这里在基于PKI密钥认证在CentOS7.9搭建OpenVPN(一)基础上进行配置
基于PKI密钥认证在CentOS7.9搭建OpenVPN(一)_yjun89的博客-CSDN博客
配置openvpn基于证书+密码认证
我们这里基于密码认证使用pam认证,需要使用到MySQL,下面下来安装MySQL。
1、安装MySQL:
1.1、安装MySQL的源:
| [root@localhost ~]# rpm -Uvh https://repo.mysql.com/mysql57-community-release-el7.rpm Retrieving https://repo.mysql.com/mysql57-community-release-el7.rpm warning: /var/tmp/rpm-tmp.mQKDO8: Header V3 DSA/SHA1 Signature, key ID 5072e1f5: NOKEY Preparing... ################################# [100%] Updating / installing... 1:mysql57-community-release-el7-11 ################################# [100%] [root@localhost ~]# |
1.2、删除mariadb:
| [root@localhost ~]# rpm -e --nodeps `rpm -qa| grep mariadb` |
1.3、安装MySQL 7:
| [root@worker02 yum.repos.d]# yum install mysql-community-server mysql-community-devel -y |
| 报错提示: The GPG keys listed for the "MySQL 5.7 Community Server" repository are already installed but they are not correct for this package. Check that the correct key URLs are configured for this repository. 解决方法: rpm --import https://repo.mysql.com/RPM-GPG-KEY-mysql-2022 或者安装的时候不校验数字签名: yum -y install mysql-server --nogpgcheck--nogpgcheck |
1.4、启动MySQL,并找出默认密码:
| [root@slb1 openvpn-2.5.7]# systemctl start mysqld [root@slb1 openvpn-2.5.7]# grep 'pass' /var/log/mysqld.log 2022-10-31T22:53:22.400570Z 1 [Note] A temporary password is generated for root@localhost: 3rhhd?WE9&uv [root@slb1 openvpn-2.5.7]# |
1.5、连接进入MySQL,修改密码:
| [root@slb1 openvpn-2.5.7]# mysql -uroot -p Enter password: Welcome to the MySQL monitor. Commands end with ; or \g. Your MySQL connection id is 4 Server version: 5.7.40 Copyright (c) 2000, 2022, Oracle and/or its affiliates. Oracle is a registered trademark of Oracle Corporation and/or its affiliates. Other names may be trademarks of their respective owners. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. mysql> mysql> set global validate_password_policy=0; Query OK, 0 rows affected (0.00 sec) mysql> set global validate_password_length=1; Query OK, 0 rows affected (0.00 sec) mysql> alter user root@'localhost' identified by 'yjun#123'; Query OK, 0 rows affected (0.00 sec) mysql> |
1.6、先创建OpenVPN需要使用到的数据库和连接数据库的用户,数据库名称设置为openvpn,连接数据库的用户为vpn,用户密码设置为vpnadmin,然后再数据库中插入连接vpn的用户,操作如下:
1.6.1 创建OpenVPN所使用是数据库和连接数据库的账号
| mysql> create database openvpn; mysql> grant all on openvpn.* to vpn@localhost identified by 'vpnadmin'; mysql> flush privileges; |
1.6.2、在创建在好的openvpn库中创建表,别名设置为vpnuserta:
| mysql> use openvpn; mysql> create table vpnuserta (name char(50) NOT NULL,password char(200) default null,active int(10) not null default 1,primary key (name)); |
1.6.3 在表中插入用户:
| mysql> insert into vpnuserta (name,password) values('qd',password('qd123')); mysql> insert into vpnuserta (name,password) values('test1',password('123456')); mysql> desc vpnuserta; |
2、安装基于pam认证的插件,安装pam-mysql
2.1、下载网站
https://github.com/NigelCunningham/pam-MySQL/tags
下载包地址:
https://codeload.github.com/NigelCunningham/pam-MySQL/tar.gz/refs/tags/v0.8.1
2.2、 安装依赖关系:
| [root@localhost ~]# yum install autoconf libtool make gcc mysql-community-devel pam-devel -y |
2.3、上传下载的安装包至系统:
| [root@localhost ~]# rz rz waiting to receive. Starting zmodem transfer. Press Ctrl+C to cancel. Transferring pam-MySQL-0.8.1.tar.gz... 100% 48 KB 48 KB/sec 00:00:01 0 Errors [root@localhost ~]# |
2.4、解压tar包:
| [root@localhost ~]# tar xf pam-MySQL-0.8.1.tar.gz [root@localhost ~]# cd pam-MySQL-0.8.1 [root@localhost pam-MySQL-0.8.1]# |
2.4.1. 生成pam-mysql的configure配置文件,用于配置编译和安装参数
| [root@localhost pam-MySQL-0.8.1]# libtoolize [root@localhost pam-MySQL-0.8.1]# aclocal [root@localhost pam-MySQL-0.8.1]# autoheader [root@localhost pam-MySQL-0.8.1]# autoreconf -f -i |
2.5. Run "./configure". 可能需要下面的一些参数进行配置:
| [root@localhost pam-MySQL-0.8.1]# ./configure --with-pam-mods-dir=/usr/lib64/security/ checking for a BSD-compatible install... /usr/bin/install -c checking whether build environment is sane... yes .............................................................................................. config.status: executing depfiles commands config.status: executing libtool commands [root@localhost pam-MySQL-0.8.1]# |
2.6. 运行make命令构建模块
| [root@localhost pam-MySQL-0.8.1]# make make all-am make[1]: Entering directory `/root/pam-MySQL-0.8.1' ................................................................................ make[1]: Leaving directory `/root/pam-MySQL-0.8.1' [root@localhost pam-MySQL-0.8.1]# |
2.7. 运行 "make install" 安装module.
| [root@localhost pam-MySQL-0.8.1]# make install make[1]: Entering directory `/root/pam-MySQL-0.8.1' .............................................................................. /usr/bin/mkdir -p '/usr/lib64/security/' /bin/sh ./libtool --mode=install /usr/bin/install -c pam_mysql.la '/usr/lib64/security/' libtool: install: /usr/bin/install -c .libs/pam_mysql.so /usr/lib64/security/pam_mysql.so .............................................................................................. make[1]: Leaving directory `/root/pam-MySQL-0.8.1' [root@localhost pam-MySQL-0.8.1]# |
3、生成openvpn pam验证配置文件连接数据库
创建openvpn pam验证配置文件
[root@worker02 pam_mysql-0.7RC1]# vim /etc/pam.d/openvpn_mysql
添加以下内容
| auth sufficient pam_mysql.so user=vpn passwd=vpnadmin host=localhost db=openvpn table=vpnuserta usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2 account required pam_mysql.so user=vpn passwd=vpnadmin host=localhost db=openvpn table=vpnuserta usercolumn=name passwdcolumn=password where=active=1 sqllog=0 crypt=2 |
保存退出
注意:这里的pam_mysql.so是调用/usr/lib64/security/目录下的pam_mysql.so如果编译安装pam_mysql时放在其他目录下会导致认证失败。
查看系统日志: tail /var/log/messages:
4、修改OpenVPN的server端的配置文件,启用用户名和密码认证和pam的认证:
配置文件/etc/server.conf配置,配配置文件中增加如下参数:
| username-as-common-name #启用用户名密码进行认证 plugin /usr/local/openvpn/lib/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn_mysql #调用MySQL插件 |
修改后如下
| port 1194 |
监听端口 |
| proto tcp |
监听协议 |
| dev tun |
采用路由隧道模式 |
| ca /etc/openvpn/ca.crt |
ca证书路径 |
| cert /etc/openvpn/server.crt |
服务器证书 |
| key /etc/openvpn/server.key # This file should be kept secret |
服务器秘钥 |
| dh /etc/openvpn/dh.pem |
密钥交换协议文件 |
| server 10.88.0.0 255.255.255.0 |
给vpn客户端分配地址池,注意:不能和VPN服务器内网网段有相同 |
| ifconfig-pool-persist ipp.txt |
|
| push "10.88.0.0 255.255.255.0" |
通告分配给客户端的网络,还需要通告内网的网段,如果不通告内网网段,那么客户端接入后将无法访问内网中的主机 |
| push "172.16.10.0 255.255.255.0" |
通告企业总部内部网段,这样客户端接入后才可以访问总部内网中的主机 |
| push "redirect-gateway def1 bypass-dhcp" |
给网关 |
| push "dhcp-option DNS 8.8.8.8" |
dhcp分配dns |
| client-to-client |
VPN客户端之间互相通信 |
| keepalive 10 120 |
存活时间,10秒ping一次,120 如未收到响应则视为断线 |
| tls-auth /etc/openvpn/ta.key 0 # This file is secret |
开启TLS-auth,使用ta.key防御攻击,拒绝服务攻击的证书文件.服务器端的第二个参数值为0,客户端的为1 |
| cipher AES-256-GCM |
加密模式,默认使用CBC,需要改为GCM模式 |
| comp-lzo |
传输数据压缩 |
| max-clients 100 |
最多允许 100 客户端连接 |
| persist-key |
|
| persist-tun |
|
| status openvpn-status.log |
|
| log /var/log/openvpn.log |
|
| verb 3 |
|
| username-as-common-name |
#启用用户名密码进行认证 |
| plugin /usr/local/openvpn/lib/openvpn/plugins/openvpn-plugin-auth-pam.so openvpn_mysql |
#调用MySQL插件 |
5、在OpenVPN客户端配置文件也需要增加如下参数,就是启用用户和密码认证:
修改客户端安装路径config目录下的client.opvn配置文件,在最后增加
| auth-user-pass |
修改后完整如下:
| client dev tun proto tcp remote 113.65.10.1 33808 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert client.crt key client.key remote-cert-tls server tls-auth ta.key 1 cipher AES-256-GCM comp-lzo verb 3 auth-nocache auth-user-pass |
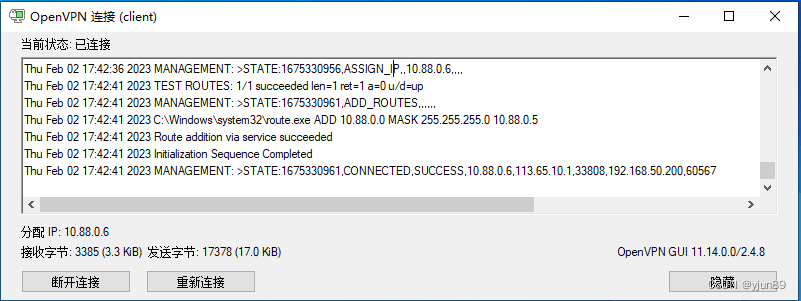
6、点开openvpn客户端:

如下需要使用用户密码进行认证:

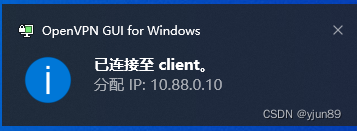
连接完成后: