Freeipa - LDAP与autofs配置
什么是freeipa
移步官网
服务器分配规划
| 服务器名称 | IP地址 |
|---|---|
| ipa server & NFS server | 192.168.50.147 |
| ipa client host | 192.168.50.158 |
配置freeipa 服务器
步骤
freeIPA服务器
安装需要的包
[root@ipa ~]# yum update -y
... snippet ommitted ...
[root@ipa ~]# yum install -y ipa-server ipa-server-dns
... snippet ommitted ...
设置ipa域名解析
[root@ipa ~]# cat << EOF >> /etc/hosts
> 192.168.50.157 server.ipa.test
> EOF
安装ipa server
[root@localhost ~]# ipa-server-install --setup-dns --allow-zone-overlap
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the Network Time Daemon (ntpd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure DNS (bind)
* Configure the KDC to enable PKINIT
To accept the default shown in brackets, press the Enter key.
WARNING: conflicting time&date synchronization service 'chronyd' will be disabled
in favor of ntpd
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
<hostname>.<domainname>
Example: master.example.com.
Server host name [server.ipa.test]:
Warning: skipping DNS resolution of host server.ipa.test
The domain name has been determined based on the host name.
Please confirm the domain name [ipa.test]:
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
Please provide a realm name [IPA.TEST]:
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password:
Password (confirm):
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password:
Password (confirm):
Checking DNS domain ipa.test., please wait ...
Do you want to configure DNS forwarders? [yes]:
Following DNS servers are configured in /etc/resolv.conf: 192.168.50.1
Do you want to configure these servers as DNS forwarders? [yes]:
All DNS servers from /etc/resolv.conf were added. You can enter additional addresses now:
Enter an IP address for a DNS forwarder, or press Enter to skip:
Checking DNS forwarders, please wait ...
DNS server 192.168.50.1: answer to query '. SOA' is missing DNSSEC signatures (no RRSIG data)
Please fix forwarder configuration to enable DNSSEC support.
(For BIND 9 add directive "dnssec-enable yes;" to "options {}")
WARNING: DNSSEC validation will be disabled
Do you want to search for missing reverse zones? [yes]:
Do you want to create reverse zone for IP 192.168.50.157 [yes]:
Please specify the reverse zone name [50.168.192.in-addr.arpa.]:
Using reverse zone(s) 50.168.192.in-addr.arpa.
The IPA Master Server will be configured with:
Hostname: server.ipa.test
IP address(es): 192.168.50.157
Domain name: ipa.test
Realm name: IPA.TEST
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 192.168.50.1
Forward policy: only
Reverse zone(s): 50.168.192.in-addr.arpa.
Continue to configure the system with these values? [no]: yes
... snippet ommitted ...
==============================================================================
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
* 53: bind
UDP Ports:
* 88, 464: kerberos
* 53: bind
* 123: ntp
2. You can now obtain a kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificates stored in /root/cacert.p12
These files are required to create replicas. The password for these
files is the Directory Manager password
登录到IPA
[root@server ~]# kinit admin
Password for [email protected]:
查看服务状态
[root@server ~]# ipactl status
Directory Service: RUNNING
krb5kdc Service: RUNNING
kadmin Service: RUNNING
named Service: RUNNING
httpd Service: RUNNING
ipa-custodia Service: RUNNING
ntpd Service: RUNNING
pki-tomcatd Service: RUNNING
ipa-otpd Service: RUNNING
ipa-dnskeysyncd Service: RUNNING
ipa: INFO: The ipactl command was successful
Firefox登录freeIPA管理网页
创建用户
网页创建用户(略)
命令行创建用户
[root@server ~]# ipa user-add
First name: lisa
Last name: jones
User login [ljones]:
-------------------
Added user "ljones"
-------------------
User login: ljones
First name: lisa
Last name: jones
Full name: lisa jones
Display name: lisa jones
Initials: lj
Home directory: /home/ljones
GECOS: lisa jones
Login shell: /bin/sh
Principal name: [email protected]
Principal alias: [email protected]
Email address: [email protected]
UID: 864600003
GID: 864600003
Password: False
Member of groups: ipausers
Kerberos keys available: False
[root@server ~]# ipa user-add jsmith --first=John --last=Smith --manager=bjensen [email protected] --homedir=/home/work/johns --password #非交互式创建
开防火墙策略,以让客户端能访问并加入该IPA服务器
列出防火墙有什么服务
[root@server ~]# firewall-cmd --get-service
RH-Satellite-6 RH-Satellite-6-capsule amanda-client amanda-k5-client amqp amqps apcupsd audit bacula bacula-client bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client distcc dns docker-registry docker-swarm dropbox-lansync elasticsearch etcd-client etcd-server finger freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master git gre high-availability http https imap imaps ipp ipp-client ipsec irc ircs iscsi-target isns jenkins kadmin kerberos kibana klogin kpasswd kprop kshell ldap ldaps libvirt libvirt-tls lightning-network llmnr managesieve matrix mdns minidlna mongodb mosh mountd mqtt mqtt-tls ms-wbt mssql murmur mysql nfs nfs3 nmea-0183 nrpe ntp nut openvpn ovirt-imageio ovirt-storageconsole ovirt-vmconsole plex pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius redis rpc-bind rsh rsyncd rtsp salt-master samba samba-client samba-dc sane sip sips slp smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh steam-streaming svdrp svn syncthing syncthing-gui synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client upnp-client vdsm vnc-server wbem-http wbem-https wsman wsmans xdmcp xmpp-bosh xmpp-client xmpp-local xmpp-server zabbix-agent zabbix-server
查看freeipa-ldap(s)对应的端口
[root@server ~]# cd /usr/lib/firewalld/services/
[root@server services]# cat freeipa-ldap.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>FreeIPA with LDAP</short>
<description>FreeIPA is an LDAP and Kerberos domain controller for Linux systems. Enable this option if you plan to provide a FreeIPA Domain Controller using the LDAP protocol. You can also enable the 'freeipa-ldaps' service if you want to provide the LDAPS protocol. Enable the 'dns' service if this FreeIPA server provides DNS services and 'freeipa-replication' service if this FreeIPA server is part of a multi-master replication setup.</description>
<port protocol="tcp" port="80"/>
<port protocol="tcp" port="443"/>
<port protocol="tcp" port="88"/>
<port protocol="udp" port="88"/>
<port protocol="tcp" port="464"/>
<port protocol="udp" port="464"/>
<port protocol="udp" port="123"/>
<port protocol="tcp" port="389"/>
</service>
[root@server services]# cat freeipa-ldaps.xml
<?xml version="1.0" encoding="utf-8"?>
<service>
<short>FreeIPA with LDAPS</short>
<description>FreeIPA is an LDAP and Kerberos domain controller for Linux systems. Enable this option if you plan to provide a FreeIPA Domain Controller using the LDAPS protocol. You can also enable the 'freeipa-ldap' service if you want to provide the LDAP protocol. Enable the 'dns' service if this FreeIPA server provides DNS services and 'freeipa-replication' service if this FreeIPA server is part of a multi-master replication setup.</description>
<port protocol="tcp" port="80"/>
<port protocol="tcp" port="443"/>
<port protocol="tcp" port="88"/>
<port protocol="udp" port="88"/>
<port protocol="tcp" port="464"/>
<port protocol="udp" port="464"/>
<port protocol="udp" port="123"/>
<port protocol="tcp" port="636"/>
</service>
开防火墙策略
[root@server services]# firewall-cmd --add-service={freeipa-ldap,freeipa-ldaps,dns,mountd,rpc-bind} --permanent && firewall-cmd --reload
success
success
查看防火墙
[root@server services]# firewall-cmd --list-all
public (active)
target: default
icmp-block-inversion: no
interfaces: eth0
sources:
services: dhcpv6-client dns freeipa-ldap freeipa-ldaps mountd nfs nfs3 rpc-bind ssh
ports:
protocols:
masquerade: no
forward-ports:
source-ports:
icmp-blocks:
rich rules:
配置freeIPA客户端
设置主机名
[root@host-001 ~]# hostnamectl set-hostname host-001.ipa.test
设置DNS
[root@host-001 ~]# cat /etc/sysconfig/network-scripts/ifcfg-eth0 | grep DNS
DNS1=192.168.50.157
PEERDNS="no"
安装ipa-client
[root@host-001 ~]# ipa-client-install
WARNING: ntpd time&date synchronization service will not be configured as
conflicting service (chronyd) is enabled
Use --force-ntpd option to disable it and force configuration of ntpd
Discovery was successful!
Client hostname: host-001.ipa.test
Realm: IPA.TEST
DNS Domain: ipa.test
IPA Server: server.ipa.test
BaseDN: dc=ipa,dc=test
Continue to configure the system with these values? [no]: yes
Skipping synchronizing time with NTP server.
User authorized to enroll computers: admin
Password for [email protected]:
Successfully retrieved CA cert
Subject: CN=Certificate Authority,O=IPA.TEST
Issuer: CN=Certificate Authority,O=IPA.TEST
Valid From: 2021-06-10 14:29:47
Valid Until: 2041-06-10 14:29:47
Enrolled in IPA realm IPA.TEST
Created /etc/ipa/default.conf
New SSSD config will be created
Configured sudoers in /etc/nsswitch.conf
Configured /etc/sssd/sssd.conf
Configured /etc/krb5.conf for IPA realm IPA.TEST
trying https://server.ipa.test/ipa/json
[try 1]: Forwarding 'schema' to json server 'https://server.ipa.test/ipa/json'
trying https://server.ipa.test/ipa/session/json
[try 1]: Forwarding 'ping' to json server 'https://server.ipa.test/ipa/session/json'
[try 1]: Forwarding 'ca_is_enabled' to json server 'https://server.ipa.test/ipa/session/json'
Systemwide CA database updated.
Hostname (host-001.ipa.test) does not have A/AAAA record.
Missing reverse record(s) for address(es): 192.168.50.158.
Adding SSH public key from /etc/ssh/ssh_host_rsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ecdsa_key.pub
Adding SSH public key from /etc/ssh/ssh_host_ed25519_key.pub
[try 1]: Forwarding 'host_mod' to json server 'https://server.ipa.test/ipa/session/json'
SSSD enabled
Configured /etc/openldap/ldap.conf
Configured /etc/ssh/ssh_config
Configured /etc/ssh/sshd_config
Configuring ipa.test as NIS domain.
Client configuration complete.
The ipa-client-install command was successful
回到IPA服务器网页,可以看到主机成功加入
automount服务端配置
家目录配置
NFS服务器(家目录的创建与导出)
[root@server ~]# mkdir -p /exports/home/
[root@server ~]# cat /etc/exports
/exports/home *(rw)
[root@server ~]# exportfs -av
exporting *:/exports/home
[root@server ~]# showmount -e
Export list for server.ipa.test:
/exports/home *
[root@server ~]# #然后再写一个脚本,每创建一个新用户,就使用mkhomedir_helper在NFS server上创建家目录,然后将其move到/exports/home/文件夹下。
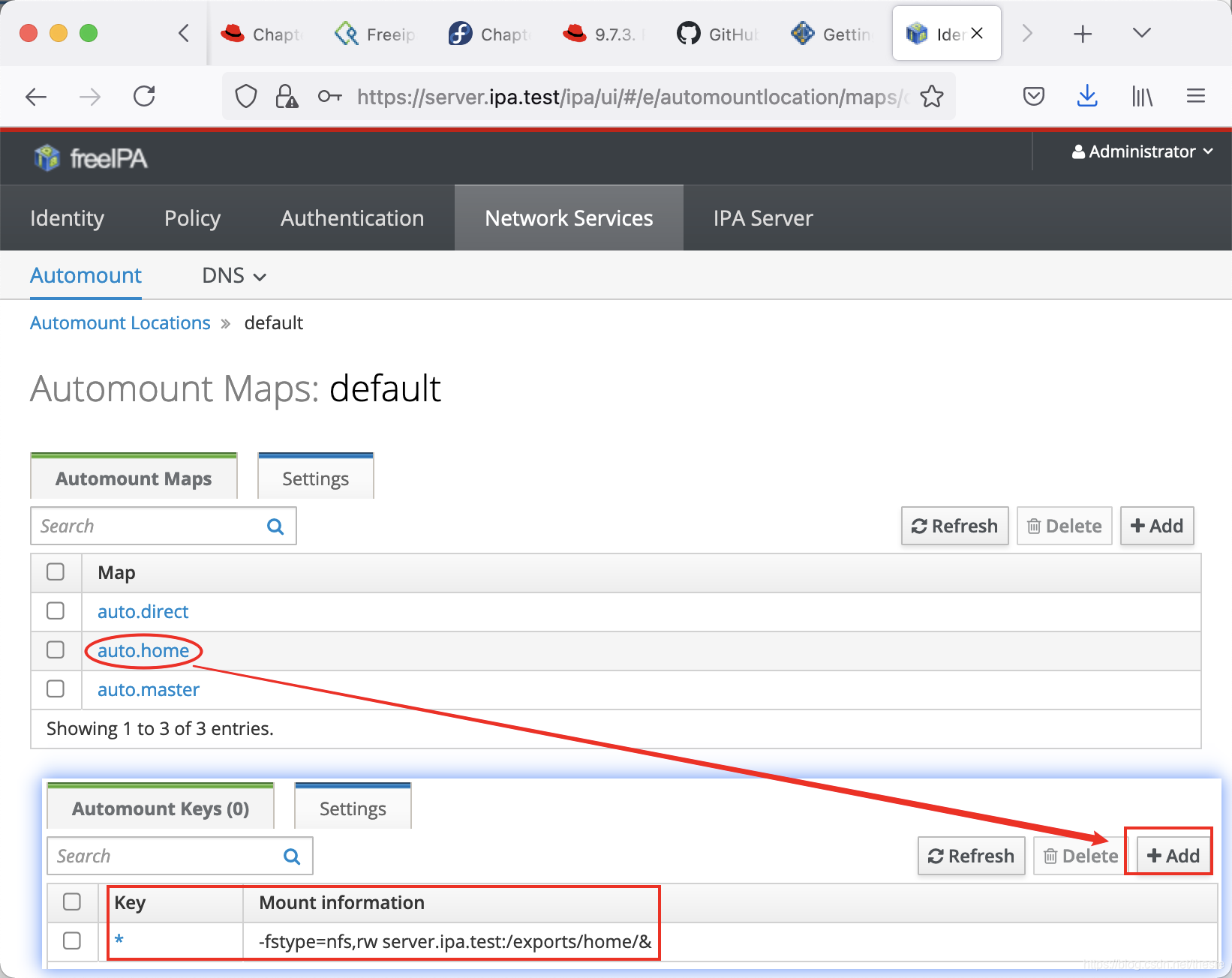
在freeIPA管理页面,添加automount信息
Network Services -> Automount -> default
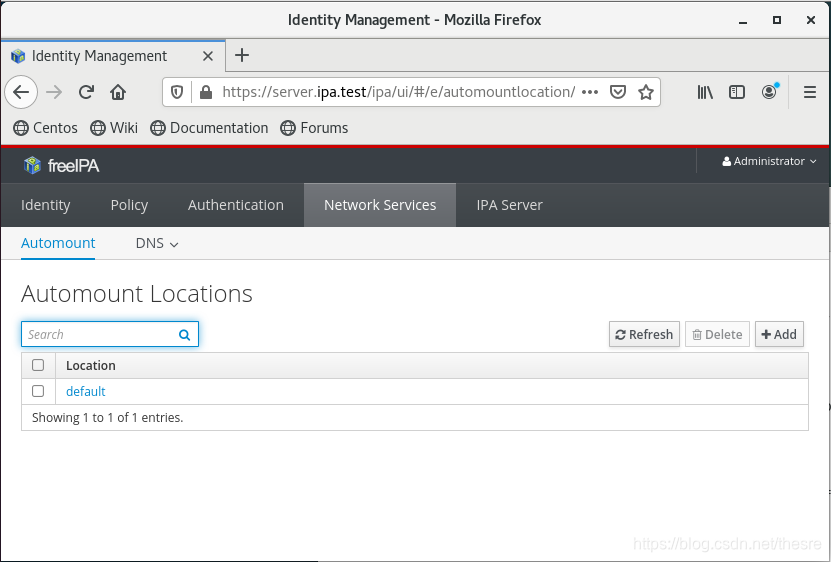 点击default,这里默认有两个Automount Map,名为auto.direct与auto.master。我们点击auto.master,增加一个
点击default,这里默认有两个Automount Map,名为auto.direct与auto.master。我们点击auto.master,增加一个Key为/home,Mount information为auto.home的条目(填写时Map name为auto.home,Mount point为/home)。
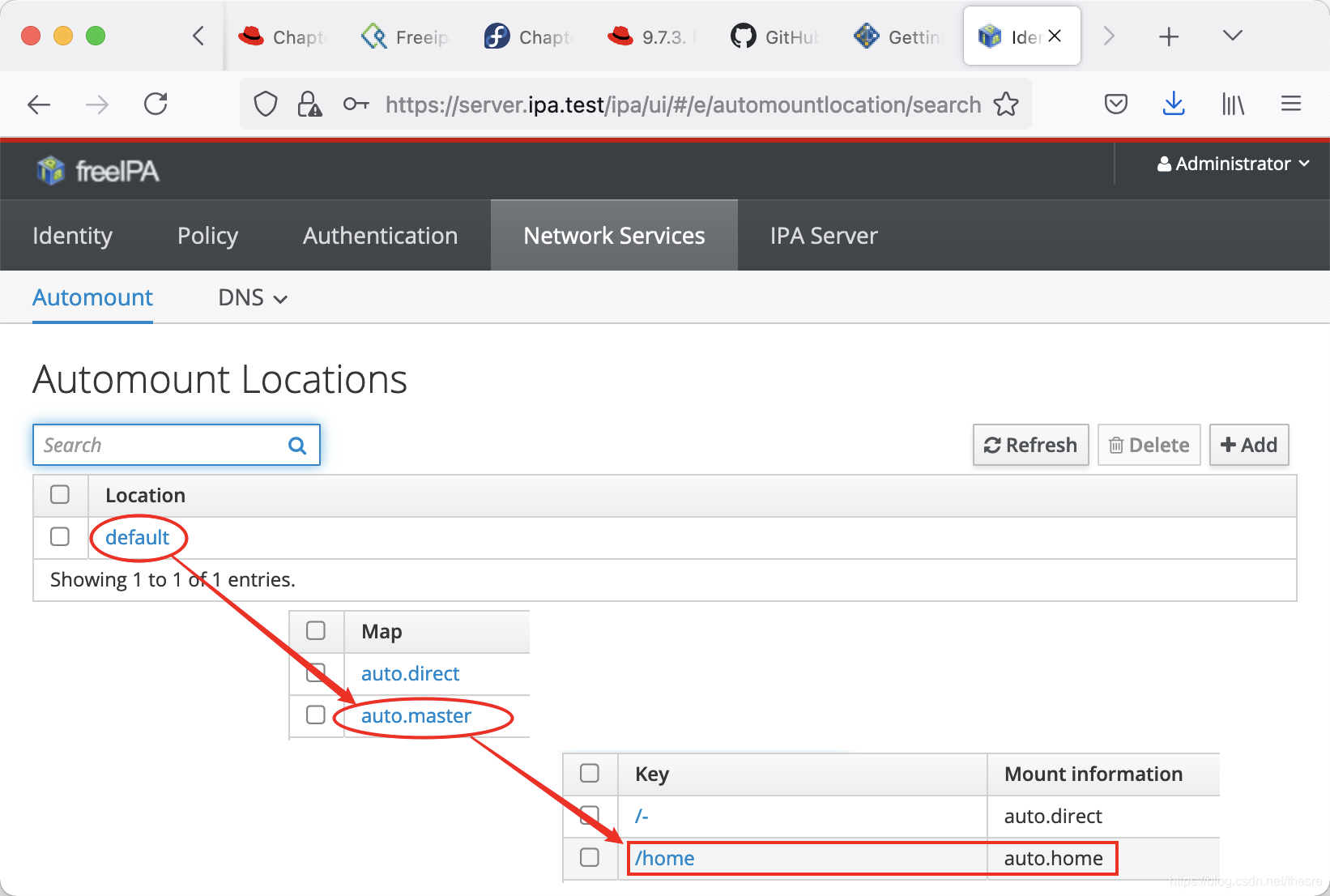
在auto.home中,增加Key为*,Mount information为-fstype=nfs,rw server.ipa.test:/exports/home/&的条目
 到这里我们服务端配置完成,包括freeIPA的安装与配置,家目录automount配置的编写。
到这里我们服务端配置完成,包括freeIPA的安装与配置,家目录automount配置的编写。
automount客户端配置
[root@host-001 ~]# cat /etc/sysconfig/autofs
#
# Init syatem options
#
# If the kernel supports using the autofs miscellanous device
# and you wish to use it you must set this configuration option
# to "yes" otherwise it will not be used.
#
USE_MISC_DEVICE="yes"
#
# Use OPTIONS to add automount(8) command line options that
# will be used when the daemon is started.
#
#OPTIONS=""
#
MAP_OBJECT_CLASS="automountMap"
ENTRY_OBJECT_CLASS="automount"
MAP_ATTRIBUTE="automountMapName"
ENTRY_ATTRIBUTE="automountKey"
VALUE_ATTRIBUTE="automountInformation"
#LDAP_URI="ldap:///dc=ipa,dc=test"
LDAP_URI="ldap://server.ipa.test"
SEARCH_BASE="cn=default,cn=automount,dc=ipa,dc=test"
[root@host-001 ~]# cat /etc/autofs_ldap_auth.conf #可运行klist -k获得当前机器的principal information
<?xml version="1.0" ?>
<!--
This files contains a single entry with multiple attributes tied to it.
See autofs_ldap_auth.conf(5) for more information.
-->
<autofs_ldap_sasl_conf
usetls="no"
tlsrequired="no"
authrequired="yes"
authtype="GSSAPI"
clientprinc="host/[email protected]"
/>
[root@host-001 ~]# cat /etc/nsswitch.conf| grep automount #增加automount来源,ldap放到第二个位置。
automount: files ldap nisplus sss
[root@host-001 ~]# systemctl restart autofs #重启autofs
验证
[root@host-001 ~]# ls /home #/home目录下无目录,autofs是访问时触发挂载的,因此在此时/home下还看不到任何目录。
[root@host-001 ~]# ssh host-001 -l ljones #以普通账号登陆运算机,可以看到家目录被mount上了。
Password:
Password expired. Change your password now.
Current Password:
New password:
Retype new password:
Last failed login: Sun Jun 13 11:08:42 CST 2021 from host-001.ipa.test on ssh:notty
There were 4 failed login attempts since the last successful login.
Last login: Sun Jun 13 10:15:57 2021
-sh-4.2$ pwd
/home/ljones
-sh-4.2$ df -h| grep -B1 /home
Filesystem Size Used Avail Use% Mounted on
server.ipa.test:/exports/home/ljones 36G 5.0G 31G 15% /home/ljones
[root@host-001 ~]# ls /home #/home目录下多了ljones目录。
ljones
总结
参考资料
https://access.redhat.com/solutions/4350171 //解决ipa-server-install command failed, exception: RuntimeError: CA did not start in 300.0s
https://docs.fedoraproject.org/en-US/Fedora/18/html/FreeIPA_Guide/index.html
https://www.server-world.info/en/note?os=Fedora_26&p=freeipa&f=1
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/linux_domain_identity_authentication_and_policy_guide/users#home-directories //在NFS自动创建家目录在现有的freeIPA机制是不支持的。
https://www.freeipa.org/images/f/f7/Administration_Guide.pdf
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/6/html/deployment_guide/sssd-ldap-autofs