Nessus 自动更新配置
- Nessus software update
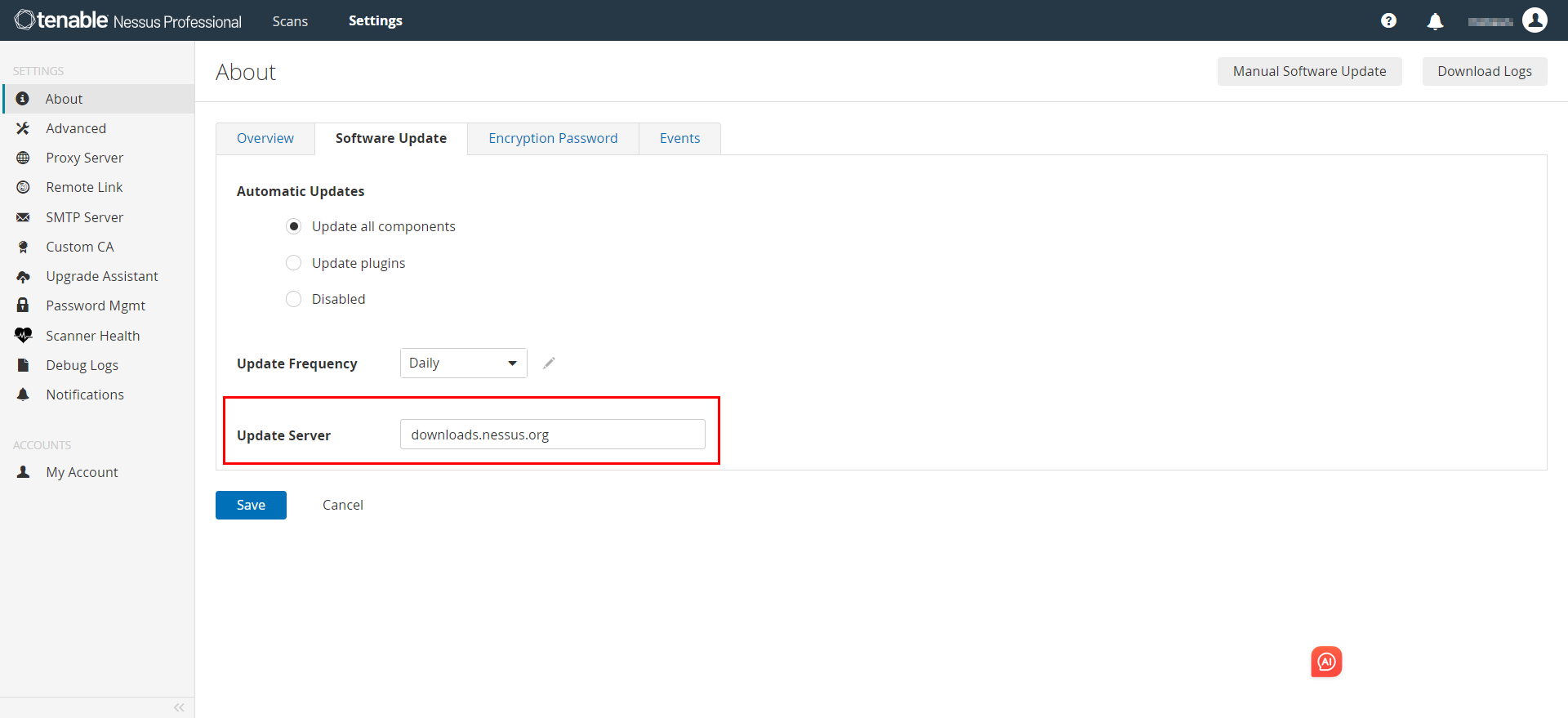
Nessus软件更新配置,可以指定更新服务器,如果未指定,默认也是会指向官方的更新服务器。
- 防火墙配置允许policy
Nessus自动更新,还需要自动连接互联网,需要在防火墙上配置Policy,允许连接访问:
- Nessus 自动更新: https://downloads.nessus.org
- 下载 Nessus 应用程序:https://www.tenable.com/downloads/nessus
根据选用的Nessus产品不同,需要开放的自动更新或者下载的url也会有所区别,整理大部分tenable产品自动更新所需的url:
- https://plugins.nessus.org
- https://downloads.nessus.org
- https://plugins-customers.nessus.org
- https://plugins-us.nessus.org
- https://plugins.cloud.tenable.com
- https://appliance.cloud.tenable.com
- https://tenablesecurity.com
- https://cloud.tenable.com
这些都需要对应产品,并在防火墙策略中进行配置,以允许访问实现autoupdate。
如果是Nessus增加log4shell相关的插件,还需要额外增加两个通配符域名:
- *.w.nessus.org
- *.r.nessus.org
Nessus服务端口开放
Nessus profession 版本需要开放端口
大多数企业应该都是购买的Nessus profession 版本,这个版本需要开放的端口如下:
Incoming TCP Port 22 - Command-line interface
Incoming TCP Port 8834 - User Interface, TSC communication, and API calls
Outgoing TCP Port 25 - SMTP email notification
Outgoing TCP Port 389 - LDAP Authentication (may also use 636 for LDAPS)
Outgoing TCP Port 443 - Plugin updates and TVM communication
Outgoing TCP Port 3128 - Web Proxy communication (may also use 8080 or any other custom port)
Outgoing UDP Port 53 - DNS resolution, required for malware scan
Incoming TCP Port 22 允许通过SSH的方式连接,并用命令行模式进行配置。
Incoming TCP Port 8834 管理Nessus,通常采用WEB,而8834是管理web的端口。
如果有使用Nessus agent,安装Nessus agent后,Nessus Manager会自动更新Nessus agent。但是也需要开通如下端口:
Outgoing TCP Port 443 - TVM or Sensor Proxy communication
Outgoing TCP Port 8834 - Nessus Manager communication
Sensor Proxy
Sensor Proxy需要开放的端口列表如下:
Incoming TCP Port 22 - Command-line interface
Incoming TCP Port 443 - Agent communication
Outgoing UDP Port 123 - NTP synchronization
Outgoing TCP Port 443 - Tenable Vulnerability Management communication and OS updates
Outgoing UDP Port 53 - DNS resolution
Tenable Security Center (TSC)
以下是部分Tenable的产品对应需要用到的端口信息,因本人使用的环境没有用到这么多产品,所以就不一一细说了。
Incoming TCP Port 22 - Remote repository sync with other TSC deployments and interaction with TSC internals
Incoming TCP Port 443 - User Interface, API calls, and remote repositories initial key push
Outgoing TCP Port 22 - SSH for LCE event query and remote repository sync
Outgoing TCP Port 25 - SMTP Email notification (may also use 587 for secure email or other non-standard port)
Outgoing TCP Port 389 - LDAP Authentication (may also use 636 for LDAPS)
Outgoing TCP Port 443 - Plugins update and Tenable.io communication
Outgoing UDP Port 514 - Syslog forwarding (optional, may also use TCP Port 514)
Outgoing TCP Port 1243 - LCE Event Vulnerability Data Reporting
Outgoing TCP Port 3128 - Web Proxy communication (may also use 8080 or any other custom port)
Outgoing TCP Port 8834 - Nessus and Nessus Manager communication
Outgoing TCP Port 8835 - Nessus Network Monitor communication
Outgoing UDP Port 53 - DNS resolution
Tenable OT Security (TOT)
以下是部分Tenable的产品对应需要用到的端口信息,因本人使用的环境没有用到这么多产品,所以就不一一细说了。
Tenable OT Security Enterprise Manager (IEM)
Incoming TCP Port 22 - SSH and IEM pairing
Incoming TCP Port 443 - Web UI access and IEM pairing
Outgoing TCP Port 22 - SSH and IEM pairing
Outgoing TCP Port 443 - Web UI access and IEM pairing
Tenable OT Security Industrial Core Platform (ICP)
Incoming TCP Port 22 - SSH, Sensor pairing, IEM pairing
Incoming TCP Port 443 - Web UI access, Sensor pairing, IEM pairing
Incoming TCP Port 28303 - Sensor pairing (TOT version 3.14 and lower)
Incoming TCP Port 28304 - Sensor pairing (TOT version 3.16 and higher)
Outgoing TCP Port 22 - SSH, Sensor pairing, IEM pairing
Outgoing TCP Port 443 - Web UI access, Sensor pairing, IEM pairing, communication with TSC, HTTPS fingerprinting
Outgoing TCP Port 80 - HTTP fingerprinting
Outgoing TCP Port 102 - S7/S7+ protocol
Outgoing TCP Port 389 - LDAPS communication
Outgoing TCP Port 636 - LDAPS communication
Outgoing TCP Port 445 - WMI queries
Outgoing TCP Port 502 - Modbus protocol
Outgoing ICMP - Asset discovery
Outgoing TCP Port 5432 - PostgreSQL queries
Outgoing TCP Port 44818 - CIP protocol
Outgoing TCP Port 53 - DNS
Outgoing UDP Port 53 - DNS
Outgoing TCP Port 25 - SMTP email
Outgoing UDP Port 514 - Syslog forwarding
Outgoing UDP Port 161 - SNMP queries
Outgoing UDP Port 137 - NBNS queries
Outgoing UDP Port 138 - NetBIOS queries
Tenable OT Security Sensor
Incoming TCP Port 22 - SSH, Sensor pairing
Incoming TCP Port 443 - Sensor pairing
Outgoing TCP Port 28303 - Sensor pairing (TOT version 3.14 and lower)
Outgoing TCP Port 28304 - Sensor pairing (TOT version 3.16 and higher)
Outgoing TCP Port 22 - SSH, Sensor pairing
Outgoing TCP Port 443 - Sensor pairing
Outgoing TCP Port 80 - HTTP fingerprinting
Outgoing TCP Port 102 - S7/S7+ protocol
Outgoing TCP Port 389 - LDAPS communication
Outgoing TCP Port 636 - LDAPS communication
Outgoing TCP Port 445 - WMI queries
Outgoing TCP Port 502 - Modbus protocol
Outgoing ICMP - Asset discovery
Outgoing TCP Port 5432 - PostgreSQL queries
Outgoing TCP Port 44818 - CIP protocol
Outgoing TCP Port 53 - DNS
Outgoing UDP Port 53 - DNS
Outgoing TCP Port 25 - SMTP email
Outgoing UDP Port 514 - Syslog forwarding
Outgoing UDP Port 161 - SNMP queries
Outgoing UDP Port 137 - NBNS queries
Outgoing UDP Port 138 - NetBIOS queries
Tenable Cloud Security (TCS)
On-Premise Code Scanner - Incoming TCP Port 9020 - Receive jobs from SCM, Web UI, receive authorization from SCM authorizer
On-Premise Code Scanner - Outgoing TCP Port 443 (to internet) - Send data to TCS cloud service
Nessus Professional 和 Nessus Expert 之间的区别
这里扩展分享一个Nessus Professional 和 Nessus Expert 之间的区别。
Nessus Expert 于2022年就发布了。
Nessus Expert 直接在 Nessus Professional 的基础上构建,包含 Nessus Professional 的所有功能。不同之处在于 Nessus Expert 添加了一些功能,扩展了客户解决现代攻击面安全问题的能力。
那么关键的功能差异是什么?
- Nessus Expert 提供扫描基础设施即代码 (IaC) 的功能。这允许客户在实施之前扫描 IaC 代码存储库以识别任何漏洞和策略违规行为。
- Nessus Expert 提供执行外部攻击面发现的能力。这允许客户扫描顶级域并识别可通过互联网访问的所有子域。