Membership
If you’ve read through the documentation on identity you’ve seen how a PKI can provide verifiable identities through a chain of trust. Now let’s see how these identities can be used to represent the trusted members of a blockchain network.
如果您已阅读关于身份的文档,您就会看到PKI如何通过信任链提供可验证的身份。现在让我们看看这些身份如何用来表示区块链网络的可信任成员。
This is where a Membership Service Provider (MSP) comes into play — it identifies which Root CAs and Intermediate CAs are trusted to define the members of a trust domain, e.g., an organization, either by listing the identities of their members, or by identifying which CAs are authorized to issue valid identities for their members, or — as will usually be the case — through a combination of both.
这是会员服务提供商(MSP)开始发挥作用的地方 - 它通过列出成员的身份,或者通过识别哪些CA被授权为他们的成员发放有效的身份,或者 - 通常情况下 - 通过两者的组合,去识别哪些根CA或者中级CA是受信任的,进而可以定义一个信任域的成员,例如,一个组织机构。
The power of an MSP goes beyond simply listing who is a network participant or member of a channel. An MSP can identify specific roles an actor might play either within the scope of the organization the MSP represents (e.g., admins, or as members of a sub-organization group), and sets the basis for defining access privileges in the context of a network and channel (e.g., channel admins, readers, writers).
MSP的能力不仅仅在于列出谁是网络参与者或管道(channel)成员。MSP可以确定参与者可能在MSP所代表的组织范围内(例如,管理员或者作为子组织组的成员)发挥的具体角色,并为在网络环境和管道(channel)中定义访问权限奠定基础。
The configuration of an MSP is advertised to all the channels where members of the corresponding organization participate (in the form of a channel MSP). In addition to the channel MSP, peers, orderers, and clients also maintain a local MSP to authenticate member messages outside the context of a channel and to define the permissions over a particular component (who has the ability to install chaincode on a peer, for example).
MSP的配置广播给相应组织成员参与的所有管道(channel)(以管道(channel)MSP的形式)。除了管道(channel)MSP之外,peers,orderers和客户端还维护一个本地MSP,以便在管道(channel)上下文之外验证成员消息,并定义对特定组件的权限(例如,谁能够在peer上安装链码)。
In addition, an MSP can allow for the identification of a list of identities that have been revoked — as discussed in the Identity documentation — but we will talk about how that process also extends to an MSP.
此外,MSP可以识别已被撤销的身份列表 - 正如身份证明文件中所述 - 但我们将讨论该过程如何延伸到MSP。
We’ll talk more about local and channel MSPs in a moment. For now let’s see what MSPs do in general.
我们稍后会详细讨论本地和管道(channel)MSP。现在让我们来看看MSP通常会做什么。
Mapping MSPs to Organizations/将MSP映射到组织
An organization is a managed group of members. This can be something as big as a multinational corporation or a small as a flower shop. What’s most important about organizations (or orgs) is that they manage their members under a single MSP. Note that this is different from the organization concept defined in an X.509 certificate, which we’ll talk about later.
一个组织是一个受管理的成员组。这可能和跨国公司一样大,或者像花店一样小。组织(或组织)最重要的是他们在一个单一的MSP下管理其成员。请注意,这与在X.509证书中定义的组织概念不同,我们稍后会讨论该证书。
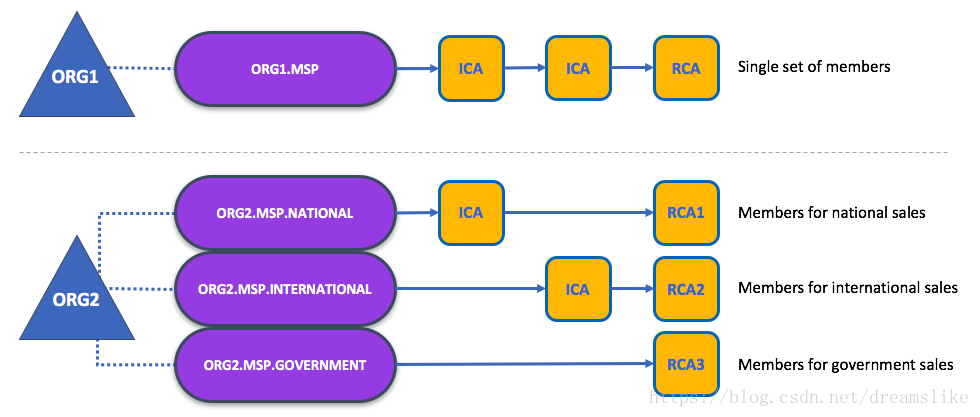
The exclusive relationship between an organization and its MSP makes it sensible to name the MSP after the organization, a convention you’ll find adopted in most policy configurations. For example, organization ORG1 would likely have an MSP called something like ORG1-MSP. In some cases an organization may require multiple membership groups — for example, where channels are used to perform very different business functions between organizations. In these cases it makes sense to have multiple MSPs and name them accordingly, e.g., ORG2-MSP-NATIONAL and ORG2-MSP-GOVERNMENT, reflecting the different membership roots of trust within ORG2 in the NATIONAL sales channel compared to the GOVERNMENT regulatory channel.
组织与MSP之间的独有的关系使得在组织之后命名MSP是明智的,在大多数策略配置中,您会发现一个惯例。例如,组织ORG1可能会有一个叫做ORG1-MSP的MSP。在某些情况下,组织可能需要多个成员资格组 - 例如,管道(channels)用于在组织之间执行完全不同的业务职能。在这些情况下,拥有多个MSP并相应地命名它们是有意义的,例如ORG2-MSP-NATIONAL和ORG2-MSP-GOVERNMENT,反映了与政府监管管道(channel)相比,国家销售管道(channel)中ORG2中不同的成员信任根源。
Two different MSP configurations for an organization. The first configuration shows the typical relationship between an MSP and an organization — a single MSP defines the list of members of an organization. In the second configuration, different MSPs are used to represent different organizational groups with national, international, and governmental affiliation.
组织的两种不同的MSP配置。 第一种配置显示MSP和组织之间的典型关系 - 单个MSP定义组织成员的列表。 在第二种配置中,不同的MSP用于代表具有国家,国际和政府关系的不同组织团体。
Organizational Units and MSPs/组织单位和MSP
An organization is often divided up into multiple organizational units (OUs), each of which has a certain set of responsibilities. For example, the ORG1 organization might have both ORG1-MANUFACTURING and ORG1-DISTRIBUTION OUs to reflect these separate lines of business. When a CA issues X.509 certificates, the OU field in the certificate specifies the line of business to which the identity belongs.
一个组织经常被分成多个组织单位(OU),每个组织单位都有一定的责任。例如,ORG1组织可能同时具有ORG1-MANUFACTURING和ORG1-DISTRIBUTION OU以反映这些单独的业务线。当CA颁发X.509证书时,证书中的OU字段将指定该身份所属的业务线。
We’ll see later how OUs can be helpful to control the parts of an organization who are considered to be the members of a blockchain network. For example, only identities from the ORG1-MANUFACTURING OU might be able to access a channel, whereas ORG1-DISTRIBUTION cannot.
我们稍后会看到OU如何有助于控制被视为区块链网络成员的组织部分。例如,只有来自ORG1-MANUFACTURING OU的身份可能能够访问某个管道(channel),而ORG1-DISTRIBUTION则不能。
Finally, though this is a slight misuse of OUs, they can sometimes be used by different organizations in a consortium to distinguish each other. In such cases, the different organizations use the same Root CAs and Intermediate CAs for their chain of trust, but assign the OU field to identify members of each organization. We’ll also see how to configure MSPs to achieve this later.
最后,虽然这是对OU的轻微滥用,但它们有时可以由联盟中的不同组织用于区分彼此。在这种情况下,不同的组织为其信任链使用相同的根CA和中间CA,但分配OU字段以标识每个组织的成员。我们也会看到如何配置MSP来实现这一点。
Local and Channel MSPs/本地和管道(channel)MSP
MSPs appear in two places in a blockchain network: channel configuration (channel MSPs), and locally on an actor’s premise (local MSP). Local MSPs are defined for clients (users) and for nodes (peers and orderers). Node local MSPs define the permissions for that node (who the peer admins are, for example). The local MSPs of the users allow the user side to authenticate itself in its transactions as a member of a channel (e.g. in chaincode transactions), or as the owner of a specific role into the system (an org admin, for example, in configuration transactions).
MSP出现在区块链网络中的两个地方:管道(channel)配置(管道(channel)MSP)和参与者的本地场所(本地MSP)。本地MSP是为客户(用户)和节点(peers和orderers)定义的。节点本地MSP定义该节点的权限(例如,peer管理员是谁)。用户的本地MSP允许用户在其交易中作为管道(channel)成员(例如链码交易),或者作为系统中特定角色的所有者(组织管理员,例如,配置交易)进行身份验证。
Every node and user must have a local MSP defined, as it defines who has administrative or participatory rights at that level (peer admins will not necessarily be channel admins, and vice versa).
每个节点和用户必须定义一个本地MSP,因为它定义了在该级别具有管理或参与权限的人员(peer管理员不一定是管道(channel)管理员,反之亦然)。
In contrast, channel MSPs define administrative and participatory rights at the channel level. Every organization participating in a channel must have an MSP defined for it. Peers and orderers on a channel will all share the same view of channel MSPs, and will therefore be able to correctly authenticate the channel participants. This means that if an organization wishes to join the channel, an MSP incorporating the chain of trust for the organization’s members would need to be included in the channel configuration. Otherwise transactions originating from this organization’s identities will be rejected.
相反,管道(channel)MSP在管道(channel)层面定义管理和参与权。参与管道(channel)的每个组织都必须为其定义MSP。管道(channel)上的peers和orderers 将共享相同的管道(channel)MSP视图,因此能够正确认证管道(channel)参与者。这意味着如果一个组织希望加入该管道(channel),那么需要在管道(channel)配置中包含一个包含该组织成员的信任链的MSP。否则来自该组织身份的交易将被拒绝。
The key difference here between local and channel MSPs is not how they function — both turn identities into roles — but their scope.
本地和管道(channel)MSPs之间的关键区别不在于它们的功能 - 它们都将身份转化为角色 - 而是它们的范围。
Local and channel MSPs. The trust domain (e.g., the organization) of each peer is defined by the peer’s local MSP, e.g., ORG1 or ORG2. Representation of an organization on a channel is achieved by adding the organization’s MSP to the channel configuration. For example, the channel of this figure is managed by both ORG1 and ORG2. Similar principles apply for the network, orderers, and users, but these are not shown here for simplicity.
本地和管道(channel)MSPs。每个peer的信任域(例如组织)由peer的本地MSP(例如ORG1或ORG2)定义。通过将组织的MSP添加到管道(channel)配置来实现组织在管道(channel)上的表示。例如,该图的管道(channel)由ORG1和ORG2管理。类似的原则适用于网络,orderers和用户,但为简单起见,这里没有显示。
You may find it helpful to see how local and channel MSPs are used by seeing what happens when a blockchain administrator installs and instantiates a smart contract, as shown in the diagram above.
您可能会发现,通过查看区块链管理员安装并实例化智能合约时发生的情况,了解本地和管道(channel)MSP的使用方式很有用,如上图所示。
An administrator B connects to the peer with an identity issued by RCA1 and stored in their local MSP. When B tries to install a smart contract on the peer, the peer checks its local MSP, ORG1-MSP, to verify that the identity of B is indeed a member of ORG1. A successful verification will allow the install command to complete successfully. Subsequently, B wishes to instantiate the smart contract on the channel. Because this is a channel operation, all organizations on the channel must agree to it. Therefore, the peer must check the MSPs of the channel before it can successfully commit this command. (Other things must happen too, but concentrate on the above for now.)
管理员B使用RCA1颁发的身份连接到peer端,并存储在其本地MSP中。当B尝试在peer体上安装智能合约时,peer体检查其本地MSP ORG1-MSP,以验证B的身份确实是ORG1的成员。成功验证将允许安装命令成功完成。随后,B希望实例化该渠管道(channel)上的智能合约。由于这是管道(channel)操作,管道(channel)中的所有组织都必须同意。因此,peer方必须先检查管道(channel)的MSP,然后才能成功提交此命令。 (其他事情也必须发生,但现在要专注于上述内容。)
Local MSPs are only defined on the file system of the node or user to which they apply. Therefore, physically and logically there is only one local MSP per node or user. However, as channel MSPs are available to all nodes in the channel, they are logically defined once in the channel configuration. However, a channel MSP is also instantiated on the file system of every node in the channel and kept synchronized via consensus. So while there is a copy of each channel MSP on the local file system of every node, logically a channel MSP resides on and is maintained by the channel or the network.
本地MSP仅定义于其应用的节点或用户的文件系统上。因此,在物理上和逻辑上,每个节点或用户只有一个本地MSP。但是,由于管道(channel)MSP对管道(channel)中的所有节点均可用,因此它们在管道(channel)配置中,逻辑上只被定义一次。但是,管道(channel)MSP也在管道(channel)中的每个节点的文件系统上实例化,并通过共识保持同步。因此,虽然每个节点的本地文件系统上存在每个管道(channel)MSP的副本,逻辑上,管道(channel)MSP驻留在管道(channel)或网络上并由其维护。
MSP Levels/MSP级别
The split between channel and local MSPs reflects the needs of organizations to administer their local resources, such as a peer or orderer nodes, and their channel resources, such as ledgers, smart contracts, and consortia, which operate at the channel or network level. It’s helpful to think of these MSPs as being at different levels, with MSPs at a higher level relating to network administration concerns while MSPs at a lower level handle identity for the administration of private resources. MSPs are mandatory at every level of administration — they must be defined for the network, channel, peer, orderer, and users.
管道(channel)与本地MSP之间的分割反映了组织机构在管道(channel)或网络级别上管理其本地资源(例如peer或orderer节点)及其管道(channel)资源(例如在管道(channel)或网络级别运营的总账,智能合约和财团)的需求。 将这些MSP视为处于不同级别是有帮助的,其中MSP处于与网络管理问题有关的较高级别,而处在较低级别的MSP为私有资源的管理处理身份。 MSP在每个管理级别都是强制性的 – 必须为网络,管道(channel),peer,orderer和用户定义它们。
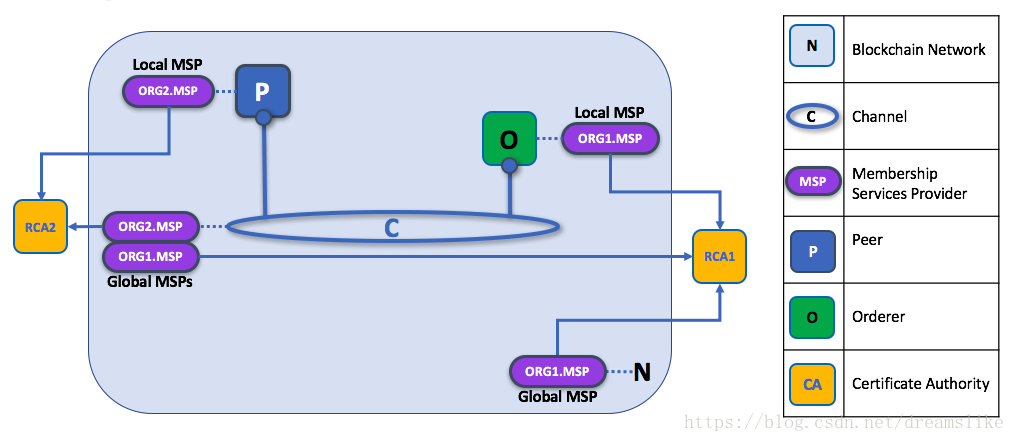
MSP Levels. The MSPs for the peer and orderer are local, whereas the MSPs for a channel (including the network configuration channel) are shared across all participants of that channel. In this figure, the network configuration channel is administered by ORG1, but another application channel can be managed by ORG1 and ORG2. The peer is a member of and managed by ORG2, whereas ORG1 manages the orderer of the figure. ORG1 trusts identities from RCA1, whereas ORG2 trusts identities from RCA2. Note that these are administration identities, reflecting who can administer these components. So while ORG1 administers the network, ORG2.MSP does exist in the network definition.
MSP级别。peer者和orderer的MSP是本地的,而管道(channel)的MSP(包括网络配置管道(channel))在该管道(channel)的所有参与者之间共享。在该图中,网络配置管道(channel)由ORG1管理,但另一个应用程序管道(channel)可由ORG1和ORG2管理。peer体是ORG2的成员,并由ORG2管理,而ORG1管理图形的orderer。 ORG1信任来自RCA1的身份,而ORG2信任来自RCA2的身份。请注意,这些是管理身份,反映了谁可以管理这些组件。所以当ORG1管理网络时,ORG2.MSP确实存在于网络定义中。
Network MSP: The configuration of a network defines who are the members in the network — by defining the MSPs of the participant organizations — as well as which of these members are authorized to perform administrative tasks (e.g., creating a channel).
网络MSP:网络配置通过定义参与者组织的MSP以及这些成员中哪些成员有权执行管理任务(例如创建管道(channel))来定义网络中的成员。
Channel MSP: It is important for a channel to maintain the MSPs of its members separately. A channel provides private communications between a particular set of organizations which in turn have administrative control over it. Channel policies interpreted in the context of that channel’s MSPs define who has ability to participate in certain action on the channel, e.g., adding organizations, or instantiating chaincodes. Note that there is no necessary relationship between the permission to administrate a channel and the ability to administrate the network configuration channel (or any other channel). Administrative rights exist within the scope of what is being administrated (unless the rules have been written otherwise — see the discussion of the ROLE attribute below).
管道(channel)MSP:管道(channel)分开维护其成员的MSP非常重要。管道(channel)提供了一组特定的组织之间的私人通信,这些组织又对其进行管理控制。在该管道(channel)的MSP上下文中解释的管道(channel)策略定义谁能够参与管道(channel)上的某些操作,例如添加组织或实例化连锁代码。请注意,管理管道(channel)的权限与管理网络配置管道(channel)(或任何其他管道(channel))的权限之间没有必要的关系。管理权限存在于正在管理的范围内(除非规则另有书面 – 请参阅下面关于ROLE属性的讨论)。
Peer MSP: This local MSP is defined on the file system of each peer and there is a single MSP instance for each peer. Conceptually, it performs exactly the same function as channel MSPs with the restriction that it only applies to the peer where it is defined. An example of an action whose authorization is evaluated using the peer’s local MSP is the installation of a chaincode on the peer.
peerMSP:本地MSP在每个peer方的文件系统上定义,并且每个peer方都有一个MSP实例。从概念上讲,它执行的功能与管道(channel)MSP完全相同,限制条件是它仅适用于定义它的peer方。使用peer方的本地MSP评估其授权的操作的示例是在peer方上安装链码。
Orderer MSP: Like a peer MSP, an orderer local MSP is also defined on the file system of the node and only applies to that node. Like peer nodes, orderers are also owned by a single organization and therefore have a single MSP to list the actors or nodes it trusts.
ordererMSP:与peerMSP一样,orderer本地MSP也在节点的文件系统上定义,并且仅适用于该节点。与peer节点相似,orderers也由单个组织拥有,因此只有一个MSP来列出其信任的参与者或节点。
MSP Structure/MSP结构
So far, you’ve seen that the most important element of an MSP are the specification of the root or intermediate CAs that are used to establish an actor’s or node’s membership in the respective organization. There are, however, more elements that are used in conjunction with these two to assist with membership functions.
到目前为止,您已经看到,MSP最重要的元素是用于确定相应组织中的参与者或节点成员资格的根CA或中间CA的规范。 但是,有更多的元素与这两个元素结合使用来协助会员职能。
The figure above shows how a local MSP is stored on a local filesystem. Even though channel MSPs are not physically structured in exactly this way, it’s still a helpful way to think about them.
上图显示了本地MSP如何存储在本地文件系统中。尽管管道(channel)MSP的物理结构并不完全如此,但它仍然是一个有用的方式来思考它们。
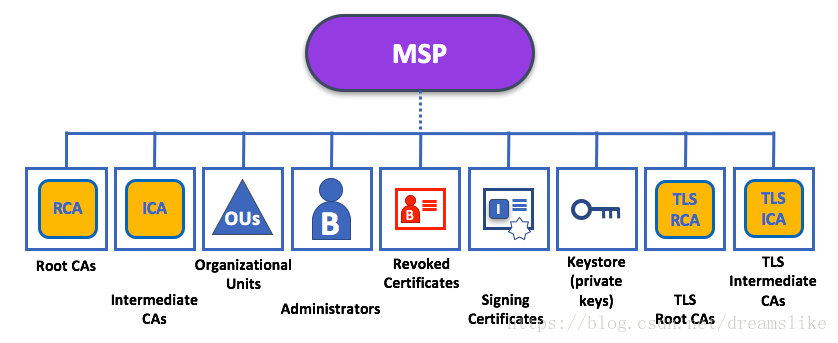
As you can see, there are nine elements to an MSP. It’s easiest to think of these elements in a directory structure, where the MSP name is the root folder name with each subfolder representing different elements of an MSP configuration.
正如你所看到的,MSP有九个要素。在目录结构中考虑这些元素是最简单的,其中MSP名称是根文件夹名称,每个子文件夹代表MSP配置的不同元素。
Let’s describe these folders in a little more detail and see why they are important.
-
Root CAs: This folder contains a list of self-signed X.509 certificates of the Root CAs trusted by the organization represented by this MSP. There must be at least one Root CA X.509 certificate in this MSP folder.
根CA:此文件夹包含由此MSP代表的组织信任的根CA的自签名X.509证书列表。此MSP文件夹中必须至少有一个根CA X.509证书。
This is the most important folder because it identifies the CAs from which all other certificates must be derived to be considered members of the corresponding organization.
这是最重要的文件夹,因为它标识所有其他证书必须从中派生出来的CA,以便被视为相应组织的成
-
Intermediate CAs: This folder contains a list of X.509 certificates of the Intermediate CAs trusted by this organization. Each certificate must be signed by one of the Root CAs in the MSP or by an Intermediate CA whose issuing CA chain ultimately leads back to a trusted Root CA.
中级CA:此文件夹包含此组织信任的中级CA的X.509证书列表。每个证书都必须由MSP中的一个根CA签署,或者由中间CA签署,该中间CA的颁发CA链最终可追述到受信任根CA。
An intermediate CA may represent a different subdivision of the organization (like ORG1-MANUFACTURING and ORG1-DISTRIBUTION do for ORG1), or the organization itself (as may be the case if a commercial CA is leveraged for the organization’s identity management). In the latter case intermediate CAs can be used to represent organization subdivisions. Here you may find more information on best practices for MSP configuration. Notice, that it is possible to have a functioning network that does not have an Intermediate CA, in which case this folder would be empty.
中间CA可能代表组织的不同细分(如ORG1-MANUFACTURING和ORG1-DISTRIBUTION针对ORG1)或组织本身(如果商业CA用于组织身份管理时可能会出现这种情况)。在后一种情况下,中间CA可以用来表示组织细分。在这里您可以找到关于MSP配置最佳实践的更多信息。请注意,可能有一个没有中间CA的功能网络,在这种情况下,该文件夹将为空。
Like the Root CA folder, this folder defines the CAs from which certificates must be issued to be considered members of the organization.
与根CA文件夹一样,此文件夹定义了CAs, 由这些CAs颁发的证书才能被视为组织成员.
-
Organizational Units (OUs): These are listed in the
$FABRIC_CFG_PATH/msp/config.yamlfile and contain a list of organizational units, whose members are considered to be part of the organization represented by this MSP. This is particularly useful when you want to restrict the members of an organization to the ones holding an identity (signed by one of MSP designated CAs) with a specific OU in it.
组织单位(OU):它们列在$ FABRIC_CFG_PATH / msp / config.yaml文件中,其中包含一个组织单位列表,其成员被认为是该MSP所代表的组织的一部分。当您希望将组织的成员限制为持有身份(由MSP指定的CA之一签名)且具有特定OU的组织时,这一点尤其有用。
Specifying OUs is optional. If no OUs are listed, all the identities that are part of an MSP — as identified by the Root CA and Intermediate CA folders — will be considered members of the organization.
指定OU是可选的。如果未列出OU,则由根CA和中间CA文件夹所标识MSP的身份----将被视为该组织的成员。
-
Administrators: This folder contains a list of identities that define the actors who have the role of administrators for this organization. For the standard MSP type, there should be one or more X.509 certificates in this list.
管理员:该文件夹包含一个身份列表,用于定义具有该组织管理员角色的参与者。对于标准MSP类型,此列表中应该有一个或多个X.509证书。
It’s worth noting that just because a actor has the role of an administrator it doesn’t mean that they can administer particular resources! The actual power a given identity has with respect to administering the system is determined by the policies that manage system resources. For example, a channel policy might specify that ORG1-MANUFACTURING administrators have the rights to add new organizations to the channel, whereas the ORG1-DISTRIBUTION administrators have no such rights.
值得注意的是,仅仅因为参与者具有管理员的角色,并不意味着他们可以管理特定的资源!一个给定的身份在管理系统方面的实际能力取决于管理系统资源的策略。例如,管道(channel)策略可能会指定ORG1-MANUFACTURING管理员有权将新组织添加到管道(channel),而ORG1-DISTRIBUTION管理员则没有此权限。
Even though an X.509 certificate has a ROLE attribute (specifying, for example, that a actor is an admin), this refers to a actor’s role within its organization rather than on the blockchain network. This is similar to the purpose of the OU attribute, which — if it has been defined — refers to a actor’s place in the organization.
即使X.509证书具有ROLE属性(例如,指定参与者是管理员),这也是指参与者在其组织中而不是区块链网络中的角色。这与OU属性的用途类似,如果它已被定义 - 指的是参与者在组织中的位置。
The ROLE attribute can be used to confer administrative rights at the channel level if the policy for that channel has been written to allow any administrator from an organization (or certain organizations) permission to perform certain channel functions (such as instantiating chaincode). In this way, an organizational role can confer a network role.
如果该管道(channel)的已经写入的策略允许来自组织(或某些组织)的任何管理员执行某些管道(channel)功能(例如实例化链式代码),则ROLE属性可用于在管道(channel)道级别赋予管理权限。通过这种方式,组织角色可以赋予网络角色。
-
Revoked Certificates: If the identity of an actor has been revoked, identifying information about the identity — not the identity itself — is held in this folder. For X.509-based identities, these identifiers are pairs of strings known as Subject Key Identifier (SKI) and Authority Access Identifier (AKI), and are checked whenever the X.509 certificate is being used to make sure the certificate has not been revoked.
吊销的证书:如果某个参与者的身份已被吊销,则识别有关该身份的信息 - 而不是身份本身 - 保存在此文件夹中。对于基于X.509的身份,这些标识符是称为主题密钥标识符(SKI)和权限访问标识符(AKI)的字符串对,并且每当使用X.509证书时都会进行检查以确保证书尚未撤销。
This list is conceptually the same as a CA’s Certificate Revocation List (CRL), but it also relates to revocation of membership from the organization. As a result, the administrator of an MSP, local or channel, can quickly revoke a actor or node from an organization by advertising the updated CRL of the CA the revoked certificate as issued by. This “list of lists” is optional. It will only become populated as certificates are revoked.
此列表在概念上与CA的证书撤销列表(CRL)相同,但它也涉及从组织撤销会员资格。因此,MSP的本地或管道(channel)管理员可以通过将更新后的CA撤销证书的CRL进行公告,从而快速撤销组织中的参与者或节点。这个“列表清单”是可选的。它只会在证书被撤销时填充。
-
Node Identity: This folder contains the identity of the node, i.e., cryptographic material that — in combination to the content of
KeyStore— would allow the node to authenticate itself in the messages that is sends to other participants of its channels and network. For X.509 based identities, this folder contains an X.509 certificate. This is the certificate a peer places in a transaction proposal response, for example, to indicate that the peer has endorsed it — which can subsequently be checked against the resulting transaction’s endorsement policy at validation time.
节点身份:该文件夹包含节点的身份,即密码材料 - 与KeyStore的内容相结合 - 将允许节点在发送给其信道和网络的其他参与者的消息中对自身进行身份验证。对于基于X.509的身份,此文件夹包含一个X.509证书。例如,这是peer方在交易提议响应中的证书,以表明peer方已经认可了该证书 - 随后可以在验证时根据所得到的交易的背书(endorsement)策略来检查该证书。
This folder is mandatory for local MSPs, and there must be exactly one X.509 certificate for the node. It is not used for channel MSPs.
该文件夹对于本地MSP是必需的,并且该节点必须只有一个X.509证书。它不用于管道(channel)MSP。
-
KeyStorefor Private Key: This folder is defined for the local MSP of a peer or orderer node (or in an client’s local MSP), and contains the node’s signing key. This key matches cryptographically the node’s identity included in Node Identity folder and is used to sign data — for example to sign a transaction proposal response, as part of the endorsement phase.
私钥KeyStore:该文件夹为peer或orderer节点(或客户端的本地MSP)的本地MSP定义,并包含节点的签名密钥。此密钥以加密方式与节点标识文件夹中包含的节点标识匹配,并用于签署数据 - 例如签署交易提议响应,作为认可阶段的一部分。
This folder is mandatory for local MSPs, and must contain exactly one private key. Obviously, access to this folder must be limited only to the identities of users who have administrative responsibility on the peer.
文件夹对本地MSP是强制性的,并且必须包含一个私钥。显然,访问此文件夹的权限只限于对peer方负有管理责任的用户的身份。
Configuration of a channel MSPs does not include this folder, as channel MSPs solely aim to offer identity validation functionalities and not signing abilities.
管道(channel)MSP的配置不包括此文件夹,因为管道(channel)MSP仅仅旨在提供身份验证功能而不是签名功能。
-
TLS Root CA: This folder contains a list of self-signed X.509 certificates of the Root CAs trusted by this organization for TLS communications. An example of a TLS communication would be when a peer needs to connect to an orderer so that it can receive ledger updates.
TLS根CA:此文件夹包含此组织为TLS通信所信任的根CA的自签名X.509证书列表。 TLS通信的一个例子是peer端需要连接到orderer以便它可以接收总账更新。
MSP TLS information relates to the nodes inside the network — the peers and the orderers, in other words, rather than the applications and administrations that consume the network.
换句话说,MSP TLS信息与网络内部的节点(即peers和定向器)相关,而不是消耗网络的应用程序和管理。
There must be at least one TLS Root CA X.509 certificate in this folder.
此文件夹中必须至少有一个TLS根CA X.509证书。
-
TLS Intermediate CA: This folder contains a list intermediate CA certificates CAs trusted by the organization represented by this MSP for TLS communications. This folder is specifically useful when commercial CAs are used for TLS certificates of an organization. Similar to membership intermediate CAs, specifying intermediate TLS CAs is optional.
TLS中级CA:此文件夹包含由此MSP代表的组织信任的用于TLS通信的列表中间CA证书CA。当商业CA用于组织的TLS证书时,此文件夹特别有用。与成员中间CA类似,指定中间TLS CA是可选的。
For more information about TLS, click here.
有关TLS的更多信息,请单击此处。
If you’ve read this doc as well as our doc on Identity), you should have a pretty good grasp of how identities and membership work in Hyperledger Fabric. You’ve seen how a PKI and MSPs are used to identify the actors collaborating in a blockchain network. You’ve learned how certificates, public/private keys, and roots of trust work, in addition to how MSPs are physically and logically structured.
如果您已阅读此文档以及关于Identity的文档),您应该很好地掌握Hyperledger Fabric中的身份和成员身份。您已经看到PKI和MSP如何用于识别在区块链网络中合作的参与者。除了MSP的物理和逻辑结构外,您还了解了证书,公钥/私钥和信任根的工作原理。