2018 HEBTUCTF Sudoku&Viginere
下载附件,为一个doc文件,打开后发现是一个数独游戏,和一个密码。

完成数独后:
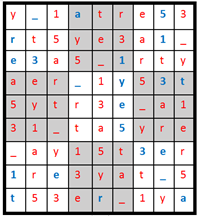
看数独表很像Viginere的密码表,根据45 34 57 74 15 35 26 86 47 39,在密码表上选取:
密文 先横后竖 先竖后横
45 r 1
34 r 5
57 y _
74 5 1
15 5 t
35 t _
26 1 3
86 r a
47 1 5
39 3 y
得到两个解密后的字符串:
rry55t1r13
15_1t_3a5y
分别尝试提交,最后确定flag为:HEBTUCTF{15_1t_3a5y}
4进制
下载附件,为一个文本文件,打开后,是一串数字:
1212 1230 1201 1213 1323 1012 1233 1311 1302 1202 1201 1303 1211 301 302 303 1331
根据题目可知是4进制。我们要转为十进制,再查ASCII表。以第一个数字为例:
1212=143+242+141+240=102,查表为f
编写程序:
s='1212 1230 1201 1213 1323 1012 1233 1311 1302 1202 1201 1303 1211 301 302 303 1331'
l=s.split(' ')
for i in l:
tmp=0
for j in range(len(i)):
tmp+=(4**j)*int(i[-j-1])
print (chr(int(tmp)),end='')
运行后就可以得到flag
栅栏密码
打开题目,给出一串字符串:fa{660cb679d7866ffalg7d27e041cfbd18ed}
根据题目,进行栅栏密码解密,使用密码机器:

得到flag
Ook
下载附件,是一个文件文件,打开后都是OoK的编码,
打开https://www.splitbrain.org/services/ook,输入密文,选择Ook to text

就可以得到flag
CRC32 BOOM!
下载附件,为一个压缩包
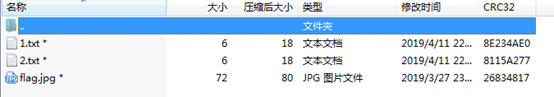
看到1,.txt和2.txt的文件大小很小,只有6个字节,尝试使用crc爆破:
使用CRC32.py进行爆破:


将两张图内的字符串组成密码字典:
s1=["1x5NQ8","9O2a5H","G1qi4N","IsCdeH","NjDZOc","OvJ7Un","P8CUk2","PT0xov","QTqIto","Rh5f6k","XBiGbJ","Z3AdV_","gsombC","mY3L6b","newctf","p7plP7","t3mmQT","vBENeA"]
s2=["17LE1V","53QD05","5Cm55e","6cfFvu","9l8GQb","BzTRNZ","EcSldq","HqVcs7","JpB1Br","LuKbrT","TRyOcs","_5IbAC","bugku_","dpn8Ey","mz9jRH","q5ekFH","w0l8vn","yOOyO0","zRUFdx"]
l=[]
for i in s2:
for j in s1:
l.append(i+j)
with open ('pw.txt', 'w') as fo:
for k in l:
fo.write(k+'\n')
使用Advanced Archive Password Recovery进行字典爆破:

得到密码为bugku_newctf
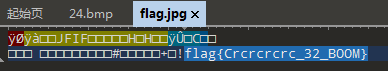
解压出flag.jpg。结果无法打开。
用文本打开,可以看到flag就在文件尾部:
2018 AFCTF Morse
下载附件为一个压缩包,打开后为一个文本,内容如下:
-..../.----/-..../-..../-..../...--/--.../....-/-..../-..../--.../-.../...--/.----/--.../...--/..---/--.../--.../....-/...../..-./--.../...--/...--/-----/...../..-./...--/...--/...--/....-/...--/...../--.../----./--.../-..
将/替换为空格。进行莫斯解密:
得到:
61666374667B317327745F73305F333435797D
进行Hex to text:

得到flag
山东省大学生网络技术大赛-baby
下载附件,是一个脚本文件:
# -*- coding: utf-8 -*-
from Crypto.PublicKey import RSA
import libnum
import uuid
flag = "flag{***************}"
rsa = RSA.generate(4096,e=3)
p = rsa.p
d = rsa.d
e = rsa.e
N = rsa.n
m = libnum.s2n(flag)
c = pow(m, e, N)
print "[+]c:",c
print "[+]N:",N
'''
[+]c: 3442467842482561323703237574537907554035337622762971103210557480050349359873041624336261782731509068910003360547049942482415036862904844600484976674423604861710166033558576921438068555951948966099658902606725292551952345193132973996288566246138708754810511646811362017769063041425115712305629748341207792305694590742066971202523405301561233341991037374101265623265332070787449332991792097090044761973705909217137119649091313457206589803479797894924402017273543719924849592070328396276760381501612934039653
[+]N: 691316677109436623113422493782665795857921917893759942123087462879884062720557906429183155859597756890896192044003240821906332575292476160072039505771794531255542244123516929671277306361467074545720823735806308003091983427678300287709469582282466572230066580195227278214776280213722215953097747453437289734469454712426107967188109548966907237877840316009828476200388327329144783877033491238709954473809991152727333616022406517443130542713167206421787038596312975153165848625721911080561242646092299016802662913017071685740548699163836007474224715426587609549372289181977830092677128368806113131459831182390520942892670696447128631485606579943885812260640805756035377584155135770155915782120025116486061540105139339655722904721294629149025033066823599823964444620779259106176913478839370100891213072100063101232635183636552360952762838656307300621195248059253614745118852163569388418086291748805100175008658387803878200034840215506516715640621165661642177371863874586069524022258642915100615596032443145034847031564356671559179212705466145609698475546210994748949121359853094247990533075004393534565421776468785821261291309463205314057882016266066365636018084499158806717036972590848458891019171583268920180691221168453612029698510271
'''
是一个RSA算法,给出了n,c和e,但e很小为3。可以确定是低指数攻击。写脚本如下:
from gmpy2 import iroot
import libnum
n = 691316677109436623113422493782665795857921917893759942123087462879884062720557906429183155859597756890896192044003240821906332575292476160072039505771794531255542244123516929671277306361467074545720823735806308003091983427678300287709469582282466572230066580195227278214776280213722215953097747453437289734469454712426107967188109548966907237877840316009828476200388327329144783877033491238709954473809991152727333616022406517443130542713167206421787038596312975153165848625721911080561242646092299016802662913017071685740548699163836007474224715426587609549372289181977830092677128368806113131459831182390520942892670696447128631485606579943885812260640805756035377584155135770155915782120025116486061540105139339655722904721294629149025033066823599823964444620779259106176913478839370100891213072100063101232635183636552360952762838656307300621195248059253614745118852163569388418086291748805100175008658387803878200034840215506516715640621165661642177371863874586069524022258642915100615596032443145034847031564356671559179212705466145609698475546210994748949121359853094247990533075004393534565421776468785821261291309463205314057882016266066365636018084499158806717036972590848458891019171583268920180691221168453612029698510271
c = 3442467842482561323703237574537907554035337622762971103210557480050349359873041624336261782731509068910003360547049942482415036862904844600484976674423604861710166033558576921438068555951948966099658902606725292551952345193132973996288566246138708754810511646811362017769063041425115712305629748341207792305694590742066971202523405301561233341991037374101265623265332070787449332991792097090044761973705909217137119649091313457206589803479797894924402017273543719924849592070328396276760381501612934039653
k = 0
while 1:
res=iroot(c+k*n,3)
if(res[1]==True):
print(libnum.n2s(int(res[0])))
break
k=k+1
运行后,就可以得到flag
键盘之争
打开之后是看不懂的字符串,根据题目,可能是键盘布局不一样。
将QWER布局转为dvorak布局,使用脚本:
dic={r"'":"q",
r",":"w",
r".":"e",
"p":"4",
"y":"t",
"f":"y",
"g":"u",
"c":"i",
"r":"o",
"l":"p",
r"/":r"[",
r"=":r"]",
r'"':'Q',
r"<":"W",
r">":"E",
"P":"R",
"Y":"T",
"F":"Y",
"G":"U",
"C":"I",
"R":"O",
"L":"P",
r"?":r"{",
r"+":r"}",
"a":"a",
"A":"A",
"o":"s",
"O":"S",
"e":"d",
"E":"D",
"u":"f",
"U":"F",
"i":"g",
"I":"G",
"d":"h",
"D":"H",
"h":"j",
"H":"J",
"t":"k",
"T":"K",
"n":"l",
"N":"L",
"s":";",
"S":":",
r"-":r"'",
r'_':r'"',
r";":"z",
r":":"Z",
"q":"x",
"Q":"X",
"j":"c",
"J":"C",
"k":"v",
"K":"V",
"x":"b",
"X":"B",
"b":"n",
"B":"N",
"m":"m",
"M":"M",
"w":r",",
"W":r"<",
"v":r".",
"V":r">",
"z":r"/",
"Z":r"?",
r'!':"!",
r"@":r"@",
r"#":r"#",
r"$":r"$",
r"%":r"%",
r"^":r"^",
r"&":r"&",
r"*":r"*",
r"(":r"(",
r")":r")",
r"[":r"-",
r"]":r"=",
r"{":r"_",
r"}":r"+"}
s=r'ypau_kjg;"g;"ypau+'
for i in s:
print (" ".join([key for key, value in dic.items() if value == i]),end='')
运行后,就可以看到flag
将{}内的进行md5加密,就可以提交了。
2020sdnisc-ezRSA
下载附件,打开后为一个文本,内容为:
n = 0xa1d4d377001f1b8d5b2740514ce699b49dc8a02f12df9a960e80e2a6ee13b7a97d9f508721e3dd7a6842c24ab25ab87d1132358de7c6c4cee3fb3ec9b7fd873626bd0251d16912de1f0f1a2bba52b082339113ad1a262121db31db9ee1bf9f26023182acce8f84612bfeb075803cf610f27b7b16147f7d29cc3fd463df7ea31ca860d59aae5506479c76206603de54044e7b778e21082c4c4da795d39dc2b9c0589e577a773133c89fa8e3a4bd047b8e7d6da0d9a0d8a3c1a3607ce983deb350e1c649725cccb0e9d756fc3107dd4352aa18c45a65bab7772a4c5aef7020a1e67e6085cc125d9fc042d96489a08d885f448ece8f7f254067dfff0c4e72a63557L
e1 = 0xf4c1158fL
c1 = 12051796366524088489284445109295502686341498426965277230069915294159131976231473789977279364263965099422235647723775278060569378071469131866368399394772898224166518089593340803913798327451963589996734323497943301819051718709807518655868569656941242449109980876397661605271517459716669684900920279597477446629607627693769738733623143693170696779851882404994923673483971528314806130892416509854017091137325195201225617407959645788145876202882024723106204183257094755002924708009138560347432552090905489132135154932987521239299578509008290614398700799670928805692609756924823628055245227290288940649158862576448537833423L
e2 = 0xf493f7d1L
c2 = 16648382384980770705624348910895797622774711113202207693584907182552301186239613809347201161450012615995859738410661452438496756353485538305614949211776668793864984429696790944750894691957799234264508530084026894611228513698963347402329109838109621609770406925700520983387811451074838470370044678634099202003480925903267508744006195455234025325060817223813858985074720872124168142943926467694676717713503559007112874381750005406371400109962943508349497151148446064846096531445037416174913915923050332242843403926133165817310272633884358263778516770288515592959832151762499526363131801945163501999337808208074381212795L
发现只有一个n,两个e,两个c。推测为共模攻击。
使用脚本:
from libnum import n2s,s2n
from gmpy2 import invert
def egcd(a, b):
if a == 0:
return (b, 0, 1)
else:
g, y, x = egcd(b % a, a)
return (g, x - (b // a) * y, y)
def main():
n = int('0xa1d4d377001f1b8d5b2740514ce699b49dc8a02f12df9a960e80e2a6ee13b7a97d9f508721e3dd7a6842c24ab25ab87d1132358de7c6c4cee3fb3ec9b7fd873626bd0251d16912de1f0f1a2bba52b082339113ad1a262121db31db9ee1bf9f26023182acce8f84612bfeb075803cf610f27b7b16147f7d29cc3fd463df7ea31ca860d59aae5506479c76206603de54044e7b778e21082c4c4da795d39dc2b9c0589e577a773133c89fa8e3a4bd047b8e7d6da0d9a0d8a3c1a3607ce983deb350e1c649725cccb0e9d756fc3107dd4352aa18c45a65bab7772a4c5aef7020a1e67e6085cc125d9fc042d96489a08d885f448ece8f7f254067dfff0c4e72a63557',16)
c1 = 12051796366524088489284445109295502686341498426965277230069915294159131976231473789977279364263965099422235647723775278060569378071469131866368399394772898224166518089593340803913798327451963589996734323497943301819051718709807518655868569656941242449109980876397661605271517459716669684900920279597477446629607627693769738733623143693170696779851882404994923673483971528314806130892416509854017091137325195201225617407959645788145876202882024723106204183257094755002924708009138560347432552090905489132135154932987521239299578509008290614398700799670928805692609756924823628055245227290288940649158862576448537833423
c2 = 16648382384980770705624348910895797622774711113202207693584907182552301186239613809347201161450012615995859738410661452438496756353485538305614949211776668793864984429696790944750894691957799234264508530084026894611228513698963347402329109838109621609770406925700520983387811451074838470370044678634099202003480925903267508744006195455234025325060817223813858985074720872124168142943926467694676717713503559007112874381750005406371400109962943508349497151148446064846096531445037416174913915923050332242843403926133165817310272633884358263778516770288515592959832151762499526363131801945163501999337808208074381212795
e1 = int('0xf4c1158f',16)
e2 = int('0xf493f7d1',16)
s = egcd(e1, e2)
s1 = s[1]
s2 = s[2]
if s1<0:
s1 = - s1
c1 = invert(c1, n)
elif s2<0:
s2 = - s2
c2 = invert(c2, n)
m = pow(c1,s1,n)*pow(c2,s2,n) % n
print n2s(m)
if __name__ == '__main__':
main()
运行后得到flag:
baby_dsa
DSA完全不懂,现学,相关知识如下链接:
https://www.jarvisw.com/?p=169
用大佬的脚本:
from Crypto.Util.number import *
from hashlib import sha512,md5
def hash(message):
return int(sha512(message).hexdigest(), 16)
def sign(message, pubkey, privkey, random1):
p, q, g, y = pubkey
x = privkey
k = pow(y, x, g) * random1 % q
r = pow(g, k, p) % q
s = inverse(k, q) * (hash(message) + x * r) % q
return r, s
public = (3297226463037324458008837284498963372649038889390685051849680175016505646001761220109858921624266044035133134135402561235635833428206886888308027772353030767400921078346868377298401213812053250316002033941692272192644613252296579884516731560436501073253924457646558698855484781747029397755111633297587215976579633451933658235385386539518006570069653575146060016811911140614606471930327341368582979836042585406811352236326065292636484550807213756482153084427714549694264685695977531537425682212155553568848666088576932888234659355213664909753781753917401161977762663658097504411914908081677033980915039079517766159760522261279115347385813009437510156898969769563687869495721977265444799585634019880951532080217960456901788918439265788169910062822889580199366417455186595489973000351770200485095008494228829300145039695936946379585625051402553034971207474762463147744467360158847593356030745194143276254949463650698210515569533, 82302835442112137125891403368151249910268706824854786126600390413622302196443, 1156233264299340971106498371495495695225880592354374034142195518472540521911699506391311324676590685365234887170345722135060009885002334748836477169806166169806180231794918961214520698361874839110454610266388341977984902756569838594616255112661600466818870137432772800368859461445854700956291885576855069405183771903076277144927769029433730710613058788277691211698675287829143272152835171859480781061918556840079857761203012054552142555673071865310355331986288606422711525790877591376770834180618492794265362178603111236615495225612101250344421932588038244804199229449738675082560512062564365473035097263889257937140778993389305893378514344032352806521972367991027459721160744835688761657797398841523104074451793557924512992305640697344011520550723893828185707635141404445213445935586965289450282024222064488965878769991566367115153619761583843561579531705057955933288008556165952066173304891391375100346312776539530448611005, 290999623787731812697719691852061290246619413463636312382146969900546384514710782843153962704851916091601679028830866176332331519515156301401537173069908181509028464322647352256632424684809349121024262597006913707483811117644197481959053785475083406472583099140506505071300193356002443007750220524932219191932969202270343323955035291396808472686684787610559114702054784699365490860392737061056233160308943296478540798353134878937088336672928162894332961762277559345860479916248086821117811990391025187125193074059001086441305977133252774698996653122297123447837449168657347308016270030881395674066421144002959751936839166935726200833785132736328859710351871352567511516142170956091885352178579302299634322254818383978585773136692588922976043617337904545396146755609284163743476297772686548475170197605412847689587171522453229055932712714154869989454808561458852031769119489235598402066924082778376081494632258448434048562053)
p, q, g, y = public
tmp1 = (b'0234e7971889def7e60348f77db94b7a', (10859236269959765735236393779936305217305574331839234502190226708929991582386, 13707557323895695260471053137828523837745895683218331343360027380310980108819))
tmp2 = (b'16c5ac270b72f70319657b4410d985d4', (41960642246379067640524709416001536058292817319109764317369777224426218746518, 74676725322515593502346275468843411563746982149373670021082686341369076719088))
message1, r1, s1 = tmp1[0], tmp1[1][0], tmp1[1][1]
message2, r2, s2 = tmp2[0], tmp2[1][0], tmp2[1][1]
hm1, hm2 = hash(message1), hash(message2)
#print(hm1, hm2)
for random1 in range(1, 512):
for random2 in range(1, 512):
random1_inv = inverse(random1, q)
random_mul = random1_inv * random2
x = (s1 * hm2 - s2 * hm1 * random_mul) * inverse(s2 * r1 * random_mul - s1 * r2, q)
x = x % q
#print(x)
#print(sign(message1, public, x, random1))
#print(tmp1[1])
if sign(message1, public, x, random1) == tmp1[1]:
print(x)
flag = 'flag{'+md5(long_to_bytes(x)).hexdigest()+'}'
print(flag)
print(random2)
exit()
print(random1)
得到flag:

2018 AFCTF BASE
下载附件,是一个文本,很大,打开看了下,是一个很长的字符串,有09,AZ,怀疑是16进制,
解码后,看到后面有个“=”,怀疑是base64。
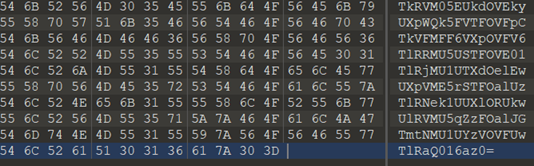
多次base64后,看到结尾是“=”,但解码后是乱码,看到题目是base。怀疑不是base32,就是base16。
写脚本:
import base64
with open (r'C: \flag_encode.txt','r',encoding='utf-8') as f:
for a in f:
while 1:
try :
a=base64.b64decode(a).decode("utf-8")
except:
pass
try:
a=base64.b32decode(a).decode("utf-8")
except:
pass
try:
a=base64.b16decode(a).decode('utf-8')
except:
pass
if "{" in a:
print (a)
break
运行后得到flag
2018 AFCTF MagicNum
下载附件,是一个文本,里面是好几个小数,

不明白有什么用,先进行进制转换
将浮点型转为16进制:
运行脚本,就可看到flag:
import struct
import binascii
s=[72065910510177138000000000000000.000000,71863209670811371000000.000000,18489682625412760000000000000000.000000,72723257588050687000000.000000,4674659167469766200000000.000000,19061698837499292000000000000000000000.000000]
a=''
b=''
for i in s:
i=float(i)
tmp=struct.pack('<f', i).hex()#小端
a+=tmp
for j in s:
j=float(j)
tmp=struct.pack('>f', j).hex()#大端
b+=tmp
print (binascii.a2b_hex(a))
print (binascii.a2b_hex(b))