提示:用到的工具 Od
1 .打开OD 附加Wechat.exe进程,选择Wechatwin.dll模块

选择Wechatwin.dll模块

右键Find搜索字符串SessionMgr::processMsgAdd
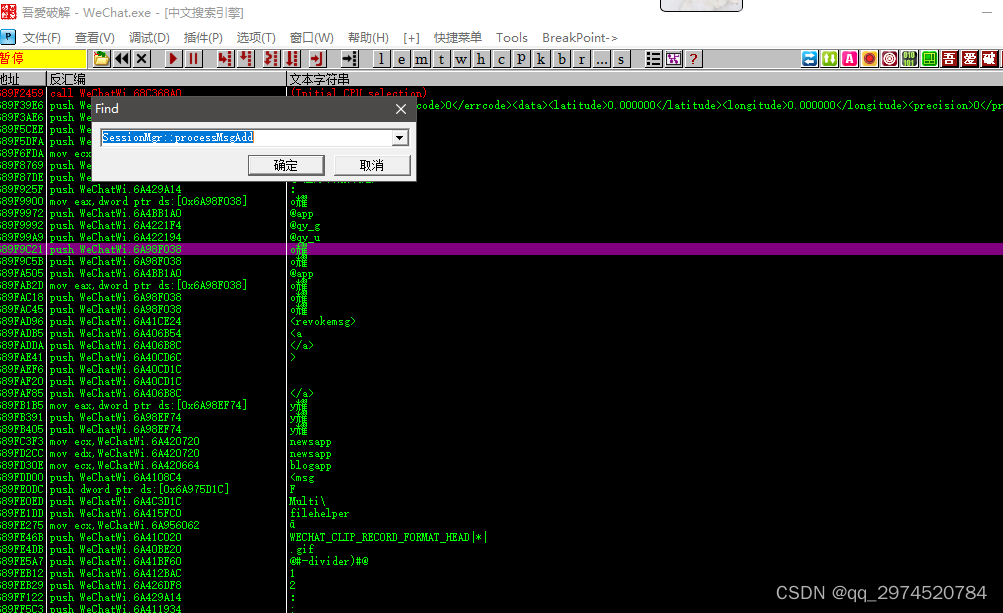
找到后双击进去
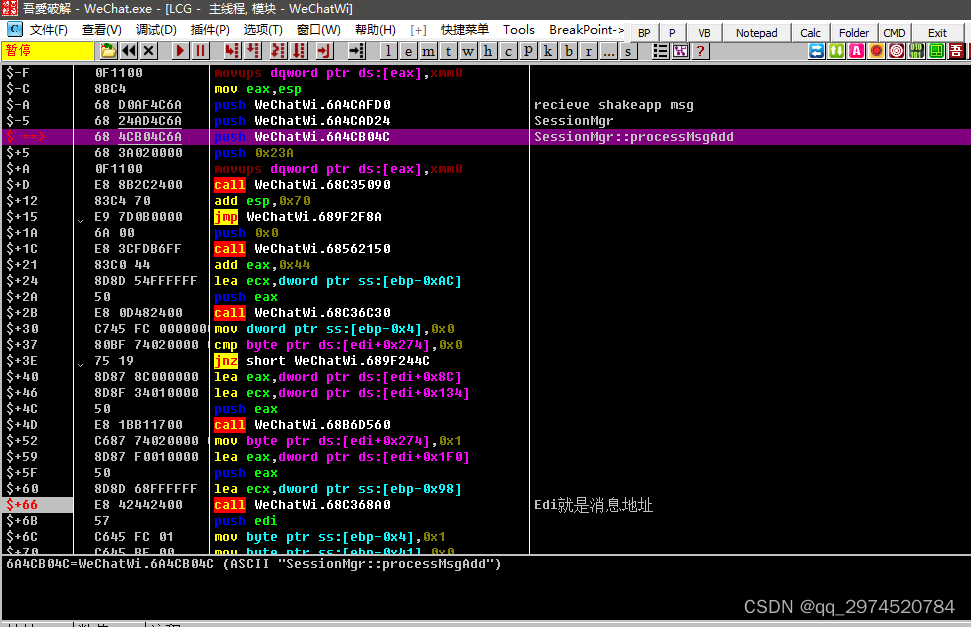
SessionMgr::processMsgAdd地址+66就是消息HookCall 取Edi 就可以获取消息内容与id
$-12 > 83EC 10 sub esp,0x10
$-F > 0F1100 movups dqword ptr ds:[eax],xmm0
$-C > 8BC4 mov eax,esp
$-A > 68 D0AF4C6A push WeChatWi.6A4CAFD0 ; recieve shakeapp msg
$-5 > 68 24AD4C6A push WeChatWi.6A4CAD24 ; SessionMgr
$ ==> > 68 4CB04C6A push WeChatWi.6A4CB04C ; SessionMgr::processMsgAdd
$+5 > 68 3A020000 push 0x23A
$+A > 0F1100 movups dqword ptr ds:[eax],xmm0
$+D > E8 8B2C2400 call WeChatWi.68C35090
$+12 > 83C4 70 add esp,0x70
$+15 > E9 7D0B0000 jmp WeChatWi.689F2F8A
$+1A > 6A 00 push 0x0
$+1C > E8 3CFDB6FF call WeChatWi.68562150
$+21 > 83C0 44 add eax,0x44
$+24 > 8D8D 54FFFFFF lea ecx,dword ptr ss:[ebp-0xAC]
$+2A > 50 push eax
$+2B > E8 0D482400 call WeChatWi.68C36C30
$+30 > C745 FC 0000000>mov dword ptr ss:[ebp-0x4],0x0
$+37 > 80BF 74020000 0>cmp byte ptr ds:[edi+0x274],0x0
$+3E > 75 19 jnz short WeChatWi.689F244C
$+40 > 8D87 8C000000 lea eax,dword ptr ds:[edi+0x8C]
$+46 > 8D8F 34010000 lea ecx,dword ptr ds:[edi+0x134]
$+4C > 50 push eax
$+4D > E8 1BB11700 call WeChatWi.68B6D560
$+52 > C687 74020000 0>mov byte ptr ds:[edi+0x274],0x1
$+59 > 8D87 F0010000 lea eax,dword ptr ds:[edi+0x1F0]
$+5F > 50 push eax
$+60 > 8D8D 68FFFFFF lea ecx,dword ptr ss:[ebp-0x98]
$+66 > E8 42442400 call WeChatWi.68C368A0 ; 消息HOOKCall Edi就是消息地址
$+6B > 57 push edi