1、首先查看一下pki文档目录结构
drwxr-xr-x. 6 root root 4096 Aug 4 2017 CA
drwxr-xr-x. 4 root root 4096 Jan 19 20:16 ca-trust
drwxr-xr-x. 2 root root 4096 Jan 19 20:16 java
drwxr-xr-x. 2 root root 4096 Jan 19 20:44 nssdb
drwxr-xr-x 2 root root 4096 Jan 19 20:16 nss-legacy
drwxr-xr-x. 2 root root 4096 Jan 19 20:16 rpm-gpg
drwx------. 2 root root 4096 Aug 7 2017 rsyslog
drwxr-xr-x. 5 root root 4096 May 10 00:33 tlspki:指的是公钥基础设施
解释一下这些文件夹:
CA
认证中心
通过发放和维护数字证书来建立一套信任网络,同一信任网络中的用户通过申请到的数字证书来完成身份认证和安全处理
进入到CA目录
drwxr-xr-x. 2 root root 4096 Aug 4 2017 certs
drwxr-xr-x. 2 root root 4096 Aug 4 2017 crl
drwxr-xr-x. 2 root root 4096 Aug 4 2017 newcerts
drwx------. 2 root root 4096 Aug 4 2017 private看到了四个文件夹,分别是用于存放证书证书、私钥、公钥的
ca-trust
This directory /etc/pki/ca-trust is used by a system of consolidated
CA certificates.
用tree命令查看文档目录结构
.
|-- ca-legacy.conf
|-- extracted
| |-- java
| | |-- cacerts
| | `-- README
| |-- openssl
| | |-- ca-bundle.trust.crt
| | `-- README
| |-- pem
| | |-- email-ca-bundle.pem
| | |-- objsign-ca-bundle.pem
| | |-- README
| | `-- tls-ca-bundle.pem
| `-- README
|-- README
`-- source
|-- anchors
|-- blacklist
|-- ca-bundle.legacy.crt -> /usr/share/pki/ca-trust-legacy/ca-bundle.legacy.default.crt
`-- README
在Java目录中的Readme文件中写着:
This directory /etc/pki/ca-trust/extracted/java/ contains
CA certificate bundle files which are automatically created
based on the information found in the
/usr/share/pki/ca-trust-source/ and /etc/pki/ca-trust/source/
directories.
也就是说,这些证书的生成是基于/usr/share/pki/ca-trust-source/ and /etc/pki/ca-trust/source/这两个目录的,在openssl中的readme文件中有相似的描述在extracted中的readme中写着
This directory /etc/pki/ca-trust/extracted/ contains
CA certificate bundle files which are automatically created.
//这个目录包含有ca证书的可执行文件,且是系统自动生成的。
If your application isn't able to load the PKCS#11 module p11-kit-trust.so,
then you can use these files in your application to load a list of global
root CA certificates.
Please never manually edit the files stored in this directory,
because your changes will be lost and the files automatically overwritten,
each time the update-ca-trust command gets executed.
//不要动这里面的文件(不要修改),否则会出事儿
Please refer to the update-ca-trust(8) manual page for additional information.进入到source目录,查看readme:
This directory /etc/pki/ca-trust/source/ contains CA certificates and
trust settings in the PEM file format. The trust settings found here will be
interpreted with a high priority - higher than the ones found in
/usr/share/pki/ca-trust-source/.
//这个没有了包含ca证书和信任设置在pem文件里。这里的设置有比较高的优先级。
=============================================================================
QUICK HELP: To add a certificate in the simple PEM or DER file formats to the
list of CAs trusted on the system:
Copy it to the
/etc/pki/ca-trust/source/anchors/
subdirectory, and run the
update-ca-trust
command.
If your certificate is in the extended BEGIN TRUSTED file format,
then place it into the main source/ directory instead.
=============================================================================
nssdb
是一种nosql,基于内存的非关系型数据库
pkcs11.txt
//pkcs11.txt 针对密码设备的接口指令标准,查看里面的结果如下:
parameters=configdir='sql:/etc/pki/nssdb' certPrefix='' keyPrefix='' secmod='secmod.db' flags= updatedir='' updateCertPrefix='' updateKeyPrefix='' updateid='' updateTokenDescription=''
NSS=Flags=internal,moduleDBOnly,critical trustOrder=75 cipherOrder=100 slotParams=(1={slotFlags=[RSA,DSA,DH,RC2,RC4,DES,RANDOM,SHA1,MD5,MD2,SSL,TLS,AES,Camellia,SEED,SHA256,SHA512] askpw=any timeout=30})nss-legacy
里面只有一个config配置文件,里面的内容如下:
# To re-enable legacy algorithms, edit this file
# Note that the last empty line in this file must be preserved
library=
name=Policy
NSS=flags=policyOnly,moduleDB
config="disallow=md5 allow=DH-MIN=1023:DSA-MIN=1023:RSA-MIN=1023"rmp-gpg
GPG在Linux上的应用主要是实现官方发布的包的签名机制
tls
顾名思义:TLS就是安全传输层协议
说明这个文件夹下面的东西就是跟https访问相关的东西。
lrwxrwxrwx 1 root root 49 Jan 19 20:16 cert.pem -> /etc/pki/ca-trust/extracted/pem/tls-ca-bundle.pem
drwxr-xr-x. 2 root root 4096 May 10 07:59 certs
drwxr-xr-x. 2 root root 4096 May 10 00:14 misc
-rw-r--r-- 1 root root 10923 May 17 2017 openssl.cnf
drwxr-xr-x. 2 root root 4096 May 10 00:55 private其中certs是证书目录,private目录是放私钥的。misc是存放证书相关指令集的库文件,里面的内容如下:
-rwxr-xr-x 1 root root 5178 Aug 4 2017 CA
-rwxr-xr-x 1 root root 119 Aug 4 2017 c_hash
-rwxr-xr-x 1 root root 152 Aug 4 2017 c_info
-rwxr-xr-x 1 root root 112 Aug 4 2017 c_issuer
-rwxr-xr-x 1 root root 110 Aug 4 2017 c_name都是shell脚本文件。
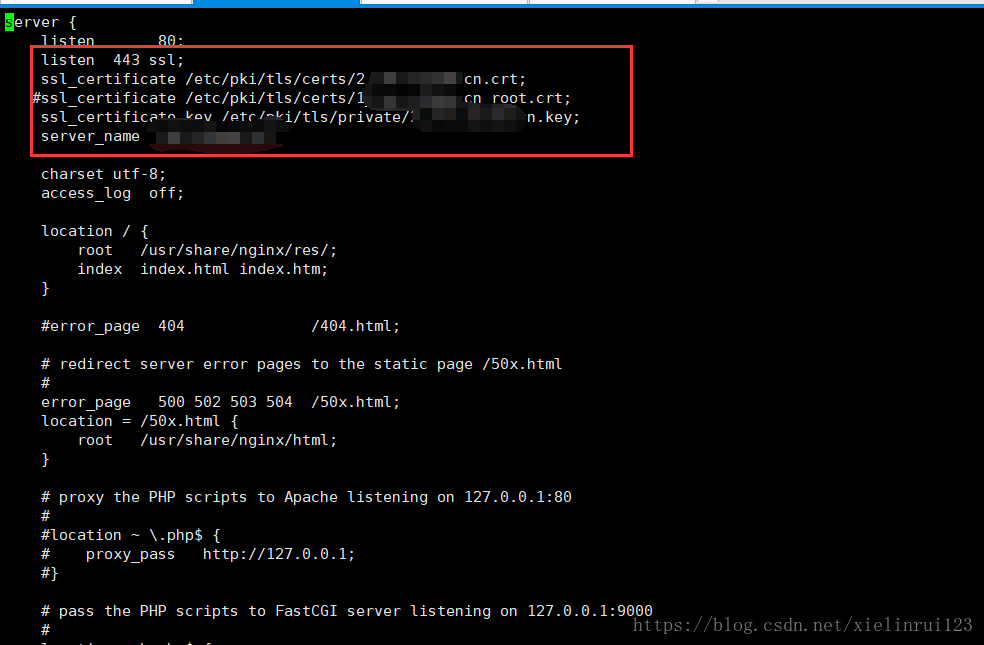
2、将从腾讯云中申请的域名证书的.crt文件放置到certs目录下,将.key文件放置到private目录下就可以了。
然后进入到nginx的配置文件所在目录,系统默认是在/etc/nginx下面,然后进入到conf.d目录下,创建一个新的网站配置文件,最好以域名命名,避免配置多了之后名字冲突。
这样就配好了。
多个子域名之间互相调用会存在跨域问题,当由网页访问api时,需在http块中添加如下:
add_header Access-Control-Allow-Origin *;
add_header Access-Control-Allow-Headers "ApiAuth,Origin, X-Requested-With, Content-Type, Accept";
add_header Access-Control-Allow-Methods "GET, POST, OPTIONS";如果是网页到网页,则只需要:
add_header Access-Control-Allow-Origin *;
add_header Access-Control-Allow-Headers "Origin, X-Requested-With, Content-Type, Accept";
add_header Access-Control-Allow-Methods "GET, POST, OPTIONS";即可。