1、optee中Symmetric ciphers、HASH、RNG等算法的注册模型
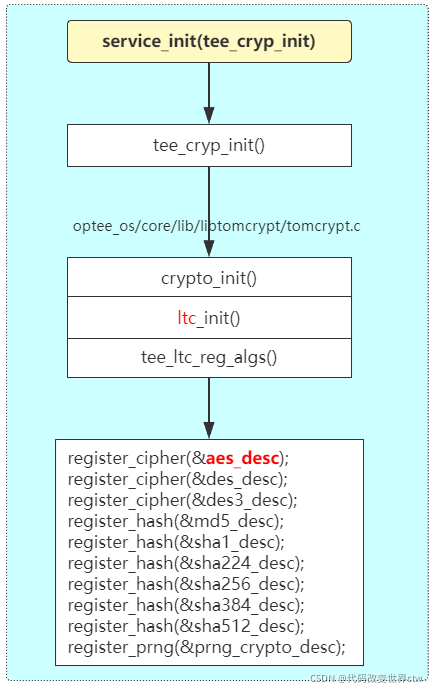
1.1、aes_desc 结构模型
(1)、如果开启硬件加速(如ARM Cryptography Extension), 则编译和使用下面结构体
(optee_os/core/lib/libtomcrypt/aes_accel.c)
const struct ltc_cipher_descriptor aes_desc = {
.name = "aes",
.ID = 6,
.min_key_length = 16,
.max_key_length = 32,
.block_length = 16,
.default_rounds = 10,
.setup = rijndael_setup,
.ecb_encrypt = rijndael_ecb_encrypt,
.ecb_decrypt = rijndael_ecb_decrypt,
.done = rijndael_done,
.keysize = rijndael_keysize,
.accel_ecb_encrypt = aes_ecb_encrypt_nblocks,
.accel_ecb_decrypt = aes_ecb_decrypt_nblocks,
.accel_cbc_encrypt = aes_cbc_encrypt_nblocks,
.accel_cbc_decrypt = aes_cbc_decrypt_nblocks,
.accel_ctr_encrypt = aes_ctr_encrypt_nblocks,
.accel_xts_encrypt = aes_xts_encrypt_nblocks,
.accel_xts_decrypt = aes_xts_decrypt_nblocks,
};
(2)、如果没有开启硬件加速, 则编译和使用下面结构体,采取纯软的实现方法
(optee_os/core/lib/libtomcrypt/src/ciphers/aes/aes.c)
const struct ltc_cipher_descriptor aes_desc =
{
"aes",
6,
16, 32, 16, 10,
SETUP, ECB_ENC, ECB_DEC, ECB_TEST, ECB_DONE, ECB_KS,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL
};
(3)、有关ltc_cipher_descriptor 结构体的描述,如下:
(optee_os/core/lib/libtomcrypt/src/headers/tomcrypt_cipher.h)
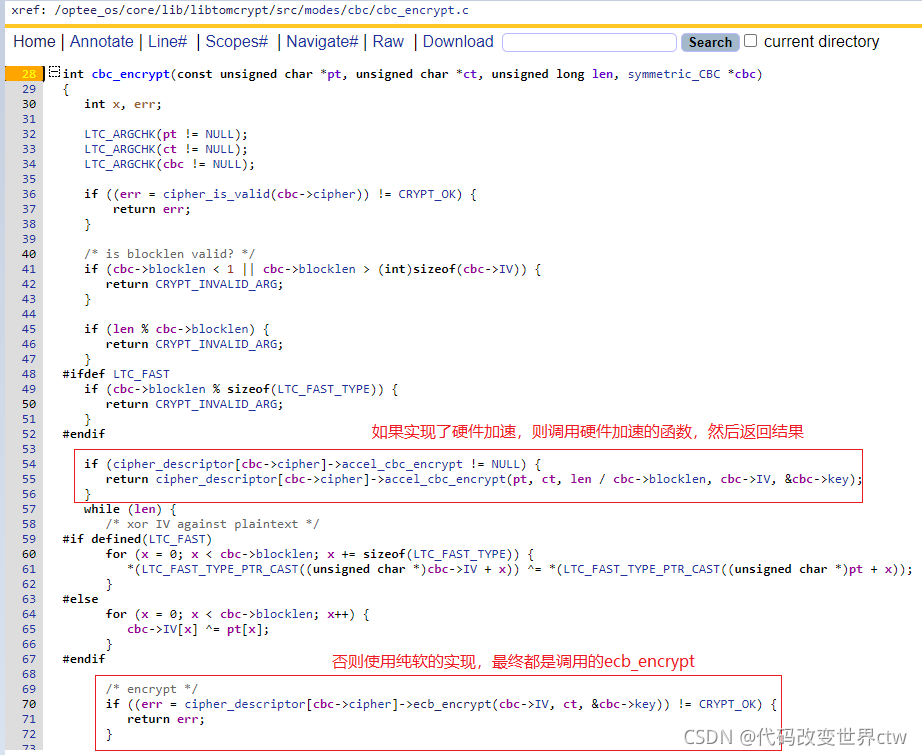
extern const struct ltc_cipher_descriptor {
/** name of cipher */
const char *name;
/** internal ID */
unsigned char ID;
/** min keysize (octets) */
int min_key_length,
/** max keysize (octets) */
max_key_length,
/** block size (octets) */
block_length,
/** default number of rounds */
default_rounds;
/** Setup the cipher
@param key The input symmetric key
@param keylen The length of the input key (octets)
@param num_rounds The requested number of rounds (0==default)
@param skey [out] The destination of the scheduled key
@return CRYPT_OK if successful
*/
int (*setup)(const unsigned char *key, int keylen, int num_rounds, symmetric_key *skey);
(4)、硬件加速(如ARM Cryptography Extension)底层算法的实现
- aes_ecb_encrypt_nblocks
- aes_ecb_decrypt_nblocks
- aes_cbc_encrypt_nblocks
- aes_cbc_decrypt_nblocks
- aes_ctr_encrypt_nblocks
- aes_xts_encrypt_nblocks
- aes_xts_decrypt_nblocks
ARM-CE底层算法的实现,都在aes_modes_armv8a_ce_a64.S文件中,最终调用的是AESD、AESE等ARM-CE指令
(optee_os/core/arch/arm/crypto/aes_modes_armv8a_ce_a64.S)
FUNC ce_aes_cbc_encrypt , :
ld1 {
v4.16b}, [x5] /* get iv */
enc_prepare w3, x2, x6
.Lcbcencloop4x:
subs w4, w4, #4
bmi .Lcbcenc1x
ld1 {
v0.16b-v3.16b}, [x1], #64 /* get 4 pt blocks */
eor v0.16b, v0.16b, v4.16b /* ..and xor with iv */
encrypt_block v0, w3, x2, x6, w7
eor v1.16b, v1.16b, v0.16b
encrypt_block v1, w3, x2, x6, w7
eor v2.16b, v2.16b, v1.16b
encrypt_block v2, w3, x2, x6, w7
eor v3.16b, v3.16b, v2.16b
encrypt_block v3, w3, x2, x6, w7
st1 {
v0.16b-v3.16b}, [x0], #64
mov v4.16b, v3.16b
b .Lcbcencloop4x
.Lcbcenc1x:
adds w4, w4, #4
beq .Lcbcencout
.Lcbcencloop:
ld1 {
v0.16b}, [x1], #16 /* get next pt block */
eor v4.16b, v4.16b, v0.16b /* ..and xor with iv */
encrypt_block v4, w3, x2, x6, w7
st1 {
v4.16b}, [x0], #16
subs w4, w4, #1
bne .Lcbcencloop
.Lcbcencout:
st1 {
v4.16b}, [x5] /* return iv */
ret
END_FUNC ce_aes_cbc_encrypt
(5)、不开启硬件加速,纯软算法的实现
(optee_os/core/lib/libtomcrypt/src/ciphers/aes/aes.c)
65 #define SETUP rijndael_enc_setup
66 #define ECB_ENC rijndael_enc_ecb_encrypt
67 #define ECB_KS rijndael_enc_keysize
68 #define ECB_DONE rijndael_enc_done
具体的实现都在如下路径,其实就是使用C语言实现的算法
(optee_os/core/lib/libtomcrypt/src/ciphers/aes/aes.c)
#ifdef LTC_CLEAN_STACK
static int _rijndael_ecb_encrypt(const unsigned char *pt, unsigned char *ct, const symmetric_key *skey)
#else
int ECB_ENC(const unsigned char *pt, unsigned char *ct, const symmetric_key *skey)
#endif
{
ulong32 s0, s1, s2, s3, t0, t1, t2, t3;
const ulong32 *rk;
int Nr, r;
LTC_ARGCHK(pt != NULL);
LTC_ARGCHK(ct != NULL);
LTC_ARGCHK(skey != NULL);
Nr = skey->rijndael.Nr;
if (Nr < 2 || Nr > 16)
return CRYPT_INVALID_ROUNDS;
rk = skey->rijndael.eK;
/*
* map byte array block to cipher state
* and add initial round key:
*/
LOAD32H(s0, pt ); s0 ^= rk[0];
LOAD32H(s1, pt + 4); s1 ^= rk[1];
LOAD32H(s2, pt + 8); s2 ^= rk[2];
LOAD32H(s3, pt + 12); s3 ^= rk[3];
#ifdef LTC_SMALL_CODE
for (r = 0; ; r++) {
rk += 4;
t0 =
Te0(LTC_BYTE(s0, 3)) ^
Te1(LTC_BYTE(s1, 2)) ^
Te2(LTC_BYTE(s2, 1)) ^
Te3(LTC_BYTE(s3, 0)) ^
rk[0];
t1 =
Te0(LTC_BYTE(s1, 3)) ^
Te1(LTC_BYTE(s2, 2)) ^
Te2(LTC_BYTE(s3, 1)) ^
Te3(LTC_BYTE(s0, 0)) ^
rk[1];
t2 =
Te0(LTC_BYTE(s2, 3)) ^
Te1(LTC_BYTE(s3, 2)) ^
Te2(LTC_BYTE(s0, 1)) ^
Te3(LTC_BYTE(s1, 0)) ^
rk[2];
t3 =
Te0(LTC_BYTE(s3, 3)) ^
Te1(LTC_BYTE(s0, 2)) ^
Te2(LTC_BYTE(s1, 1)) ^
Te3(LTC_BYTE(s2, 0)) ^
rk[3];
if (r == Nr-2) {
break;
}
s0 = t0; s1 = t1; s2 = t2; s3 = t3;
}
rk += 4;
#else
....
#endif
(5)、aes加解密算法的调用