目录
POR BLOCKCHAIN
In this section, we propose a PoR blockchain to maintain the above reputation mechanism and storage allocation records. The blockchain provides a consensus ledger for a series of transactions made by nodes in the network, and it also adapts to the consensus of reputation and storage allocation. Based on the reputation mechanism, we use PoR as the consensus mechanism in our design instead of classic PoW or PoS mechanisms.
在本节中,我们提出了一个 PoR 区块链来维护上述信誉机制和存储分配记录。 区块链为网络中节点进行的一系列交易提供了一个共识账本,同时也适应了声誉和存储分配的共识。 基于信誉机制,我们在设计中使用 PoR 作为共识机制,而不是经典的 PoW 或 PoS 机制。
A. Recording Information by Blockchain We have introduced the reputation mechanism and the storage allocation in previous sections, and we need a structure for nodes in edge networks to apply them. The structure should provide a reliable information recording function so that each node can reach a consensus on information recording. The blockchain is widely used in edge networks for nodes to reach a consensus, and it can provide an immutable ledger for recording information. We then discuss how blockchain records the required information.
Reputation mechanism: Global reputations are computed by aggregating personal reputations. All nodes need to reach a consensus on global reputations so that nodes can calculate the algorithm in Section V based on the same global reputations. It faces two challenges. First, personal reputations are constantly changing, it is hard for nodes to keep updating the newest global reputations. Second, the network latency makes the personal reputation records of nodes inevitably different, and the different global reputations calculated by nodes cannot reach a consensus. To solve the challenges, we let block generators record current global reputations when generating blocks. More specifically, based on global reputations recorded in the previous block and personal reputation transactions in the current block, the generator of the current block calculates new global reputations and records them in the current block. Once a node receives a new block, it validates the content in the new block and computes the global reputation by aggregating personal reputations recorded in the new block and previous blocks. The node applies the global reputations recorded in this block when needed and refreshes the reputation records until it accepts the next block. Therefore, all nodes follow the global reputations recorded in the latest block.
Storage allocation: Recording storage allocation is for the convenience of nodes to know where it is stored when querying data. When a node is ready to store a piece of new data, it obtains locations to be stored according to the storage allocation algorithm. Then it broadcasts the data summary and storage location in the form of transactions. The blockchain records those transactions, and other nodes can query the storage location of any data.
A. 区块链记录信息 我们在前面的章节中介绍了信誉机制和存储分配,我们需要一个边缘网络中的节点结构来应用它们。 该结构应提供可靠的信息记录功能,以便每个节点能够就信息记录达成共识。 区块链被广泛用于边缘网络中的节点达成共识,它可以提供一个不可变的账本来记录信息。 然后我们讨论区块链如何记录所需的信息。
声誉机制:全局声誉是通过聚合个人声誉来计算的。所有节点都需要就全局信誉达成共识,以便节点可以根据相同的全局信誉计算第五节中的算法。它面临两个挑战。首先,个人声誉在不断变化,节点很难不断更新最新的全局声誉。其次,网络延迟使得节点的个人声誉记录不可避免地存在差异,节点计算的不同全局声誉无法达成共识。为了解决这些挑战,我们让块生成器在生成块时记录当前的全局声誉。更具体地说,当前区块的生成器根据前一个区块中记录的全局声誉和当前区块中的个人声誉交易,计算出新的全局声誉并将其记录在当前区块中。一旦一个节点收到一个新区块,它就会验证新区块中的内容,并通过汇总新区块和之前区块中记录的个人声誉来计算全局声誉。节点在需要时应用记录在此块中的全局信誉并刷新信誉记录,直到它接受下一个块。因此,所有节点都遵循最新区块中记录的全局声誉。
存储分配:记录存储分配是为了方便节点在查询数据时知道存储在哪里。 当一个节点准备好存储一条新数据时,它会根据存储分配算法获取要存储的位置。 然后它以交易的形式广播数据汇总和存储位置。 区块链记录这些交易,其他节点可以查询任何数据的存储位置。
B. Consensus Mechanisms Overview The blockchain needs a consensus mechanism so that all nodes can reach a consensus on the content of the block. PoW and PoS are common consensus mechanisms in previous blockchain applications. These consensus mechanisms are mainly used to confirm the generators for new blocks. PoW selects new block generators through the consumption of proven computing power, and PoS selects new block generators based on the assets owned by participants. PoR is an emerging consensus mechanism. The basic idea of PoR is to let the node with the most increase of global reputation value in each block be the generator. Intuitively speaking, the node with the most increase of global reputation is the node that makes the most profit at the reputation aspect. It needs to be honest to obtain the support of other nodes and obtain the corresponding increase in reputation. As evidence of personal and global reputations, the block generator needs to record changes in both reputations. Commonly used consensus mechanisms, such as PoW and PoS, have limitations in our environment. The PoW mechanism needs to consume a lot of computing resources. In edge computing environments, the computing resources owned by different devices are unbalanced and predictable. Using the PoW mechanism not only consumes a lot of computing power but also makes it difficult for most edge nodes to compete for generating blocks. The PoS mechanism leads to inevitable centralization, that is, the block generators are always the same group of nodes, which makes it possible for them to manipulate the reputation mechanism. Therefore, in our environment, PoW and PoS mechanisms are inappropriate.
B. 共识机制概述 区块链需要一个共识机制,让所有节点都能就区块的内容达成共识。 PoW 和 PoS 是以往区块链应用中常见的共识机制。这些共识机制主要用于确认新区块的生成者。 PoW 通过消耗经过验证的算力来选择新的区块生成器,PoS 根据参与者拥有的资产来选择新的区块生成器。 PoR 是一种新兴的共识机制。 PoR 的基本思想是让每个区块中全局信誉值增加最多的节点作为生成者。直观地说,全局声誉增长最多的节点是在声誉方面获利最多的节点。需要诚实才能获得其他节点的支持,获得相应的声望提升。作为个人和全局声誉的证据,块生成器需要记录两种声誉的变化。常用的共识机制,如 PoW 和 PoS,在我们的环境中存在局限性。 PoW 机制需要消耗大量的计算资源。在边缘计算环境中,不同设备所拥有的计算资源是不平衡且可预测的。使用 PoW 机制不仅会消耗大量的算力,也使得大多数边缘节点难以竞争出块。 PoS 机制导致不可避免的中心化,即区块生成者始终是同一组节点,这使得它们可以操纵声誉机制。因此,在我们的环境中,PoW 和 PoS 机制是不合适的。
C. PoR Blockchain Design We describe the specific PoR blockchain in detail. PoR needs a reputation mechanism as a foundation, and we have already proposed a reputation mechanism in Section IV. The reputation mechanism allows nodes to evaluate the personal reputation of others and generates the global reputation of each node. We next describe in detail how to use the existing reputation mechanism to design a PoR blockchain.
Restricting reputation updates: The reputation mechanism has no restriction for the frequency and timing of reputation updates. If a large number of nodes send reputation update information at a high frequency, a large amount of reputation update information will flood the network. To solve the above problem, we limit the frequency and timing of reputation updates. We stipulate that nodes can update the reputation only if they have finished an interaction. In our storage allocation environment, the interaction means that node i requests data from node j, and they can update the reputation of each other once. In order to prove that a reputation update is related to an interaction, the reputation update information points to the corresponding data interaction. Thus, the frequency and timing of reputation updates are related to the frequency of data requests, and we need to restrict the frequency of data requests. The attacker can achieve the purpose of frequent malicious evaluations through frequent data requests. To avoid this situation, we allow one node to ask another node for the same piece of data once in one block. The reason is that for the same piece of data, the node has a cache for its recent access. For different pieces of data, they are generally stored in different nodes. The extra interaction messages will be ignored by other nodes.
Selecting block generators: The node with the most increase of global reputation in the current block is selected as the new block generator. The selection is as fair as possible to obtain confirmation from other nodes. However, a malicious node can behave maliciously in the beginning, then behave honestly to make a fluctuation of its global reputation between two different blocks. To avoid this case, we further add a constraint that the block generator must have a global reputation in the top 50%. This constraint prevents a node from becoming a block generator by reputation boost in a short period. Assume the current block is the t-th block in the blockchain, and the global reputation of node i is gi(t) after applying all personal reputation changes recorded in the t-th block. Assume V0(t) contains the top 50% of the nodes in global reputation in the t-th block. If the block generator of the t-th block is node i, it satisfies
Generating new blocks: We describe the block generation process from the perspective of one node. The node continuously exchanges data in the network to generate corresponding transactions and reputation updates. The node broadcasts this information to the entire network after signing and receives such information from other nodes. When the number of data exchange transactions and reputation updates reaches a certain number, a new block is required to package and record these transactions and reputation updates on the blockchain. The node calculates new personal reputations through local personal reputation records and reputation updates that will be recorded in the new block. The node then computes the global reputation and checks whether it is the node with the highest reputation in the new block. If it is, it will broadcast the new block to the entire network. Otherwise, other nodes will generate new blocks, the node will check received blocks, and select a block generated by the correct block generator to continue working on it. To verify the validity of the block and the generator, the node verifies the transactions in the block and calculates the corresponding global reputation based on the content of the block.
Permissioned blockchain: Traditional blockchain is permissionless blockchain, which means nodes spread out the Internet can join or leave a permissionless blockchain without permission from any party. On contrary, a permissioned blockchain has restrictions in its memberships, users cannot join a permissioned blockchain freely.
We use permissioned blockchain instead of permissionless blockchain in our design. The reason is that permissioned blockchain improves the security performance of the reputation mechanism. The cost of attacks against reputation mechanisms in a permissionless environment is low, such as whitewashing attacks and Sybil attacks. A permitted blockchain has thresholds for joining nodes, or they have to pass the audit of existing nodes. The attacker needs to spend high costs to obtain identities in the blockchain. With the help of the reputation system, malicious nodes will be exposed, greatly increasing the cost of attack and improving the security performance. Note that nodes need approval to enter and leave the permissioned blockchain. We give block generators the right to approve nodes to enter the network or remove nodes from the network. As long as several consecutive block generators approve, a node enters or moves out of the permissioned blockchain. The more specific design is beyond the scope of this paper.
C. PoR 区块链设计 我们详细描述了具体的 PoR 区块链。 PoR 需要信誉机制作为基础,我们已经在第四节提出了信誉机制。声誉机制允许节点评估他人的个人声誉并生成每个节点的全局声誉。我们接下来详细描述如何使用现有的信誉机制来设计 PoR 区块链。
-
限制信誉更新:信誉机制对信誉更新的频率和时间没有限制。如果大量节点高频率发送信誉更新信息,大量的信誉更新信息将淹没网络。为了解决上述问题,我们限制了信誉更新的频率和时间。我们规定节点只有在完成交互后才能更新信誉。在我们的存储分配环境中,交互意味着节点 i 向节点 j 请求数据,并且它们可以更新彼此的信誉一次。为了证明信誉更新与交互有关,信誉更新信息指向对应的数据交互。因此,声誉更新的频率和时间与数据请求的频率有关,我们需要限制数据请求的频率。攻击者可以通过频繁的数据请求来达到频繁恶意评价的目的。为了避免这种情况,我们允许一个节点在一个块中向另一个节点请求相同的数据。原因是对于同一条数据,该节点有一个缓存供其最近访问。对于不同的数据,它们通常存储在不同的节点中。额外的交互消息将被其他节点忽略。
-
选择区块生成者:选择当前区块中全局声誉增加最多的节点作为新的区块生成者。选择尽可能公平,以获得其他节点的确认。然而,恶意节点可以在开始时表现出恶意,然后诚实地表现出其在两个不同区块之间的全局声誉的波动。为了避免这种情况,我们进一步添加了一个约束条件,即块生成器必须在前 50% 中具有全局声誉。此约束可防止节点短期内通过声誉提升而成为块生成器。假设当前区块是区块链中的第 t 个区块,在应用所有记录在第 t 个区块中的个人声誉变化后,节点 i 的全局声誉为 gi(t)。假设 V‘(t) 包含第 t 个区块中全局信誉排名前 50% 的节点。如果第 t 个块的块生成器是节点 i,则满足
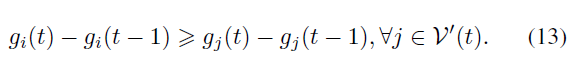
-
生成新块:我们从一个节点的角度来描述块生成过程。节点不断地在网络中交换数据以生成相应的交易和信誉更新。节点在签名后将此信息广播到全网,并从其他节点接收此类信息。当数据交换交易和信誉更新的数量达到一定数量时,需要一个新的区块将这些交易和信誉更新打包并记录在区块链上。节点通过将记录在新区块中的本地个人声誉记录和声誉更新来计算新的个人声誉。然后节点计算全局信誉,并检查它是否是新区块中信誉最高的节点。如果是,它会将新区块广播到整个网络。否则,其他节点将生成新的块,该节点将检查收到的块,并选择由正确的块生成器生成的块继续工作。为了验证区块和生成者的有效性,节点验证区块中的交易,并根据区块的内容计算相应的全局信誉。
-
许可区块链:传统区块链是无许可区块链,即散布在互联网上的节点可以在未经任何一方许可的情况下加入或离开无许可区块链。相反,许可区块链对其成员资格有限制,用户不能自由加入许可区块链。
我们在设计中使用许可区块链而不是无许可区块链。原因是许可区块链提高了信誉机制的安全性能。在未经许可的环境中,针对声誉机制的攻击成本很低,例如white-washing attacks攻击和Sybil攻击。允许的区块链具有加入节点的阈值,或者它们必须通过现有节点的审核。攻击者需要花费高昂的成本来获取区块链中的身份。
D. Security Analysis We discuss the security performance of PoR.
Bad-mouthing attack: In our PoR blockchain, the form of bad-mouthing attack is that the attacker conducts malicious evaluations after data interactions, which improves its own reputation and reduces the reputation of other nodes to gain the advantage of becoming a block generator in the competition. Since it is difficult for a third-party node that is not an interactive participant to obtain the actual interaction process between two nodes, it is difficult to detect malicious evaluations by the attacker. However, this attack is difficult to affect PoR. First, evaluations from a single node have a limited impact on the global reputation. Second, a node that keeps evaluating the personal reputation of others maliciously will be detected by honest nodes, and it will receive negative feedback from honest nodes. This leads to a decline in the global reputation of the node, and the node is at a disadvantage in the competition of block generators. Therefore, an attacker who performs a badmouthing attack cannot give an advantage to competing block generators.
Denial of Service attack: In our environment, the attacker performs a DoS attack by sending a large amount of spam feedback information to flood the network to block the transmission of normal reputation feedback. Since one node can only ask another node for the same piece of data once in one block, the number of times that any pair of nodes can evaluate each other is limited. Therefore, the attacker cannot send a large amount of spam reputation updates, and our PoR mechanism can effectively prevent DoS attacks.
Sybil attack: The attacker has two ways to perform Sybil attacks on our PoR blockchain. The first way is to create a large number of puppet nodes and use these nodes to perform malicious operations. The creation of a large number of puppet nodes is hard in permissioned environment since it is generally easy to find and consumes a lot of costs. Thus, this form of attack is hard to implement in our permissioned environment. The second way is that the attacker lets a node exit after its reputation is low, then the attacker joins the network with a new identity, which is also known as a whitewashing attack. However, re-entering the network requires costs, such as the time cost of waiting to join the permissioned blockchain and the monetary cost of identity mortgages. Moreover, the reputation of the new identity will be lowered if it keeps behaving maliciously. Therefore, it is difficult for Sybil Attack to play a role in the permissioned PoR blockchain.
D. 安全分析 我们讨论 PoR 的安全性能。
-
恶意攻击:在我们的 PoR 区块链中,恶意攻击的形式是攻击者在数据交互后进行恶意评估,从而提高自己的声誉,降低其他节点的声誉,从而获得成为区块的优势发电机在比赛中。由于非交互参与者的第三方节点很难获得两个节点之间的实际交互过程,因此很难检测到攻击者的恶意评价。但是,这种攻击很难影响 PoR。首先,来自单个节点的评估对全局声誉的影响有限。其次,不断恶意评价他人个人声誉的节点会被诚实节点检测到,并且会收到来自诚实节点的负面反馈。这导致节点的全局声誉下降,节点在出块者的竞争中处于劣势。因此,执行恶意攻击的攻击者无法为竞争的块生成器提供优势。 2)拒绝服务攻击:在我们的环境中,攻击者通过发送大量垃圾邮件反馈信息来淹没网络以阻止正常信誉反馈的传输,从而进行DoS攻击。由于一个节点在一个块中只能向另一个节点请求同一条数据一次,因此任何一对节点可以相互评估的次数是有限的。因此,攻击者无法发送大量垃圾邮件信誉更新,而我们的 PoR 机制可以有效防止 DoS 攻击。
-
Sybil 攻击:攻击者有两种方式对我们的 PoR 区块链进行 Sybil 攻击。第一种方式是创建大量傀儡节点,利用这些节点进行恶意操作。在许可环境中创建大量 puppet 节点是很困难的,因为它通常很容易找到并且消耗大量成本。因此,这种形式的攻击很难在我们许可的环境中实施。第二种方式是攻击者让一个节点信誉低后退出,然后攻击者以新的身份加入网络,也称为洗白攻击。但是,重新进入网络需要成本,例如等待加入许可区块链的时间成本和身份抵押的货币成本。此外,如果新身份继续作恶,其声誉也会降低。因此,Sybil Attack 很难在许可的 PoR 区块链中发挥作用。
Summary
A. 区块链记录信息
声誉机制:
个人声誉在不断变化,节点很难不断更新最新的全局声誉。
网络延迟使得节点的个人声誉记录不可避免地存在差异,节点计算的不同全局声誉无法达成共识。
为了解决这些挑战,当前区块的生成器根据前一个区块中记录的全局声誉和当前区块中的个人声誉交易,计算出新的全局声誉并将其记录在当前区块中。一旦一个节点收到一个新区块,它就会验证新区块中的内容,并通过汇总新区块和之前区块中记录的个人声誉来计算全局声誉。节点在需要时应用记录在此块中的全局信誉并刷新信誉记录,直到它接受下一个块。因此,所有节点都遵循最新区块中记录的全局声誉。
存储分配: 当一个节点准备好存储一条新数据时,它会根据存储分配算法获取要存储的位置。 然后它以交易的形式广播数据汇总和存储位置。 区块链记录这些交易,其他节点可以查询任何数据的存储位置。
B. 共识机制概述 PoR 是一种新兴的共识机制。 PoR 的基本思想是让每个区块中全局信誉值增加最多的节点作为生成者。直观地说,全局声誉增长最多的节点是在声誉方面获利最多的节点。需要诚实才能获得其他节点的支持,获得相应的声望提升。作为个人和全局声誉的证据,块生成器需要记录两种声誉的变化。
C. PoR 区块链设计
-
限制信誉更新:限制了信誉更新的频率和时间。我们规定节点只有在完成交互后才能更新信誉。在我们的存储分配环境中,交互意味着节点 i 向节点 j 请求数据,并且它们可以更新彼此的信誉一次。声誉更新的频率和时间与数据请求的频率有关,我们需要限制数据请求的频率。攻击者可以通过频繁的数据请求来达到频繁恶意评价的目的。
-
选择区块生成者:选择当前区块中全局声誉增加最多的节点作为新的区块生成者。添加了一个约束条件,即块生成器必须是具有全局声誉前 50% 节点。此约束可防止节点短期内通过声誉提升而成为块生成器。假设当前区块是区块链中的第 t 个区块,在应用所有记录在第 t 个区块中的个人声誉变化后,节点 i 的全局声誉为 gi(t)。假设 V‘(t) 包含第 t 个区块中全局信誉排名前 50% 的节点。如果第 t 个块的块生成器是节点 i,则满足
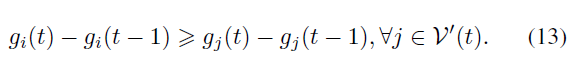
即:必须大于同一个区块中的其他节点的增长速度。
-
生成新块:我们从一个节点的角度来描述块生成过程。节点不断地在网络中交换数据以生成相应的交易和信誉更新。节点在签名后将此信息广播到全网,并从其他节点接收此类信息。当数据交换交易和信誉更新的数量达到一定数量时,需要一个新的区块将这些交易和信誉更新打包并记录在区块链上。节点通过将记录在新区块中的本地个人声誉记录和声誉更新来计算新的个人声誉。然后节点计算全局信誉,并检查它是否是新区块中信誉最高的节点。如果是,它会将新区块广播到整个网络。否则,其他节点将生成新的块,该节点将检查收到的块,并选择由正确的块生成器生成的块继续工作。为了验证区块和生成者的有效性,节点验证区块中的交易,并根据区块的内容计算相应的全局信誉。
-
许可区块链:
使用许可区块链,原因是许可区块链提高了信誉机制的安全性能。在未经许可的环境中,针对声誉机制的攻击成本很低。
D. 安全分析
-
恶意攻击:在我们的 PoR 区块链中,恶意攻击的形式是攻击者在数据交互后进行恶意评估,从而提高自己的声誉,降低其他节点的声誉,从而获得成为区块的优势。这种攻击很难影响 PoR。
-
来自单个节点的评估对全局声誉的影响有限。
-
不断恶意评价他人个人声誉的节点会被诚实节点检测到,并且会收到来自诚实节点的负面反馈。导致节点的全局声誉下降,节点在出块者的竞争中处于劣势。
-
-
拒绝服务攻击:DoS攻击,由于一个节点在一个块中只能向另一个节点请求同一条数据一次,因此任何一对节点可以相互评估的次数是有限的。有效防止 DoS 攻击。
-
Sybil 攻击:
-
第一种方式:创建大量傀儡节点,利用这些节点进行恶意操作。在许可环境中创建大量节点很困难的消耗大量成本。
-
第二种方式:攻击者让节点信誉低后退出,然后攻击者以新的身份加入网络,也称为whitewashing attack。重新进入网络需要成本,例如等待加入许可区块链的时间成本和身份抵押的货币成本。此外,如果新身份继续作恶,其声誉也会降低。
-