# chmod 400 pass.txt
启动客户端
[root@vpnclient openvpn]#openvpn--config /etc/openvpn/sunny.ovpn --askpass /etc/openvpn/pass.txt &
echo ‘openvpn --config /etc/openvpn/sunny.ovpn --askpass/etc/openvpn/pass.txt >/dev/null &’>>/etc/rc.local#开机自启
五、测试连通性
在vpnclient端ping
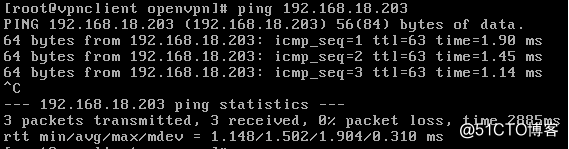
在lanserver端抓包显示
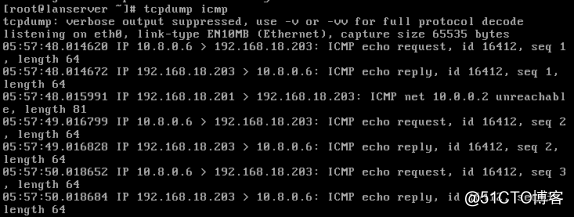
参考:
https://openvpn.net/index.php/open-source/documentation.html
http://blog.51cto.com/francis198/1830639