目录
功能介绍
“.pem”为数字证书的常见格式,可以通过离线的方式直接导入路由器。同时通过“pfx2pem.exe”这个工具也可以将生成的“.pfx”格式的证书转换为".pem"格式,再导入路由器;pfx到pem的转换软件,参见附件。
一、组网需求
将“.pem”格式的证书文件导入路由器。
二、组网拓扑
三、配置要点
1、确认路由器的系统时间是否正确
2、导入CA根证书
3、导入路由器私钥
4、导入路由器证书
5、配置忽略证书有效性和时间检查(可选)
注意:使用写字板程序打开该证书文件后,可以看到路由器私钥、路由器证书、和CA根证书。可以通过以下方法来区分这几个证书信息:
(1)路由器私钥:从“-----BEGIN RSA PRIVATE KEY-----”到“-----END RSA PRIVATE KEY-----”结束,之间的内容为路由器私钥信息,证书导入时将路由器私钥信息(包括“-----BEGIN RSA PRIVATE KEY-----”和“-----END RSA PRIVATE KEY-----”)粘贴到路由器中。
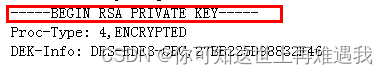
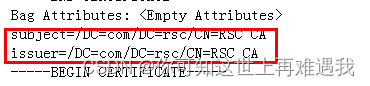
(2)路由器证书:关注“subject”与“issuer”字段后的内容,如果“subject”与“issuer”字段内容不同,则后继的“-----BEGIN CERTIFICATE-----”和“-----END CERTIFICATE-----”之间即为路由器证书信息。证书导入时将路由器证书信息(包括“-----BEGIN CERTIFICATE-----”和“-----END CERTIFICATE-----”)粘贴到路由器中。

(3)CA根证书:关注“subject”与“issuer”字段后的内容,如果“subject”与“issuer”字段内容完全相同,则后继的“-----BEGIN CERTIFICATE-----”和“-----END CERTIFICATE-----”之间即为CA根证书信息。证书导入时将CA根证书信息(包括“-----BEGIN CERTIFICATE-----”和“-----END CERTIFICATE-----”)粘贴到路由器中。
四、配置步骤
1、确认路由器的系统时间是否正确
Ruijie#show clock
05:01:40 UTC Thu, Mar 6, 2003
注意:证书涉及到吊销列表,证书的有效期等属性,和时间关联,做证书之前,需要保证时间同步。
条件允许的情况下,建议设置NTP。
2、导入CA根证书
3、导入路由器私钥
4、导入路由器证书
具体操作步骤如下:
Ruijie(config)#crypto pki import ruijie pem terminal 123456//通过crypto pki import命令导入证书,并指定trustpoint名称为ruijie,PEM证书密码为123456.
% Enter PEM-formatted CA certificate.
% End with a blank line or "quit" on a line by itself.
-----BEGIN CERTIFICATE-----
MIIDsjCCApqgAwIBAgIQZcc6gCrozIVP+65pSDNoXDANBgkqhkiG9w0BAQUFADA7
MRMwEQYKCZImiZPyLGQBGRYDY29tMRMwEQYKCZImiZPyLGQBGRYDcnNjMQ8wDQYD
VQQDEwZSU0MgQ0EwHhcNMTAxMjI5MDUzMDAwWhcNMjAxMjI5MDUzOTMwWjA7MRMw
EQYKCZImiZPyLGQBGRYDY29tMRMwEQYKCZImiZPyLGQBGRYDcnNjMQ8wDQYDVQQD
EwZSU0MgQ0EwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQDncaGha6dq
NJbABhyV/v9w+1XZQceI1XQyOSf8+33x/LeA4f49e39/1oWzI29chHRBvzS0vyvx
4QY0Z/4Ecjh17QXHAyOVWatc/fTRLfEWn1LU+PsQA44tqs7RbxuzVQpzzovQmJw9
VyjC13HUSdquL+kqVe9DqMKKzUaTctQ16YePDWfCUA0XKnxd/rdYSrva7U6+papx
v0AdWmLeNNAv36wlar4n12LTppcXo0/oxN2eVfK6TBkT8W47NXRegYPGFAcTR/BF
QK8eMFQLiwi1CffsNoE1NpmhDUtYwRQ3m/JsY0tgyKFgMMibkbqBslq33p6zXvUE
h41qned5Azg1AgMBAAGjgbEwga4wCwYDVR0PBAQDAgGGMA8GA1UdEwEB/wQFMAMB
Af8wHQYDVR0OBBYEFIJiMJD5jU//bnOzNzd7Q9JffyPjMF0GA1UdHwRWMFQwUqBQ
oE6GJWh0dHA6Ly9yc2MtY2EvQ2VydEVucm9sbC9SU0MlMjBDQS5jcmyGJWZpbGU6
Ly9cXFJTQy1DQVxDZXJ0RW5yb2xsXFJTQyBDQS5jcmwwEAYJKwYBBAGCNxUBBAMC
AQAwDQYJKoZIhvcNAQEFBQADggEBAFazbsPV0FXCpsRx5xk/ErOyzXf1cbE4eqWL
OKes0OoWA6y1Fg9zvxWX7z5SorPByJqC9Ci+ej0fmxaUqMqtd3Dx+YeFLFryszHu
YdcaNrU6YAbUHL/UvNcgwM8DLm53AagSZoV3qV4g6jra5osd7/MtObuFclgH09L2
0J8oclBJZOODk4GWsQkyhgTEAiA9WXwC470GiApXTqeQKO4Zo6io2GtVj571UIt8
QaVt237eiZtYQoadaQh6maH1wM87RXWxB+KwLOzk8TqxAy1ke0yASeG8Z23s3/pW
rlq0rdOCEhpoXggAttVRcfGEf/rnVHJr/z44HjeAeMawVqvxWjA=
-----END CERTIFICATE-----
quit//以上粘贴CA根证书信息,并通过quit退出
Certificate has the following attributes:
MD5 fingerprint: F9637FD9 3D5F5C33 D6E067C3 5F7952CC
SHA1 fingerprint: FC07C4BE 8E769C57 C4182A80 2904D9F1 A0DE80D5
%% Do you accept this certificate?[yes/no]:yes //输入yes接受该CA根证书
% CA Certificate successfully readed
%% All ca certificate imported?[yes/no]:yes //如果存在多级根证书,则输入no继续导入二级CA根证书
% Enter PEM-formatted encrypted private key.
% End with "quit" on a line by itself.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: DES-EDE3-CBC,27BB225D98832F46
CjJAF3LOLuKyuhgFTJG2obem5X7Yhy0c6YDP+rKKxATUIL5iZvYw8EcQcPO3+wYr
syIN/5LSsvJE0hVttnVF9mlcbMQhI5y39ZmYc1saoNKu8HXA64CiMbzfadsnp+37
shcHf3xnBJ2b8zLZSbj8hdw5qN2d9N4vlQE3pXGuHZxPAJ9rJ3hnA5PKMbFzWq/T
uxW+w0S2s89Q4Yh8X/BBCMLOU1hyrubluDGq2Hct+jBUQIIQFiKEi4kh2m6Jn15h
Un6zmKzb3dp9fNGSA8Z8ZTWHbZXxBEckfBaLlasxR+qLlP1SYZg5D8fLGxtt1olZ
mhE17CAsychvXqJ/izKcqKaHl0W75jbJBseSXyHqOSSN9ZohbBWX/RtBe3tfJnpy
CTwuwSi+XRAYqmHdTZZFi3HWPhuPI2hFntoldUcFDJnPhNfqECy36V/uhY5yQS39
/n4ZE2TJRDLpYA9W4Wtu6NyhsoSLvB2Se5TktiyjRQ/WNJ2eRSOMigDCoRkjnrkl
S3qLoPfLRhTZM4lzTvOu9lcwbDT5rxAQbDdIDgwZ7VlZcsrLqRt3Az0BQVYrk48w
5Q1pw4We89tGUmfWxLhawyTnh3OWesuQs+eGMt+aZ1jv1cOBtLXu5F4lQXhbWXxn
RVQUxmjd3OMJY792p3T0bEWGj/A+4pqoLCFc8BYNMqnXVxkFx1rKYk9mTiSH00q5
IKjDb037ZqWtfJp5BawE4tQji+P0aQBOu4HeLTmC3vDffDdSOa563+w35jPgGdRd
jfCs5j4rye9TjyxPOzJlL8dOB/LseFcQKylCRY2fIuFMOIRdacyrVw==
-----END RSA PRIVATE KEY-----
quit//以上粘贴路由器私钥信息,并通过quit退出
% RSA private key successfully imported.
% Enter PEM-formatted certificate.
% End with a blank line or "quit" on a line by itself.
-----BEGIN CERTIFICATE-----
MIIEUTCCAzmgAwIBAgIKYQ6LcwAAAAAAGTANBgkqhkiG9w0BAQUFADA7MRMwEQYK
CZImiZPyLGQBGRYDY29tMRMwEQYKCZImiZPyLGQBGRYDcnNjMQ8wDQYDVQQDEwZS
U0MgQ0EwHhcNMTEwNTE1MDc1NTMwWhcNMTIwNTE1MDgwNTMwWjCBgDELMAkGA1UE
BhMCQ04xDzANBgNVBAgTBmZ1amlhbjEPMA0GA1UEBxMGZnV6aG91MQ8wDQYDVQQK
EwZydWlqaWUxDDAKBgNVBAsTA3RhYzENMAsGA1UEAxMEdGVzdDEhMB8GCSqGSIb3
DQEJARYSdGVzdEBydWlqaWUuY29tLmNuMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCB
iQKBgQCwr2+43hE0JFNMEPFVYGoQd59Izz7b1/IiyiaADmgVbvVR8iD8NEEV84HZ
y1pCuGNNuUzC3KYaO9Cu8/rny2Kh2Nj7+7URDC7VmGxfjWtZsNIhMTFpypADfsSt
X15PUUjK99S47ep5qF+p9MK4SS586CMWbjn3+vDmOrjIoIFJCwIDAQABo4IBkzCC
AY8wDgYDVR0PAQH/BAQDAgTwMEQGCSqGSIb3DQEJDwQ3MDUwDgYIKoZIhvcNAwIC
AgCAMA4GCCqGSIb3DQMEAgIAgDAHBgUrDgMCBzAKBggqhkiG9w0DBzAdBgNVHQ4E
FgQUkZzrJ8oXlfZDgX3/DnUzzZsOalEwEwYDVR0lBAwwCgYIKwYBBQUHAwIwHwYD
VR0jBBgwFoAUgmIwkPmNT/9uc7M3N3tD0l9/I+MwXQYDVR0fBFYwVDBSoFCgToYl
aHR0cDovL3JzYy1jYS9DZXJ0RW5yb2xsL1JTQyUyMENBLmNybIYlZmlsZTovL1xc
UlNDLUNBXENlcnRFbnJvbGxcUlNDIENBLmNybDCBggYIKwYBBQUHAQEEdjB0MDgG
CCsGAQUFBzAChixodHRwOi8vcnNjLWNhL0NlcnRFbnJvbGwvUlNDLUNBX1JTQyUy
MENBLmNydDA4BggrBgEFBQcwAoYsZmlsZTovL1xcUlNDLUNBXENlcnRFbnJvbGxc
UlNDLUNBX1JTQyBDQS5jcnQwDQYJKoZIhvcNAQEFBQADggEBABhU7nMrGyB9mW5J
C+qcpIrF/wnuXJI0o9HHVD1BXghuEOoc+DAPd1F2BNs2t3j8GPAUTsK4uzhODaN2
gn2yV3kLrlJ0UXTBmC7rPoGQPPoB17j01S6s3Ugb5SrEUxQPG0Sr4XgIJHfZbi+e
JWpq0ol3jfCyClV7Zqvoa0od+kvMENPzoKNsv/gLVYRR+YH0RraPvqCG38S9B+K2
42Mxn+NPDUHje+jJv/XhMcsm45UbL8TctUDCJ6OqoyZNK0Lz/y3vDxMMu8AZ09rU
rEFZ2orHgsev6mwySjssBg681Bq6xh1jHZ9Wh4PS4dGOQCtx+VIdY6qY50w5Ve63
Zhd/09E=
-----END CERTIFICATE-----
quit//以上粘贴路由器证书信息,并通过quit退出
% Router Certificate successfully imported//所有证书导入完成
5、配置忽略证书有效性和时间检查(可选)
crypto pki trustpoint ruijie//进入证书的相应trustpoint
time-check none//关闭证书的时间检查
revocation-check none //不检查证书是否被吊销
注意:
1、RSR10-02设备没有时钟芯片,断电后时间会初始化为1970-01-01导致基于数字证书的IPSEC VPN协商失败,必须配置NTP时间同步或在证书crypto pki trustpoint XX模式下配置timeout-check none来关闭时间检查。
2、所有非在线申请数字证书的3G客户端,需要在crypto pki trustpoint XX模式下配置revocation-check来关闭设备的CRL检查,除非设备能解析CA服务的域名地址。
五、配置验证
通过show crypto pki certificates ruijie可以查看名称为“ruijie”的证书信息:
Ruijie#show crypto pki certificates ruijie
% CA certificate info://CA根证书信息
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
65:c7:3a:80:2a:e8:cc:85:4f:fb:ae:69:48:33:68:5c
Issuer: DC=com, DC=rsc, CN=RSC CA
Validity
Not Before: Dec 29 05:30:00 2010 GMT
Not After : Dec 29 05:39:30 2020 GMT //证书的有效期,如果设备时间不在证书有效期内则证书无法使用
Subject: DC=com, DC=rsc, CN=RSC CA
Associated Trustpoints: ruijie
% Router certificate info://路由器证书信息
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
61:0e:8b:73:00:00:00:00:00:19
Issuer: DC=com, DC=rsc, CN=RSC CA
Validity
Not Before: May 15 07:55:30 2011 GMT
Not After : May 15 08:05:30 2012 GMT
Subject: C=CN, ST=fujian, L=fuzhou, O=ruijie, OU=tac, CN=test/[email protected]
Associated Trustpoints: ruijie