1 Vault介绍
Vault 是一个基于身份的秘密和加密管理系统。秘密是您想要严格控制访问的任何内容,例如 API 加密密钥、密码和证书。 Vault 提供由身份验证和授权方法控制的加密服务。使用 Vault 的 UI、CLI 或 HTTP API,可以安全地存储和管理、严格控制(限制)和审核对机密和其他敏感数据的访问。
2 为什么需要 Vault
- 执行密码轮换策略很痛苦
- 掌握机密的员工离职后可能泄密或是恶意报复
- 开发者不小心把机密信息随着代码上传到公网的源码仓库造成泄密
- 管理多个系统的机密非常麻烦
- 需要将机密信息安全地加密后存储,但又不想将密钥暴露给应用程序,以防止应用程序被入侵后连带密钥一起泄漏
3 Vault 架构图
Vault 只暴漏了存储后端(Storage Backend) 和 API,其他部分都被保护起来了。Vault 并不信任后端存储,存放的都是密文。

参考:二、vault - vault的架构_vault 原理图-CSDN博客
4 安装部署
4.1 二进制部署
4.1.1 下载二进制资源包
$ ls
vault_1.15.4_linux_amd64.zip4.1.2 解压安装
$ unzip vault_1.15.4_linux_amd64.zip
Archive: vault_1.15.4_linux_amd64.zip
inflating: vault
$ mv vault /usr/bin/4.2 yum方式安装
$ yum install -y yum-utils
$ yum-config-manager --add-repo https://rpm.releases.hashicorp.com/RHEL/hashicorp.repo
$ yum -y install vault5 Vault使用
5.1 启动 Vault
5.1.1 Dev 模式
$ vault server -dev
==> Vault server configuration:
Administrative Namespace:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: GODEBUG, HISTCONTROL, HISTSIZE, HOME, HOSTNAME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, OLDPWD, PATH, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _
Go Version: go1.21.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: false
Recovery Mode: false
Storage: inmem
Version: Vault v1.15.4, built 2023-12-04T17:45:28Z
Version Sha: 9b61934559ba31150860e618cf18e816cbddc630
==> Vault server started! Log data will stream in below:
2023-12-19T21:48:24.515+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-12-19T21:48:24.515+0800 [INFO] incrementing seal generation: generation=1
2023-12-19T21:48:24.515+0800 [WARN] no `api_addr` value specified in config or in VAULT_API_ADDR; falling back to detection if possible, but this value should be manually set
2023-12-19T21:48:24.516+0800 [INFO] core: Initializing version history cache for core
2023-12-19T21:48:24.516+0800 [INFO] events: Starting event system
2023-12-19T21:48:24.516+0800 [INFO] core: security barrier not initialized
2023-12-19T21:48:24.516+0800 [INFO] core: security barrier initialized: stored=1 shares=1 threshold=1
2023-12-19T21:48:24.516+0800 [INFO] core: post-unseal setup starting
2023-12-19T21:48:24.525+0800 [INFO] core: loaded wrapping token key
2023-12-19T21:48:24.525+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T21:48:24.525+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T21:48:24.525+0800 [INFO] core: no mounts; adding default mount table
2023-12-19T21:48:24.529+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T21:48:24.530+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T21:48:24.530+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T21:48:24.532+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T21:48:24.532+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T21:48:24.532+0800 [INFO] rollback: starting rollback manager
2023-12-19T21:48:24.532+0800 [INFO] core: restoring leases
2023-12-19T21:48:24.533+0800 [INFO] expiration: lease restore complete
2023-12-19T21:48:24.533+0800 [INFO] identity: entities restored
2023-12-19T21:48:24.533+0800 [INFO] identity: groups restored
2023-12-19T21:48:24.533+0800 [INFO] core: Recorded vault version: vault version=1.15.4 upgrade time="2023-12-19 13:48:24.533557895 +0000 UTC" build date=2023-12-04T17:45:28Z
2023-12-19T21:48:24.806+0800 [INFO] core: post-unseal setup complete
2023-12-19T21:48:24.807+0800 [INFO] core: root token generated
2023-12-19T21:48:24.807+0800 [INFO] core: pre-seal teardown starting
2023-12-19T21:48:24.807+0800 [INFO] rollback: stopping rollback manager
2023-12-19T21:48:24.807+0800 [INFO] core: pre-seal teardown complete
2023-12-19T21:48:24.807+0800 [INFO] core.cluster-listener.tcp: starting listener: listener_address=127.0.0.1:8201
2023-12-19T21:48:24.807+0800 [INFO] core.cluster-listener: serving cluster requests: cluster_listen_address=127.0.0.1:8201
2023-12-19T21:48:24.807+0800 [INFO] core: post-unseal setup starting
2023-12-19T21:48:24.807+0800 [INFO] core: loaded wrapping token key
2023-12-19T21:48:24.807+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T21:48:24.807+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T21:48:24.808+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T21:48:24.808+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T21:48:24.809+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T21:48:24.810+0800 [INFO] rollback: starting rollback manager
2023-12-19T21:48:24.810+0800 [INFO] core: restoring leases
2023-12-19T21:48:24.810+0800 [INFO] identity: entities restored
2023-12-19T21:48:24.810+0800 [INFO] identity: groups restored
2023-12-19T21:48:24.810+0800 [INFO] expiration: lease restore complete
2023-12-19T21:48:24.810+0800 [INFO] core: post-unseal setup complete
2023-12-19T21:48:24.810+0800 [INFO] core: vault is unsealed
2023-12-19T21:48:24.813+0800 [INFO] core: successful mount: namespace="" path=secret/ type=kv version=""
WARNING! dev mode is enabled! In this mode, Vault runs entirely in-memory
and starts unsealed with a single unseal key. The root token is already
authenticated to the CLI, so you can immediately begin using Vault.
You may need to set the following environment variables:
$ export VAULT_ADDR='http://127.0.0.1:8200'
The unseal key and root token are displayed below in case you want to
seal/unseal the Vault or re-authenticate.
Unseal Key: SbJGQUMajGWHZSNpYCTuxemXerDVUaHTjSWEmpR8Qhg=
Root Token: hvs.vLVLD2gBlgnLAhCrc83pDWSa
Development mode should NOT be used in production installations!
^C==> Vault shutdown triggered
2023-12-19T21:48:35.466+0800 [INFO] core: marked as sealed
2023-12-19T21:48:35.467+0800 [INFO] core: pre-seal teardown starting
2023-12-19T21:48:35.467+0800 [INFO] rollback: stopping rollback manager
2023-12-19T21:48:35.467+0800 [INFO] core: pre-seal teardown complete
2023-12-19T21:48:35.467+0800 [INFO] core: stopping cluster listeners
2023-12-19T21:48:35.467+0800 [INFO] core.cluster-listener: forwarding rpc listeners stopped
2023-12-19T21:48:35.819+0800 [INFO] core.cluster-listener: rpc listeners successfully shut down
2023-12-19T21:48:35.819+0800 [INFO] core: cluster listeners successfully shut down
2023-12-19T21:48:35.819+0800 [INFO] core: vault is sealed命令执行后的返回文本中会有 Unseal Key 和 Root Token 两个参数,这两个参数很关键一定要记录好。
5.1.2 生产模式
5.1.2.1 配置文件
$ vim /etc/vault/config.hcl
storage "raft" {
path = "/data/vault"
node_id = "node-1"
}
listener "tcp" {
address = "127.0.0.1:8200"
tls_disable = "true"
}
api_addr = "http://127.0.0.1:8200"
cluster_addr = "https://127.0.0.1:8201"
ui = true
$ mkdir -p ./vault/data
5.1.2.2 启动
$ vault server -config=/etc/vault/config.hcl
==> Vault server configuration:
Administrative Namespace:
Api Address: http://127.0.0.1:8200
Cgo: disabled
Cluster Address: https://127.0.0.1:8201
Environment Variables: GODEBUG, HISTCONTROL, HISTSIZE, HOME, HOSTNAME, LANG, LESSOPEN, LOGNAME, LS_COLORS, MAIL, OLDPWD, PATH, PWD, SHELL, SHLVL, SSH_CLIENT, SSH_CONNECTION, SSH_TTY, TERM, USER, XDG_RUNTIME_DIR, XDG_SESSION_ID, _
Go Version: go1.21.4
Listener 1: tcp (addr: "127.0.0.1:8200", cluster address: "127.0.0.1:8201", max_request_duration: "1m30s", max_request_size: "33554432", tls: "disabled")
Log Level:
Mlock: supported: true, enabled: true
Recovery Mode: false
Storage: raft (HA available)
Version: Vault v1.15.4, built 2023-12-04T17:45:28Z
Version Sha: 9b61934559ba31150860e618cf18e816cbddc630
==> Vault server started! Log data will stream in below:
2023-12-19T22:08:53.771+0800 [INFO] proxy environment: http_proxy="" https_proxy="" no_proxy=""
2023-12-19T22:08:53.779+0800 [INFO] incrementing seal generation: generation=1
2023-12-19T22:08:53.856+0800 [INFO] core: Initializing version history cache for core
2023-12-19T22:08:53.856+0800 [INFO] events: Starting event system
2023-12-19T22:09:28.104+0800 [INFO] core: security barrier not initialized
2023-12-19T22:09:28.104+0800 [INFO] core: seal configuration missing, not initialized
2023-12-19T22:09:28.104+0800 [INFO] core: security barrier not initialized
2023-12-19T22:09:28.106+0800 [INFO] storage.raft: creating Raft: config="&raft.Config{ProtocolVersion:3, HeartbeatTimeout:5000000000, ElectionTimeout:5000000000, CommitTimeout:50000000, MaxAppendEntries:64, BatchApplyCh:true, ShutdownOnRemove:true, TrailingLogs:0x2800, SnapshotInterval:120000000000, SnapshotThreshold:0x2000, LeaderLeaseTimeout:2500000000, LocalID:\"node-1\", NotifyCh:(chan<- bool)(0xc00284d260), LogOutput:io.Writer(nil), LogLevel:\"DEBUG\", Logger:(*hclog.interceptLogger)(0xc002760330), NoSnapshotRestoreOnStart:true, skipStartup:false}"
2023-12-19T22:09:28.107+0800 [INFO] storage.raft: initial configuration: index=1 servers="[{Suffrage:Voter ID:node-1 Address:127.0.0.1:8201}]"
2023-12-19T22:09:28.107+0800 [INFO] storage.raft: entering follower state: follower="Node at node-1 [Follower]" leader-address= leader-id=
2023-12-19T22:09:36.223+0800 [WARN] storage.raft: heartbeat timeout reached, starting election: last-leader-addr= last-leader-id=
2023-12-19T22:09:36.223+0800 [INFO] storage.raft: entering candidate state: node="Node at node-1 [Candidate]" term=2
2023-12-19T22:09:36.226+0800 [INFO] storage.raft: election won: term=2 tally=1
2023-12-19T22:09:36.226+0800 [INFO] storage.raft: entering leader state: leader="Node at node-1 [Leader]"
2023-12-19T22:09:36.239+0800 [INFO] core: security barrier initialized: stored=1 shares=5 threshold=3
2023-12-19T22:09:36.256+0800 [INFO] core: post-unseal setup starting
2023-12-19T22:09:36.261+0800 [INFO] core: loaded wrapping token key
2023-12-19T22:09:36.261+0800 [INFO] core: successfully setup plugin runtime catalog
2023-12-19T22:09:36.261+0800 [INFO] core: successfully setup plugin catalog: plugin-directory=""
2023-12-19T22:09:36.261+0800 [INFO] core: no mounts; adding default mount table
2023-12-19T22:09:36.268+0800 [INFO] core: successfully mounted: type=cubbyhole version="v1.15.4+builtin.vault" path=cubbyhole/ namespace="ID: root. Path: "
2023-12-19T22:09:36.268+0800 [INFO] core: successfully mounted: type=system version="v1.15.4+builtin.vault" path=sys/ namespace="ID: root. Path: "
2023-12-19T22:09:36.269+0800 [INFO] core: successfully mounted: type=identity version="v1.15.4+builtin.vault" path=identity/ namespace="ID: root. Path: "
2023-12-19T22:09:36.283+0800 [INFO] core: successfully mounted: type=token version="v1.15.4+builtin.vault" path=token/ namespace="ID: root. Path: "
2023-12-19T22:09:36.284+0800 [INFO] rollback: Starting the rollback manager with 256 workers
2023-12-19T22:09:36.284+0800 [INFO] rollback: starting rollback manager
2023-12-19T22:09:36.285+0800 [INFO] core: restoring leases
2023-12-19T22:09:36.286+0800 [INFO] expiration: lease restore complete
2023-12-19T22:09:36.290+0800 [INFO] identity: entities restored
2023-12-19T22:09:36.290+0800 [INFO] identity: groups restored
2023-12-19T22:09:36.290+0800 [INFO] core: usage gauge collection is disabled
2023-12-19T22:09:36.293+0800 [INFO] core: Recorded vault version: vault version=1.15.4 upgrade time="2023-12-19 14:09:36.290555421 +0000 UTC" build date=2023-12-04T17:45:28Z
2023-12-19T22:09:36.852+0800 [INFO] core: post-unseal setup complete
2023-12-19T22:09:36.859+0800 [INFO] core: root token generated
2023-12-19T22:09:36.866+0800 [INFO] core: pre-seal teardown starting
2023-12-19T22:09:36.866+0800 [INFO] core: stopping raft active node
2023-12-19T22:09:36.866+0800 [INFO] rollback: stopping rollback manager
2023-12-19T22:09:36.866+0800 [INFO] core: pre-seal teardown complete5.2 查看vault服务状态
5.2.1 dev模式
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 1
Threshold 1
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type inmem
Cluster Name vault-cluster-5f63f394
Cluster ID 435b526b-a3fa-f015-455b-efdc6391fade
HA Enabled falsedev模式下,sealed为false,HA Enabled为false。
dev模式不可用于生产环境。
5.2.2 生产模式
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 0/3
Unseal Nonce n/a
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true5.3 server 初始化
以下均在生产模式下演示。
$ vault operator init
Unseal Key 1: omkhzlj2RQI0uYTqFjLnc49yuKNMcuzB6u0vJ8j0zFd8
Unseal Key 2: VRaHponsWwEV7R2860A/jIBEielq+Nq2b6qBeofjdWxL
Unseal Key 3: 8JjtnzwqYYzC3/RA2iojCfctb0UXS2hYbEfWFL7Vfppc
Unseal Key 4: dFhdpx2ehGdky1YnUsMz2hN4YRtZ7G8DkABD/v4xFFGF
Unseal Key 5: 9iUEPwMERYWPyago35VthjFvyST0IofsVnWMgvbR9CwT
Initial Root Token: hvs.V1KqX0oFDc9Hj1xTy6Iini3I
Vault initialized with 5 key shares and a key threshold of 3. Please securely
distribute the key shares printed above. When the Vault is re-sealed,
restarted, or stopped, you must supply at least 3 of these keys to unseal it
before it can start servicing requests.
Vault does not store the generated root key. Without at least 3 keys to
reconstruct the root key, Vault will remain permanently sealed!
It is possible to generate new unseal keys, provided you have a quorum of
existing unseal keys shares. See "vault operator rekey" for more information.5.4 对 key 解封
初始化后,vault 还不知道如何使用具体的存储,因此处于封锁状态,在上面的 output 内容中有这样一句话:
Vault initialized with 5 key shares and a key threshold of 3.
说明 threshold 为 3,也就是说至少要对 3 个 key 执行解封操作后,server 才可以使用。
$ vault operator unseal omkhzlj2RQI0uYTqFjLnc49yuKNMcuzB6u0vJ8j0zFd8
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 1/3
Unseal Nonce 31e20274-c828-a988-5221-6b4b5643a04f
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true
$ vault operator unseal VRaHponsWwEV7R2860A/jIBEielq+Nq2b6qBeofjdWxL
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed true
Total Shares 5
Threshold 3
Unseal Progress 2/3
Unseal Nonce 31e20274-c828-a988-5221-6b4b5643a04f
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
HA Enabled true
$ vault operator unseal 8JjtnzwqYYzC3/RA2iojCfctb0UXS2hYbEfWFL7Vfppc
Key Value
--- -----
Seal Type shamir
Initialized true
Sealed false
Total Shares 5
Threshold 3
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type raft
Cluster Name vault-cluster-c341ffa4
Cluster ID 17b670dc-768d-2c9b-56d1-37fabca8eb16
HA Enabled true
HA Cluster n/a
HA Mode standby
Active Node Address <none>
Raft Committed Index 31
Raft Applied Index 31每解封一个key,其Unseal Progress就会发生改变。
5.5 engine管理
5.5.1 secrets enable创建engine
和其他数据存储一样,要使用 vault 我们同样需要创建 database,但在 vault 中,数据是按照类似文件系统的 path 来组织的,需要用下面的命令来开启相应的 engine。
secrets enable 命令在指定路径上启用一个机密引擎。如果指定路径上已挂载机密引擎,则返回错误。机密引擎在启用后,通常需要进行配置。不同的机密引擎配置各异。
$ vault secrets enable -path=secret kv创建了一个 path secret,并且以 kv 类型进行存储。
如果不带-path参数,则默认以engine名称为path路径。如:
$ vault secrets enable kv Success! Enabled the kv secrets engine at: kv/ $ vault secrets list Path Type Accessor Description ---- ---- -------- ----------- cubbyhole/ cubbyhole cubbyhole_b001b5a0 per-token private secret storage identity/ identity identity_f5a58a34 identity store kv/ kv kv_d3b32d5b n/a secret/ kv kv_c7da4356 n/a sys/ system system_a72e3011 system endpoints used for control, policy and debugging
-audit-non-hmac-request-keys(string: "")- 指定在请求的数据对象中的哪些键不会被审计设备 HMAC 哈希。请注意,可以通过多次使用该选项来指定多个键,每次指定一个键-audit-non-hmac-response-keys(string: "")- 指定在响应的数据对象中的哪些键不会被审计设备 HMAC 哈希。请注意,可以通过多次使用该选项来指定多个键,每次指定一个键-default-lease-ttl(duration: "")- 该机密引擎生成的令牌租约的默认 TTL。如果未指定,则默认为 Vault 服务器全局配置的默认租约 TTL,或先前为该机密引擎配置过的值-description(string: "")- 关于此身份验证方法的易于阅读的描述-force-no-cache(bool: false)- 强制机密引擎禁用缓存。如果未加指定,则默认为 Vault 服务器全局配置的缓存设置。该参数不会影响底层存储对加密数据的缓存-local(bool: false)- 将此机密引擎标记为本地可用。本地可用的引擎数据不会被复制或是被复制机制删除-max-lease-ttl(duration: "")- 该机密引擎租约的最大 TTL 约束,如果未加指定,则默认为 Vault 服务器全局配置的最大租约 TTL 设置-path(string: "")- 可以访问机密引擎的路径。所有机密引擎的路径都必须是唯一的。默认值为机密引擎的类型名称-passthrough-request-headers(string: "")- 将要发送到机密引擎的请求中的标头值。请注意,可以通过多次使用该选项来指定多个键,每次指定一个键-allowed-response-headers(string: "")- 允许机密引擎设置在响应上的标头值。请注意,可以通过多次使用该选项来指定多个键,每次指定一个键
5.5.2 secrets disable禁用engine
secrets disable 命令禁用指定路径上的机密引擎。使用的参数对应的是启用引擎的路径而不是引擎类型。所有该引擎创建的机密在引擎被禁用时都会被吊销,数据会被删除。
由于禁用引擎时所有相关机密都将被立即吊销,所以在吊销一个关联了大量机密的机密引擎时要格外小心,这有可能对系统造成很大的负载。
$ vault secrets disable kv/
Success! Disabled the secrets engine (if it existed) at: kv/
$ vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_b001b5a0 per-token private secret storage
identity/ identity identity_f5a58a34 identity store
secret/ kv kv_c7da4356 n/a
sys/ system system_a72e3011 system endpoints used for control, policy and debugging5.5.3 secrets list查看可用engine
secrets list 命令列出 Vault 服务器上启用了的机密引擎。该命令同样输出相关启用路径的信息,包括配置的 TTL 和易于阅读的描述。TTL 值为 system 表示正在使用系统默认值。
$ vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_b001b5a0 per-token private secret storage
identity/ identity identity_f5a58a34 identity store
secret/ kv kv_c7da4356 n/a
sys/ system system_a72e3011 system endpoints used for control, policy and debugging
$ vault secrets list -format=table
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_b001b5a0 per-token private secret storage
identity/ identity identity_f5a58a34 identity store
secret/ kv kv_c7da4356 n/a
sys/ system system_a72e3011 system endpoints used for control, policy and debugging
$ vault secrets list -format=json
{
"cubbyhole/": {
"uuid": "ac89f503-3d09-2cc2-5cc1-2da4a60804cc",
"type": "cubbyhole",
"description": "per-token private secret storage",
"accessor": "cubbyhole_b001b5a0",
"config": {
"default_lease_ttl": 0,
"max_lease_ttl": 0,
"force_no_cache": false
},
"options": null,
"local": true,
"seal_wrap": false,
"external_entropy_access": false,
"plugin_version": "",
"running_plugin_version": "v1.15.4+builtin.vault",
"running_sha256": "",
"deprecation_status": ""
},
"identity/": {
"uuid": "61ce74da-62cd-69e2-b788-c9238d91882b",
"type": "identity",
"description": "identity store",
"accessor": "identity_f5a58a34",
"config": {
"default_lease_ttl": 0,
"max_lease_ttl": 0,
"force_no_cache": false,
"passthrough_request_headers": [
"Authorization"
]
},
"options": null,
"local": false,
"seal_wrap": false,
"external_entropy_access": false,
"plugin_version": "",
"running_plugin_version": "v1.15.4+builtin.vault",
"running_sha256": "",
"deprecation_status": ""
},
"secret/": {
"uuid": "26e2cdf4-8f80-d61a-07b5-690d37f926d5",
"type": "kv",
"description": "",
"accessor": "kv_c7da4356",
"config": {
"default_lease_ttl": 0,
"max_lease_ttl": 0,
"force_no_cache": false
},
"options": null,
"local": false,
"seal_wrap": false,
"external_entropy_access": false,
"plugin_version": "",
"running_plugin_version": "v0.16.1+builtin",
"running_sha256": "",
"deprecation_status": "supported"
},
"sys/": {
"uuid": "563fa19d-9329-f59a-e81f-a8ebf7859bb2",
"type": "system",
"description": "system endpoints used for control, policy and debugging",
"accessor": "system_a72e3011",
"config": {
"default_lease_ttl": 0,
"max_lease_ttl": 0,
"force_no_cache": false,
"passthrough_request_headers": [
"Accept"
]
},
"options": null,
"local": false,
"seal_wrap": true,
"external_entropy_access": false,
"plugin_version": "",
"running_plugin_version": "v1.15.4+builtin.vault",
"running_sha256": "",
"deprecation_status": ""
}
}5.5.4 secrets move移动存储路径
secrets move 命令将现有的机密引擎移动到新路径。旧机密引擎相关的所有租约都将被吊销,但与机密引擎关联的所有配置都将保留。
移动现有的机密引擎将吊销旧引擎的所有租约。
将现有机密引擎从 secret/ 移动到 kv/:
$ vault secrets move secret/ kv/5.5.5 secrets tune 调整机密信息配置
secrets tune 命令调整指定路径上的机密引擎的配置选项。参数使用的是启用机密引擎的路径,而不是引擎类型。
$ vault read secret/creds/
Key Value
--- -----
refresh_interval 768h
passcode my-long-passcode
$ vault secrets tune -default-lease-ttl=18h secret/creds/
Success! Tuned the secrets engine at: secret/creds/
$ vault read secret/creds/
Key Value
--- -----
refresh_interval 18h
passcode my-long-passcode5.6 封存vault
如果觉得系统存在风险,可以使用root token登录vault,执行以下命令将vault重新封印 。
$ vault login -address='http://127.0.0.1:8200' hvs.EjKzWarVoX2yQOQkNTrO3RCd
$ vault operator seal -address='http://127.0.0.1:8200'5.7 重建root token
如果root token泄露或root token不甚丢失,可以使用本节的方法重建root token。重建 Root 令牌有两种办法,分别是一次性密码(one time password)简称OPT,以及 pgp。本次使用OPT方式重建。
$ export VAULT_ADDR=http://127.0.0.1:8200
$ vault operator generate-root -init ##生成OPT密码,这个密码我们需要记住,后面需要用到下面来重新生成root token,会提示我们输入shared key,因为默认是需要三个shared key来生成master key,所以命令需要执行三次。最后一次命令执行时,会生成一个encoded token,我们使用otp可以将它解码为root token。
$ vault operator generate-root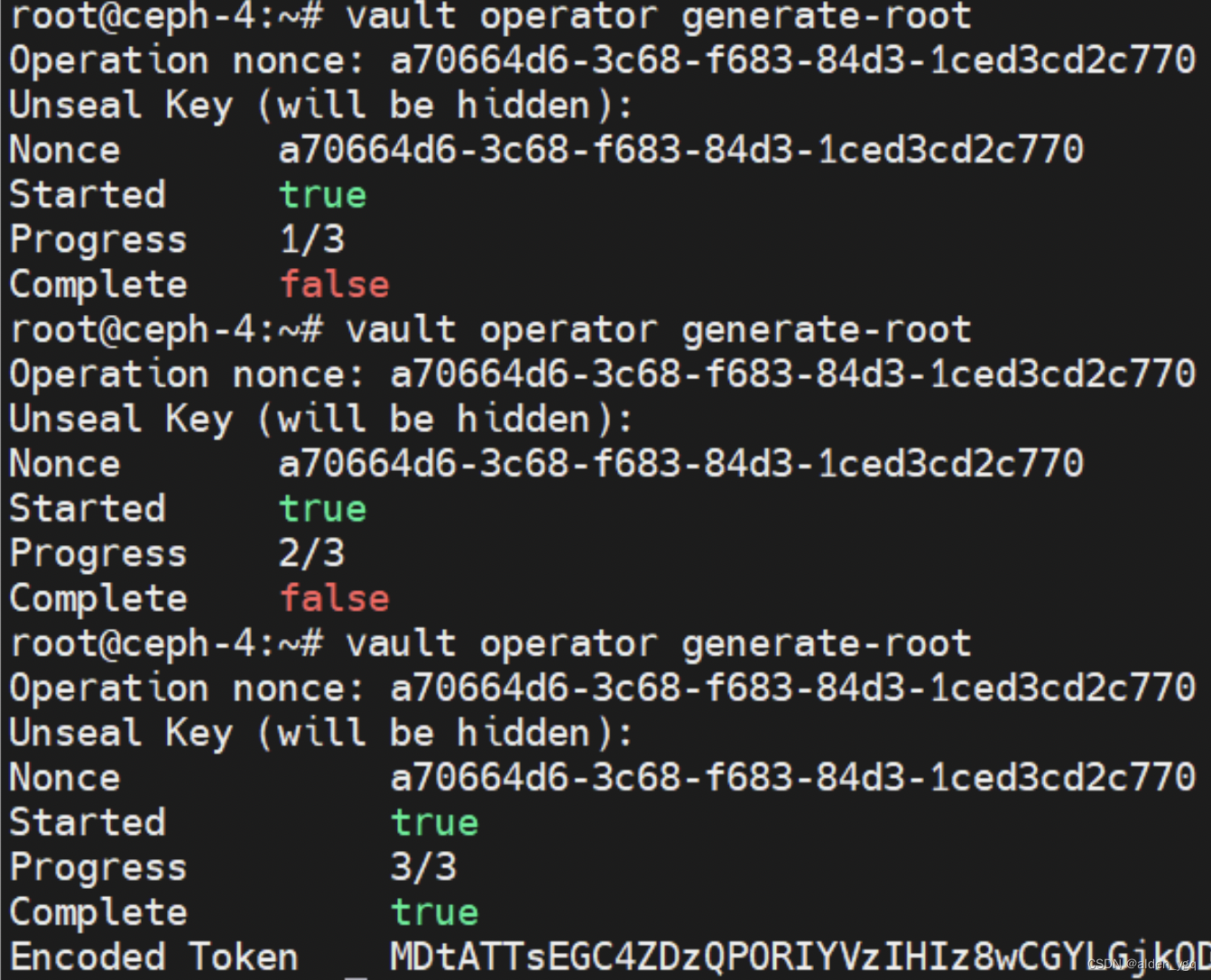
解码root token。
$ vault operator generate-root -decode=MDtATTsEGC4ZDzQPORIYVzIHIz8wCGYLGjkODA -otp=XM3cMjJcIjSzxWo6CFuMGk0CjhbY ##使用这个就可以重新生成root token了
hvs.vnRMPeguAEwaqAVrwcVHpQlU5.8 Vault 登录
$ vault login $VAULT_TOKEN
WARNING! The VAULT_TOKEN environment variable is set! The value of this
variable will take precedence; if this is unwanted please unset VAULT_TOKEN or
update its value accordingly.
Success! You are now authenticated. The token information displayed below
is already stored in the token helper. You do NOT need to run "vault login"
again. Future Vault requests will automatically use this token.
Key Value
--- -----
token hvs.gWGPZU3tEqUCetkNZVDIDUOt
token_accessor 8A3unHHaMm8VH2Vao2JtkZRk
token_duration ∞
token_renewable false
token_policies ["root"]
identity_policies []
policies ["root"]5.9 查找存储path
5.9.1 查找secret list
$ vault secrets list
Path Type Accessor Description
---- ---- -------- -----------
cubbyhole/ cubbyhole cubbyhole_b001b5a0 per-token private secret storage
identity/ identity identity_f5a58a34 identity store
secret/ kv kv_c7da4356 n/a
sys/ system system_a72e3011 system endpoints used for control, policy and debugging5.9.2 查找指定secret path list
$ vault kv list secret
Keys
----
creds
foo如果有多级,可逐级查找。
$ vault kv list secret/creds
No value found at secret/creds5.9.3 查找key=value值
$ vault kv get secret/creds
====== Data ======
Key Value
--- -----
passcode my-long-passcode5.9.4 查看kv值租期
$ vault read secret/creds
Key Value
--- -----
refresh_interval 18h
passcode my-long-passcode6 数据存储
storage 节配置存储后端,代表了 Vault 信息的持久化存储位置。每个后端都有优点、缺点、优势和权衡。例如一些后端支持高可用性,而另一些则提供更强大的备份和恢复功能。
6.1 本地存储
6.1.1 raft方式
本地以raft算法存储方式存储。
storage "raft" {
path = "/data/vault"
node_id = "node-1"
}6.1.2 本地文件方式
本地以file方式存储。
storage "file" {
path = "/mnt/vault/data"
}6.2 远端存储
6.2.1 Etcd存储实战
配置文件:
$ cat /etc/vault/config.hcl
storage "etcd" {
address = "http://10.220.43.206:2379,http://10.220.43.207:2379,http://10.220.43.208:2379"
path = "secret"
ha_enabled = "true"
etcd_api = "v3"
request_timeout = "5s"
}
listener "tcp" {
address = "127.0.0.1:8200"
tls_disable = "true"
}
api_addr = "http://127.0.0.1:8200"
cluster_addr = "https://127.0.0.1:8201"
ui = true7 常见问题
7.1 无法访问vault 8220端口
报错现象
$ vault status
Error checking seal status: Get "https://127.0.0.1:8200/v1/sys/seal-status": http: server gave HTTP response to HTTPS client第一步:确认vault服务是否启动
$ ps -ef | grep vault
root 24113 22486 0 20:18 pts/1 00:00:00 vault server -config=/etc/vault/config.hcl第二步:确定8200端口是否开启
$ netstat -ntpl | grep 8200
tcp 0 0 127.0.0.1:8200 0.0.0.0:* LISTEN 24113/vault 第三步:环境变量
$ echo $VAULT_ADDR
http://127.0.0.1:8200
$ echo $VAULT_TOKENVAULT_TOKEN是空的,设置后重试。
$ echo $VAULT_TOKEN
hvs.gWGPZU3tEqUCetkNZVDIDUOt第四步:验证
$ vault status
Key Value
--- -----
Seal Type shamir
Initialized false
Sealed true
Total Shares 0
Threshold 0
Unseal Progress 0/0
Unseal Nonce n/a
Version 1.15.4
Build Date 2023-12-04T17:45:28Z
Storage Type etcd
HA Enabled true7.2 获取key失败
报错现象
$ vault kv list secret/
Error making API request.
URL: GET http://127.0.0.1:8200/v1/sys/internal/ui/mounts/secret
Code: 403. Errors:
* preflight capability check returned 403, please ensure client's policies grant access to path "secret/"提示没有secret路径。
启动一个secret的kv类型引擎。
$ vault secrets enable -path=secret kv
Success! Enabled the kv secrets engine at: secret/
$ vault kv list secret/
No value found at secret设置一个kv存储。
$ vault kv put secret/creds passcode=my-long-passcode
Success! Data written to: secret/creds
$ vault kv list secret/
Keys
----
creds
foo
$ vault kv get secret/creds
====== Data ======
Key Value
--- -----
passcode my-long-passcode