一、什么是Wpscan?什么是Wordpres?
1.Wpscan
WPScan是一个扫描WordPress漏洞的黑盒子扫描器,可以扫描出wordpress的版本,主题,插件,后台用户以及爆破后台用户密码等。
2.Wordpress
WordPress是一种使用PHP语言和MySQL数据库开发的博客平台,用户可以在支持PHP和MySQL数据库的服务器上架设属于自己的网站。也可以把 WordPress当作一个内容管理系统(CMS)来使用。WordPress有许多第三方开发的免费模板,安装方式简单易用。
二、Wordpress系统的搭建
1.下载Wordpress
TURNKEYLINUX是linux一站式软件站,在浏览器地址栏输入 https://www.turnkeylinux.org/ 访问官网下载Wordpress

点击Wordpress进入下载页

这里显示不同版本的系统类型,VM可直接导入VM虚拟机进行安装,此处我们考虑下载文件大小选择 v 14.2 ISO版本
使用Wordpress ios 光盘镜像新建一个WordPress虚拟机,并启动虚拟机显示如下图
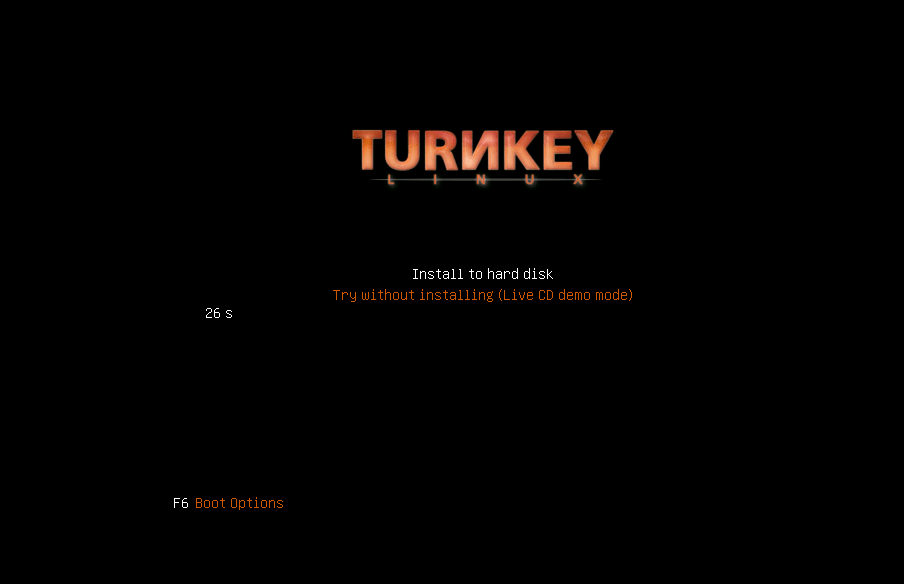
选择 Install to hard disk (选择安装到虚拟机硬盘) 按回车键显示如下图
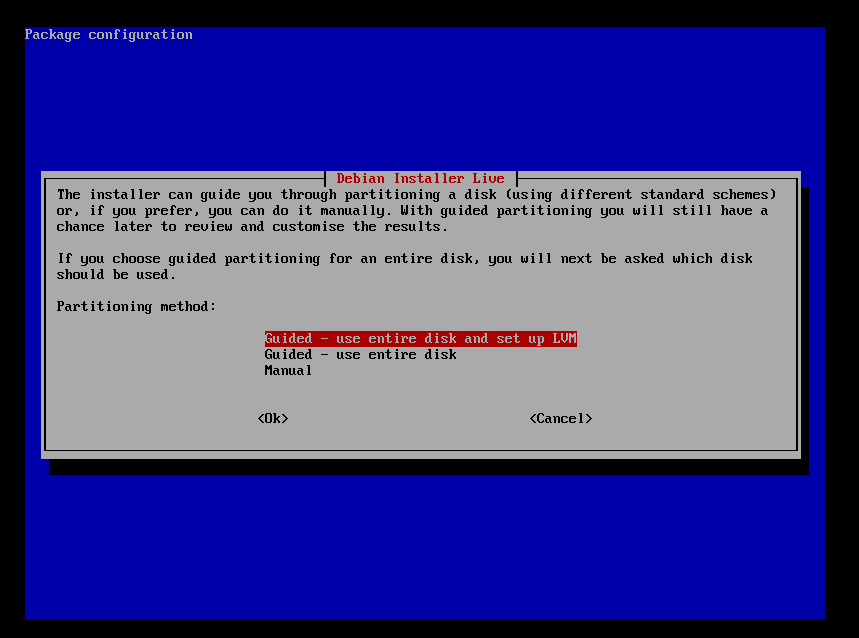
分区方式选择
1使用整个磁盘并设置为LVM
2使用整个磁盘
3手动分区
此处我们选择第一项出现如下图所示
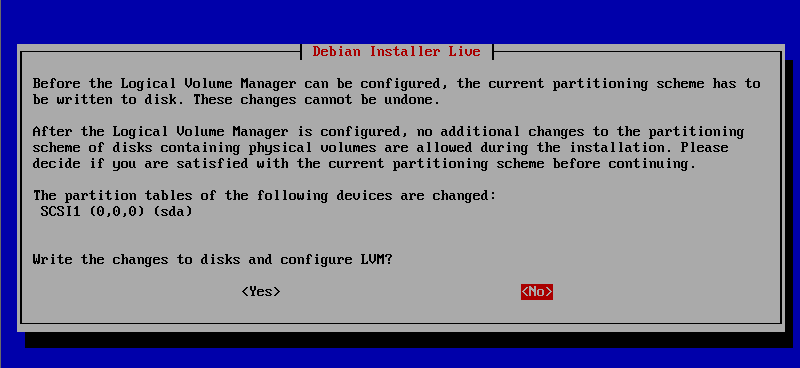
提示是否改变磁盘并设置为LVM,此处选择yes出现如下图所示

显示LVM配置信息,选择OK出现如下图所示
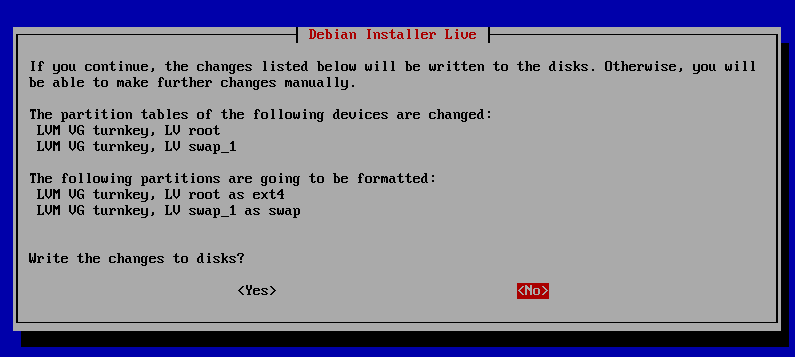
该界面显示磁盘分区信息,提示是否向磁盘写入数据,选择yes出现如下图界面
安装GRUB引导,选择yes出现如下界面
该界面提示Wordpress 已经安装完成,是否需要重新启动,此处选择yes出现如下所示界面
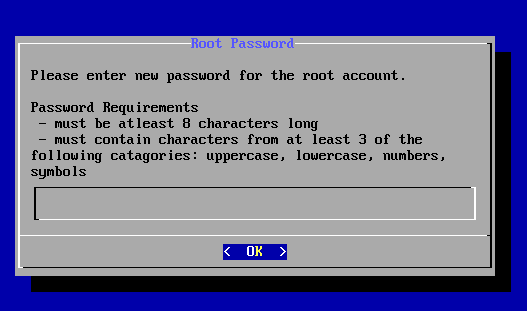
为root用户设置一个新密码,密码长度8位,由大写字母,小写字母,数字,符号至少三种组成
输入密码后回车
再次输入密码后回车出现如下图所示界面
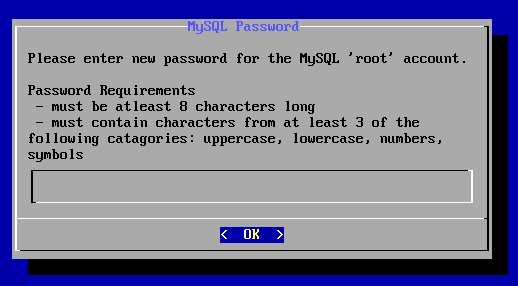
为MySQL服务的root用户输入新密码
输入密码后回车确认显示如下图所示界面
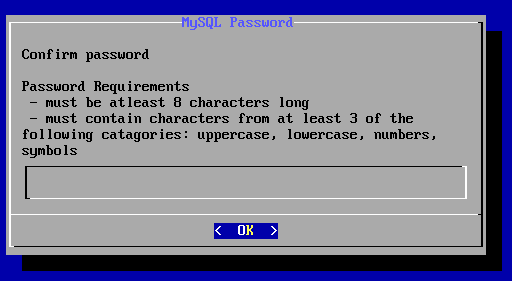
再次输入密码回车后出现如下所示界面
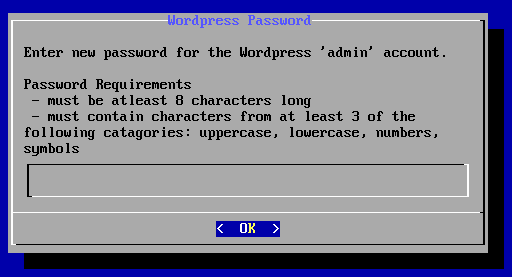
为WordPress系统的用户admin设置一个密码
输入密码后回车确认显示如下图所示界面
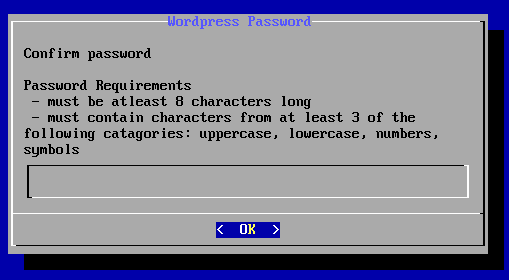
再次输入密码出现如下图所示界面
提示为admin设置邮件地址,这里默认就好,点击apply应用
显示Hub初始化服务信息,选择Skip跳过出现如下图所示界面
输入信息反馈邮箱,此跳过处默认即可,选择Skip出现如下界面
提示是否安装更新,选择Install出现如下界面
内核工具更新,此处选择REboot后出现如下界面
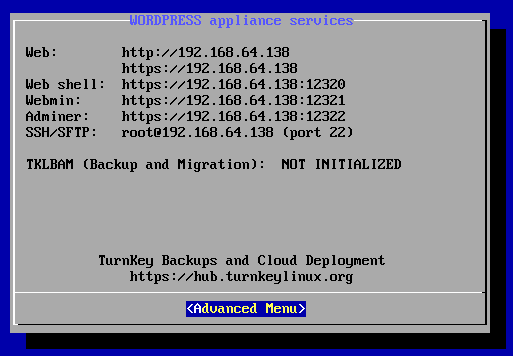
该界面显示了Wordpress应用服务的详细信息,如Web地址,Webshell地址,Webmin地址,PHPMyAdmin的地址和端口号以及SSH/SFTP地址和端口号。
出现此界面表明WordPress Turnkey Linux 搭建完成,可以使用。
三、使用Wpscsn对WordPress进行漏洞扫描
利用 “wpscan -h”命令,可查看Wpscan的版本,常用选项,功能介绍,例程等;
1 root@kali:~# wpscan -h 2 _______________________________________________________________ 3 __ _______ _____ 4 \ \ / / __ \ / ____| 5 \ \ /\ / /| |__) | (___ ___ __ _ _ __ 6 \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ 7 \ /\ / | | ____) | (__| (_| | | | | 8 \/ \/ |_| |_____/ \___|\__,_|_| |_| 9 10 WordPress Security Scanner by the WPScan Team 11 Version 2.9.1 //Wpscan版本信息 12 Sponsored by Sucuri - https://sucuri.net 13 @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ 14 _______________________________________________________________ 15 16 Help : 17 18 Some values are settable in a config file, see the example.conf.json 19 20 --update Update the database to the latest version.
#更新命令 命令“root@kali:~# wpscan --update”
21 --url | -u <target url> The WordPress URL/domain to scan.
#指定URL/域进行扫描 命令“root@kali:~# wpscan --url 地址”或“root@kali:~# wpscan -u 地址”
22 --force | -f Forces WPScan to not check if the remote site is running WordPress.
#强制Wpscan不检查远程正在运行WordPress的主机
23 --enumerate | -
24 option : 25 u usernames from id 1 to 10
#默认用户1-用户10 26 u[10-20] usernames from id 10 to 20 (you must write [] chars)
#默认用户10-20([]中字符必须写)
27 p plugins
#插件程序
28 vp only vulnerable plugins
#仅漏洞插件程序
29 ap all plugins (can take a long time)
#所有插件程序(耗时比较长)
30 tt timthumbs
#小号
31 t themes#主题
32 vt only vulnerable themes
#仅漏洞主题
33 at all themes (can take a long time)
#所有主题
34 Multiple values are allowed : "-e tt,p" will enumerate timthumbs and plugi
#多值参数
35 If no option is supplied, the default is "vt,tt,u,vp" 无参默认 37 --exclude-content-based "<regexp or string>" 38 Used with the enumeration option, will exclude all occurrences based on the regexp or string supplied. 39 You do not need to provide the regexp delimiters, but you must write the quotes (simple or double). 40 --config-file | -c <config file> Use the specified config file, see the example.conf.json.
配置文佳 41 --user-agent | -a <User-Agent> Use the specified User-Agent.
指定用户代理 42 --cookie <String> String to read cookies from.
cookie字符串读取 43 --random-agent | -r Use a random User-Agent.
代理 44 --follow-redirection If the target url has a redirection, it will be followed without asking if you wanted to do so or not
跟踪重定向目标网址 45 --batch Never ask for user input, use the default behaviour.
不请求用户输入使用默认 46 --no-color Do not use colors in the output.
不在输出中使用颜色 47 --wp-content-dir <wp content dir> WPScan try to find the content directory (ie wp-content) by scanning the index page, however you can specified it. 48 Subdirectories are allowed. WPScan尝试通过扫描索引页面来查找内容目录(即wp-content),但是您可以指定它。允许使用子目录。
49 --wp-plugins-dir <wp plugins dir> Same thing than --wp-content-dir but for the plugins directory. 50 If not supplied, WPScan will use wp-content-dir/plugins. Subdirectories are allowed ame比--wp-content-dir但是对于plugins目录。 如果没有提供,WPScan将使用wp-content-dir / plugins。 允许子目录
51 --proxy <[protocol://]host:port> Supply a proxy. HTTP, SOCKS4 SOCKS4A and SOCKS5 are supported. 52 If no protocol is given (format host:port), HTTP will be used.
53 --proxy-auth <username:password> Supply the proxy login credentials. 提供代理登陆凭证
54 --basic-auth <username:password> Set the HTTP Basic authentication.
设置HTTP基本认证
55 --wordlist | -w <wordlist> Supply a wordlist for the password brute forcer.
为暴力密码破解指定密码字典
56 --username | -U <username> Only brute force the supplied username.
指定暴力破解用户 57 --usernames <path-to-file> Only brute force the usernames from the file. 仅从密码字典中暴力破解用户名
58 --threads | -t <number of threads> The number of threads to use when multi-threading requests.
多线程指定线程数
59 --cache-ttl <cache-ttl> Typhoeus cache TTL. 60 --request-timeout <request-timeout> Request Timeout. 请求时间间隔
61 --connect-timeout <connect-timeout> Connect Timeout. 连接时间间隔
62 --max-threads <max-threads> Maximum Threads. 最大线程数
63 --throttle <milliseconds> Milliseconds to wait before doing another web request. If used, the --threads should be set to 1.
在执行另一个Web请求之前等待的毫秒数。 如果使用,则--threads应设置为1。 64 --help | -h This help screen. 65 --verbose | -v Verbose output. 66 --version Output the current version and exit. 67 68 69 Examples : 70 帮助 71 -Further help ... 72 ruby ./wpscan.rb --help
73 做“非侵入性”检查 74 -Do 'non-intrusive' checks ... 75 ruby ./wpscan.rb --url www.example.com
76 使用50个线程对枚举的用户做单词列表密码蛮力… 77 -Do wordlist password brute force on enumerated users using 50 threads ... 78 ruby ./wpscan.rb --url www.example.com --wordlist darkc0de.lst --threads 50
79 做单词表密码蛮力上的“管理员”用户名只… 80 -Do wordlist password brute force on the 'admin' username only ... 81 ruby ./wpscan.rb --url www.example.com --wordlist darkc0de.lst --username admin
82 枚举安装的插件… 83 -Enumerate installed plugins ... 84 ruby ./wpscan.rb --url www.example.com --enumerate p
85 枚举安装的主题 86 -Enumerate installed themes ... 87 ruby ./wpscan.rb --url www.example.com --enumerate t
88 枚举用户 89 -Enumerate users ... 90 ruby ./wpscan.rb --url www.example.com --enumerate u
91 枚举安装的TimTrBBS 92 -Enumerate installed timthumbs ... 93 ruby ./wpscan.rb --url www.example.com --enumerate tt
94 使用HTTP代理 95 -Use a HTTP proxy ... 96 ruby ./wpscan.rb --url www.example.com --proxy 127.0.0.1:8118
97 使用SoCKS5代理 98 -Use a SOCKS5 proxy ... (cURL >= v7.21.7 needed) 99 ruby ./wpscan.rb --url www.example.com --proxy socks5://127.0.0.1:9000
100 使用自定义内容目录 101 -Use custom content directory ... 102 ruby ./wpscan.rb -u www.example.com --wp-content-dir custom-content
103 使用自定义插件目录 104 -Use custom plugins directory ... 105 ruby ./wpscan.rb -u www.example.com --wp-plugins-dir wp-content/custom-plugins 106 更新数据库 107 -Update the DB ... 108 ruby ./wpscan.rb --update 109 调试输出 110 -Debug output ... 111 ruby ./wpscan.rb --url www.example.com --debug-output 2>debug.log 112 113 See README for further information.
wpscan -u 192.168.64.138 /wpscan --url 192.168.64.138
1 root@kali:~# wpscan -u 192.168.64.138 2 _______________________________________________________________ 3 __ _______ _____ 4 \ \ / / __ \ / ____| 5 \ \ /\ / /| |__) | (___ ___ __ _ _ __ 6 \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ 7 \ /\ / | | ____) | (__| (_| | | | | 8 \/ \/ |_| |_____/ \___|\__,_|_| |_| 9 10 WordPress Security Scanner by the WPScan Team 11 Version 2.9.1 12 Sponsored by Sucuri - https://sucuri.net 13 @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ 14 _______________________________________________________________ 15 16 [+] URL: http://192.168.64.138/ 17 [+] Started: Fri Aug 17 23:20:05 2018 18 19 [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number 20 [+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/" 21 [+] Interesting header: SERVER: Apache 22 [+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php 23 24 [+] WordPress version 4.7.4 identified from advanced fingerprinting (Released on 2017-04-20) 25 [!] 25 vulnerabilities identified from the version number 26 27 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset 28 Reference: https://wpvulndb.com/vulnerabilities/8807 29 Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html 30 Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html 31 Reference: https://core.trac.wordpress.org/ticket/25239 32 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 33 34 [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation 35 Reference: https://wpvulndb.com/vulnerabilities/8815 36 Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11 37 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 38 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066 39 [i] Fixed in: 4.7.5 40 41 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC 42 Reference: https://wpvulndb.com/vulnerabilities/8816 43 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 44 Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381 45 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062 46 [i] Fixed in: 4.7.5 47 48 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks 49 Reference: https://wpvulndb.com/vulnerabilities/8817 50 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 51 Reference: https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4 52 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065 53 [i] Fixed in: 4.7.5 54 55 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF 56 Reference: https://wpvulndb.com/vulnerabilities/8818 57 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 58 Reference: https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67 59 Reference: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html 60 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064 61 [i] Fixed in: 4.7.5 62 63 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS 64 Reference: https://wpvulndb.com/vulnerabilities/8819 65 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 66 Reference: https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6 67 Reference: https://hackerone.com/reports/203515 68 Reference: https://hackerone.com/reports/203515 69 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061 70 [i] Fixed in: 4.7.5 71 72 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF 73 Reference: https://wpvulndb.com/vulnerabilities/8820 74 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 75 Reference: https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3 76 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063 77 [i] Fixed in: 4.7.5 78 79 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection 80 Reference: https://wpvulndb.com/vulnerabilities/8905 81 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 82 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 83 Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec 84 [i] Fixed in: 4.7.6 85 86 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection 87 Reference: https://wpvulndb.com/vulnerabilities/8906 88 Reference: https://medium.com/websec/wordpress-sqli-bbb2afcc8e94 89 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 90 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 91 Reference: https://wpvulndb.com/vulnerabilities/8905 92 [i] Fixed in: 4.7.5 93 94 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect 95 Reference: https://wpvulndb.com/vulnerabilities/8910 96 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 97 Reference: https://core.trac.wordpress.org/changeset/41398 98 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725 99 [i] Fixed in: 4.7.6 100 101 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping 102 Reference: https://wpvulndb.com/vulnerabilities/8911 103 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 104 Reference: https://core.trac.wordpress.org/changeset/41457 105 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719 106 [i] Fixed in: 4.7.6 107 108 [!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer 109 Reference: https://wpvulndb.com/vulnerabilities/8912 110 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 111 Reference: https://core.trac.wordpress.org/changeset/41397 112 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722 113 [i] Fixed in: 4.7.6 114 115 [!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed 116 Reference: https://wpvulndb.com/vulnerabilities/8913 117 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 118 Reference: https://core.trac.wordpress.org/changeset/41448 119 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724 120 [i] Fixed in: 4.7.6 121 122 [!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor 123 Reference: https://wpvulndb.com/vulnerabilities/8914 124 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 125 Reference: https://core.trac.wordpress.org/changeset/41395 126 Reference: https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html 127 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726 128 [i] Fixed in: 4.7.6 129 130 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness 131 Reference: https://wpvulndb.com/vulnerabilities/8941 132 Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/ 133 Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d 134 Reference: https://twitter.com/ircmaxell/status/923662170092638208 135 Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html 136 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510 137 [i] Fixed in: 4.7.7 138 139 [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload 140 Reference: https://wpvulndb.com/vulnerabilities/8966 141 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 142 Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509 143 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092 144 [i] Fixed in: 4.7.8 145 146 [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping 147 Reference: https://wpvulndb.com/vulnerabilities/8967 148 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 149 Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de 150 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094 151 [i] Fixed in: 4.7.8 152 153 [!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping 154 Reference: https://wpvulndb.com/vulnerabilities/8968 155 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 156 Reference: https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a 157 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093 158 [i] Fixed in: 4.7.8 159 160 [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing 161 Reference: https://wpvulndb.com/vulnerabilities/8969 162 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 163 Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c 164 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091 165 [i] Fixed in: 4.7.8 166 167 [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS) 168 Reference: https://wpvulndb.com/vulnerabilities/9006 169 Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850 170 Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/ 171 Reference: https://core.trac.wordpress.org/ticket/42720 172 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776 173 [i] Fixed in: 4.7.9 174 175 [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched) 176 Reference: https://wpvulndb.com/vulnerabilities/9021 177 Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html 178 Reference: https://github.com/quitten/doser.py 179 Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html 180 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389 181 182 [!] Title: WordPress 3.7-4.9.4 - Remove localhost Default 183 Reference: https://wpvulndb.com/vulnerabilities/9053 184 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 185 Reference: https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216 186 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101 187 [i] Fixed in: 4.7.10 188 189 [!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login 190 Reference: https://wpvulndb.com/vulnerabilities/9054 191 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 192 Reference: https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e 193 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100 194 [i] Fixed in: 4.7.10 195 196 [!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag 197 Reference: https://wpvulndb.com/vulnerabilities/9055 198 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 199 Reference: https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d 200 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102 201 [i] Fixed in: 4.7.10 202 203 [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion 204 Reference: https://wpvulndb.com/vulnerabilities/9100 205 Reference: https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/ 206 Reference: http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/ 207 Reference: https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd 208 Reference: https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/ 209 Reference: https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/ 210 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895 211 [i] Fixed in: 4.7.11 212 213 [+] WordPress theme in use: twentyseventeen - v1.2 214 215 [+] Name: twentyseventeen - v1.2 216 | Location: http://192.168.64.138/wp-content/themes/twentyseventeen/ 217 | Readme: http://192.168.64.138/wp-content/themes/twentyseventeen/README.txt 218 [!] The version is out of date, the latest version is 1.7 219 | Style URL: http://192.168.64.138/wp-content/themes/twentyseventeen/style.css 220 | Theme Name: Twenty Seventeen 221 | Theme URI: https://wordpress.org/themes/twentyseventeen/ 222 | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a... 223 | Author: the WordPress team 224 | Author URI: https://wordpress.org/ 225 226 [+] Enumerating plugins from passive detection ... 227 | 1 plugin found: 228 229 [+] Name: wp-super-cache 230 | Latest version: 1.6.3 231 | Location: http://192.168.64.138/wp-content/plugins/wp-super-cache/ 232 233 [!] We could not determine a version so all vulnerabilities are printed out 234 235 [!] Title: WP-Super-Cache 1.3 - Remote Code Execution 236 Reference: https://wpvulndb.com/vulnerabilities/6623 237 Reference: http://www.acunetix.com/blog/web-security-zone/wp-plugins-remote-code-execution/ 238 Reference: http://wordpress.org/support/topic/pwn3d 239 Reference: http://blog.sucuri.net/2013/04/update-wp-super-cache-and-w3tc-immediately-remote-code-execution-vulnerability-disclosed.html 240 [i] Fixed in: 1.3.1 241 242 [!] Title: WP Super Cache 1.3 - trunk/wp-cache.php wp_nonce_url Function URI XSS 243 Reference: https://wpvulndb.com/vulnerabilities/6624 244 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 245 [i] Fixed in: 1.3.1 246 247 [!] Title: WP Super Cache 1.3 - trunk/plugins/wptouch.php URI XSS 248 Reference: https://wpvulndb.com/vulnerabilities/6625 249 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 250 [i] Fixed in: 1.3.1 251 252 [!] Title: WP Super Cache 1.3 - trunk/plugins/searchengine.php URI XSS 253 Reference: https://wpvulndb.com/vulnerabilities/6626 254 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 255 [i] Fixed in: 1.3.1 256 257 [!] Title: WP Super Cache 1.3 - trunk/plugins/domain-mapping.php URI XSS 258 Reference: https://wpvulndb.com/vulnerabilities/6627 259 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 260 [i] Fixed in: 1.3.1 261 262 [!] Title: WP Super Cache 1.3 - trunk/plugins/badbehaviour.php URI XSS 263 Reference: https://wpvulndb.com/vulnerabilities/6628 264 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 265 [i] Fixed in: 1.3.1 266 267 [!] Title: WP Super Cache 1.3 - trunk/plugins/awaitingmoderation.php URI XSS 268 Reference: https://wpvulndb.com/vulnerabilities/6629 269 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 270 [i] Fixed in: 1.3.1 271 272 [!] Title: WP Super Cache <= 1.4.2 - Stored Cross-Site Scripting (XSS) 273 Reference: https://wpvulndb.com/vulnerabilities/7889 274 Reference: http://blog.sucuri.net/2015/04/security-advisory-persistent-xss-in-wp-super-cache.html 275 [i] Fixed in: 1.4.3 276 277 [!] Title: WP Super Cache <= 1.4.4 - Cross-Site Scripting (XSS) 278 Reference: https://wpvulndb.com/vulnerabilities/8197 279 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 280 [i] Fixed in: 1.4.5 281 282 [!] Title: WP Super Cache <= 1.4.4 - PHP Object Injection 283 Reference: https://wpvulndb.com/vulnerabilities/8198 284 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 285 [i] Fixed in: 1.4.5 286 287 [+] Finished: Fri Aug 17 23:20:10 2018 288 [+] Requests Done: 50 289 [+] Memory used: 50.062 MB 290 [+] Elapsed time: 00:00:04
wpscan -u 192.168.64.138 -e u vp
命令详解 -e使用枚举方式 u 扫描ID1-ID10 vp扫描漏洞插件
1 root@kali:~# wpscan -u 192.168.64.138 -e u vp 2 _______________________________________________________________ 3 __ _______ _____ 4 \ \ / / __ \ / ____| 5 \ \ /\ / /| |__) | (___ ___ __ _ _ __ 6 \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ 7 \ /\ / | | ____) | (__| (_| | | | | 8 \/ \/ |_| |_____/ \___|\__,_|_| |_| 9 10 WordPress Security Scanner by the WPScan Team 11 Version 2.9.1 12 Sponsored by Sucuri - https://sucuri.net 13 @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ 14 _______________________________________________________________ 15 16 [+] URL: http://192.168.64.138/ 17 [+] Started: Fri Aug 17 23:30:12 2018 18 19 [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number 20 [+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/" 21 [+] Interesting header: SERVER: Apache 22 [+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php 23 24 [+] WordPress version 4.7.4 identified from advanced fingerprinting (Released on 2017-04-20) 25 [!] 25 vulnerabilities identified from the version number 26 27 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset 28 Reference: https://wpvulndb.com/vulnerabilities/8807 29 Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html 30 Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html 31 Reference: https://core.trac.wordpress.org/ticket/25239 32 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 33 34 [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation 35 Reference: https://wpvulndb.com/vulnerabilities/8815 36 Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11 37 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 38 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066 39 [i] Fixed in: 4.7.5 40 41 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC 42 Reference: https://wpvulndb.com/vulnerabilities/8816 43 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 44 Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381 45 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062 46 [i] Fixed in: 4.7.5 47 48 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks 49 Reference: https://wpvulndb.com/vulnerabilities/8817 50 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 51 Reference: https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4 52 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065 53 [i] Fixed in: 4.7.5 54 55 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF 56 Reference: https://wpvulndb.com/vulnerabilities/8818 57 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 58 Reference: https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67 59 Reference: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html 60 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064 61 [i] Fixed in: 4.7.5 62 63 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS 64 Reference: https://wpvulndb.com/vulnerabilities/8819 65 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 66 Reference: https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6 67 Reference: https://hackerone.com/reports/203515 68 Reference: https://hackerone.com/reports/203515 69 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061 70 [i] Fixed in: 4.7.5 71 72 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF 73 Reference: https://wpvulndb.com/vulnerabilities/8820 74 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 75 Reference: https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3 76 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063 77 [i] Fixed in: 4.7.5 78 79 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection 80 Reference: https://wpvulndb.com/vulnerabilities/8905 81 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 82 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 83 Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec 84 [i] Fixed in: 4.7.6 85 86 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection 87 Reference: https://wpvulndb.com/vulnerabilities/8906 88 Reference: https://medium.com/websec/wordpress-sqli-bbb2afcc8e94 89 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 90 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 91 Reference: https://wpvulndb.com/vulnerabilities/8905 92 [i] Fixed in: 4.7.5 93 94 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect 95 Reference: https://wpvulndb.com/vulnerabilities/8910 96 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 97 Reference: https://core.trac.wordpress.org/changeset/41398 98 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725 99 [i] Fixed in: 4.7.6 100 101 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping 102 Reference: https://wpvulndb.com/vulnerabilities/8911 103 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 104 Reference: https://core.trac.wordpress.org/changeset/41457 105 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719 106 [i] Fixed in: 4.7.6 107 108 [!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer 109 Reference: https://wpvulndb.com/vulnerabilities/8912 110 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 111 Reference: https://core.trac.wordpress.org/changeset/41397 112 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722 113 [i] Fixed in: 4.7.6 114 115 [!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed 116 Reference: https://wpvulndb.com/vulnerabilities/8913 117 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 118 Reference: https://core.trac.wordpress.org/changeset/41448 119 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724 120 [i] Fixed in: 4.7.6 121 122 [!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor 123 Reference: https://wpvulndb.com/vulnerabilities/8914 124 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 125 Reference: https://core.trac.wordpress.org/changeset/41395 126 Reference: https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html 127 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726 128 [i] Fixed in: 4.7.6 129 130 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness 131 Reference: https://wpvulndb.com/vulnerabilities/8941 132 Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/ 133 Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d 134 Reference: https://twitter.com/ircmaxell/status/923662170092638208 135 Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html 136 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510 137 [i] Fixed in: 4.7.7 138 139 [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload 140 Reference: https://wpvulndb.com/vulnerabilities/8966 141 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 142 Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509 143 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092 144 [i] Fixed in: 4.7.8 145 146 [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping 147 Reference: https://wpvulndb.com/vulnerabilities/8967 148 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 149 Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de 150 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094 151 [i] Fixed in: 4.7.8 152 153 [!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping 154 Reference: https://wpvulndb.com/vulnerabilities/8968 155 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 156 Reference: https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a 157 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093 158 [i] Fixed in: 4.7.8 159 160 [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing 161 Reference: https://wpvulndb.com/vulnerabilities/8969 162 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 163 Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c 164 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091 165 [i] Fixed in: 4.7.8 166 167 [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS) 168 Reference: https://wpvulndb.com/vulnerabilities/9006 169 Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850 170 Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/ 171 Reference: https://core.trac.wordpress.org/ticket/42720 172 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776 173 [i] Fixed in: 4.7.9 174 175 [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched) 176 Reference: https://wpvulndb.com/vulnerabilities/9021 177 Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html 178 Reference: https://github.com/quitten/doser.py 179 Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html 180 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389 181 182 [!] Title: WordPress 3.7-4.9.4 - Remove localhost Default 183 Reference: https://wpvulndb.com/vulnerabilities/9053 184 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 185 Reference: https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216 186 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101 187 [i] Fixed in: 4.7.10 188 189 [!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login 190 Reference: https://wpvulndb.com/vulnerabilities/9054 191 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 192 Reference: https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e 193 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100 194 [i] Fixed in: 4.7.10 195 196 [!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag 197 Reference: https://wpvulndb.com/vulnerabilities/9055 198 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 199 Reference: https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d 200 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102 201 [i] Fixed in: 4.7.10 202 203 [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion 204 Reference: https://wpvulndb.com/vulnerabilities/9100 205 Reference: https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/ 206 Reference: http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/ 207 Reference: https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd 208 Reference: https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/ 209 Reference: https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/ 210 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895 211 [i] Fixed in: 4.7.11 212 213 [+] WordPress theme in use: twentyseventeen - v1.2 214 215 [+] Name: twentyseventeen - v1.2 216 | Location: http://192.168.64.138/wp-content/themes/twentyseventeen/ 217 | Readme: http://192.168.64.138/wp-content/themes/twentyseventeen/README.txt 218 [!] The version is out of date, the latest version is 1.7 219 | Style URL: http://192.168.64.138/wp-content/themes/twentyseventeen/style.css 220 | Theme Name: Twenty Seventeen 221 | Theme URI: https://wordpress.org/themes/twentyseventeen/ 222 | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a... 223 | Author: the WordPress team 224 | Author URI: https://wordpress.org/ 225 226 [+] Enumerating plugins from passive detection ... 227 | 1 plugin found: 228 229 [+] Name: wp-super-cache 230 | Latest version: 1.6.3 231 | Location: http://192.168.64.138/wp-content/plugins/wp-super-cache/ 232 233 [!] We could not determine a version so all vulnerabilities are printed out 234 235 [!] Title: WP-Super-Cache 1.3 - Remote Code Execution 236 Reference: https://wpvulndb.com/vulnerabilities/6623 237 Reference: http://www.acunetix.com/blog/web-security-zone/wp-plugins-remote-code-execution/ 238 Reference: http://wordpress.org/support/topic/pwn3d 239 Reference: http://blog.sucuri.net/2013/04/update-wp-super-cache-and-w3tc-immediately-remote-code-execution-vulnerability-disclosed.html 240 [i] Fixed in: 1.3.1 241 242 [!] Title: WP Super Cache 1.3 - trunk/wp-cache.php wp_nonce_url Function URI XSS 243 Reference: https://wpvulndb.com/vulnerabilities/6624 244 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 245 [i] Fixed in: 1.3.1 246 247 [!] Title: WP Super Cache 1.3 - trunk/plugins/wptouch.php URI XSS 248 Reference: https://wpvulndb.com/vulnerabilities/6625 249 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 250 [i] Fixed in: 1.3.1 251 252 [!] Title: WP Super Cache 1.3 - trunk/plugins/searchengine.php URI XSS 253 Reference: https://wpvulndb.com/vulnerabilities/6626 254 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 255 [i] Fixed in: 1.3.1 256 257 [!] Title: WP Super Cache 1.3 - trunk/plugins/domain-mapping.php URI XSS 258 Reference: https://wpvulndb.com/vulnerabilities/6627 259 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 260 [i] Fixed in: 1.3.1 261 262 [!] Title: WP Super Cache 1.3 - trunk/plugins/badbehaviour.php URI XSS 263 Reference: https://wpvulndb.com/vulnerabilities/6628 264 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 265 [i] Fixed in: 1.3.1 266 267 [!] Title: WP Super Cache 1.3 - trunk/plugins/awaitingmoderation.php URI XSS 268 Reference: https://wpvulndb.com/vulnerabilities/6629 269 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 270 [i] Fixed in: 1.3.1 271 272 [!] Title: WP Super Cache <= 1.4.2 - Stored Cross-Site Scripting (XSS) 273 Reference: https://wpvulndb.com/vulnerabilities/7889 274 Reference: http://blog.sucuri.net/2015/04/security-advisory-persistent-xss-in-wp-super-cache.html 275 [i] Fixed in: 1.4.3 276 277 [!] Title: WP Super Cache <= 1.4.4 - Cross-Site Scripting (XSS) 278 Reference: https://wpvulndb.com/vulnerabilities/8197 279 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 280 [i] Fixed in: 1.4.5 281 282 [!] Title: WP Super Cache <= 1.4.4 - PHP Object Injection 283 Reference: https://wpvulndb.com/vulnerabilities/8198 284 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 285 [i] Fixed in: 1.4.5 286 287 [+] Enumerating usernames ... 288 [+] Identified the following 1 user/s: 289 +----+-------+-----------------+ 290 | Id | Login | Name | 291 +----+-------+-----------------+ 292 | 1 | admin | admin – TurnKey | 293 +----+-------+-----------------+ 294 [!] Default first WordPress username 'admin' is still used 295 296 [+] Finished: Fri Aug 17 23:30:17 2018 297 [+] Requests Done: 64 298 [+] Memory used: 52.52 MB 299 [+] Elapsed time: 00:00:04
wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt
命令详解: -e枚举方式 u 用户ID1-ID10 --wordlist使用指定字典进行密码爆破 /root/wordlist.txt 字典路径及字典文件 wordlist.txt字典文件需自己准备或使用kali自带字典
1 root@kali:~# wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt 2 _______________________________________________________________ 3 __ _______ _____ 4 \ \ / / __ \ / ____| 5 \ \ /\ / /| |__) | (___ ___ __ _ _ __ 6 \ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \ 7 \ /\ / | | ____) | (__| (_| | | | | 8 \/ \/ |_| |_____/ \___|\__,_|_| |_| 9 10 WordPress Security Scanner by the WPScan Team 11 Version 2.9.1 12 Sponsored by Sucuri - https://sucuri.net 13 @_WPScan_, @ethicalhack3r, @erwan_lr, pvdl, @_FireFart_ 14 _______________________________________________________________ 15 16 [+] URL: http://192.168.64.138/ 17 [+] Started: Fri Aug 17 23:37:59 2018 18 19 [!] The WordPress 'http://192.168.64.138/readme.html' file exists exposing a version number 20 [+] Interesting header: LINK: <http://192.168.64.138/index.php/wp-json/>; rel="https://api.w.org/" 21 [+] Interesting header: SERVER: Apache 22 [+] XML-RPC Interface available under: http://192.168.64.138/xmlrpc.php 23 24 [+] WordPress version 4.7.4 identified from advanced fingerprinting (Released on 2017-04-20) 25 [!] 25 vulnerabilities identified from the version number 26 27 [!] Title: WordPress 2.3-4.8.3 - Host Header Injection in Password Reset 28 Reference: https://wpvulndb.com/vulnerabilities/8807 29 Reference: https://exploitbox.io/vuln/WordPress-Exploit-4-7-Unauth-Password-Reset-0day-CVE-2017-8295.html 30 Reference: http://blog.dewhurstsecurity.com/2017/05/04/exploitbox-wordpress-security-advisories.html 31 Reference: https://core.trac.wordpress.org/ticket/25239 32 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-8295 33 34 [!] Title: WordPress 2.7.0-4.7.4 - Insufficient Redirect Validation 35 Reference: https://wpvulndb.com/vulnerabilities/8815 36 Reference: https://github.com/WordPress/WordPress/commit/76d77e927bb4d0f87c7262a50e28d84e01fd2b11 37 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 38 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9066 39 [i] Fixed in: 4.7.5 40 41 [!] Title: WordPress 2.5.0-4.7.4 - Post Meta Data Values Improper Handling in XML-RPC 42 Reference: https://wpvulndb.com/vulnerabilities/8816 43 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 44 Reference: https://github.com/WordPress/WordPress/commit/3d95e3ae816f4d7c638f40d3e936a4be19724381 45 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9062 46 [i] Fixed in: 4.7.5 47 48 [!] Title: WordPress 3.4.0-4.7.4 - XML-RPC Post Meta Data Lack of Capability Checks 49 Reference: https://wpvulndb.com/vulnerabilities/8817 50 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 51 Reference: https://github.com/WordPress/WordPress/commit/e88a48a066ab2200ce3091b131d43e2fab2460a4 52 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9065 53 [i] Fixed in: 4.7.5 54 55 [!] Title: WordPress 2.5.0-4.7.4 - Filesystem Credentials Dialog CSRF 56 Reference: https://wpvulndb.com/vulnerabilities/8818 57 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 58 Reference: https://github.com/WordPress/WordPress/commit/38347d7c580be4cdd8476e4bbc653d5c79ed9b67 59 Reference: https://sumofpwn.nl/advisory/2016/cross_site_request_forgery_in_wordpress_connection_information.html 60 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9064 61 [i] Fixed in: 4.7.5 62 63 [!] Title: WordPress 3.3-4.7.4 - Large File Upload Error XSS 64 Reference: https://wpvulndb.com/vulnerabilities/8819 65 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 66 Reference: https://github.com/WordPress/WordPress/commit/8c7ea71edbbffca5d9766b7bea7c7f3722ffafa6 67 Reference: https://hackerone.com/reports/203515 68 Reference: https://hackerone.com/reports/203515 69 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9061 70 [i] Fixed in: 4.7.5 71 72 [!] Title: WordPress 3.4.0-4.7.4 - Customizer XSS & CSRF 73 Reference: https://wpvulndb.com/vulnerabilities/8820 74 Reference: https://wordpress.org/news/2017/05/wordpress-4-7-5/ 75 Reference: https://github.com/WordPress/WordPress/commit/3d10fef22d788f29aed745b0f5ff6f6baea69af3 76 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-9063 77 [i] Fixed in: 4.7.5 78 79 [!] Title: WordPress 2.3.0-4.8.1 - $wpdb->prepare() potential SQL Injection 80 Reference: https://wpvulndb.com/vulnerabilities/8905 81 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 82 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 83 Reference: https://github.com/WordPress/WordPress/commit/fc930d3daed1c3acef010d04acc2c5de93cd18ec 84 [i] Fixed in: 4.7.6 85 86 [!] Title: WordPress 2.3.0-4.7.4 - Authenticated SQL injection 87 Reference: https://wpvulndb.com/vulnerabilities/8906 88 Reference: https://medium.com/websec/wordpress-sqli-bbb2afcc8e94 89 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 90 Reference: https://github.com/WordPress/WordPress/commit/70b21279098fc973eae803693c0705a548128e48 91 Reference: https://wpvulndb.com/vulnerabilities/8905 92 [i] Fixed in: 4.7.5 93 94 [!] Title: WordPress 2.9.2-4.8.1 - Open Redirect 95 Reference: https://wpvulndb.com/vulnerabilities/8910 96 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 97 Reference: https://core.trac.wordpress.org/changeset/41398 98 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14725 99 [i] Fixed in: 4.7.6 100 101 [!] Title: WordPress 3.0-4.8.1 - Path Traversal in Unzipping 102 Reference: https://wpvulndb.com/vulnerabilities/8911 103 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 104 Reference: https://core.trac.wordpress.org/changeset/41457 105 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14719 106 [i] Fixed in: 4.7.6 107 108 [!] Title: WordPress 4.4-4.8.1 - Path Traversal in Customizer 109 Reference: https://wpvulndb.com/vulnerabilities/8912 110 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 111 Reference: https://core.trac.wordpress.org/changeset/41397 112 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14722 113 [i] Fixed in: 4.7.6 114 115 [!] Title: WordPress 4.4-4.8.1 - Cross-Site Scripting (XSS) in oEmbed 116 Reference: https://wpvulndb.com/vulnerabilities/8913 117 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 118 Reference: https://core.trac.wordpress.org/changeset/41448 119 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14724 120 [i] Fixed in: 4.7.6 121 122 [!] Title: WordPress 4.2.3-4.8.1 - Authenticated Cross-Site Scripting (XSS) in Visual Editor 123 Reference: https://wpvulndb.com/vulnerabilities/8914 124 Reference: https://wordpress.org/news/2017/09/wordpress-4-8-2-security-and-maintenance-release/ 125 Reference: https://core.trac.wordpress.org/changeset/41395 126 Reference: https://blog.sucuri.net/2017/09/stored-cross-site-scripting-vulnerability-in-wordpress-4-8-1.html 127 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-14726 128 [i] Fixed in: 4.7.6 129 130 [!] Title: WordPress <= 4.8.2 - $wpdb->prepare() Weakness 131 Reference: https://wpvulndb.com/vulnerabilities/8941 132 Reference: https://wordpress.org/news/2017/10/wordpress-4-8-3-security-release/ 133 Reference: https://github.com/WordPress/WordPress/commit/a2693fd8602e3263b5925b9d799ddd577202167d 134 Reference: https://twitter.com/ircmaxell/status/923662170092638208 135 Reference: https://blog.ircmaxell.com/2017/10/disclosure-wordpress-wpdb-sql-injection-technical.html 136 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-16510 137 [i] Fixed in: 4.7.7 138 139 [!] Title: WordPress 2.8.6-4.9 - Authenticated JavaScript File Upload 140 Reference: https://wpvulndb.com/vulnerabilities/8966 141 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 142 Reference: https://github.com/WordPress/WordPress/commit/67d03a98c2cae5f41843c897f206adde299b0509 143 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17092 144 [i] Fixed in: 4.7.8 145 146 [!] Title: WordPress 1.5.0-4.9 - RSS and Atom Feed Escaping 147 Reference: https://wpvulndb.com/vulnerabilities/8967 148 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 149 Reference: https://github.com/WordPress/WordPress/commit/f1de7e42df29395c3314bf85bff3d1f4f90541de 150 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17094 151 [i] Fixed in: 4.7.8 152 153 [!] Title: WordPress 4.3.0-4.9 - HTML Language Attribute Escaping 154 Reference: https://wpvulndb.com/vulnerabilities/8968 155 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 156 Reference: https://github.com/WordPress/WordPress/commit/3713ac5ebc90fb2011e98dfd691420f43da6c09a 157 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17093 158 [i] Fixed in: 4.7.8 159 160 [!] Title: WordPress 3.7-4.9 - 'newbloguser' Key Weak Hashing 161 Reference: https://wpvulndb.com/vulnerabilities/8969 162 Reference: https://wordpress.org/news/2017/11/wordpress-4-9-1-security-and-maintenance-release/ 163 Reference: https://github.com/WordPress/WordPress/commit/eaf1cfdc1fe0bdffabd8d879c591b864d833326c 164 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-17091 165 [i] Fixed in: 4.7.8 166 167 [!] Title: WordPress 3.7-4.9.1 - MediaElement Cross-Site Scripting (XSS) 168 Reference: https://wpvulndb.com/vulnerabilities/9006 169 Reference: https://github.com/WordPress/WordPress/commit/3fe9cb61ee71fcfadb5e002399296fcc1198d850 170 Reference: https://wordpress.org/news/2018/01/wordpress-4-9-2-security-and-maintenance-release/ 171 Reference: https://core.trac.wordpress.org/ticket/42720 172 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-5776 173 [i] Fixed in: 4.7.9 174 175 [!] Title: WordPress <= 4.9.4 - Application Denial of Service (DoS) (unpatched) 176 Reference: https://wpvulndb.com/vulnerabilities/9021 177 Reference: https://baraktawily.blogspot.fr/2018/02/how-to-dos-29-of-world-wide-websites.html 178 Reference: https://github.com/quitten/doser.py 179 Reference: https://thehackernews.com/2018/02/wordpress-dos-exploit.html 180 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-6389 181 182 [!] Title: WordPress 3.7-4.9.4 - Remove localhost Default 183 Reference: https://wpvulndb.com/vulnerabilities/9053 184 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 185 Reference: https://github.com/WordPress/WordPress/commit/804363859602d4050d9a38a21f5a65d9aec18216 186 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10101 187 [i] Fixed in: 4.7.10 188 189 [!] Title: WordPress 3.7-4.9.4 - Use Safe Redirect for Login 190 Reference: https://wpvulndb.com/vulnerabilities/9054 191 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 192 Reference: https://github.com/WordPress/WordPress/commit/14bc2c0a6fde0da04b47130707e01df850eedc7e 193 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10100 194 [i] Fixed in: 4.7.10 195 196 [!] Title: WordPress 3.7-4.9.4 - Escape Version in Generator Tag 197 Reference: https://wpvulndb.com/vulnerabilities/9055 198 Reference: https://wordpress.org/news/2018/04/wordpress-4-9-5-security-and-maintenance-release/ 199 Reference: https://github.com/WordPress/WordPress/commit/31a4369366d6b8ce30045d4c838de2412c77850d 200 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-10102 201 [i] Fixed in: 4.7.10 202 203 [!] Title: WordPress <= 4.9.6 - Authenticated Arbitrary File Deletion 204 Reference: https://wpvulndb.com/vulnerabilities/9100 205 Reference: https://blog.ripstech.com/2018/wordpress-file-delete-to-code-execution/ 206 Reference: http://blog.vulnspy.com/2018/06/27/Wordpress-4-9-6-Arbitrary-File-Delection-Vulnerbility-Exploit/ 207 Reference: https://github.com/WordPress/WordPress/commit/c9dce0606b0d7e6f494d4abe7b193ac046a322cd 208 Reference: https://wordpress.org/news/2018/07/wordpress-4-9-7-security-and-maintenance-release/ 209 Reference: https://www.wordfence.com/blog/2018/07/details-of-an-additional-file-deletion-vulnerability-patched-in-wordpress-4-9-7/ 210 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-12895 211 [i] Fixed in: 4.7.11 212 213 [+] WordPress theme in use: twentyseventeen - v1.2 214 215 [+] Name: twentyseventeen - v1.2 216 | Location: http://192.168.64.138/wp-content/themes/twentyseventeen/ 217 | Readme: http://192.168.64.138/wp-content/themes/twentyseventeen/README.txt 218 [!] The version is out of date, the latest version is 1.7 219 | Style URL: http://192.168.64.138/wp-content/themes/twentyseventeen/style.css 220 | Theme Name: Twenty Seventeen 221 | Theme URI: https://wordpress.org/themes/twentyseventeen/ 222 | Description: Twenty Seventeen brings your site to life with header video and immersive featured images. With a... 223 | Author: the WordPress team 224 | Author URI: https://wordpress.org/ 225 226 [+] Enumerating plugins from passive detection ... 227 | 1 plugin found: 228 229 [+] Name: wp-super-cache 230 | Latest version: 1.6.3 231 | Location: http://192.168.64.138/wp-content/plugins/wp-super-cache/ 232 233 [!] We could not determine a version so all vulnerabilities are printed out 234 235 [!] Title: WP-Super-Cache 1.3 - Remote Code Execution 236 Reference: https://wpvulndb.com/vulnerabilities/6623 237 Reference: http://www.acunetix.com/blog/web-security-zone/wp-plugins-remote-code-execution/ 238 Reference: http://wordpress.org/support/topic/pwn3d 239 Reference: http://blog.sucuri.net/2013/04/update-wp-super-cache-and-w3tc-immediately-remote-code-execution-vulnerability-disclosed.html 240 [i] Fixed in: 1.3.1 241 242 [!] Title: WP Super Cache 1.3 - trunk/wp-cache.php wp_nonce_url Function URI XSS 243 Reference: https://wpvulndb.com/vulnerabilities/6624 244 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 245 [i] Fixed in: 1.3.1 246 247 [!] Title: WP Super Cache 1.3 - trunk/plugins/wptouch.php URI XSS 248 Reference: https://wpvulndb.com/vulnerabilities/6625 249 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 250 [i] Fixed in: 1.3.1 251 252 [!] Title: WP Super Cache 1.3 - trunk/plugins/searchengine.php URI XSS 253 Reference: https://wpvulndb.com/vulnerabilities/6626 254 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 255 [i] Fixed in: 1.3.1 256 257 [!] Title: WP Super Cache 1.3 - trunk/plugins/domain-mapping.php URI XSS 258 Reference: https://wpvulndb.com/vulnerabilities/6627 259 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 260 [i] Fixed in: 1.3.1 261 262 [!] Title: WP Super Cache 1.3 - trunk/plugins/badbehaviour.php URI XSS 263 Reference: https://wpvulndb.com/vulnerabilities/6628 264 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 265 [i] Fixed in: 1.3.1 266 267 [!] Title: WP Super Cache 1.3 - trunk/plugins/awaitingmoderation.php URI XSS 268 Reference: https://wpvulndb.com/vulnerabilities/6629 269 Reference: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2013-2008 270 [i] Fixed in: 1.3.1 271 272 [!] Title: WP Super Cache <= 1.4.2 - Stored Cross-Site Scripting (XSS) 273 Reference: https://wpvulndb.com/vulnerabilities/7889 274 Reference: http://blog.sucuri.net/2015/04/security-advisory-persistent-xss-in-wp-super-cache.html 275 [i] Fixed in: 1.4.3 276 277 [!] Title: WP Super Cache <= 1.4.4 - Cross-Site Scripting (XSS) 278 Reference: https://wpvulndb.com/vulnerabilities/8197 279 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 280 [i] Fixed in: 1.4.5 281 282 [!] Title: WP Super Cache <= 1.4.4 - PHP Object Injection 283 Reference: https://wpvulndb.com/vulnerabilities/8198 284 Reference: http://z9.io/2015/09/25/wp-super-cache-1-4-5/ 285 [i] Fixed in: 1.4.5 286 287 [+] Enumerating usernames ... 288 [+] Identified the following 1 user/s: 289 +----+-------+-----------------+ 290 | Id | Login | Name | 291 +----+-------+-----------------+ 292 | 1 | admin | admin – TurnKey | 293 +----+-------+-----------------+ 294 [!] Default first WordPress username 'admin' is still used 295 [+] Starting the password brute forcer 296 [+] [SUCCESS] Login : admin Password : Root******** 297 298 Brute Forcing 'admin' Time: 00:00:00 <===== > (2 / 3) 66.66% ETA: 00:00:00 299 +----+-------+-----------------+------------------+ 300 | Id | Login | Name | Password | 301 +----+-------+-----------------+------------------+ 302 | 1 | admin | admin – TurnKey | Root********* | 303 +----+-------+-----------------+------------------+ 304 305 [+] Finished: Fri Aug 17 23:38:06 2018 306 [+] Requests Done: 72 307 [+] Memory used: 53.016 MB 308 [+] Elapsed time: 00:00:06
常用命令
wpscan -u 192.168.64.138 -e u --wordlist /root/wordlist.txt -t 50
-t 指定50个线程数