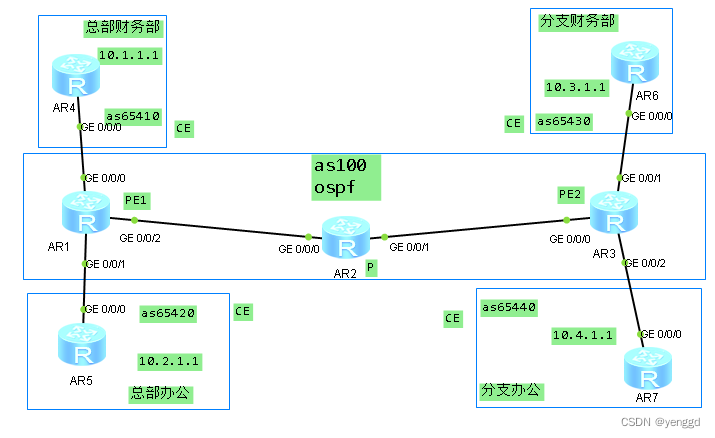
如图1所示:
1、AR4连接公司总部财务部、AR6连接分支机构财务部,AR4和AR6属于vpna;
2、 AR5连接公司总部办公、 AR7连接分支机构办公, AR5和 AR7属于vpnb。
公司要求通过部署BGP/MPLS IP VPN,实现总部和分支机构的安全互通,同时要求财务和办公区间数据隔离。
配置思路(AR1为pe1,AR2为p、AR3为pe2)
采用如下的思路配置BGP/MPLS IP VPN:
- P、PE之间配置OSPF,实现骨干网的IP连通性。
- PE、P上配置MPLS基本能力和MPLS LDP,建立MPLS LSP公网隧道,传输VPN数据。
- PE1和PE2上配置VPN实例,其中,vpna使用的VPN-target属性为111:1,vpnb使用的VPN-target属性为222:2,以实现相同VPN间互通,不同VPN间隔离。同时,与CE相连的接口和相应的VPN实例绑定,以接入VPN用户。
- PE1和PE2之间配置MP-IBGP,交换VPN路由信息。
- CE与PE之间配置EBGP,交换VPN路由信息。
AR1:
dis current-configuration
[V200R003C00]
sysname pe1
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
ip vpn-instance vpna
ipv4-family
route-distinguisher 100:1 //RD标签
vpn-target 111:1 export-extcommunity //RT标签
vpn-target 111:1 import-extcommunity //RT标签
ip vpn-instance vpnb
ipv4-family
route-distinguisher 100:2
vpn-target 222:2 export-extcommunity
vpn-target 222:2 import-extcommunity
mpls lsr-id 1.1.1.9
mpls
mpls ldp
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip binding vpn-instance vpna
ip address 10.1.1.2 255.255.255.0
interface GigabitEthernet0/0/1
ip binding vpn-instance vpnb
ip address 10.2.1.2 255.255.255.0
interface GigabitEthernet0/0/2
ip address 172.1.1.1 255.255.255.0
mpls
mpls ldp
interface NULL0
interface LoopBack1
ip address 1.1.1.9 255.255.255.255
bgp 100 // 在PE之间建立MP-IBGP对等体关系
peer 3.3.3.9 as-number 100
peer 3.3.3.9 connect-interface LoopBack1
ipv4-family unicast
undo synchronization
peer 3.3.3.9 enable
ipv4-family vpnv4
policy vpn-target
peer 3.3.3.9 enable
ipv4-family vpn-instance vpna
import-route direct
peer 10.1.1.1 as-number 65410
ipv4-family vpn-instance vpnb
import-route direct
peer 10.2.1.1 as-number 65420
ospf 1
area 0.0.0.0
network 1.1.1.9 0.0.0.0
network 172.1.1.0 0.0.0.255
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
AR2:
dis current-configuration [V200R003C00] # sysname p # snmp-agent local-engineid 800007DB03000000000000 snmp-agent # clock timezone China-Standard-Time minus 08:00:00 # portal local-server load flash:/portalpage.zip # drop illegal-mac alarm # wlan ac-global carrier id other ac id 0 # set cpu-usage threshold 80 restore 75 # mpls lsr-id 2.2.2.9 mpls # mpls ldp # #
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 172.1.1.2 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/1
ip address 172.2.1.1 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/2
interface NULL0
interface LoopBack1
ip address 2.2.2.9 255.255.255.255
ospf 1
area 0.0.0.0
network 2.2.2.9 0.0.0.0
network 172.1.1.0 0.0.0.255
network 172.2.1.0 0.0.0.255
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
AR3:
dis current-configuration
[V200R003C00]
sysname pe2
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
ip vpn-instance vpna
ipv4-family
route-distinguisher 200:1
vpn-target 111:1 export-extcommunity
vpn-target 111:1 import-extcommunity
ip vpn-instance vpnb
ipv4-family
route-distinguisher 200:2
vpn-target 222:2 export-extcommunity
vpn-target 222:2 import-extcommunity
mpls lsr-id 3.3.3.9
mpls
mpls ldp
aaa
authentication-scheme default
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipher % % K8m.Nt84DZ}e#<0`8bmE3Uw}% %
local-user admin service-type http
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 172.2.1.2 255.255.255.0
mpls
mpls ldp
interface GigabitEthernet0/0/1
ip binding vpn-instance vpna
ip address 10.3.1.2 255.255.255.0
interface GigabitEthernet0/0/2
ip binding vpn-instance vpnb
ip address 10.4.1.2 255.255.255.0
interface NULL0
interface LoopBack1
ip address 3.3.3.9 255.255.255.255
bgp 100
peer 1.1.1.9 as-number 100
peer 1.1.1.9 connect-interface LoopBack1
ipv4-family unicast
undo synchronization
peer 1.1.1.9 enable
ipv4-family vpnv4
policy vpn-target
peer 1.1.1.9 enable
ipv4-family vpn-instance vpna
import-route direct
peer 10.3.1.1 as-number 65430
ipv4-family vpn-instance vpnb
import-route direct
peer 10.4.1.1 as-number 65440
ospf 1
area 0.0.0.0
network 3.3.3.9 0.0.0.0
network 172.2.1.0 0.0.0.255
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
AR4:
dis cu
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 10.1.1.1 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
bgp 65410
peer 10.1.1.2 as-number 100
ipv4-family unicast
undo synchronization
import-route direct
peer 10.1.1.2 enable
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
AR5:
dis cu
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 10.2.1.1 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
bgp 65420
peer 10.2.1.2 as-number 100
ipv4-family unicast
undo synchronization
import-route direct
peer 10.2.1.2 enable
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
Ar6:
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 10.3.1.1 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
bgp 65430
peer 10.3.1.2 as-number 100
ipv4-family unicast
undo synchronization
import-route direct
peer 10.3.1.2 enable
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
Ar7:
dis cu
dis current-configuration
[V200R003C00]
snmp-agent local-engineid 800007DB03000000000000
snmp-agent
clock timezone China-Standard-Time minus 08:00:00
portal local-server load flash:/portalpage.zip
drop illegal-mac alarm
wlan ac-global carrier id other ac id 0
set cpu-usage threshold 80 restore 75
firewall zone Local
priority 15
interface GigabitEthernet0/0/0
ip address 10.4.1.1 255.255.255.0
interface GigabitEthernet0/0/1
interface GigabitEthernet0/0/2
interface NULL0
bgp 65440
peer 10.4.1.2 as-number 100
ipv4-family unicast
undo synchronization
import-route direct
peer 10.4.1.2 enable
user-interface con 0
authentication-mode password
user-interface vty 0 4
user-interface vty 16 20
wlan ac
return
查看:
执行display mpls ldp session命令可以看到显示结果中Status项为“Operational”。
在PE设备上执行display ip vpn-instance verbose命令可以看到VPN实例的配置情况。各PE能ping通自己接入的CE。
ping -vpn-instance vpn-instance-name -a source-ip-address dest-ip-address命令中的参数-asource-ip-address,否则可能ping不通。
在PE设备上执行display bgp peer或display bgp vpnv4 all peer命令,可以看到PE之间的BGP对等体关系已建立,并达到Established状态
执行display bgp vpnv4 vpn-instance peer命令,可以看到PE与CE之间的BGP对等体关系已建立,并达到Established状态。
在PE设备上执行display ip routing-table vpn-instance命令,可以看到去往对端CE的路由。