1. Create an executable file
(1) Create a C Program
Create a new folder called “test” in C:/, and create a text document called “1.cpp” in the folder.
Like this:
Right click the file and edit it with Notepad++. Input the codes as follows.
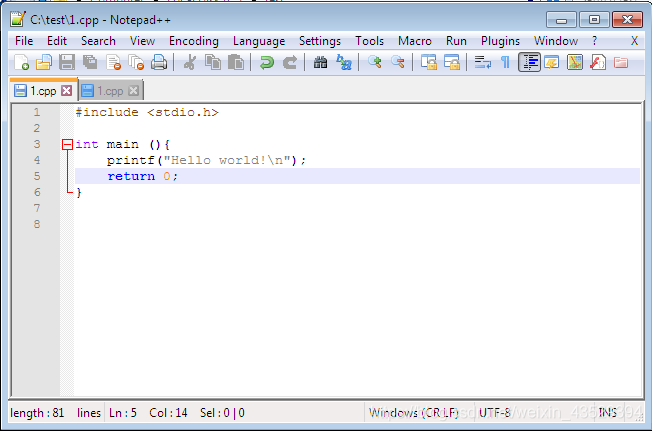
#include<stdio.h>
int main (){
printf("Hello World!\n");
return 0;
}
Save the file.
(2) Compile the C program
Open the Developer’s command prompt of Visual Studio 2017 in the start menu.
Switch to the file location C:\test using “cd C:\test”
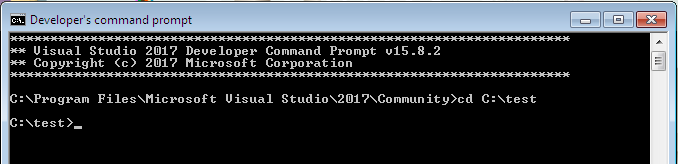
Then compile 1.cpp using “cl 1.cpp”
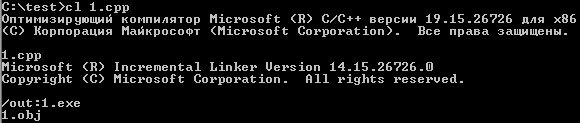
We can run it using command “1.exe”
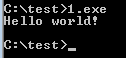
Success.
2.Pack the program
(1) Download UPX
UPX is a free, portable, extendable, high-performance executable packer for several executable formats.
We will use UPX to pack the executable file created above
Download upx from https://github.com/upx/upx/releases/download/v3.96/upx-3.96-win32.zip
Extract the zip file
(2) Pack 1.exe
- Go to the root directory of upx in Explorer, input “cmd” in path and press Enter to enter cmd in the path of upx.
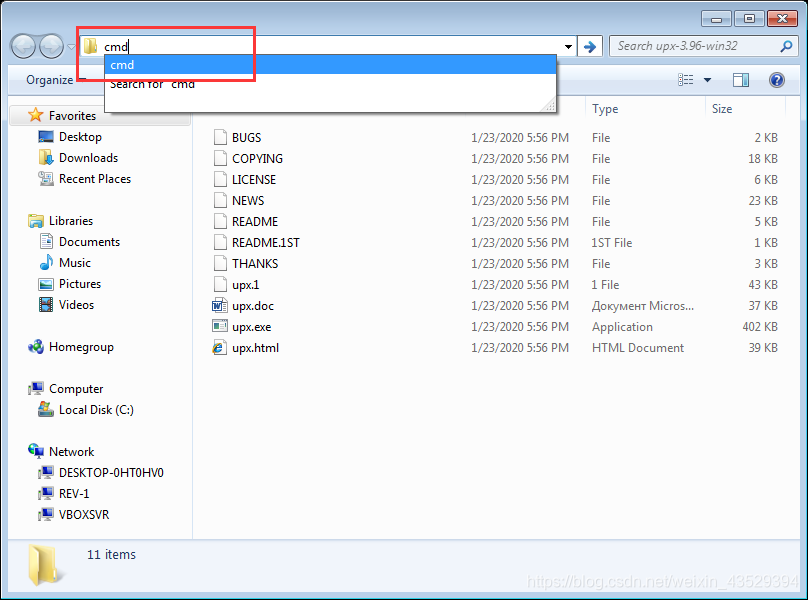
In that way, we don’t need to input the path of upx manually.
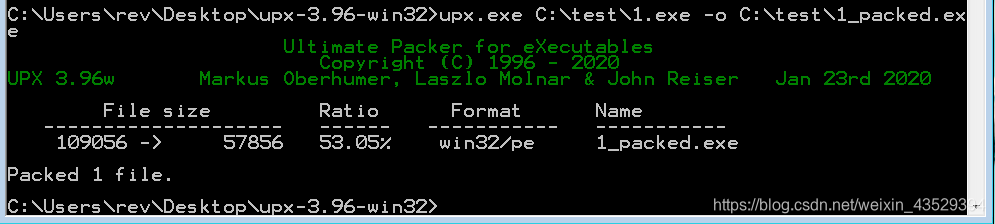
- Use command “upx.exe C:\test\1.exe -o C:\test\1_packed.exe” to pack it.
- 1_packed.exe is a packed file with the same function of 1.exe but the internal structure is different from the later. We can open it with IDA. The procedure and imports are as follows.
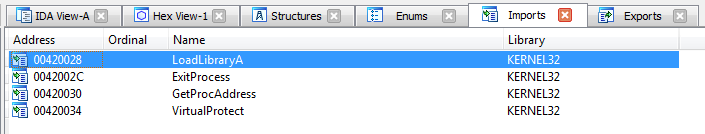
However, the procedure and imports of 1.exe are as follows.
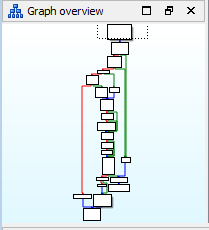

3. Unpack the program
(1) Find Original Entry Point with x32dbg
- Open x32dbg
- Drug 1_packed.exe into x32dbg
- Press F9 to run.
- Find the last jmp command
The last jmp command is the selected command in the picture.
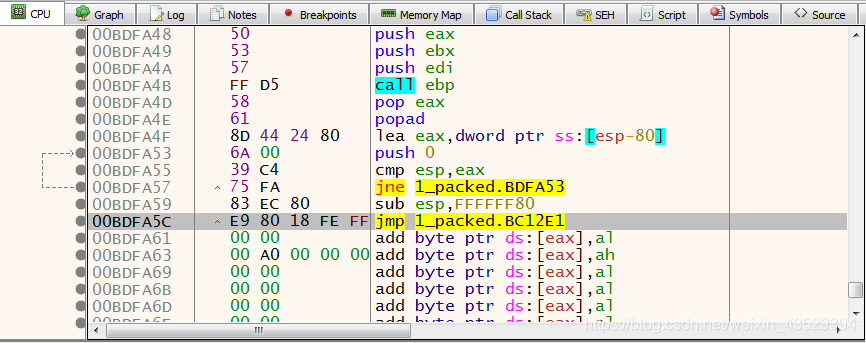
- Press F2 to set breakpoint for that command. Then Press F9 to run it.

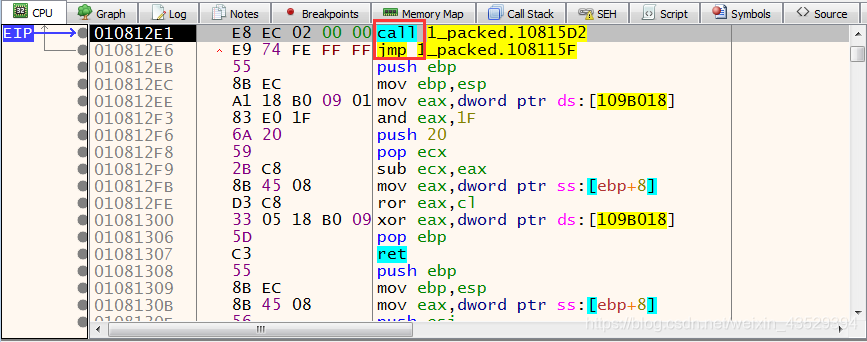
- Press F8, then we see the program which looks like C program. It begins with a “call” and a “jmp” command. In C programs the “call” command is always the entry point of the program.
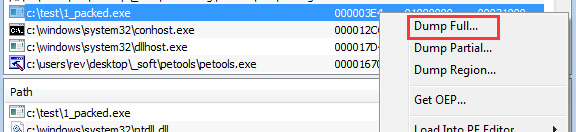
(3) Use PE Tools to save dump file
- Keep the state of x32dbg. Open PETools and find the process by its PID.
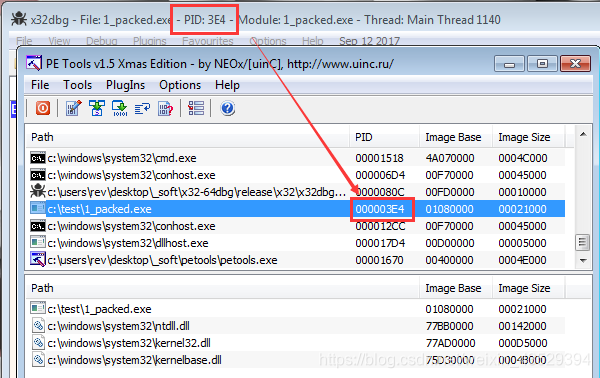
- Right click on it and select “Dump full” to save the file.
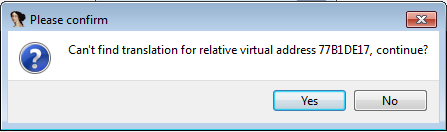
- We can find Dumped.exe cannot be run. Open it with IDA. Remeber to Press “yes” here.
(Click here and look at the first part of the article to know how to open a executable file with IDA)
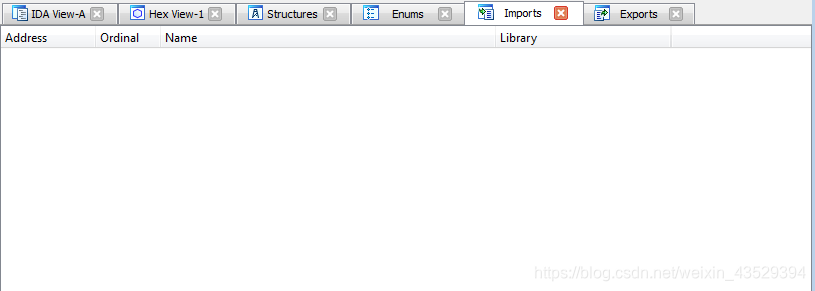
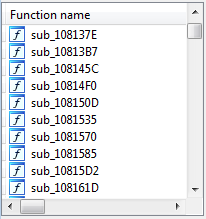
- We will find the Imports of it is empty. And there is no “strat” in function name table.
(4) Restore entry point
- Open PETools. Tools -> PE Editor. Open Dumped.exe
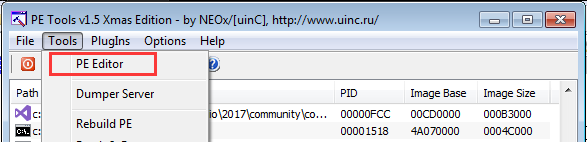
- Click “Optional Header”.
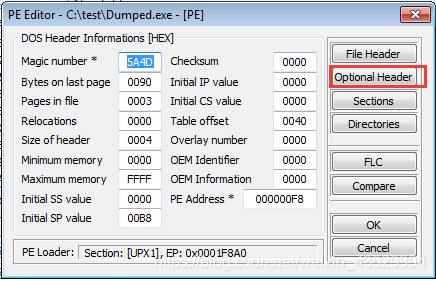
- The address of entry point is “010812E1” .
- The address of entry point is image base plus entry point. “01080000” is image base. So the entry point is 010812E1-01080000=12E1. Change the entry point inOptional Header to 12E1.
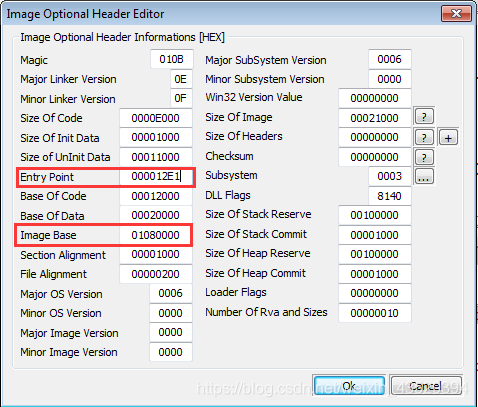
- Press Ok and press Ok.
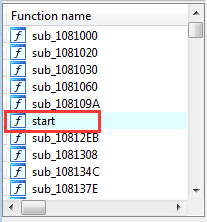
- Open Dumped.exe in IDA. Then we can see “start” in function name table. That means the entry point has been changed successfully.
(5) Get the Imports of the program
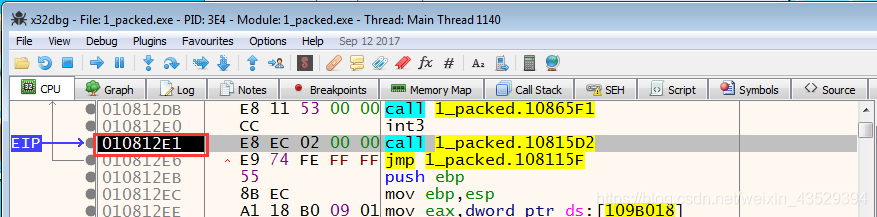
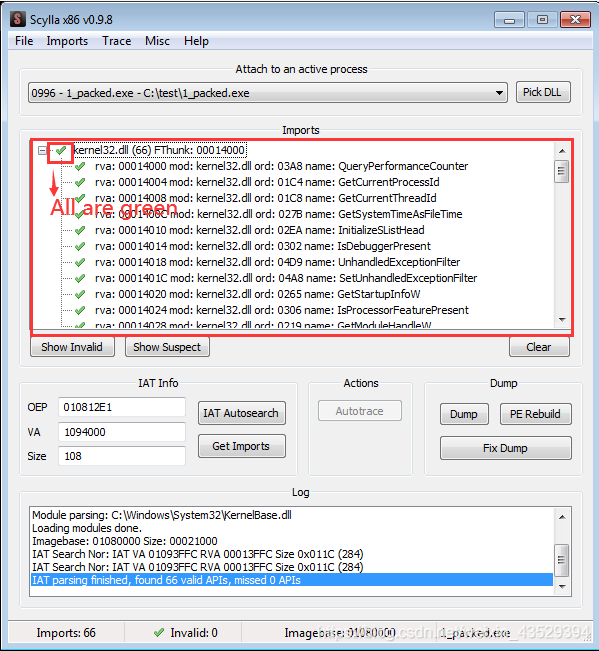
- Close IDA. Run Scylla in x32dbg.
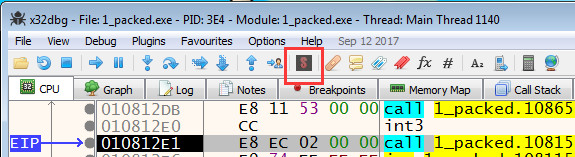
- “EIP” must point to the actual entry point of the program.
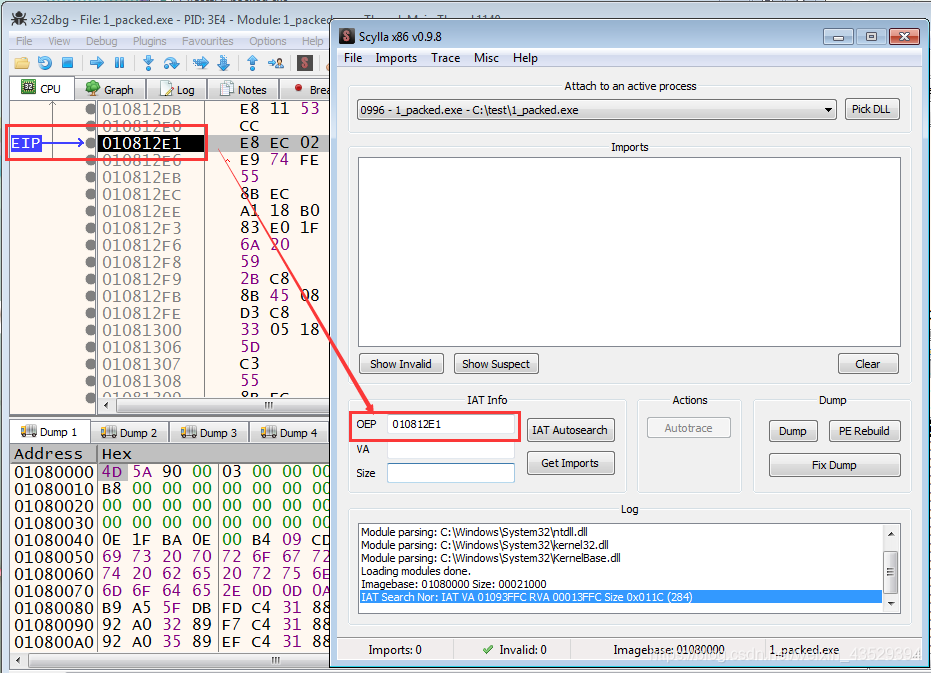
- Then press “IAT Autosearch” to automatically get the address of Import Address Table. Import Addre Table is the list of addresses of extral functions for this file.
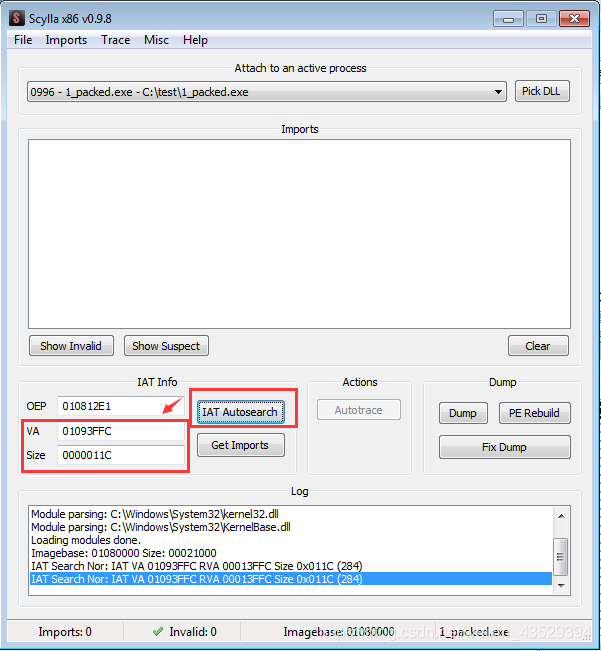
- Copy VA. Click to dump press Ctrl+G and input VA. Press OK.
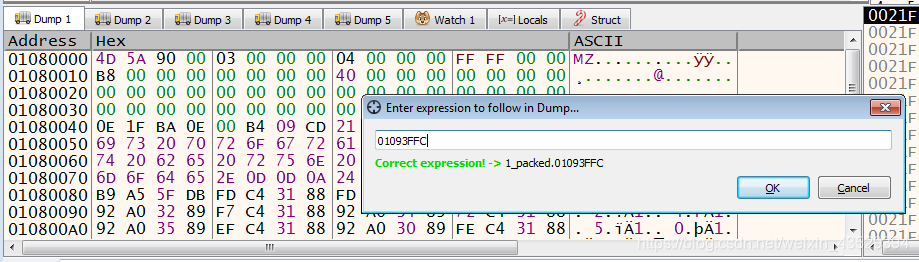
- Right click to show address.
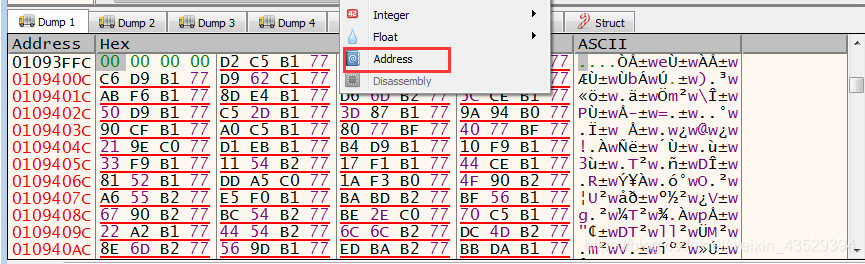
- We can see that the fisrt line is empty. So the address of “VA” needs to change to 1094000.
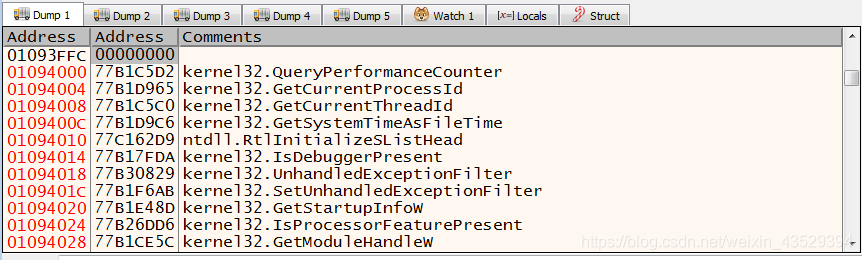
- Scroll down, then we can see the address of import table ends at 1094104.
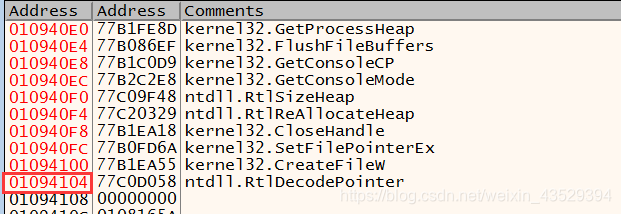
- So the size of import address table need to change to 104+4=108.
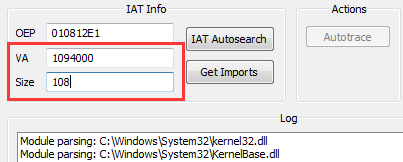
- Then press “Get Imports”. Then the functions will be imported.
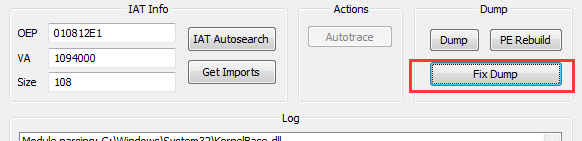
- Click “Fix Dump” and select Dump.exe. Then we got Dump_SCY.exe
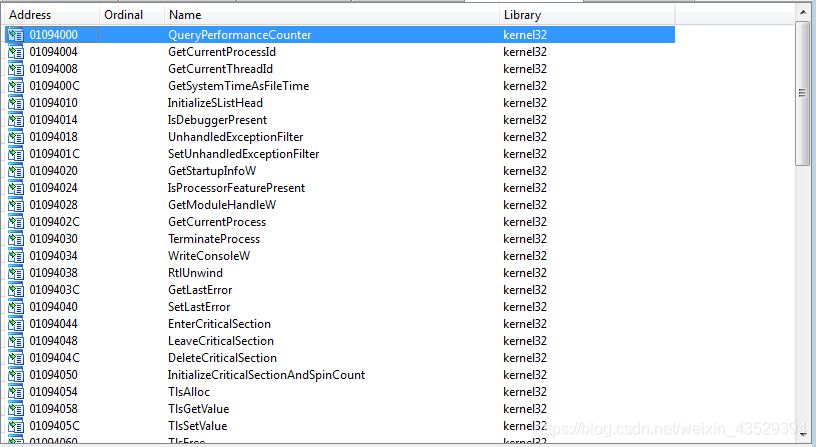
- Open Dump-SCY.exe with IDA and we can see the imports.
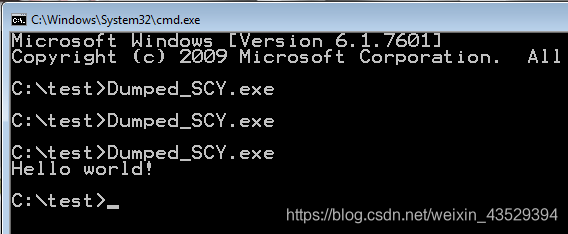
12. Run it in cmd. We can see it cannot run properly.
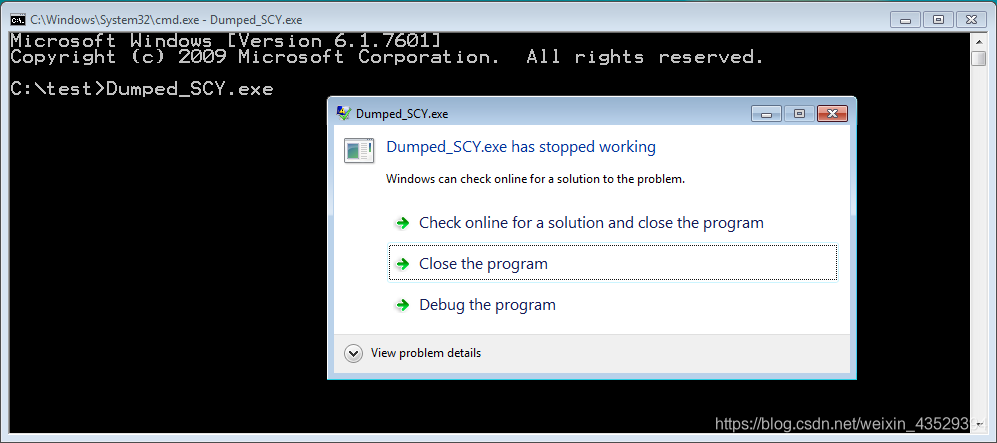
(6) Prevent address randomization
-
Make x32dbg the default debugger of the system. Run x32dbg as administrator. Options -> Preferences -> Misc -> “Set x32dbg as Just in Time debugger.” -> Save.
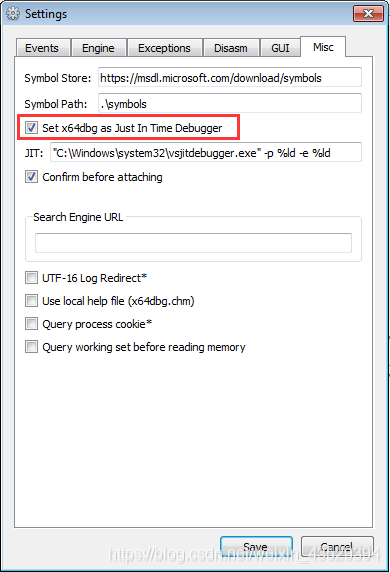
-
Run Dumped_SCY.exe again, and select Debug the program.

-
Press F8 until we see the exception.
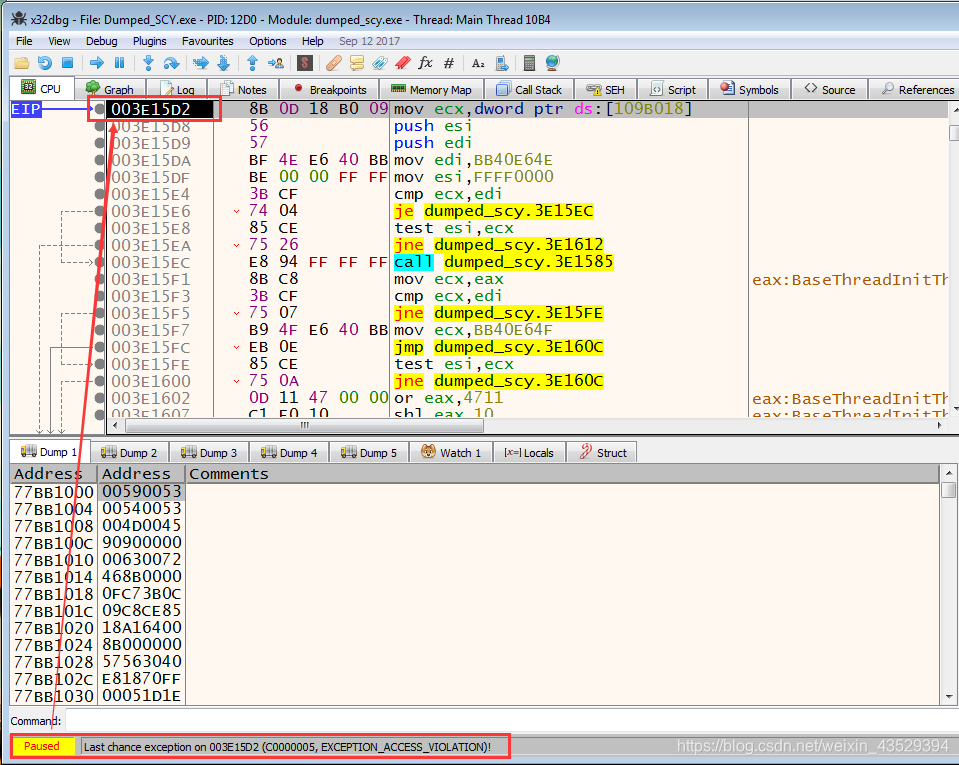
-
Press in dump, press Ctrl+G, and input 109B018. We can see that is an invalid address.
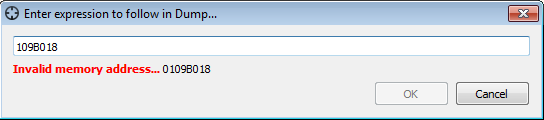
-
Because when a process starts its base address will be chosen randomly by the operation system. We need to prevent address randomization.
-
Open PETools -> Tools -> PE Editor. Open Dumped_SCY.exe. Go to File Header.
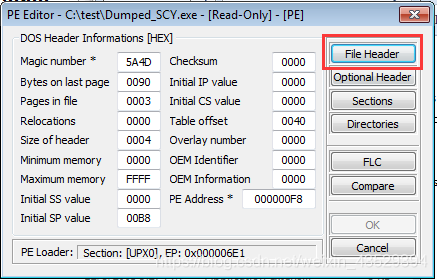
-
Go to characteristics.
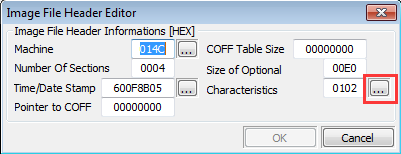
-
Enable Reloaction stripped.
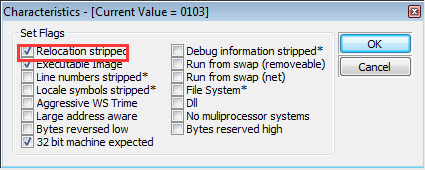
-
Press OK and OK and OK. Run it again. Success!